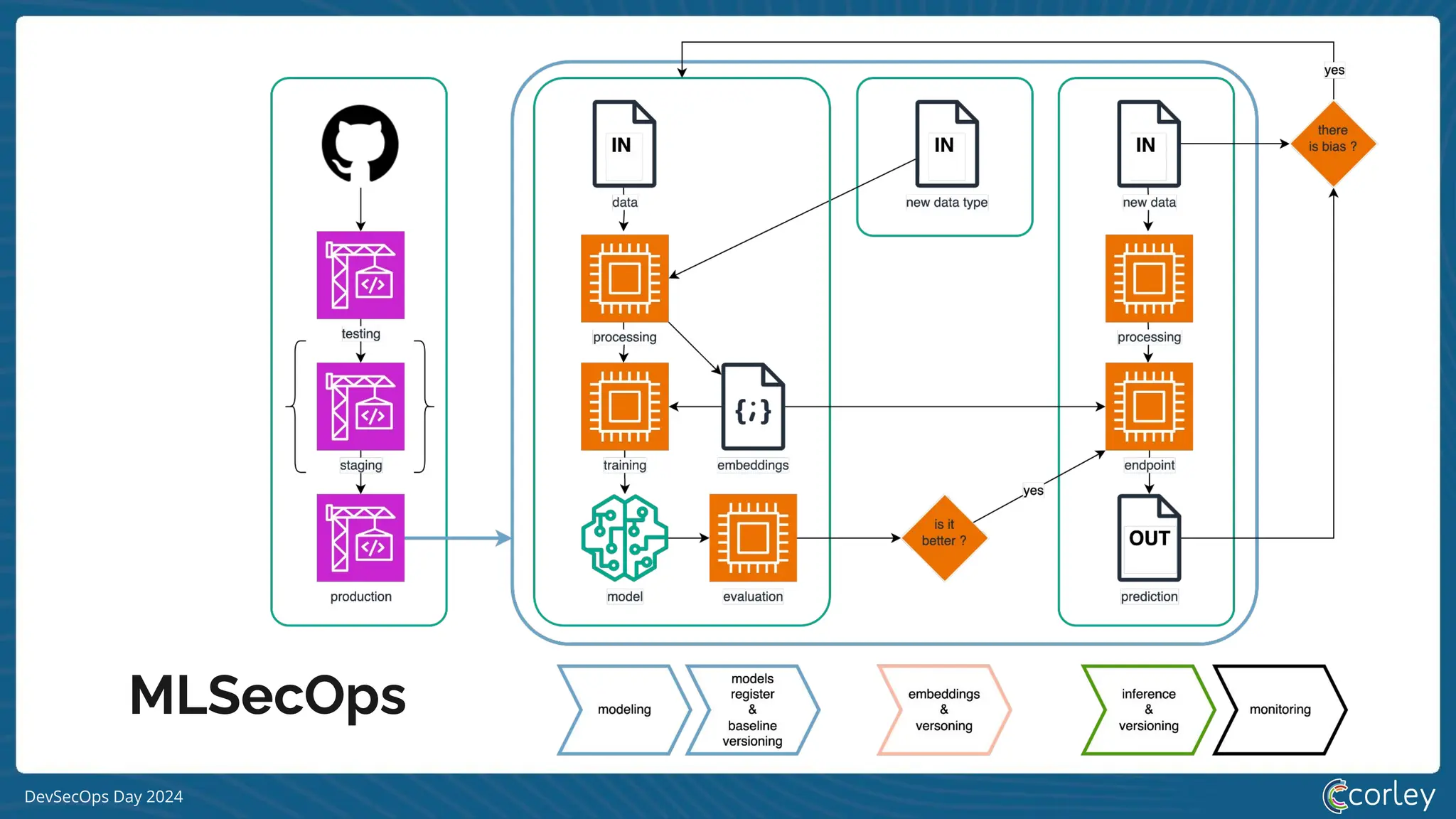
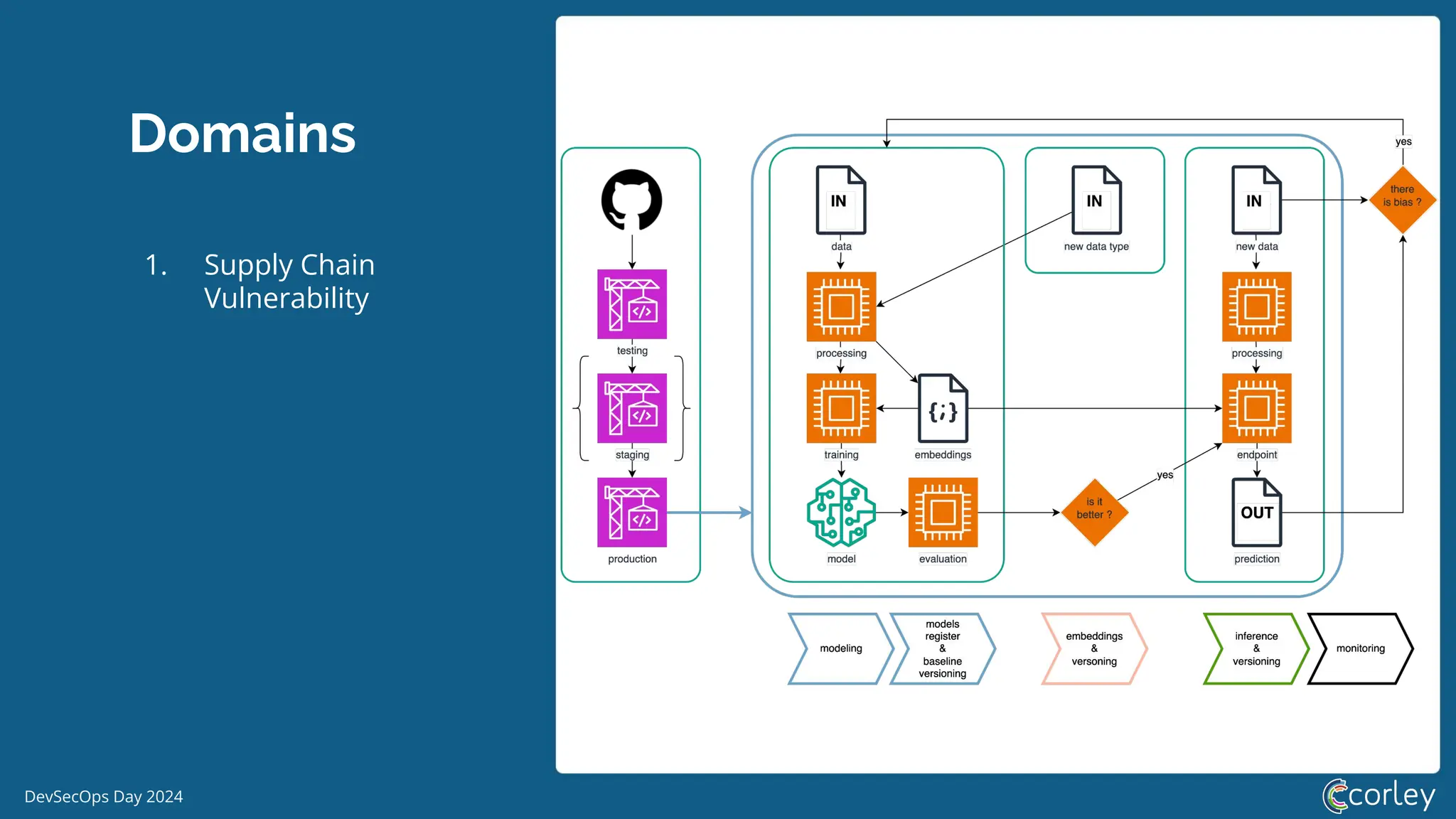
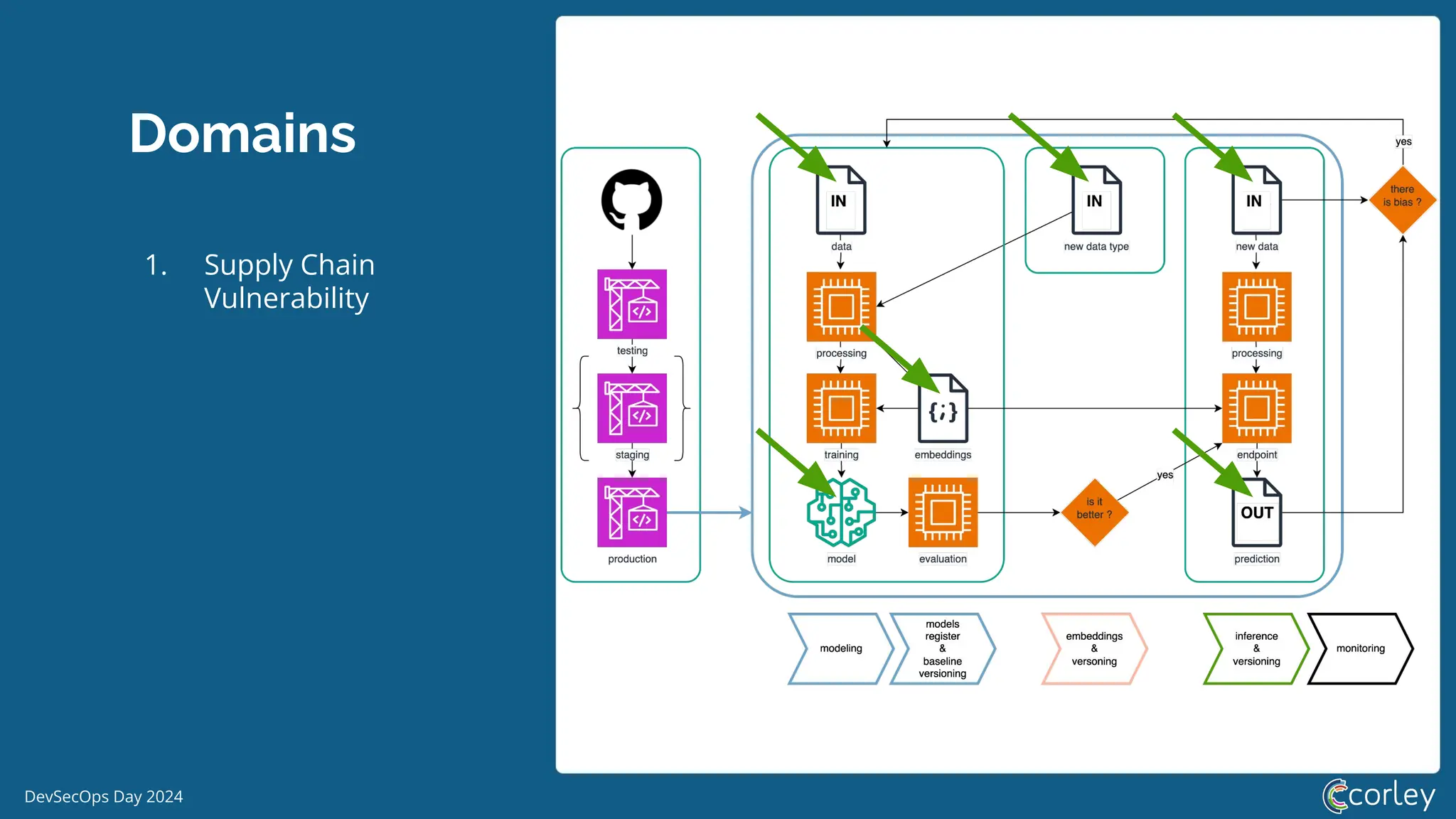
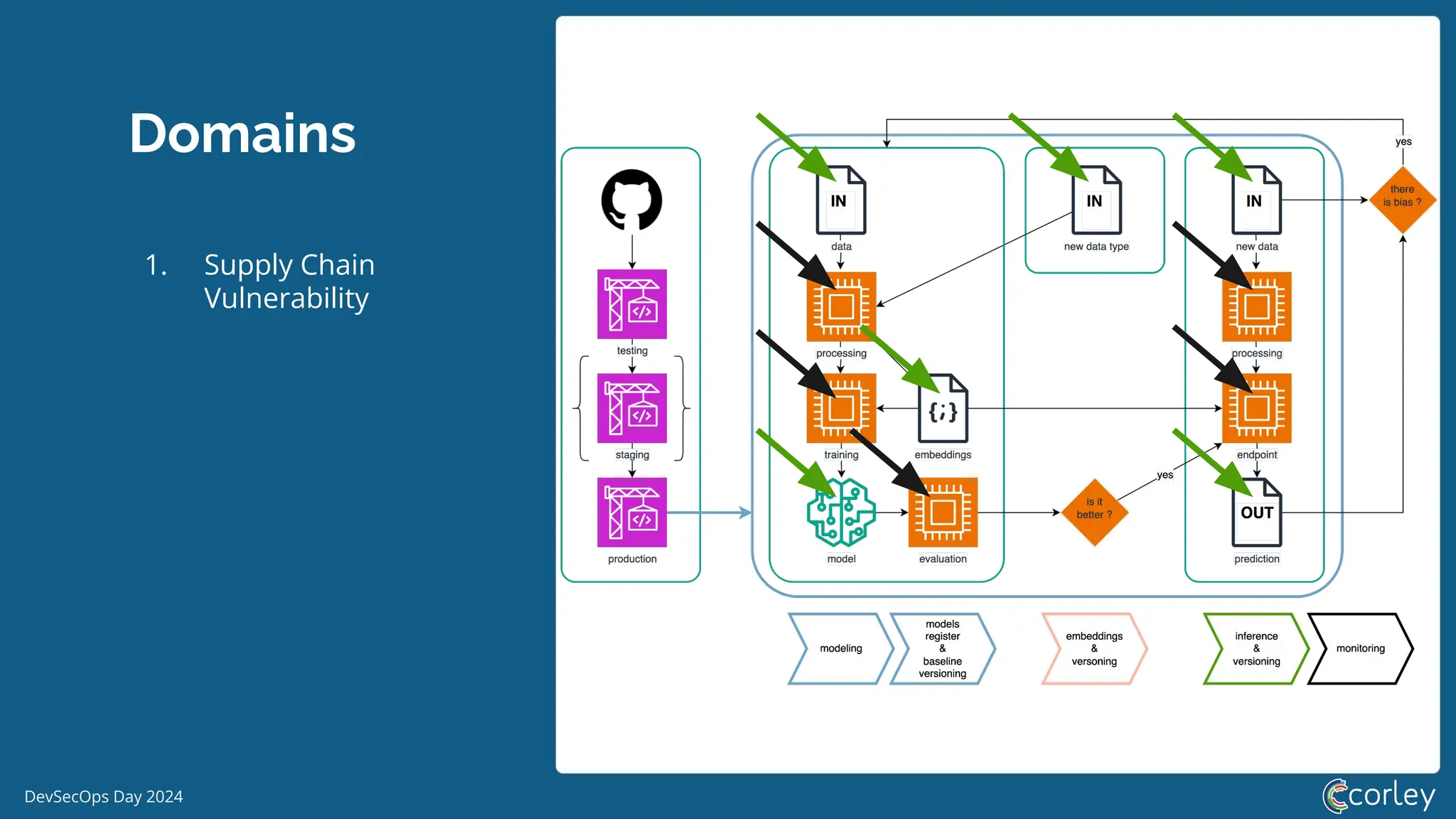
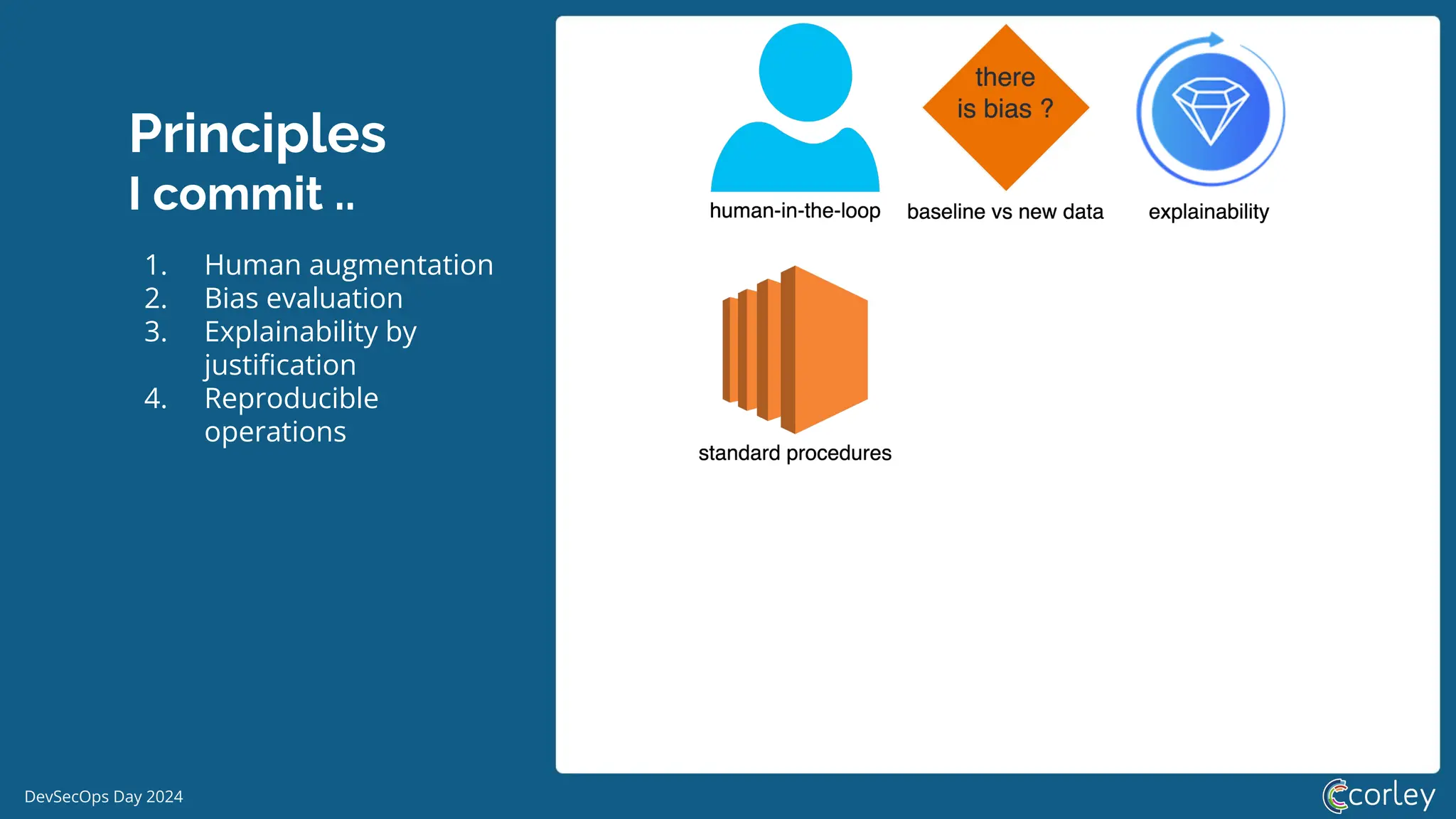
