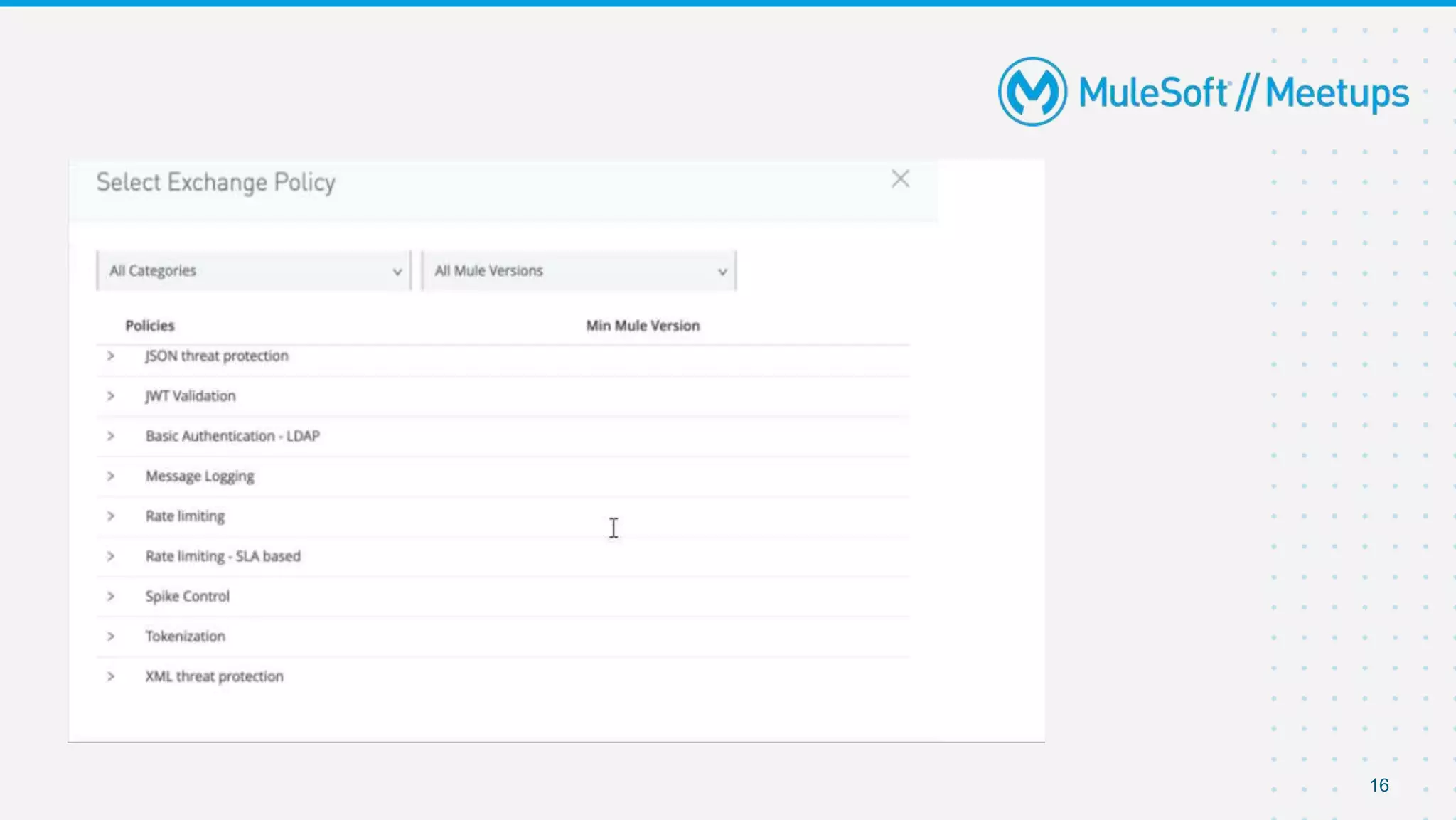
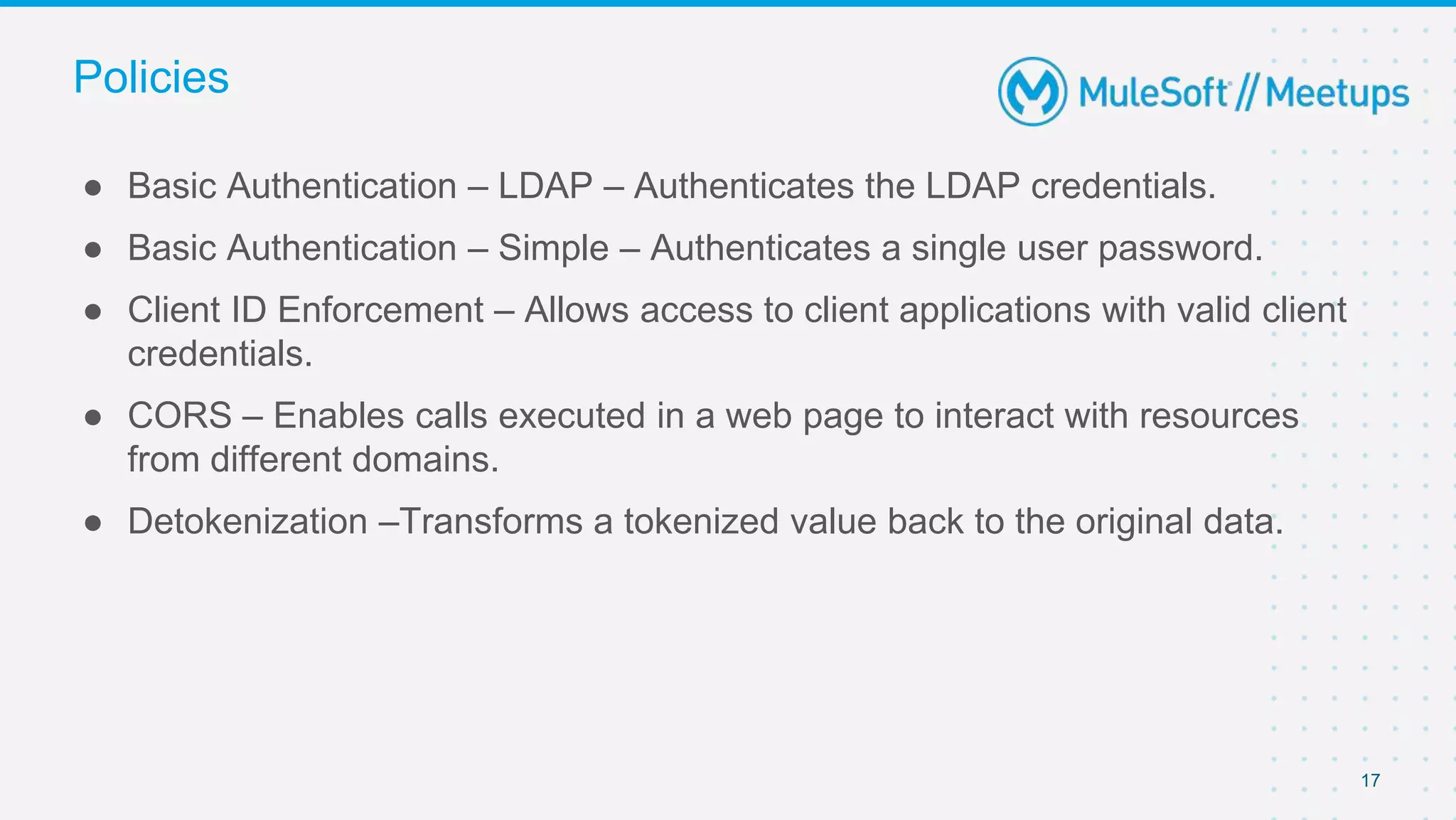
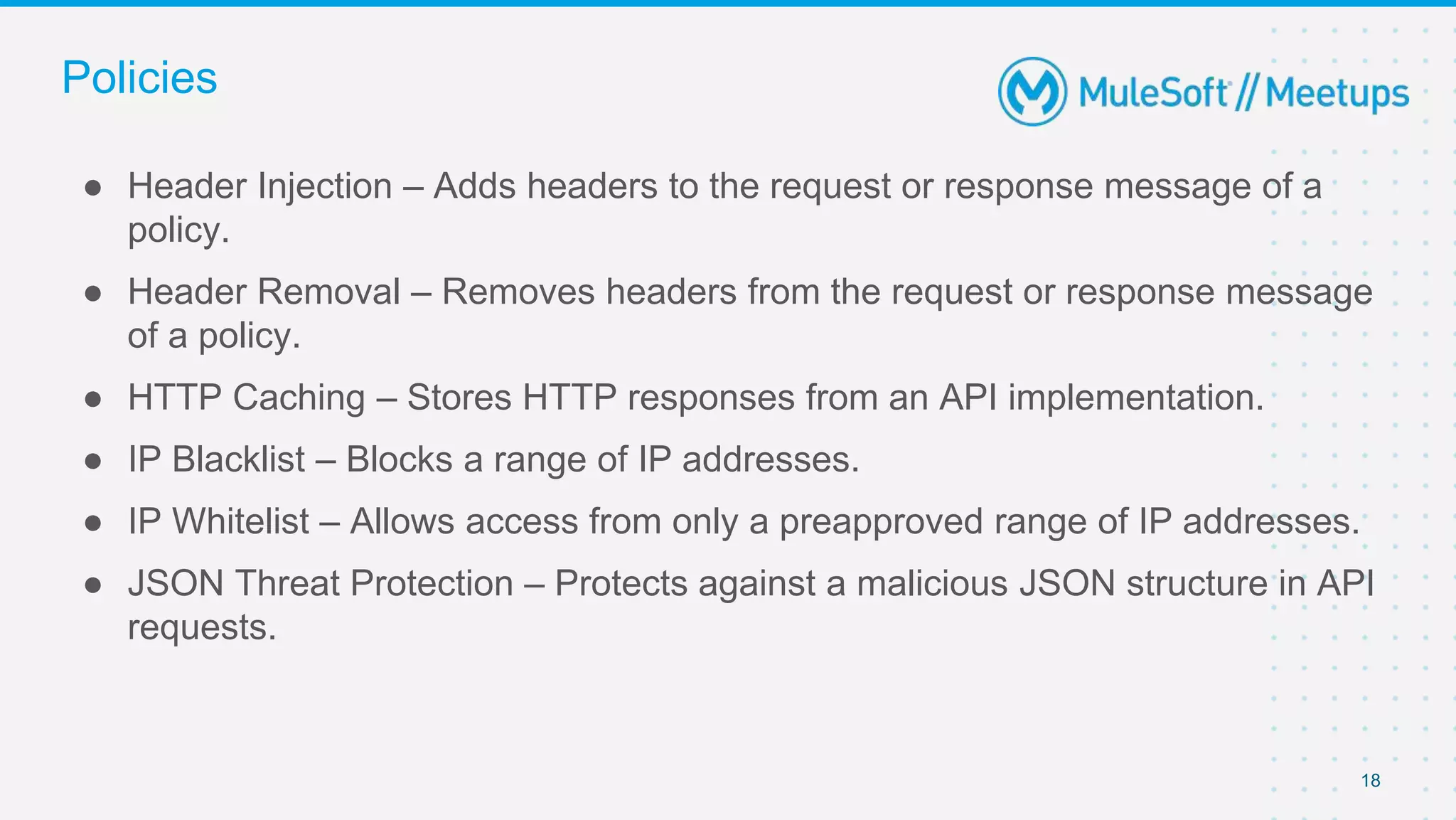
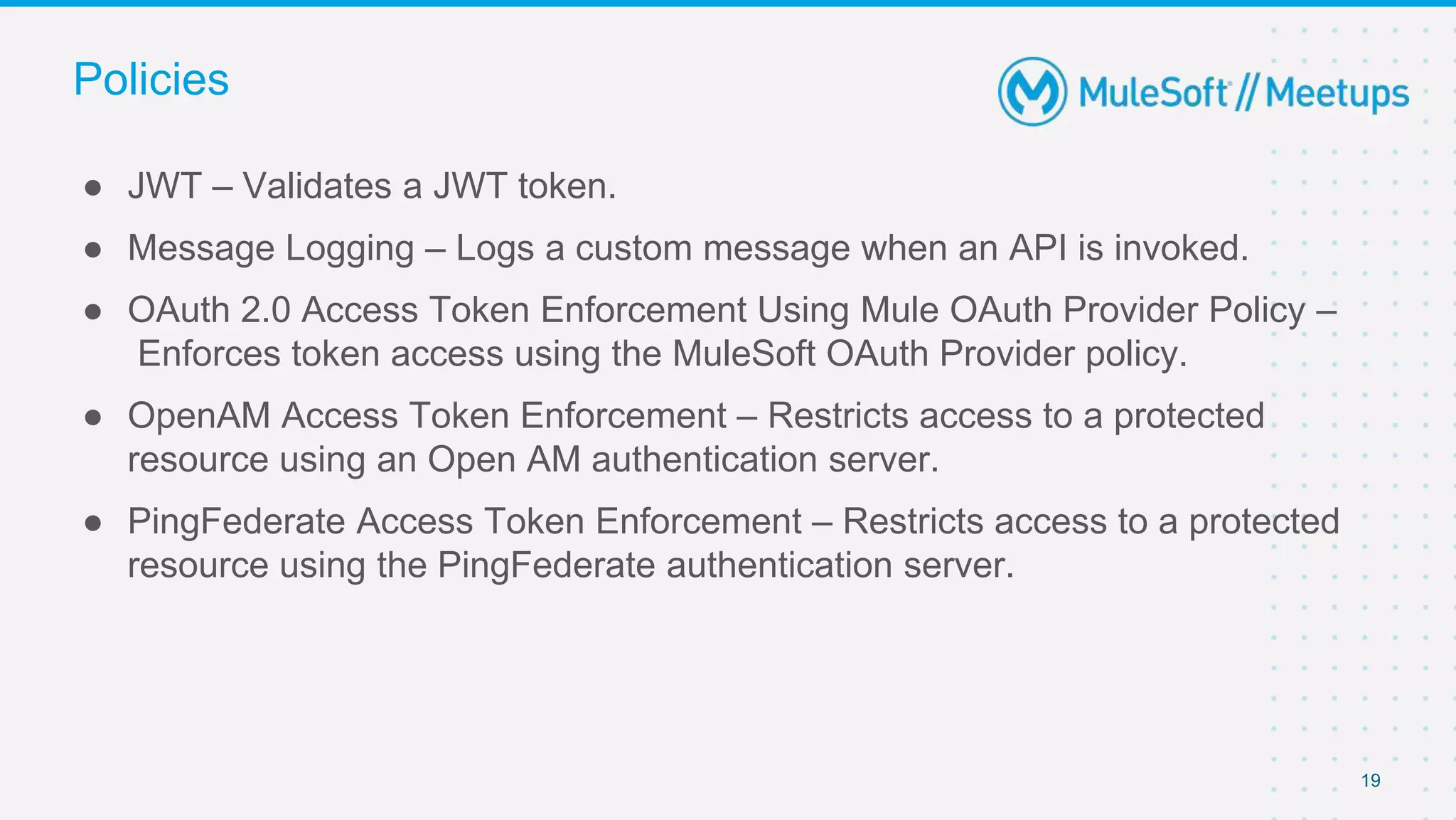
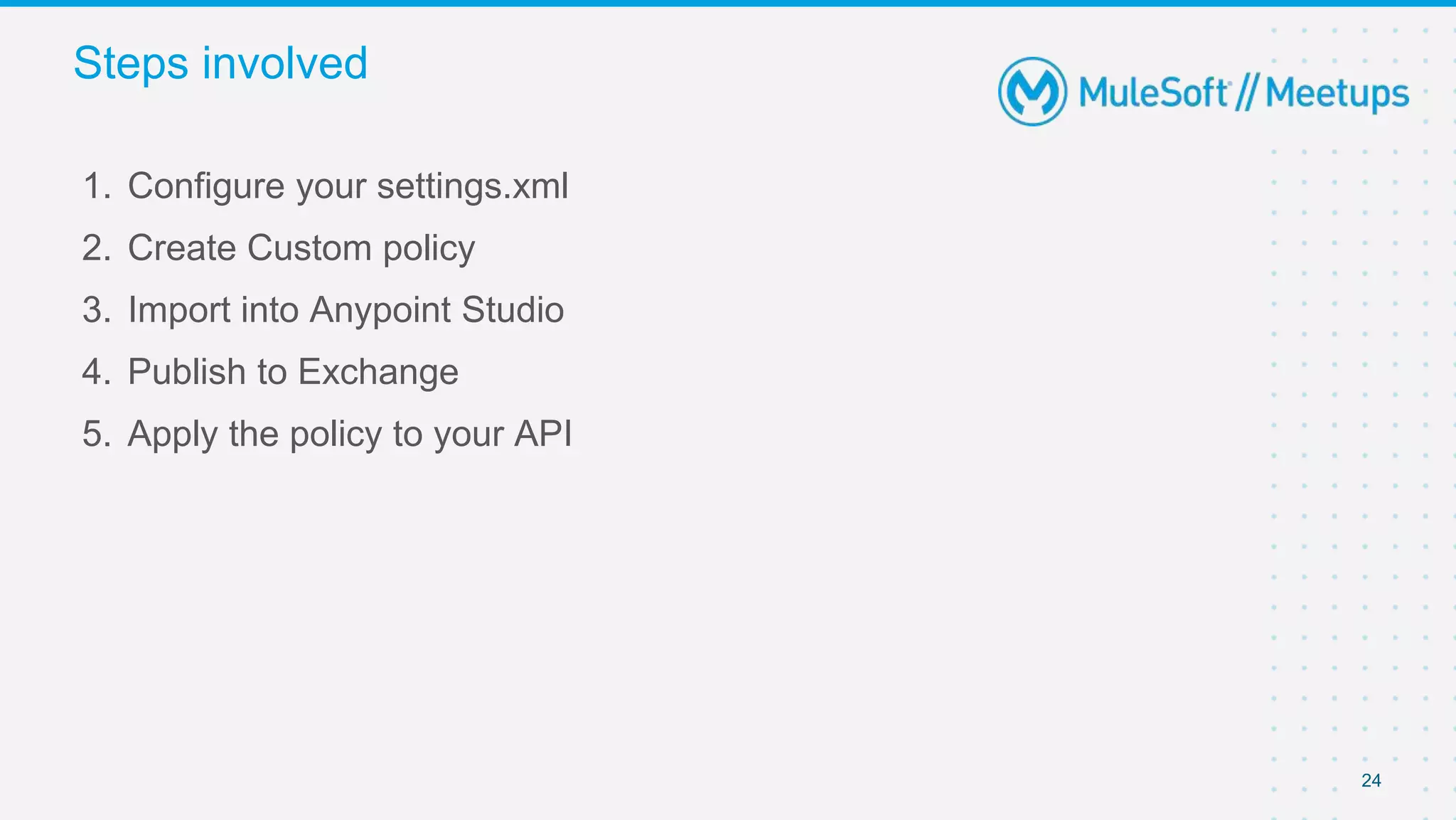
