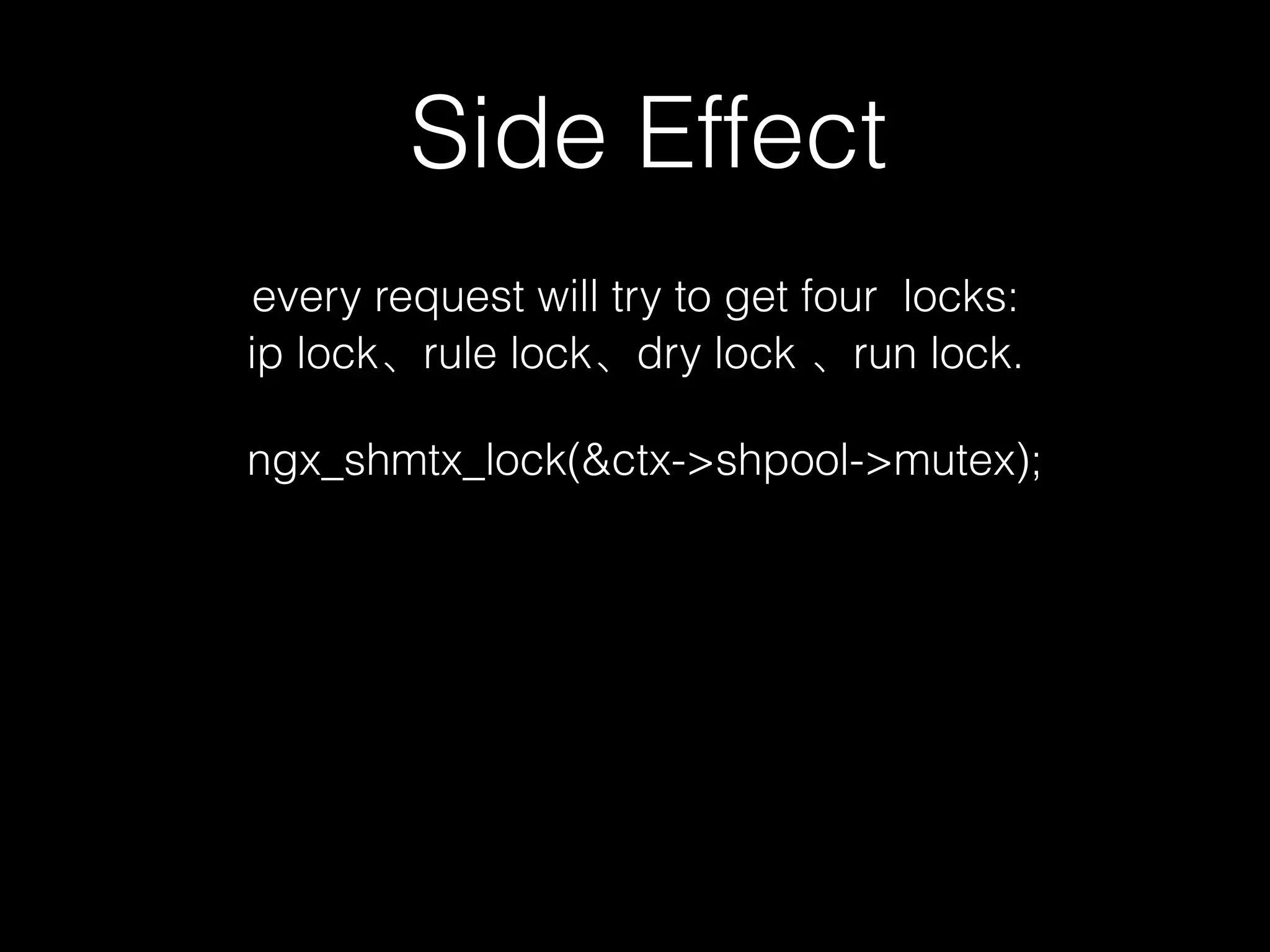
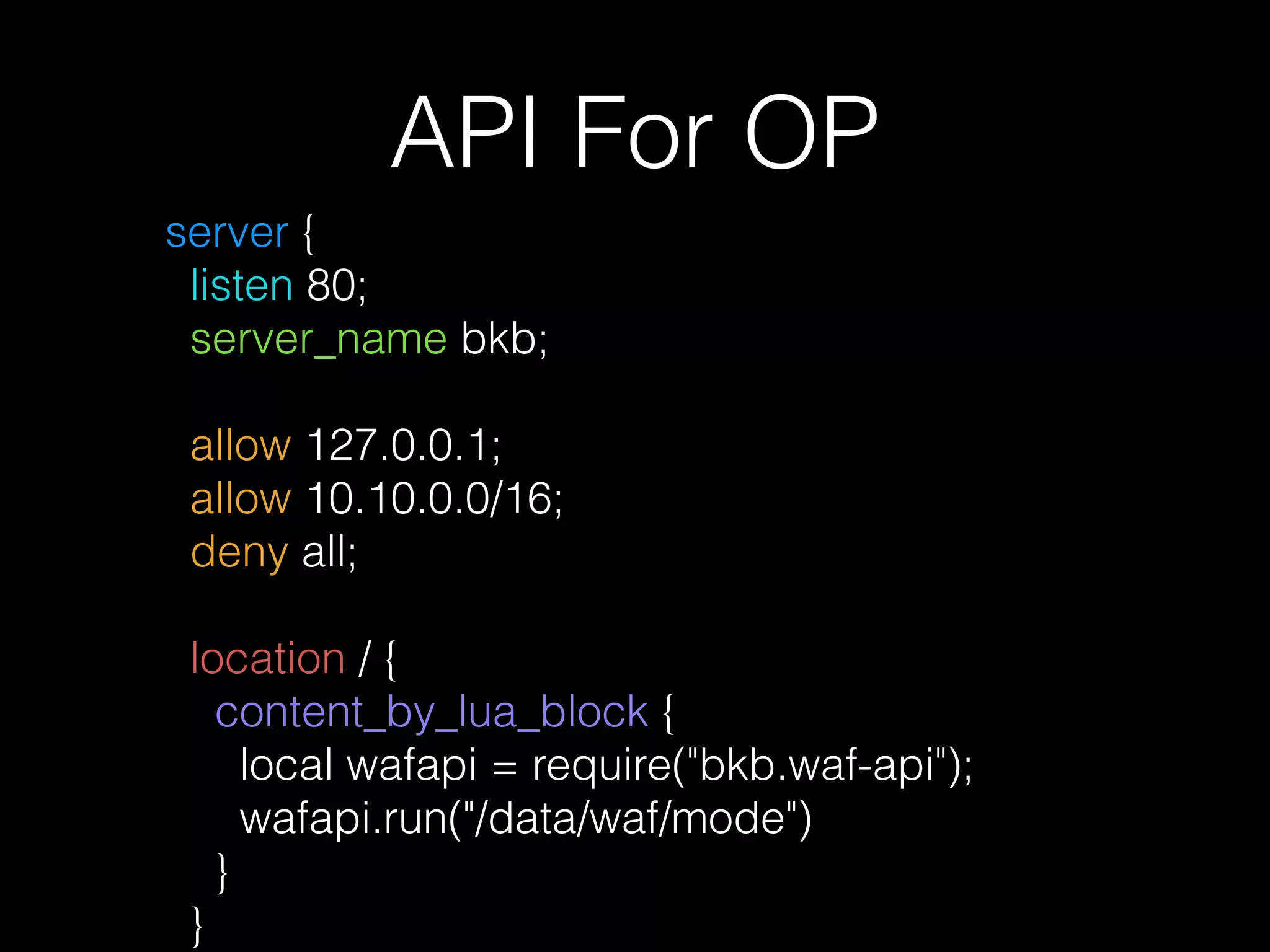
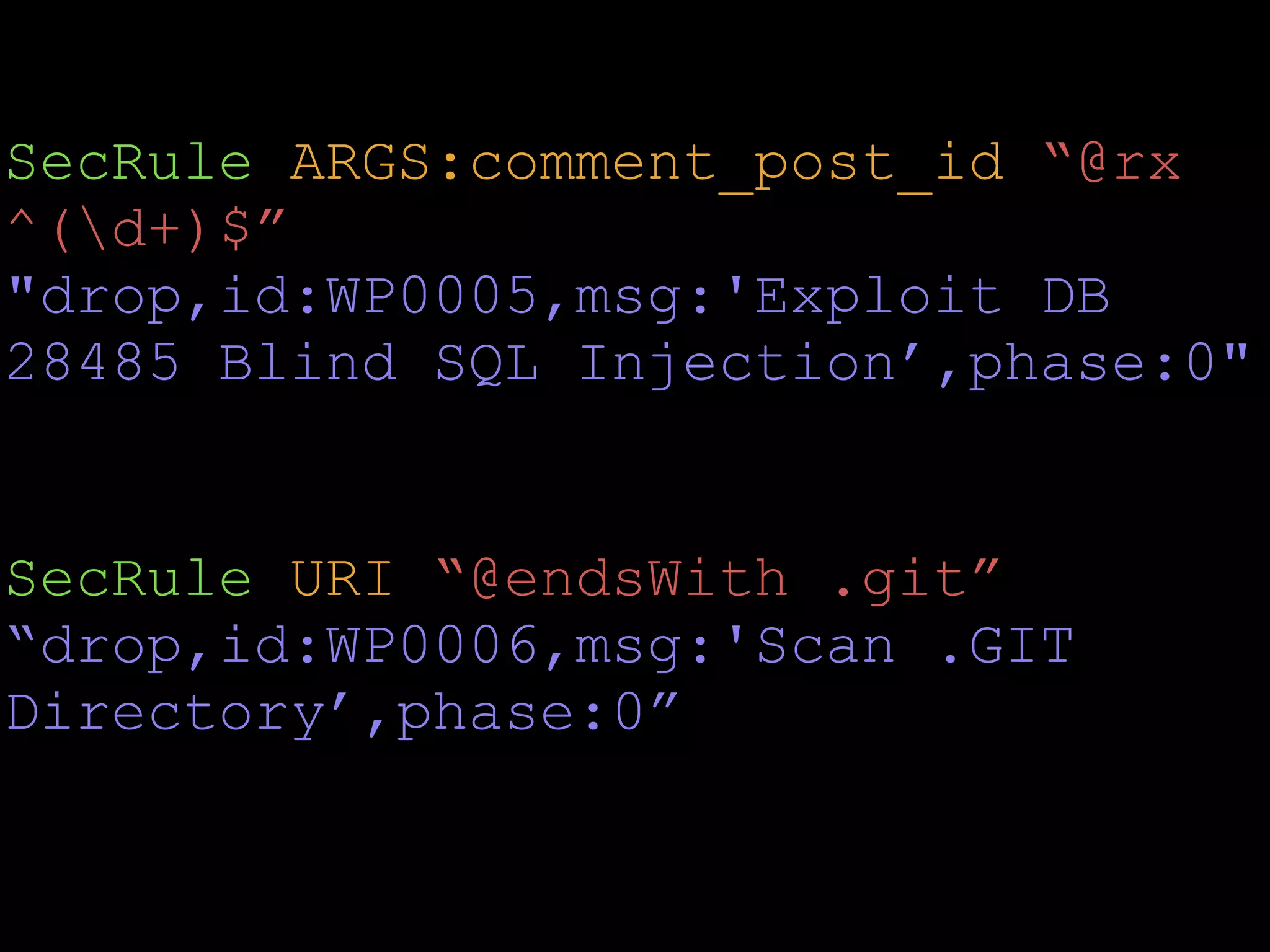
This document describes a lightweight Web Application Firewall (WAF) called A Little WAF. It summarizes the key components and functionality of the WAF, including that it uses Lua to filter HTTP traffic, compiles ModSecurity rules to Lua, supports IP blocking and common attack protection, and provides an API for configuration and monitoring.