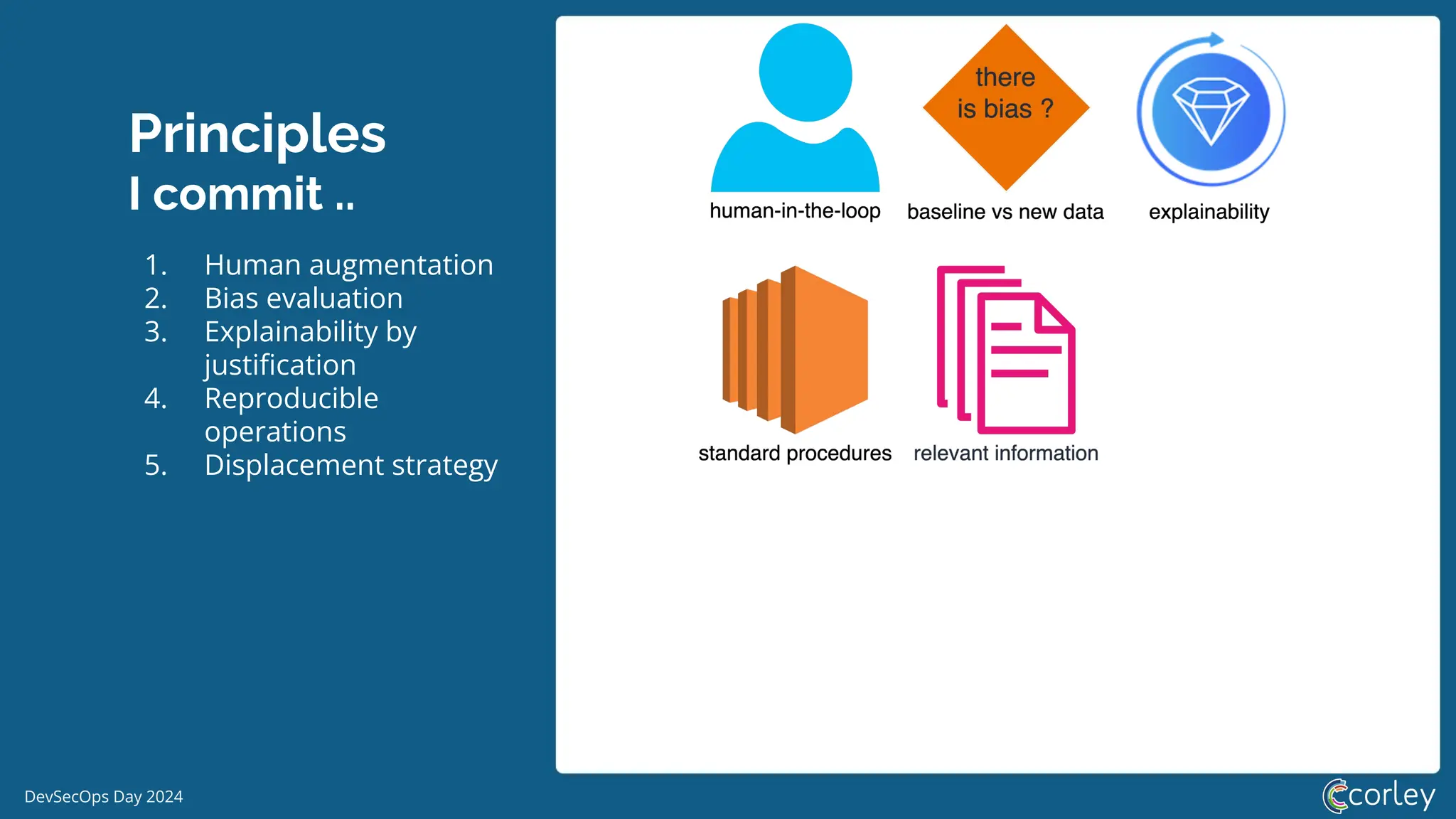
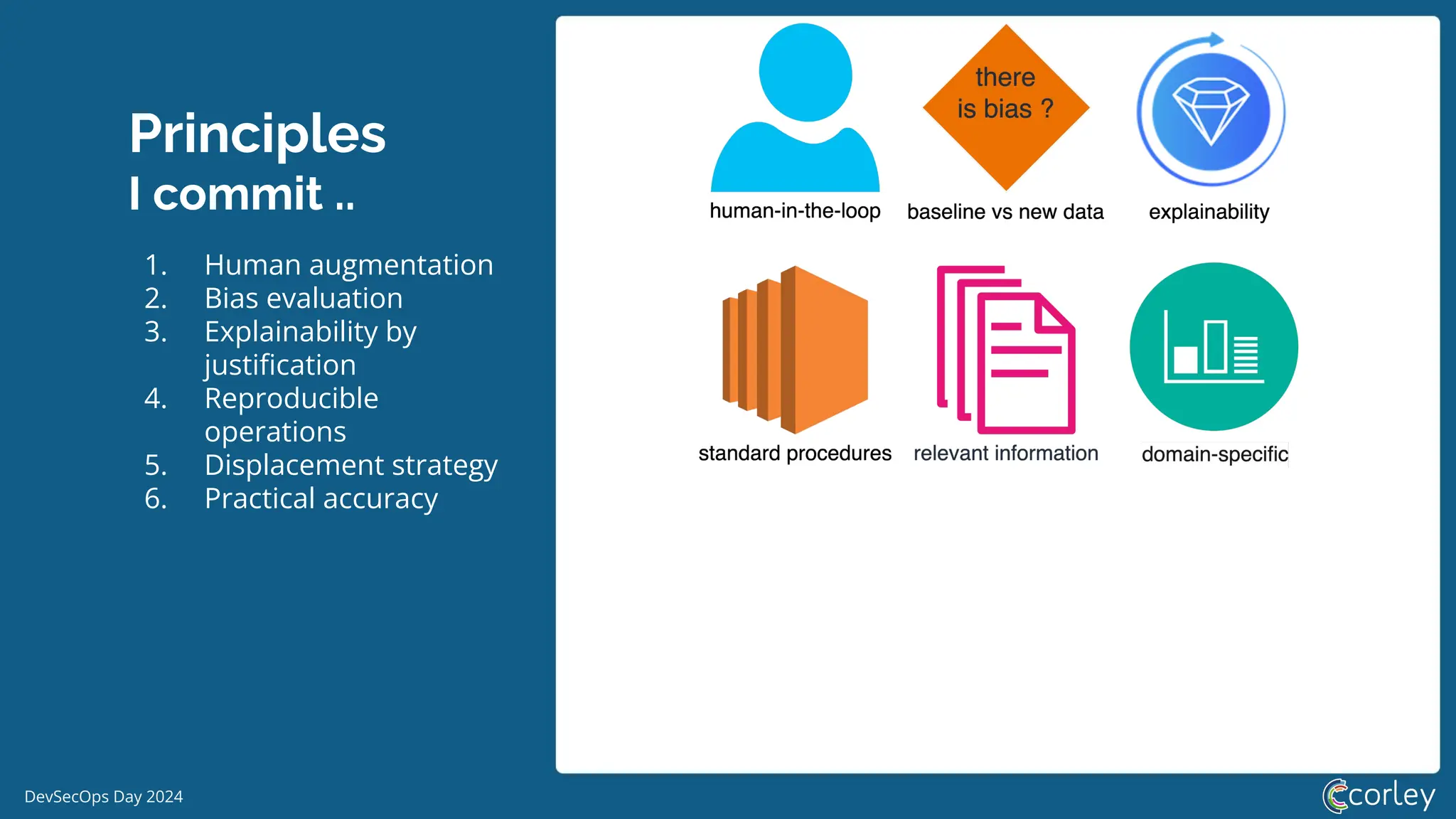
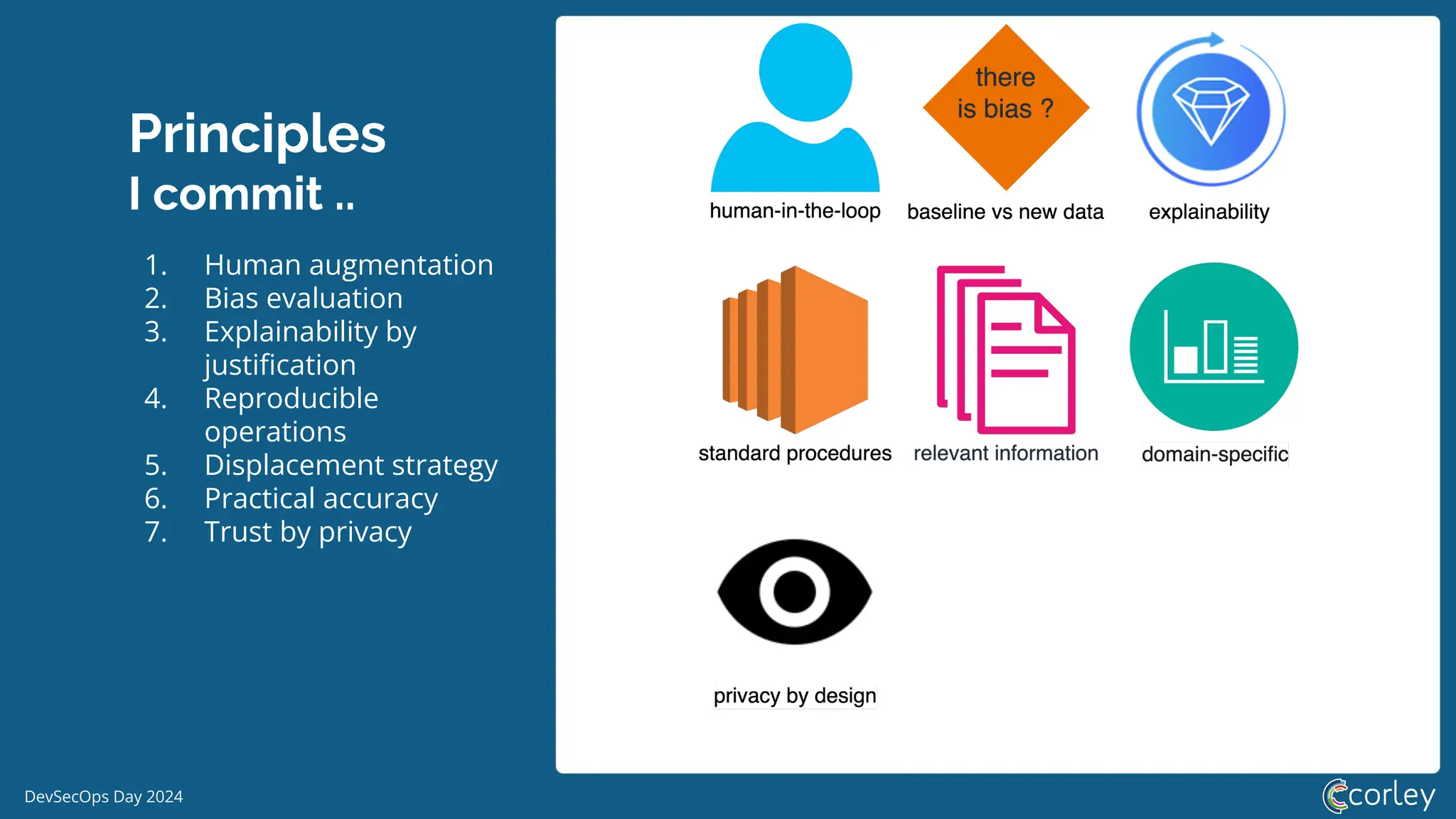
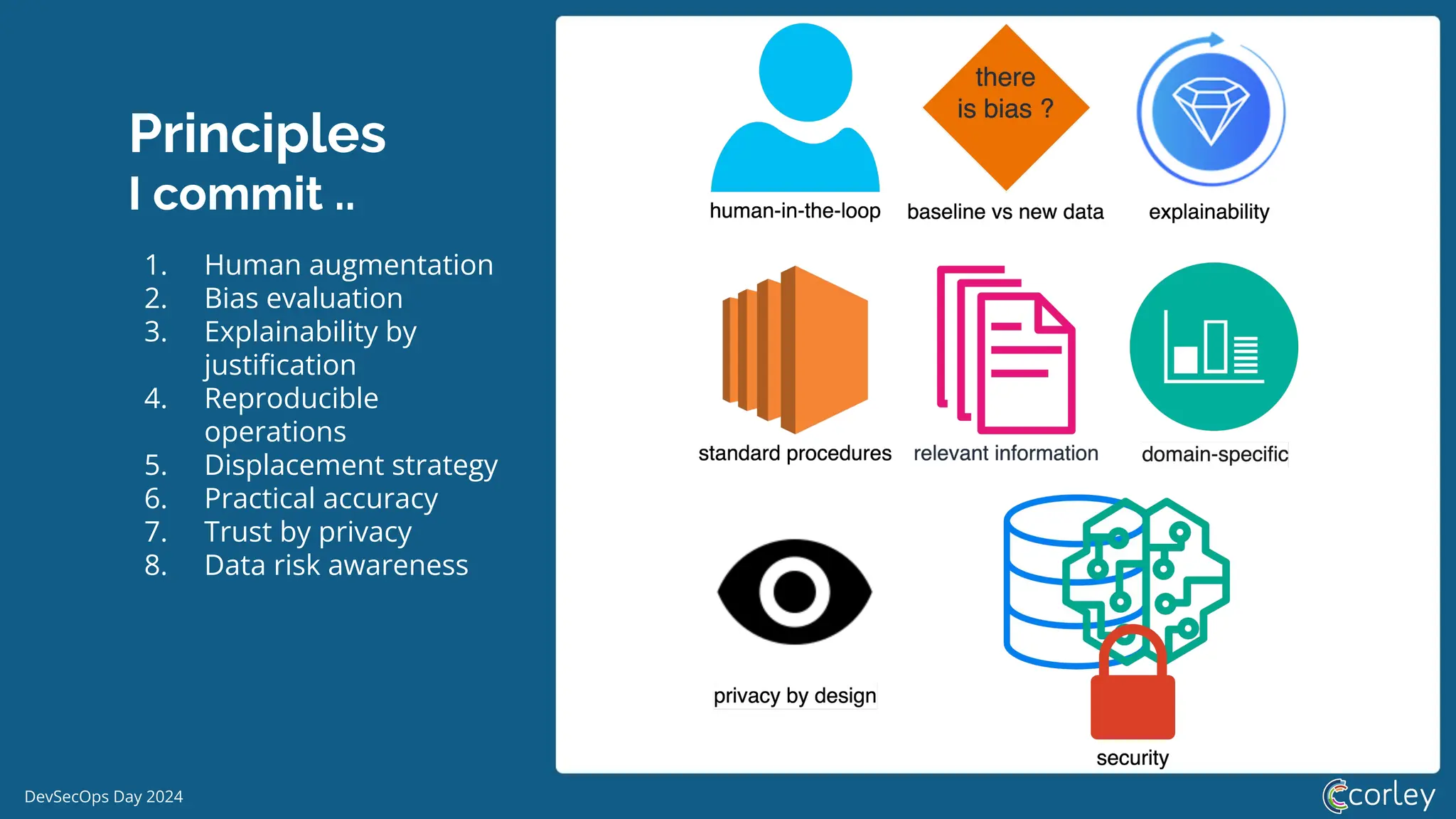