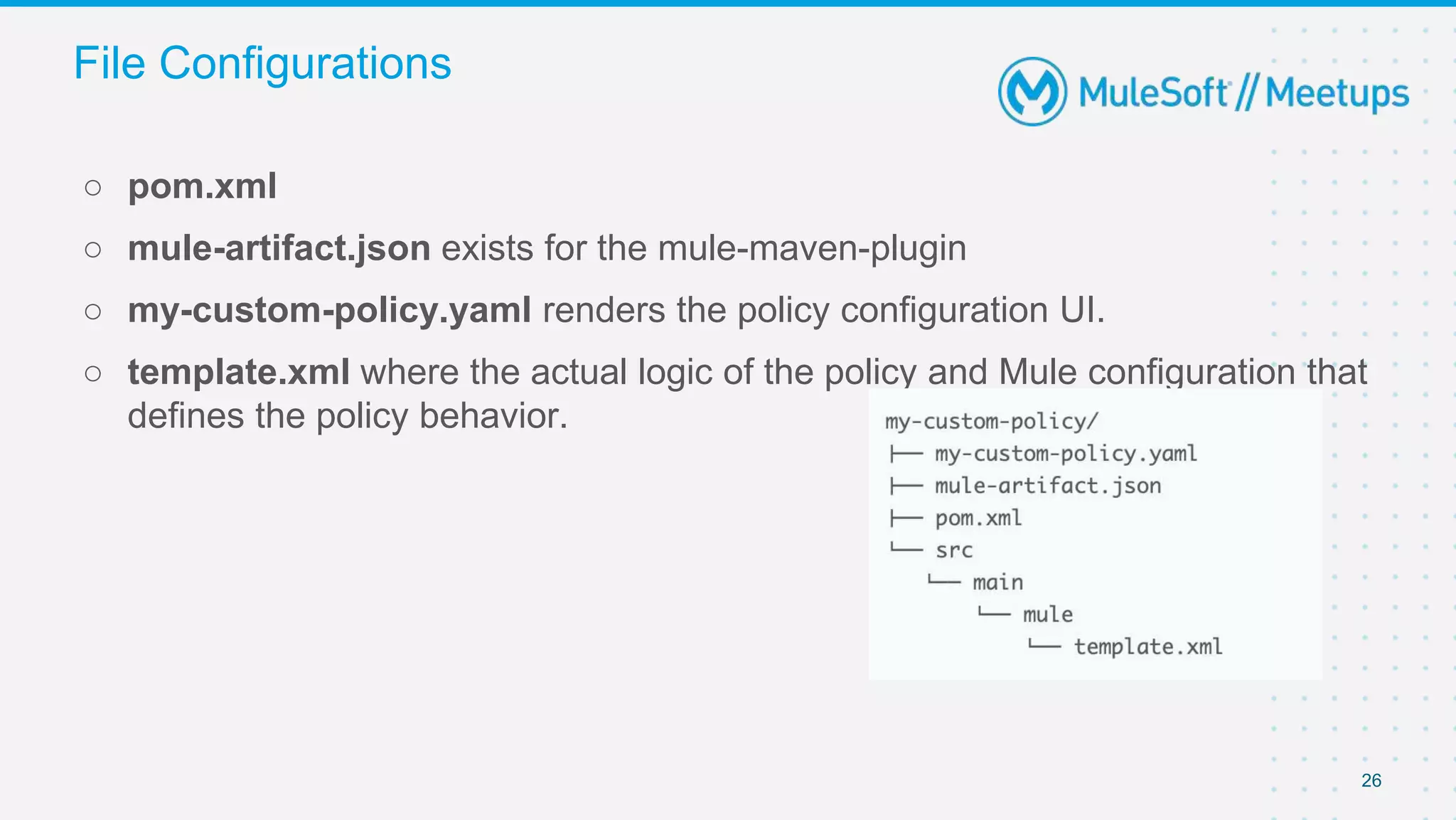
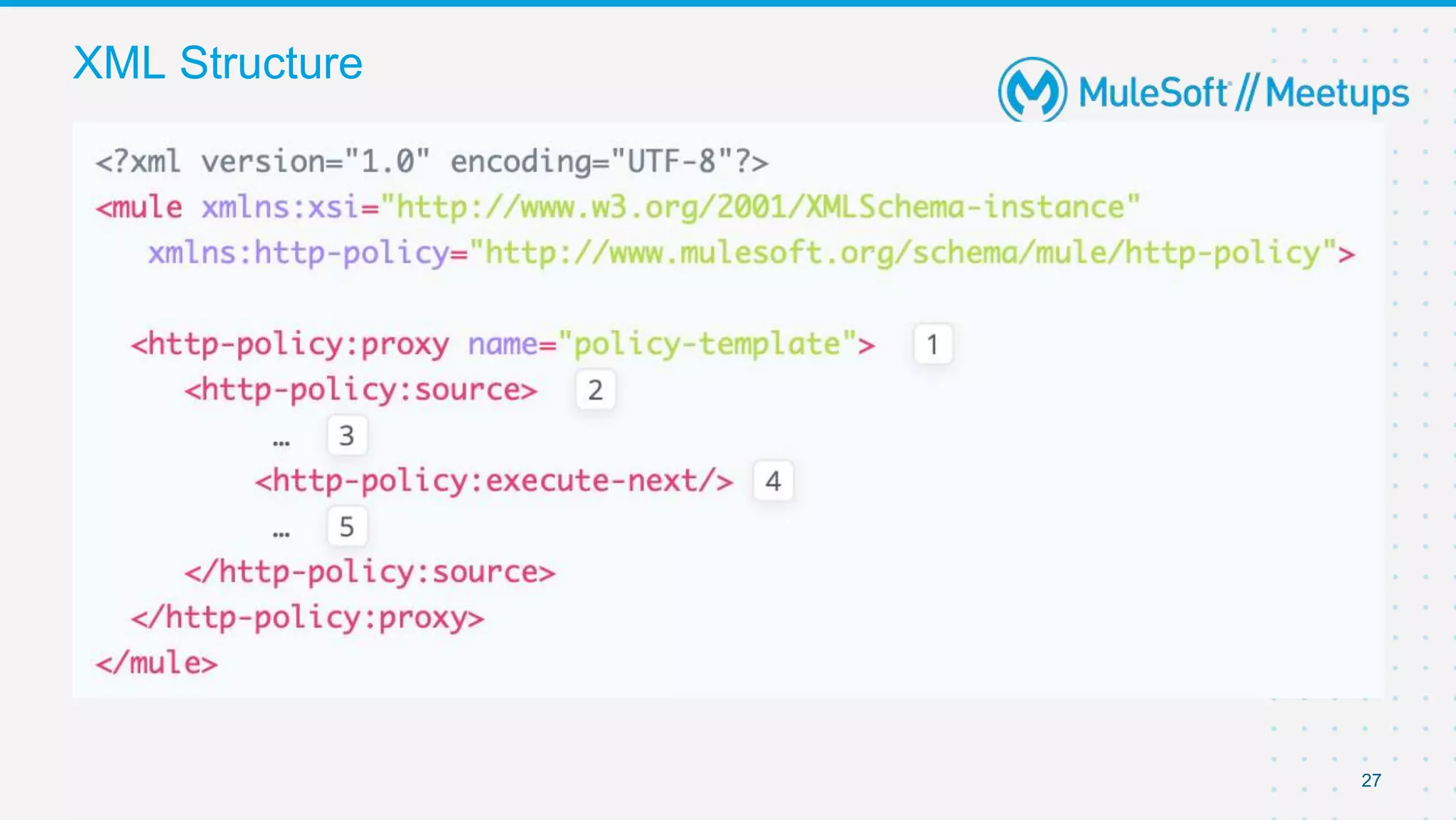
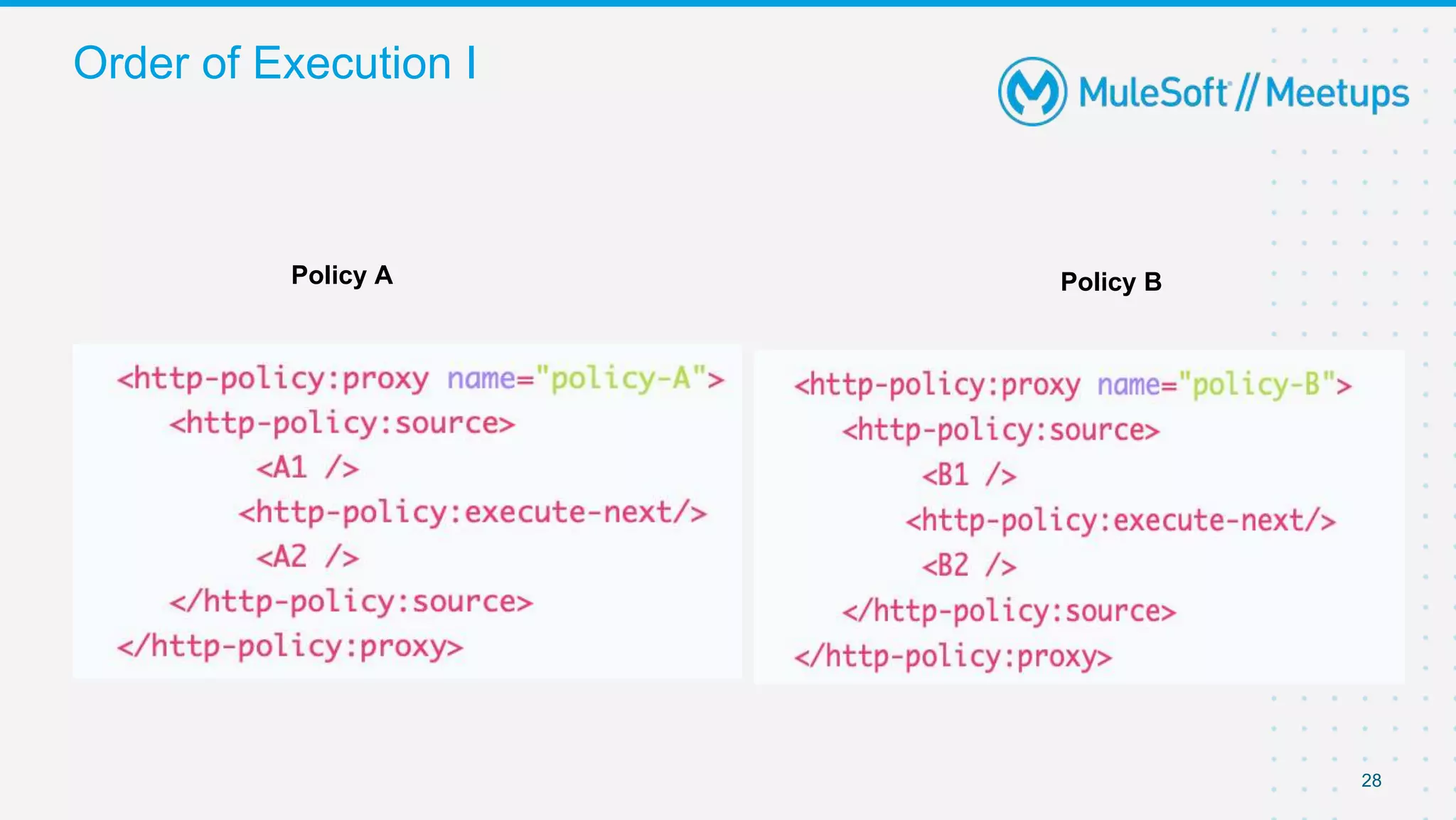
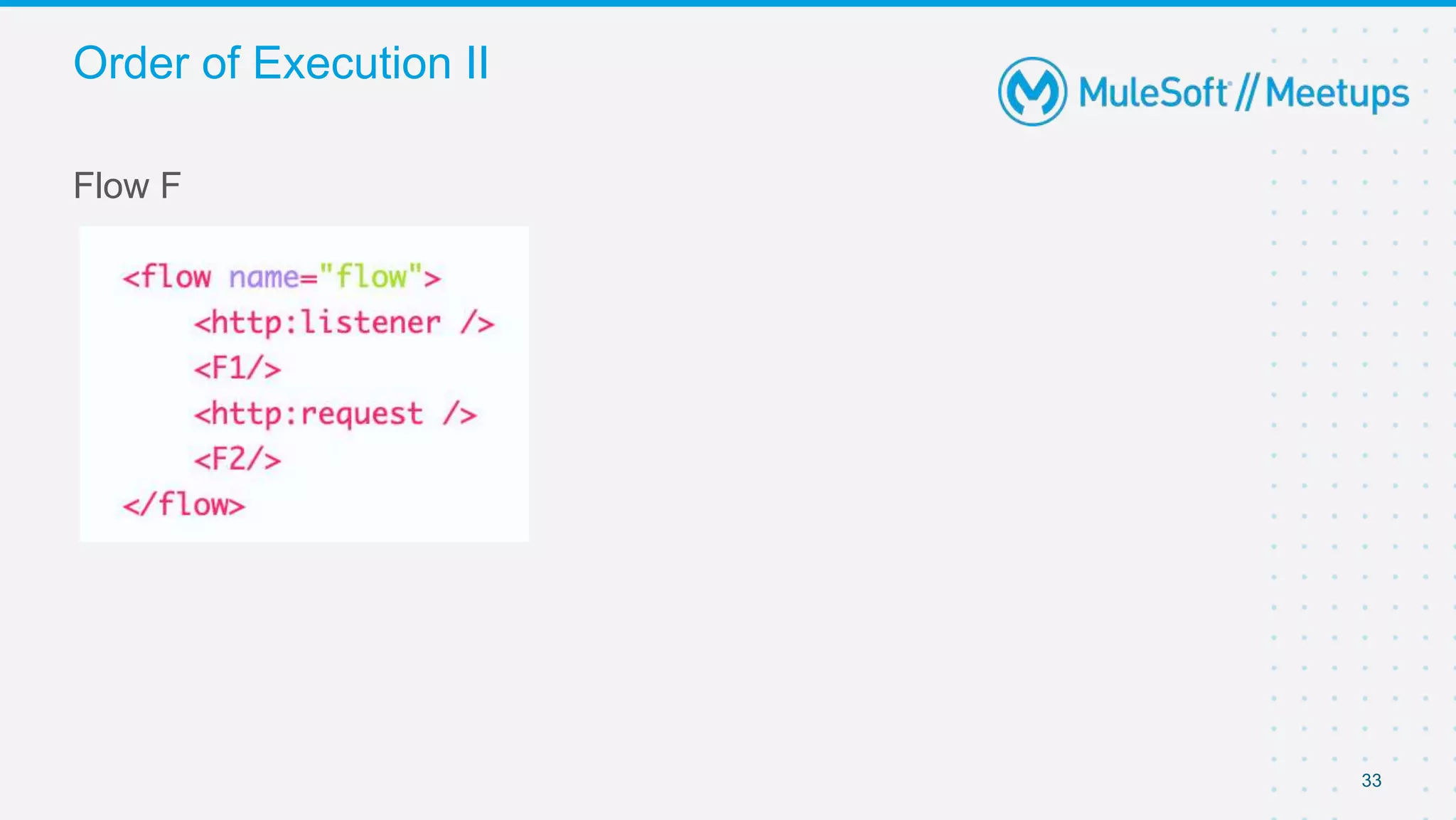
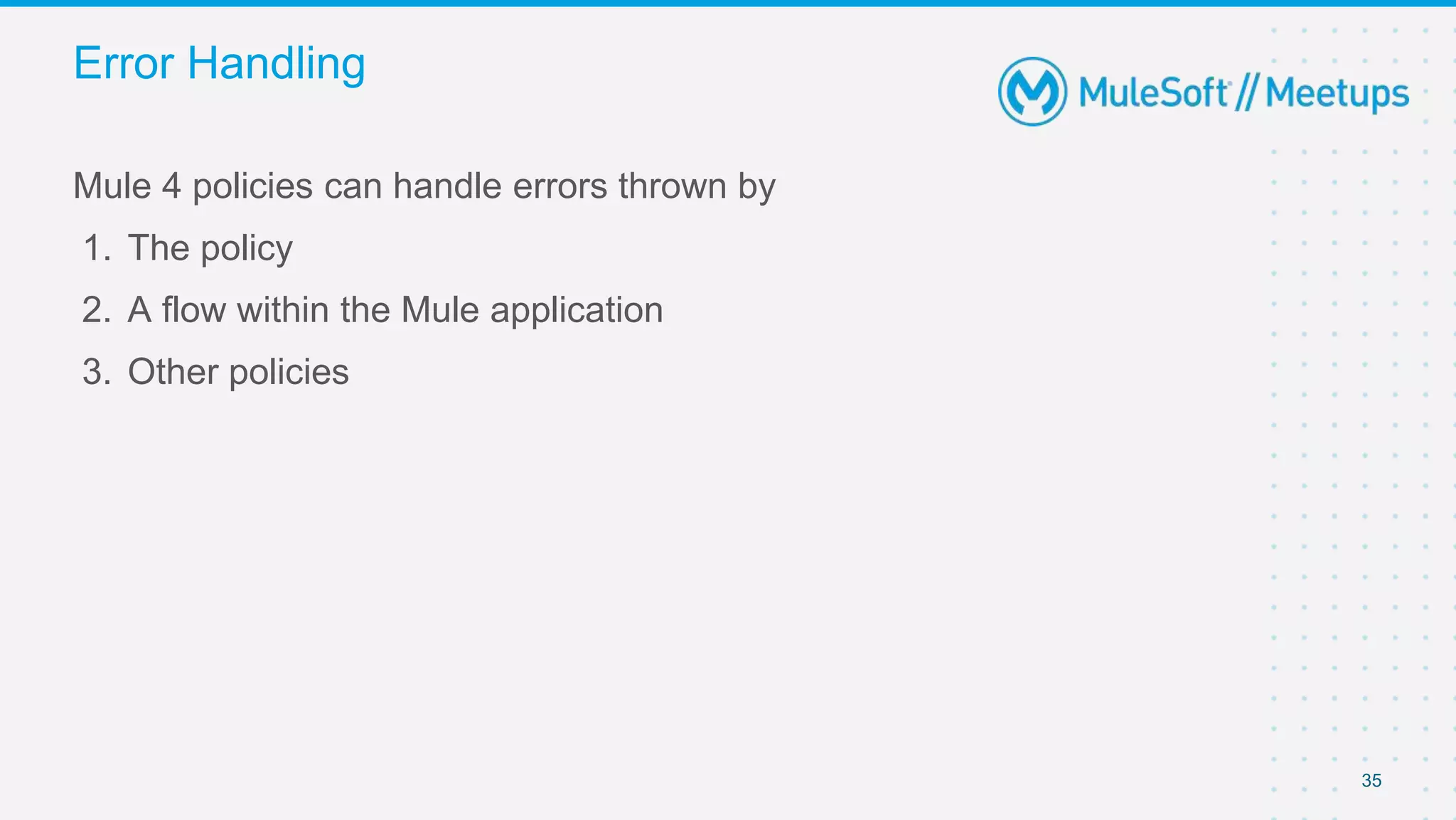
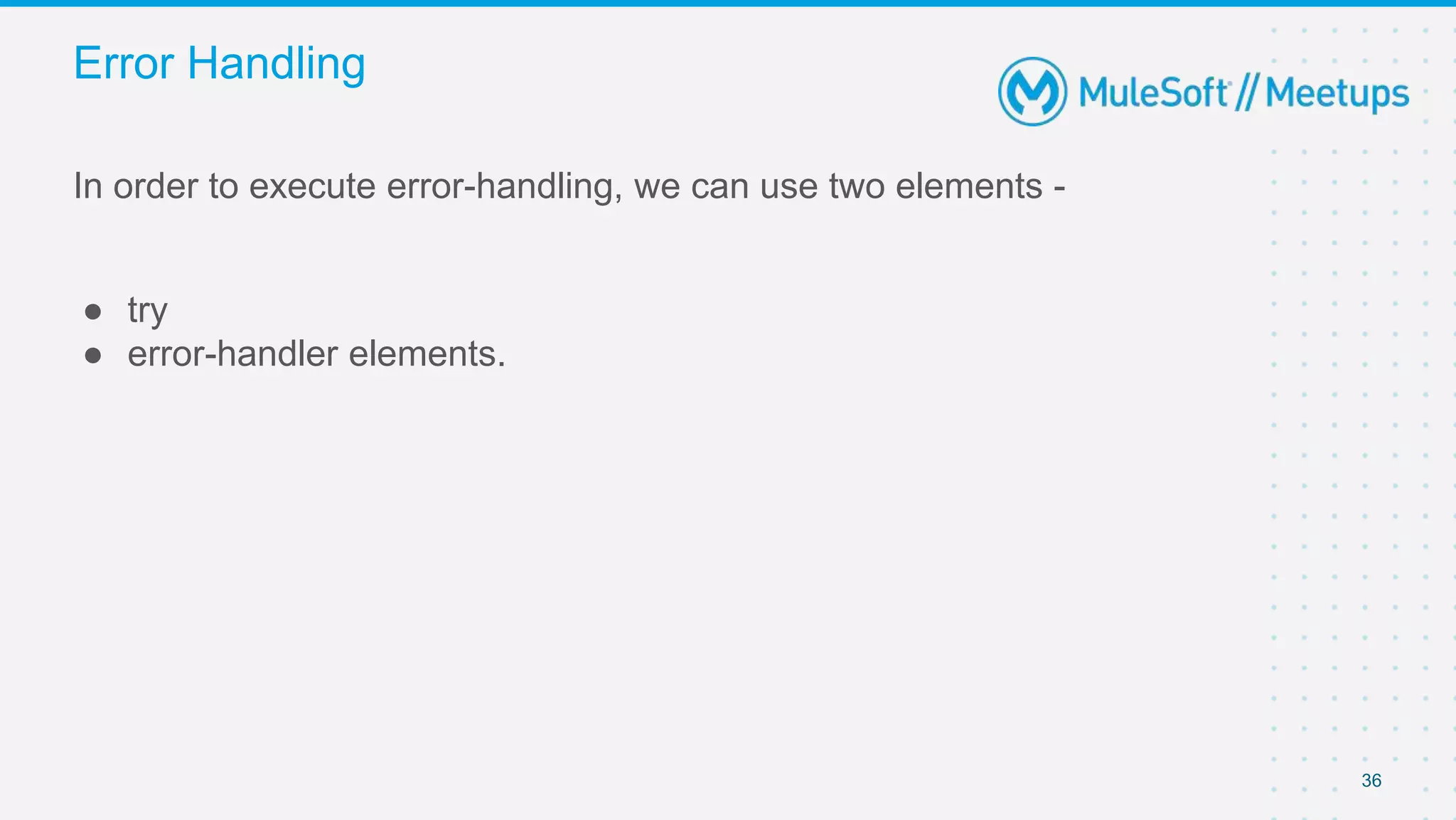
