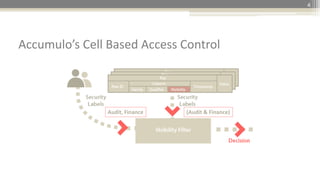
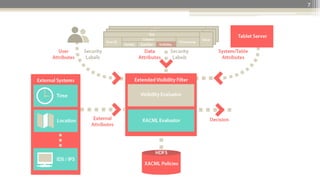
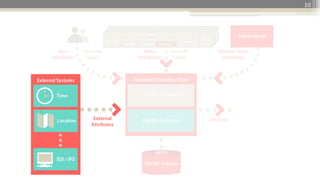
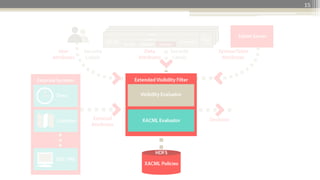
The document presents a project design for extending Accumulo to support Attribute-Based Access Control (ABAC) using XACML, aiming for minimal code changes and compatibility with existing cell-based access control. It highlights the strategic importance of ABAC in various governmental and enterprise contexts, discusses the integration and architecture of XACML, and provides use cases to elaborate on policy enforcement scenarios. The initiative seeks to enhance security, including risk-based access controls, while building community support around open-source solutions.























![30
• Possible Attribute
Use Case – Broker
Attribute Name Possible Values
ROLE CUSTOMER | BROKER
TIMEOFDAY [00:00:00, 23:59:59]
DAYOFWEEK MONDAY | TUESDAY | WEDNESDAY | THURSDAY | FRIDAY
| SATURDAY | SUNDAY
LOCATION OFFICE_XYZ | NOT_IN_OFFICE
IS_CUSTOMERS_BROKER True | False
BROKER_ID Any unique alphanumeric identifier](https://image.slidesharecdn.com/accumulosummit2015-extendingaccumulotosupportabacusingxacml-gurcangercek-v01-150501224033-conversion-gate02/85/Accumulo-Summit-2015-Extending-Accumulo-to-Support-ABAC-using-XACML-Security-30-320.jpg)
![31
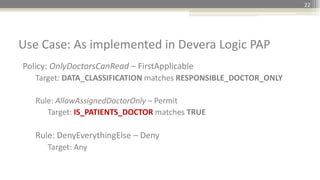
Policy Definition:
Policy: In_Office_Policy - First applicable
Target: Location regexp-match Office_[0-9] [0-9] [0-9]
and Role matches Broker
and isCustomersBroker matches True
Rule: Allow_During_Wek_Day – Permit
Target: DayOfTheWeek matches one of Monday, Tuesday, Wednesday, Thursday, Friday
Condition: TimeOfTheDay after or on 09:00:00 and TimeOfTheDay before or on 17:30:00
Rule: Deny_Other_Requests – Deny
Target: any
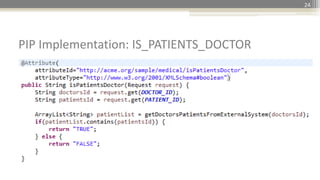
Use Case: As implemented in Devera Logic PAP](https://image.slidesharecdn.com/accumulosummit2015-extendingaccumulotosupportabacusingxacml-gurcangercek-v01-150501224033-conversion-gate02/85/Accumulo-Summit-2015-Extending-Accumulo-to-Support-ABAC-using-XACML-Security-31-320.jpg)