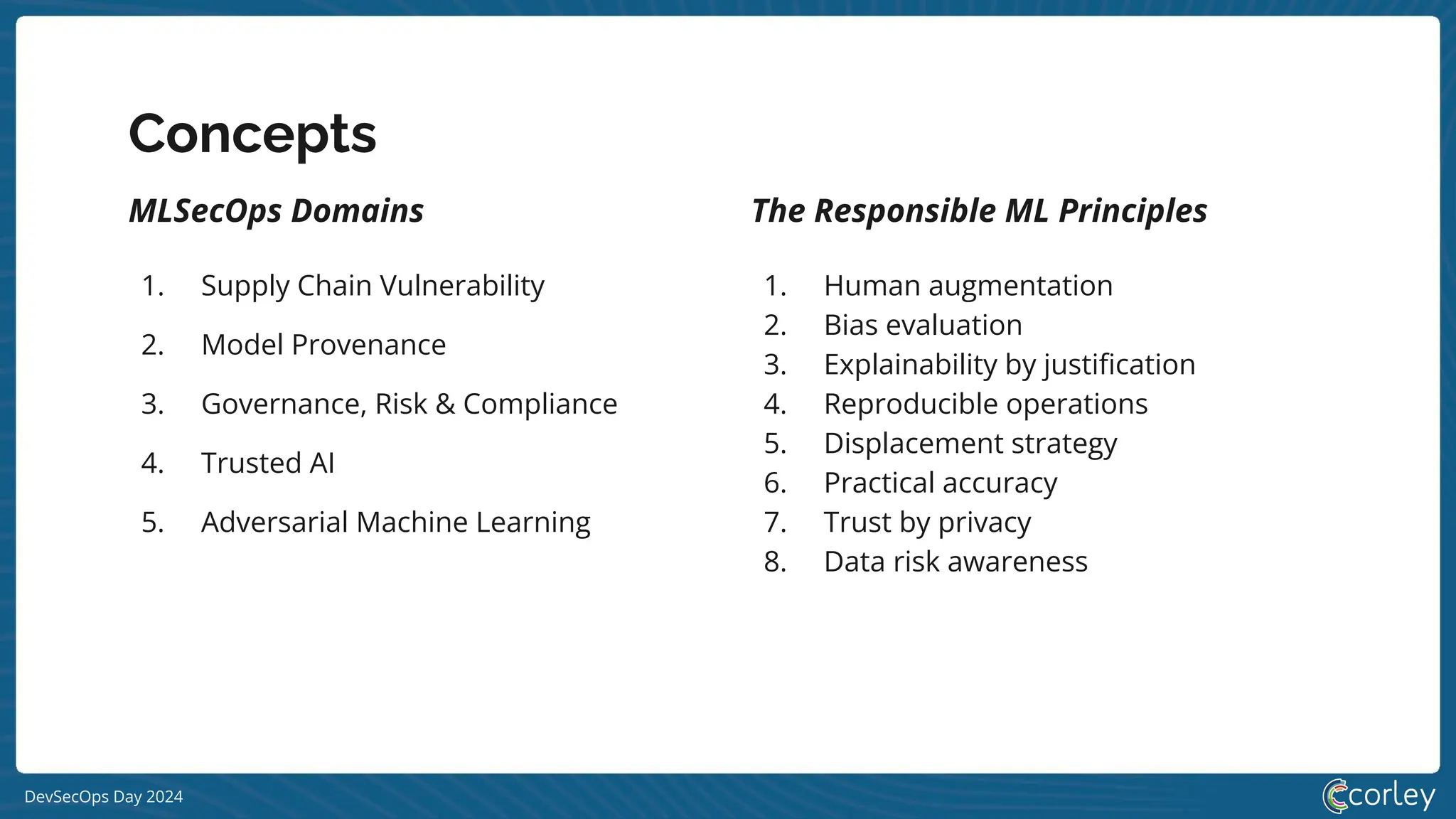
DevSecOps Day 2024 focuses on the integration of Machine Learning Security Operations (MLSecOps) with essential principles such as supply chain vulnerability, model provenance, and governance risk compliance. Key takeaways include the top ten vulnerabilities in ML and the responsible machine learning principles, emphasizing human augmentation, bias evaluation, and explainability. The event also explored strategies for maintaining security throughout the machine learning lifecycle, including monitoring and addressing adversarial risks.