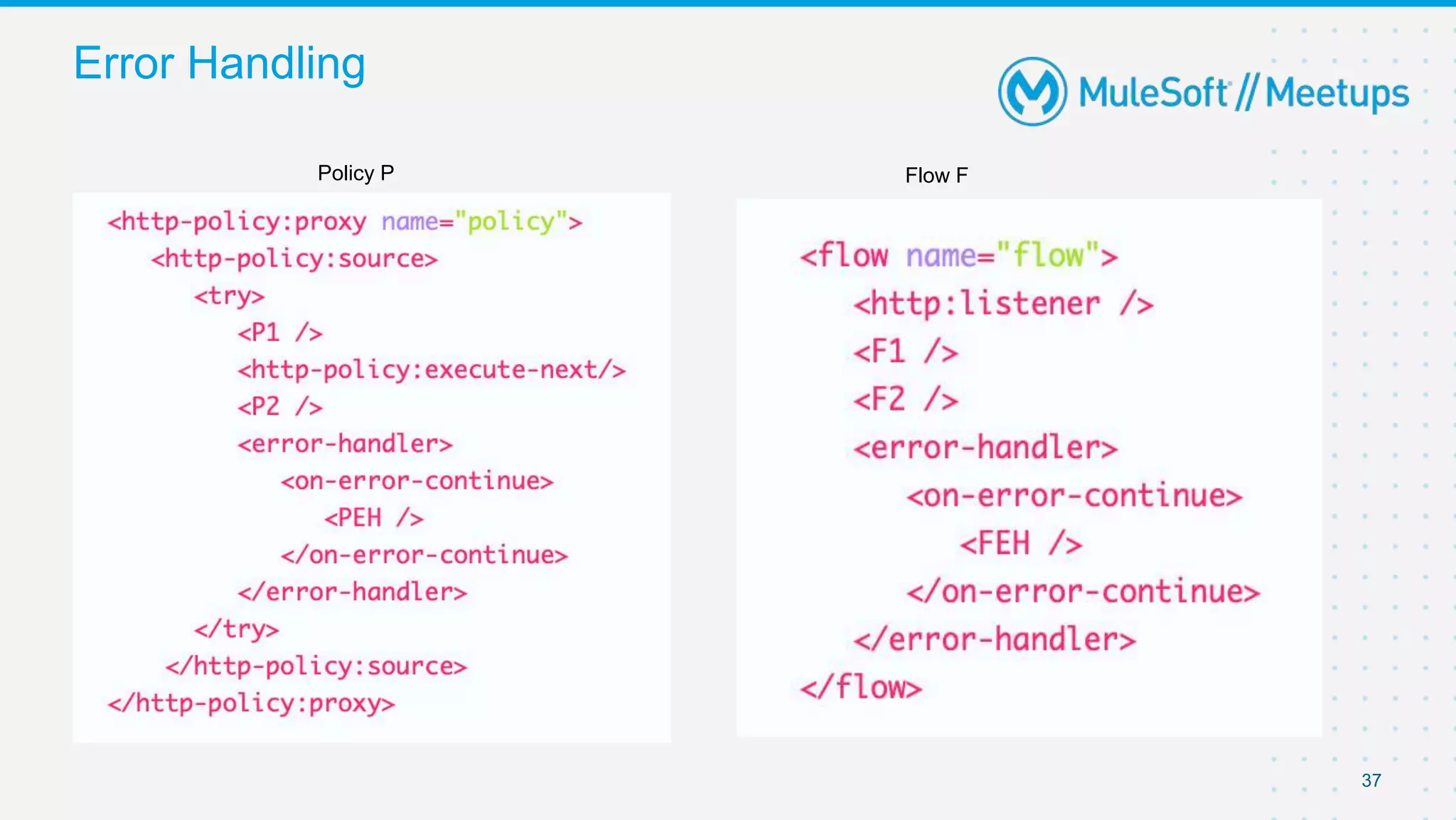
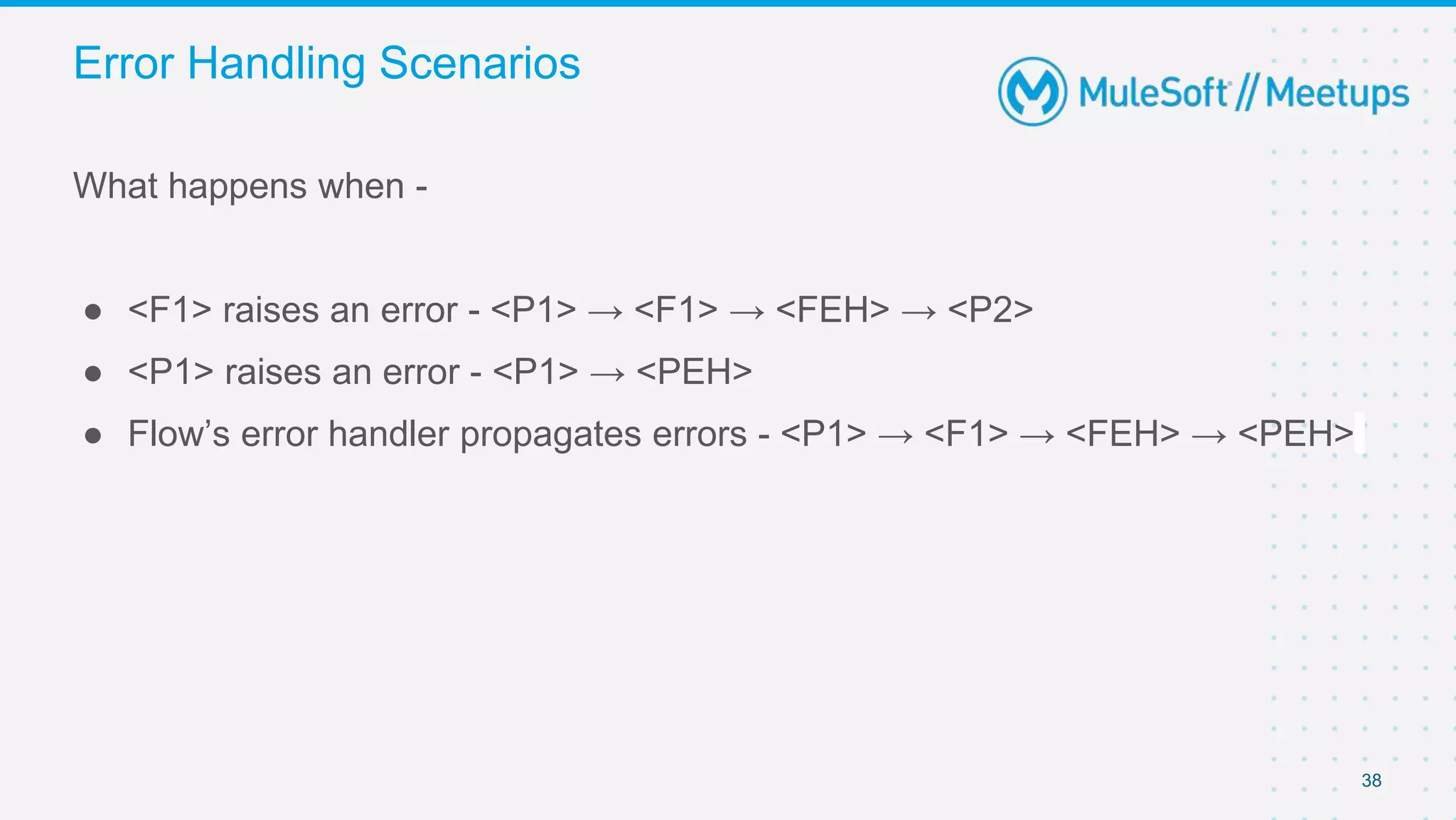
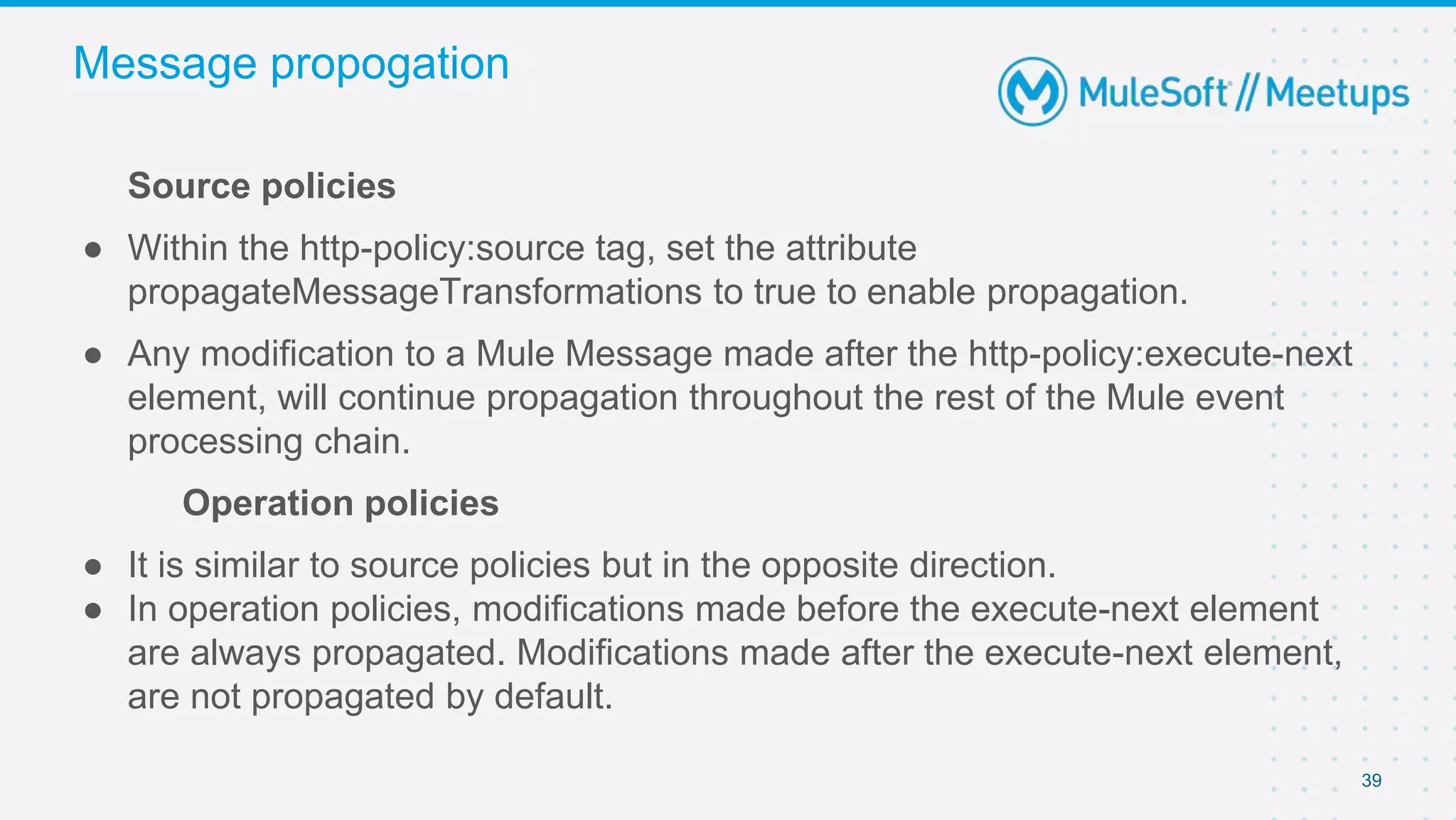
The document summarizes a presentation about custom policies in Mule 4. It includes