The document summarizes a presentation given at the 44th Hawai’i International Conference on System Sciences about enabling RFID technology in pharmaceutical supply chains. It describes a formal model for representing supply chain entities and roles, presents a quantitative analysis of network traffic for a sample US supply chain, and evaluates security considerations for different roles. The model accounts for relationships between business entities and handling units from individual items to transport vehicles. Network traffic is estimated at 234.92TB annually for a supply chain with 15 billion goods and 7 links. Security is addressed through authentication, on-tag mechanisms, and a proposed "service provider for anti-counterfeiting" role.









![Formal ModelRoles (Europe)Main Roles [1]A: Manufacturer: ~2.2kB: Center of Distribution: ~50kE: Licensed Dealer: ~140kD: Service Provider forAnti-CounterfeitingOther RolesC: Logistics ProviderF: End ConsumerHICSS11, Enabling RFID in Pharmaceutical Supply Chains, Schapranow, Jan 6, 201110](https://image.slidesharecdn.com/aformalmodelforenablingrfidinpharmaceuticalsupplychains-110107100539-phpapp02/85/A-Formal-Model-for-Enabling-RFID-in-Pharmaceutical-Supply-Chains-10-320.jpg)
![Formal ModelRoles (Europe)Main Roles [1]A: Manufacturer: ~2.2kB: Center of Distribution: ~50kE: Licensed Dealer: ~140kD: Service Provider forAnti-CounterfeitingOther RolesC: Logistics ProviderF: End ConsumerHICSS11, Enabling RFID in Pharmaceutical Supply Chains, Schapranow, Jan 6, 201111](https://image.slidesharecdn.com/aformalmodelforenablingrfidinpharmaceuticalsupplychains-110107100539-phpapp02/85/A-Formal-Model-for-Enabling-RFID-in-Pharmaceutical-Supply-Chains-11-320.jpg)
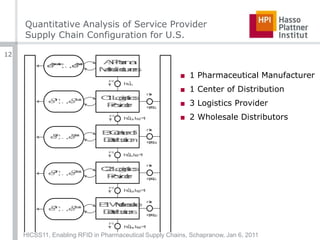

![Quantitative Analysis of Service ProviderNetwork TrafficNetwork traffic c, p pharmaceutical goods, supply chain length lFor p=15 billion and l=7: c=234.92TB / 32,475USD per year[2]Costs are adequate and can be handled by supply chain roles [3]HICSS11, Enabling RFID in Pharmaceutical Supply Chains, Schapranow, Jan 6, 201114](https://image.slidesharecdn.com/aformalmodelforenablingrfidinpharmaceuticalsupplychains-110107100539-phpapp02/85/A-Formal-Model-for-Enabling-RFID-in-Pharmaceutical-Supply-Chains-14-320.jpg)
![Quantitative Analysis of Service ProviderSecurity EvaluationManufacturer: prevent unrecognized EPC reading, e.g. by mutual authentication schemes [4]Center of distribution: on-tag security implementations, e.g. physically unclonable functions [5] or predefined passwords [6]Logistics provider: kill command [7], service providers for anti-counterfeitingWholesale Distributors: tracking and tracing via reader gatesEnd consumers: digital advice letter, service provider [8]HICSS11, Enabling RFID in Pharmaceutical Supply Chains, Schapranow, Jan 6, 201115](https://image.slidesharecdn.com/aformalmodelforenablingrfidinpharmaceuticalsupplychains-110107100539-phpapp02/85/A-Formal-Model-for-Enabling-RFID-in-Pharmaceutical-Supply-Chains-15-320.jpg)

![References[1] J. Müller, C. Pöpke, M. Urbat, A. Zeier, and H. Plattner, “A Simulation of the Pharmaceutical Supply Chain to Provide Realistic Test Data,” in Proceedings of the International Conference on Advances in System Simulation, 2009[2] Assuming Amazon EC2 mean network traffic costs per GB approx. 0.135 USD[3] M.-P. Schapranow, M. Nagora, and A. Zeier, “CoMoSeR: Cost Model for Security-Enhanced RFID-Aided Supply Chains,” in Proceedings of the 18th International Conference on Software, Telecommunication and Computer Networks, 2010[4] M.-P. Schapranow, A. Zeier, and H. Plattner, “A Dynamic Mutual RFID Authentication Model Preventing Unauthorized Third Party Access,” in Proceedings of the 4th International Conference on Network and System Security, 2010.[5] P. Tuyls and L. Batina, “RFID-Tags for Anti-Counterfeiting,” in Proceedings of the RSA Conference, 2006, pp. 115–131.[6] M.-P. Schapranow, J. Müller, S. Enderlein, M. Helmich, and A. Zeier, “Low-Cost Mutual RFID Authentication Model Using Predefined Password Lists,” in Proceedings of the 16th International Conference on Industrial Engineering and Engineering Management, 2009.[7] A. Mitrokotsa, M. R. Rieback, and A. S. Tanenbaum, “Classifi- cation of RFID Attacks,” in Proceedings of the 2nd International Workshop on RFID Technology, 2008, pp. 73–86.[8] M.-P. Schapranow, J. Müller, A. Zeier, and H. Plattner, “RFID Event Data Processing – An Architecture for Storing and Searching,” in Proceedings of the 4th International Workshop on RFID Technology - Concepts, Applications, Challenges, 2010.HICSS11, Enabling RFID in Pharmaceutical Supply Chains, Schapranow, Jan 6, 201117](https://image.slidesharecdn.com/aformalmodelforenablingrfidinpharmaceuticalsupplychains-110107100539-phpapp02/85/A-Formal-Model-for-Enabling-RFID-in-Pharmaceutical-Supply-Chains-17-320.jpg)