![DevSecOps Day 2024
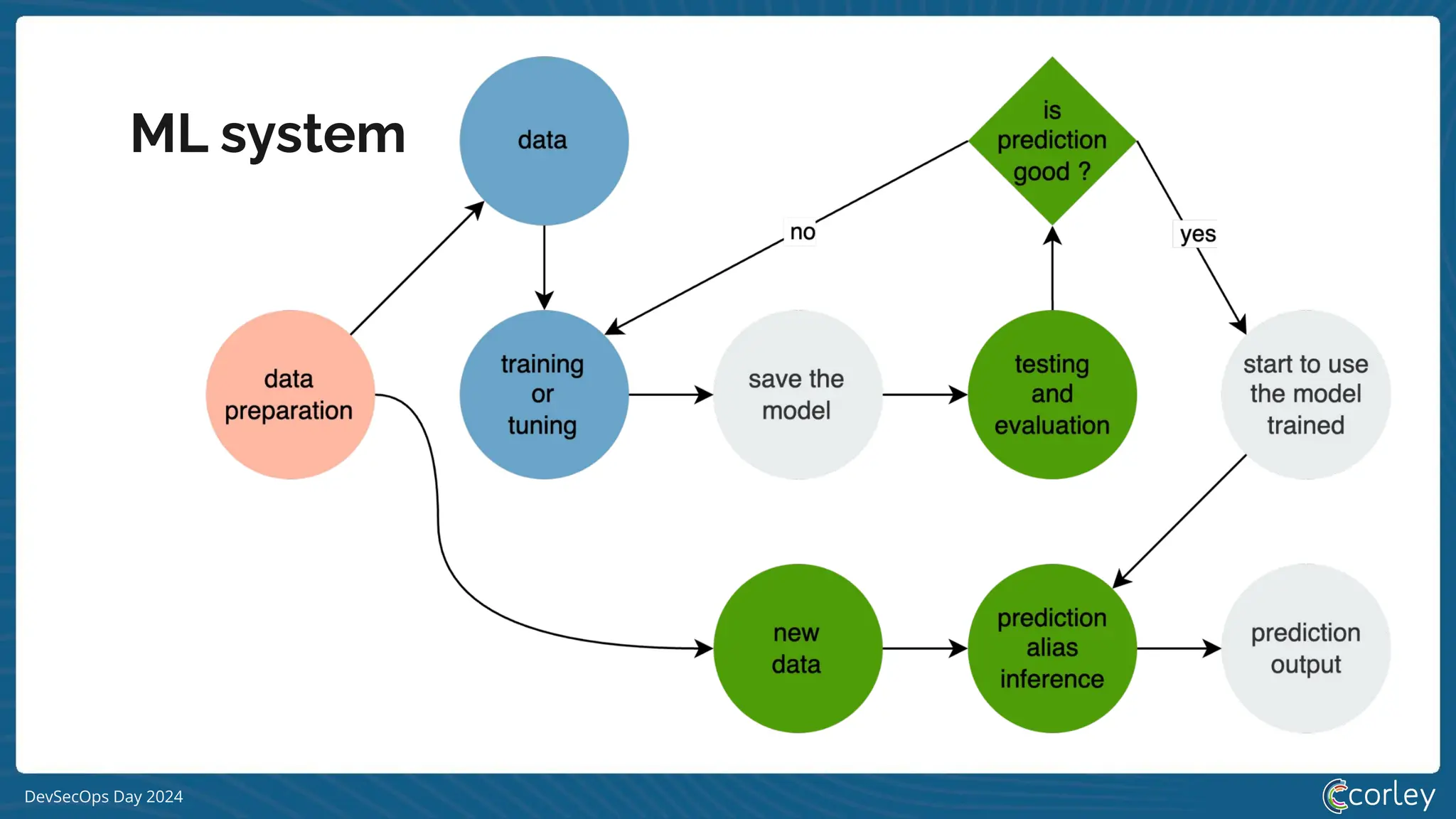
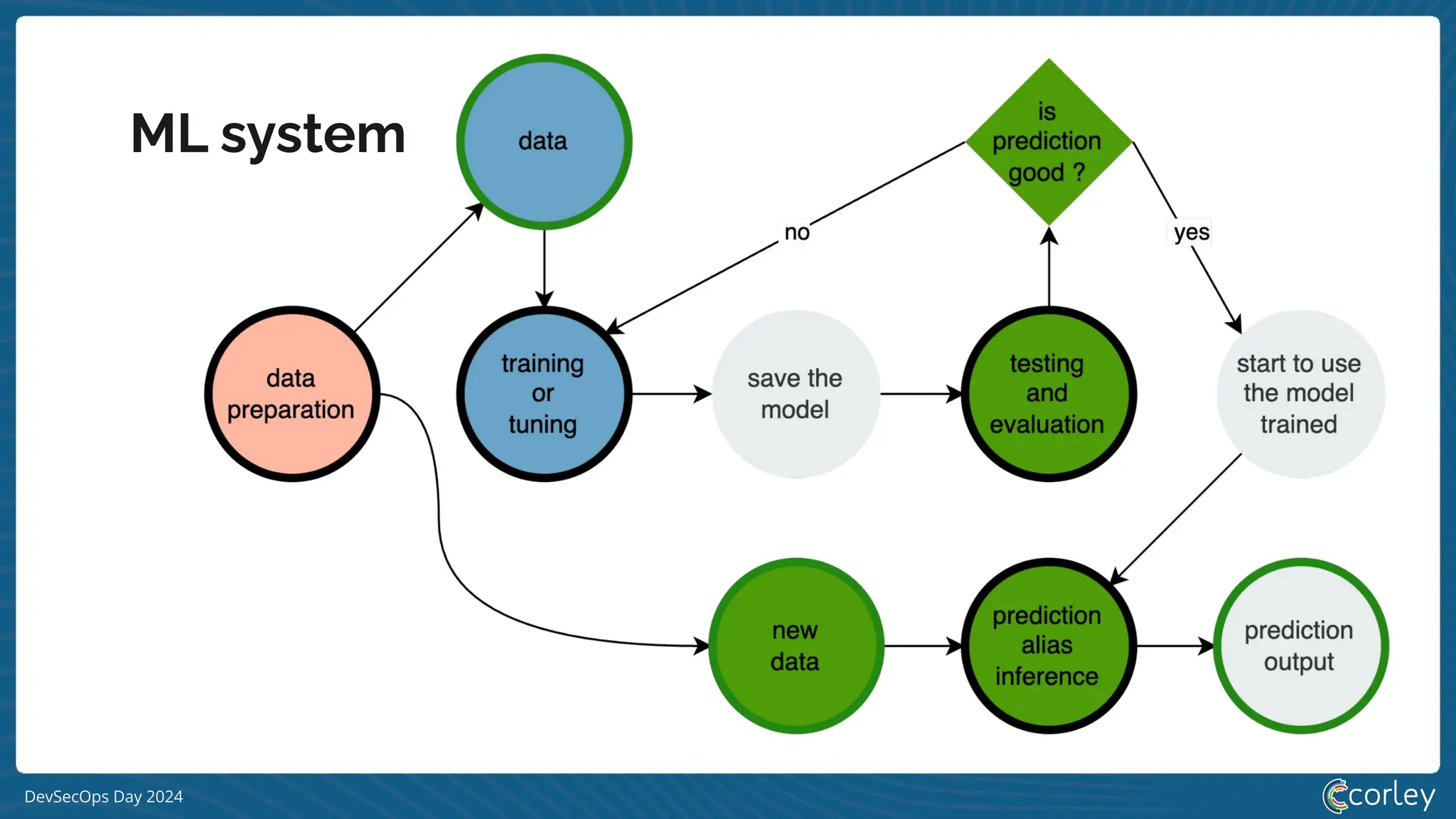
[S|L] LM system](https://image.slidesharecdn.com/devsecopsday-241101130933-6f4dca63/75/A-gentle-introduction-to-MLSecOps-2024-10-11-18-2048.jpg)
![DevSecOps Day 2024
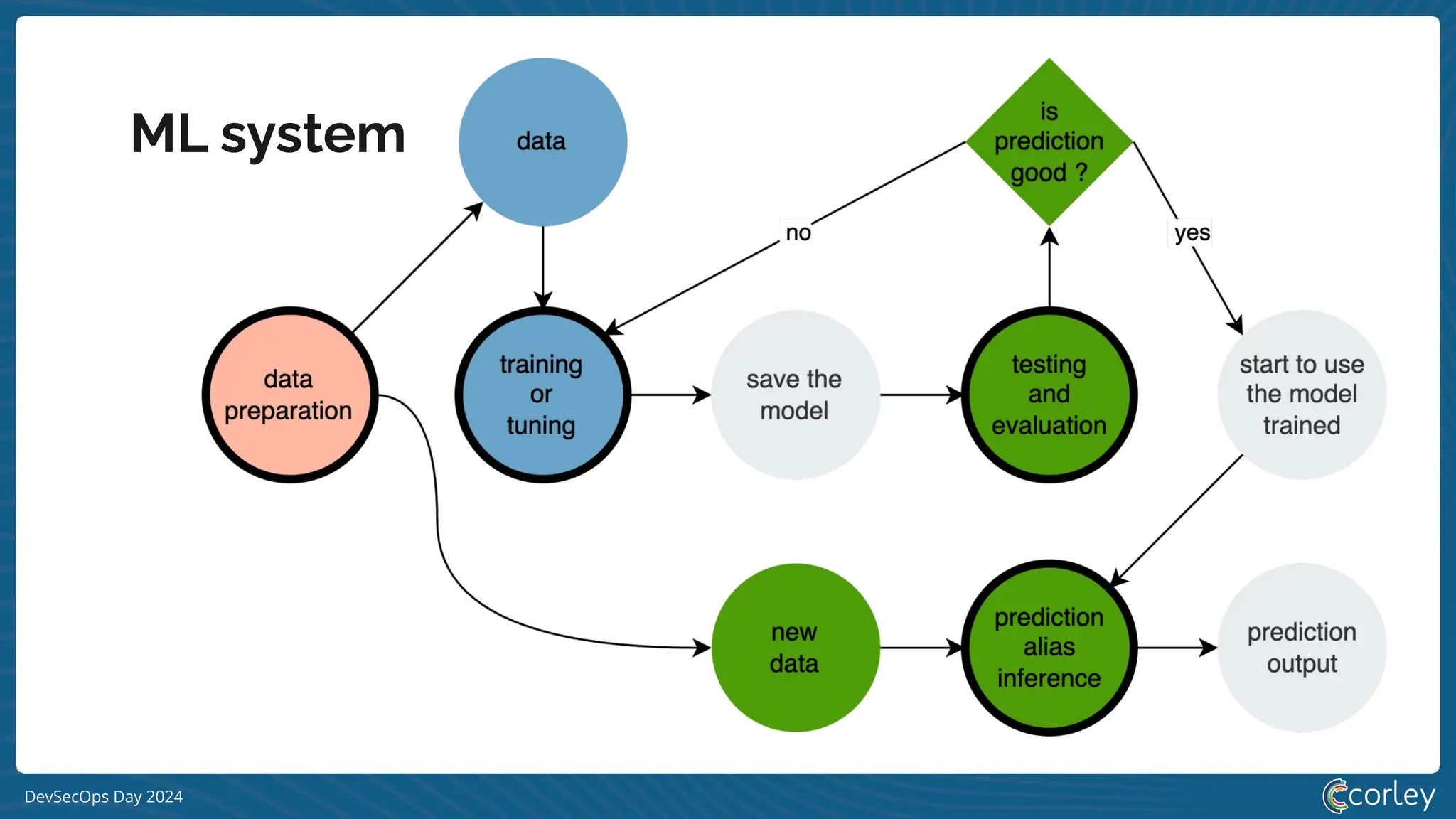
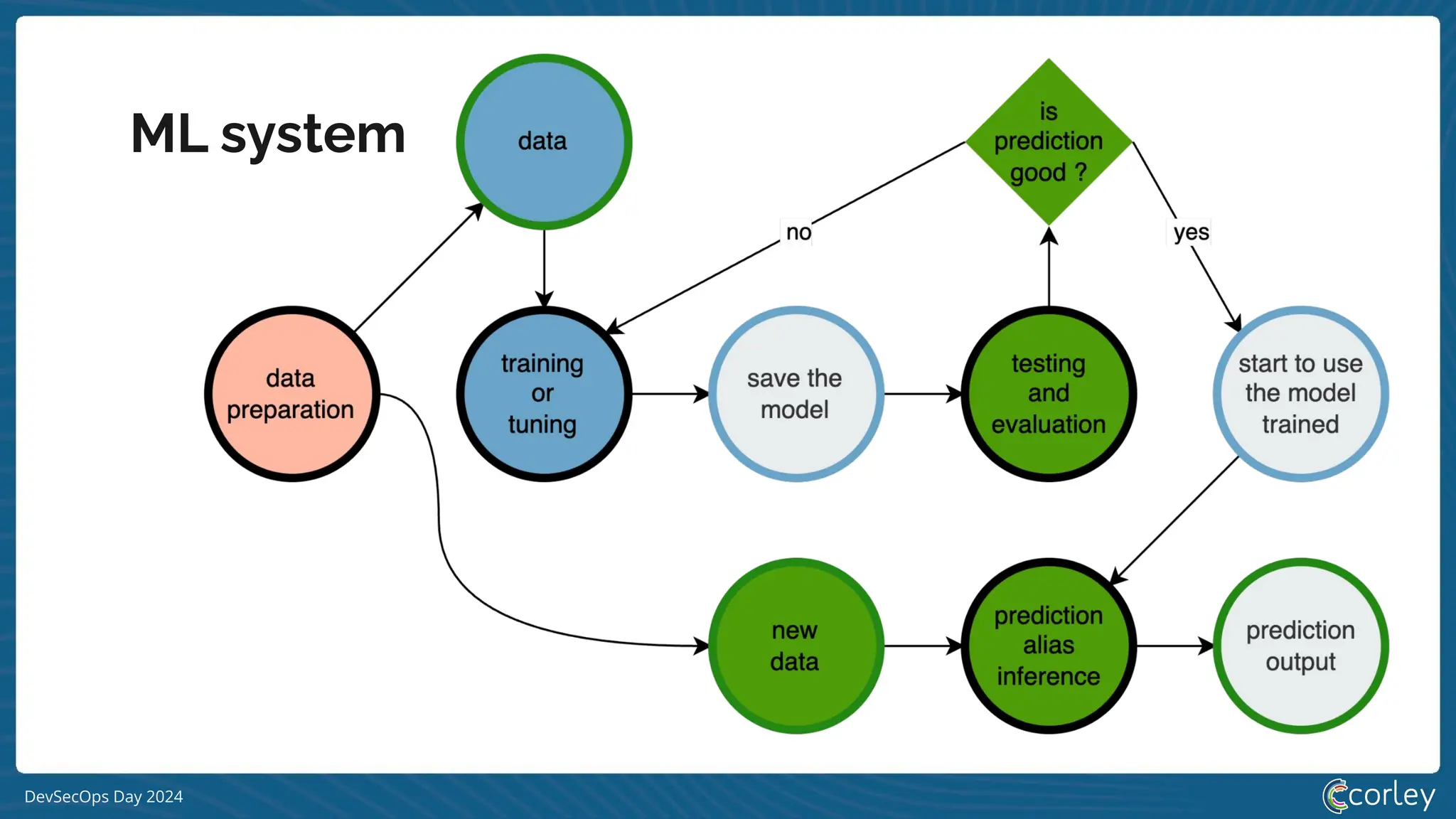
[S|L] LM system](https://image.slidesharecdn.com/devsecopsday-241101130933-6f4dca63/75/A-gentle-introduction-to-MLSecOps-2024-10-11-19-2048.jpg)
![DevSecOps Day 2024