an agenda for the presentation, background on API security and attacks, an overview of policy categories and types in Mule, steps for creating a custom policy, and a demo. The presentation covers what custom policies are, when to use them, how to develop, package, and apply them, and how to configure them with parameters and Handlebars variables. It also discusses policy execution order, propagation, and error handling. The document concludes with a trivia quiz and next steps.






![42
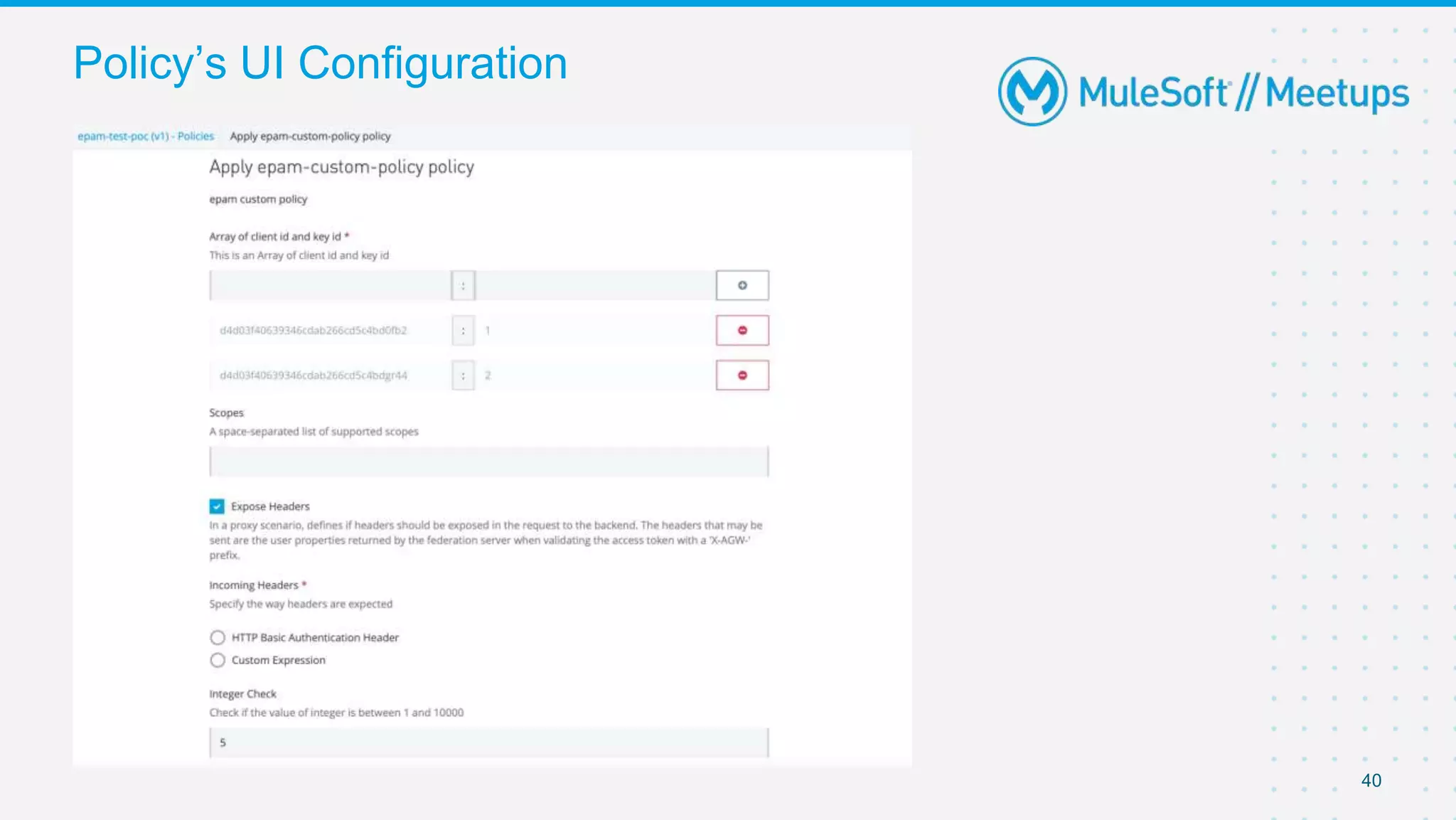
○ String: Any string expected.
○ Expression: A DataWeave expression starting with #[ and finished with ] is
expected.
○ Boolean: true or false.
○ Int: A number is expected. This type requires additional properties
○ Radio: One value of a group of options. This type requires additional
properties- minimum and maximum value
○ Keyvalues: Collection of Key-Value pairs.
Additional Configurations](https://image.slidesharecdn.com/6-demystifyingcustompoliciesinmule-211129210447/75/6-Calicut-MuleSoft-Meetup-Demystyfying-Custom-Policies-in-Mule-42-2048.jpg)