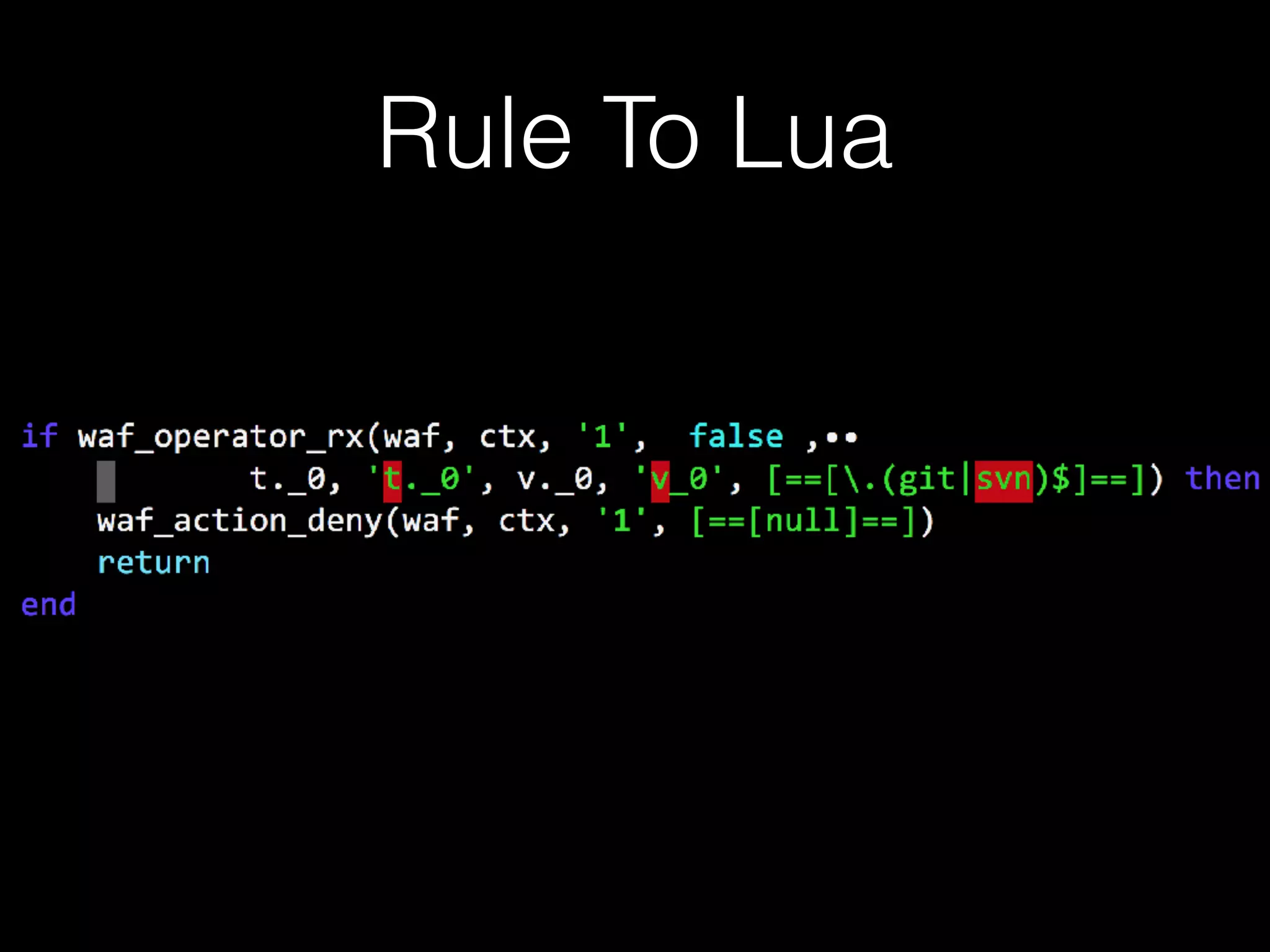



![local chunk, err = loadstring(code, ‘=rule.lua’)
if not err then
package.loaded[‘rule’] = chunk()
end
loadstring
PS: LuaVM](https://image.slidesharecdn.com/alittlewaf-161016115505/75/A-little-waf-22-2048.jpg)