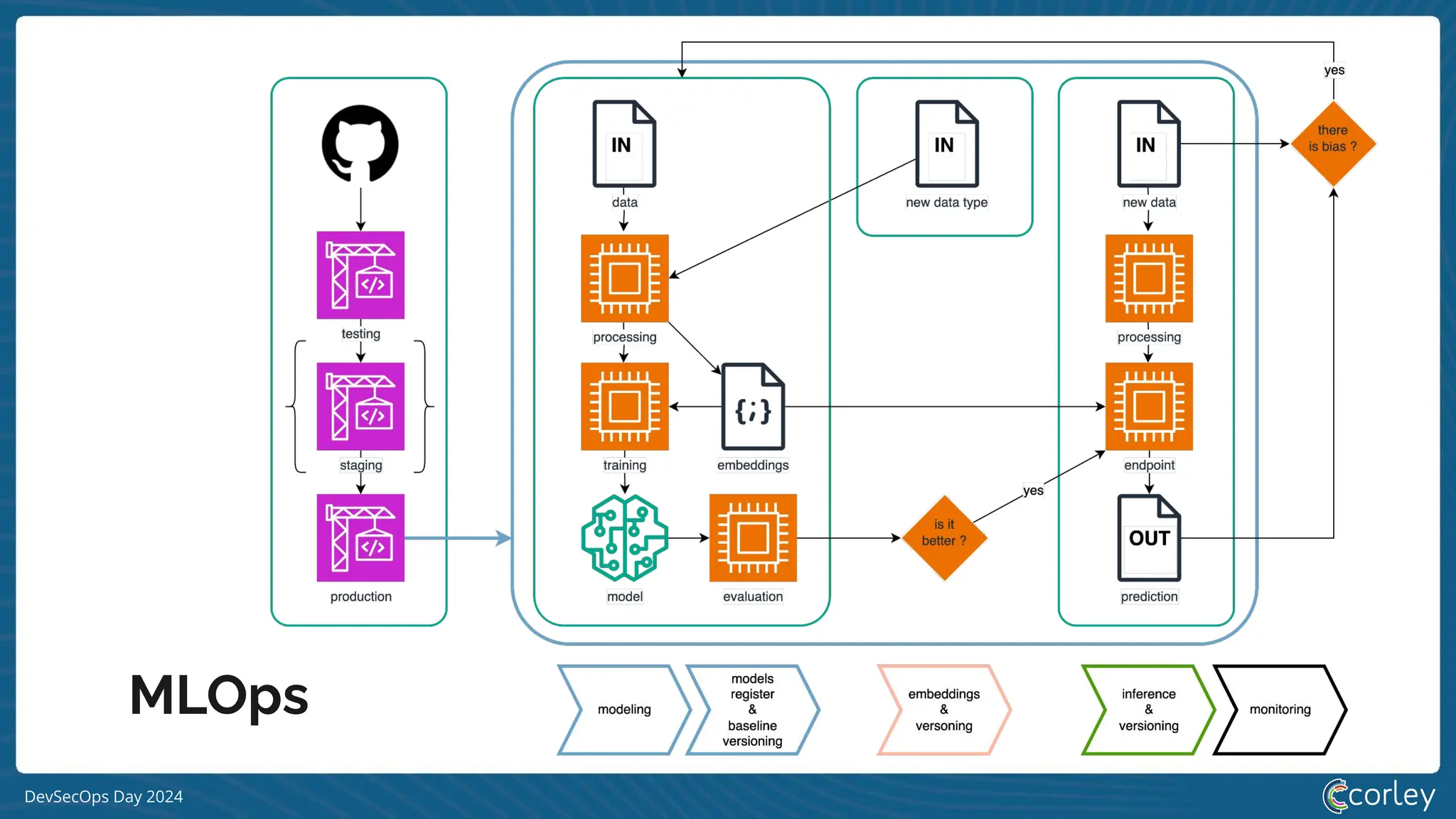
[S|L] LM system](https://image.slidesharecdn.com/devsecopsday-241101130933-6f4dca63/75/A-gentle-introduction-to-MLSecOps-2024-10-11-20-2048.jpg)
![DevSecOps Day 2024
[S|L] LMOps](https://image.slidesharecdn.com/devsecopsday-241101130933-6f4dca63/75/A-gentle-introduction-to-MLSecOps-2024-10-11-21-2048.jpg)
![DevSecOps Day 2024
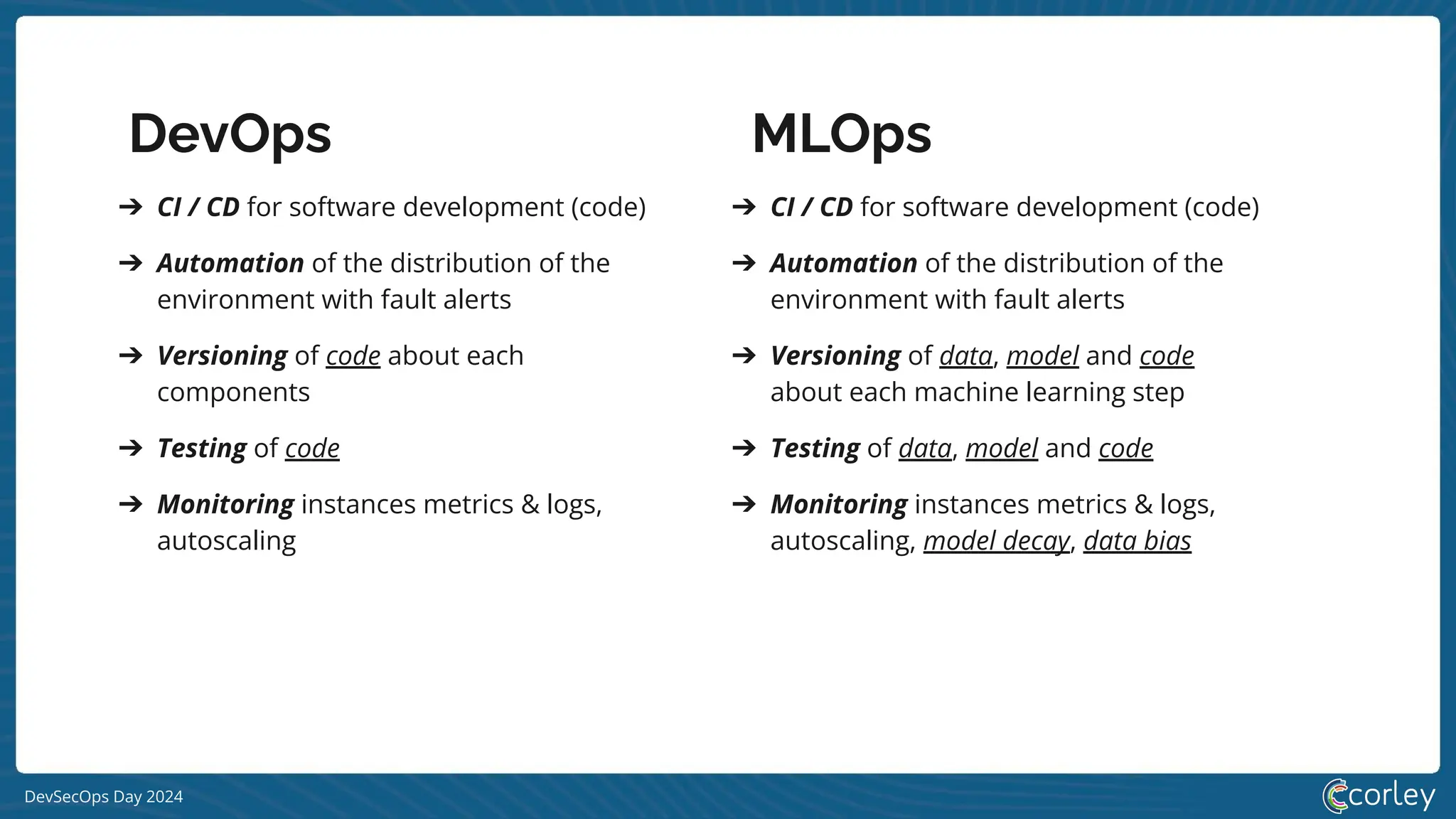
➔ CI / CD for software development (code)
➔ Automation of the distribution of the
environment with fault alerts
➔ Versioning of code about each
components
➔ Testing of code
➔ Monitoring instances metrics & logs,
autoscaling
➔ CI / CD for software development (code)
➔ Automation of the distribution of the
environment with fault alerts
➔ Versioning of data, model and code
about each machine learning step
➔ Testing of data, model and code
➔ Monitoring instances metrics & logs,
autoscaling, model decay, data bias
DevOps MLOps / [S|L] LMOps](https://image.slidesharecdn.com/devsecopsday-241101130933-6f4dca63/75/A-gentle-introduction-to-MLSecOps-2024-10-11-22-2048.jpg)