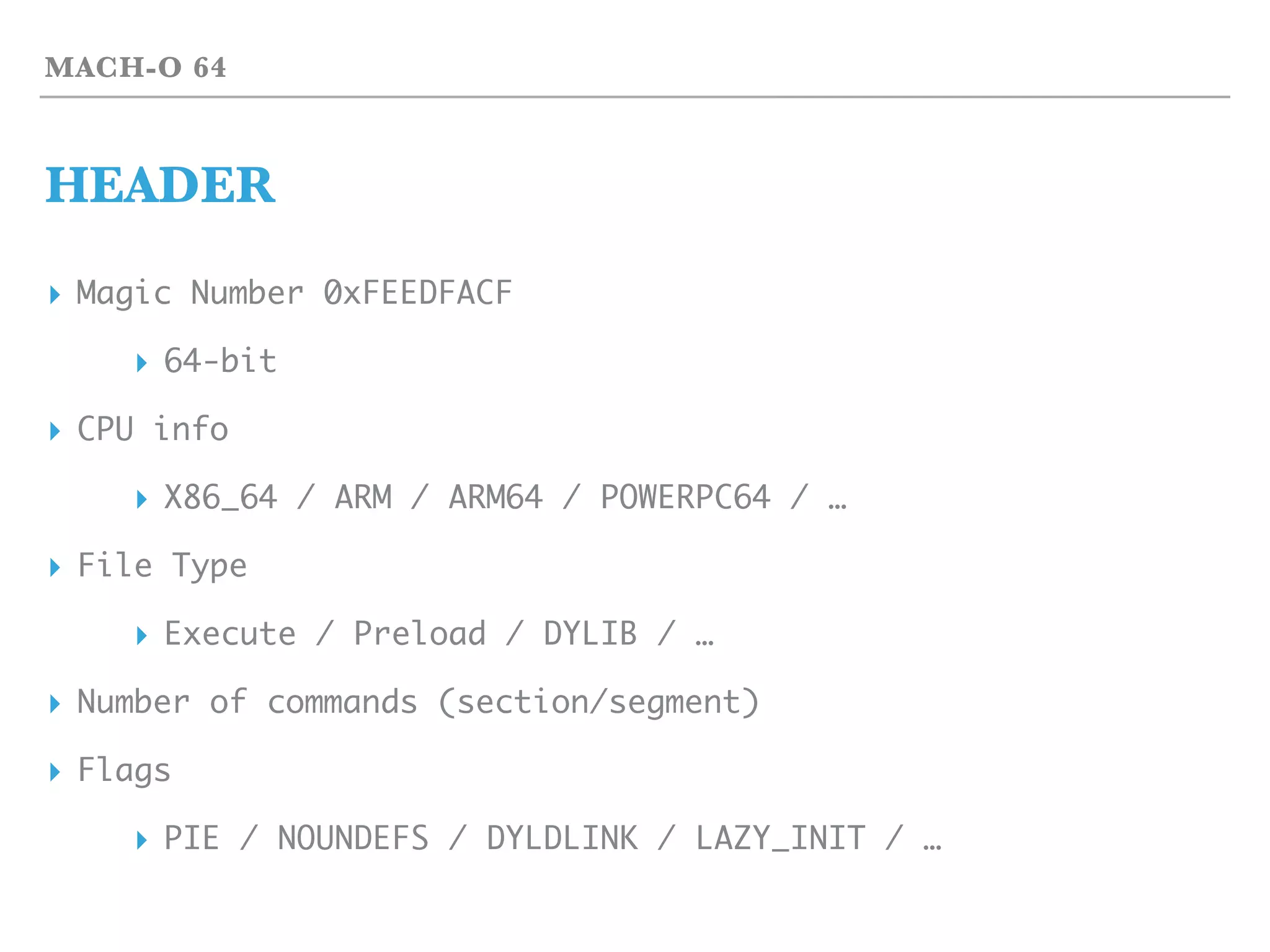
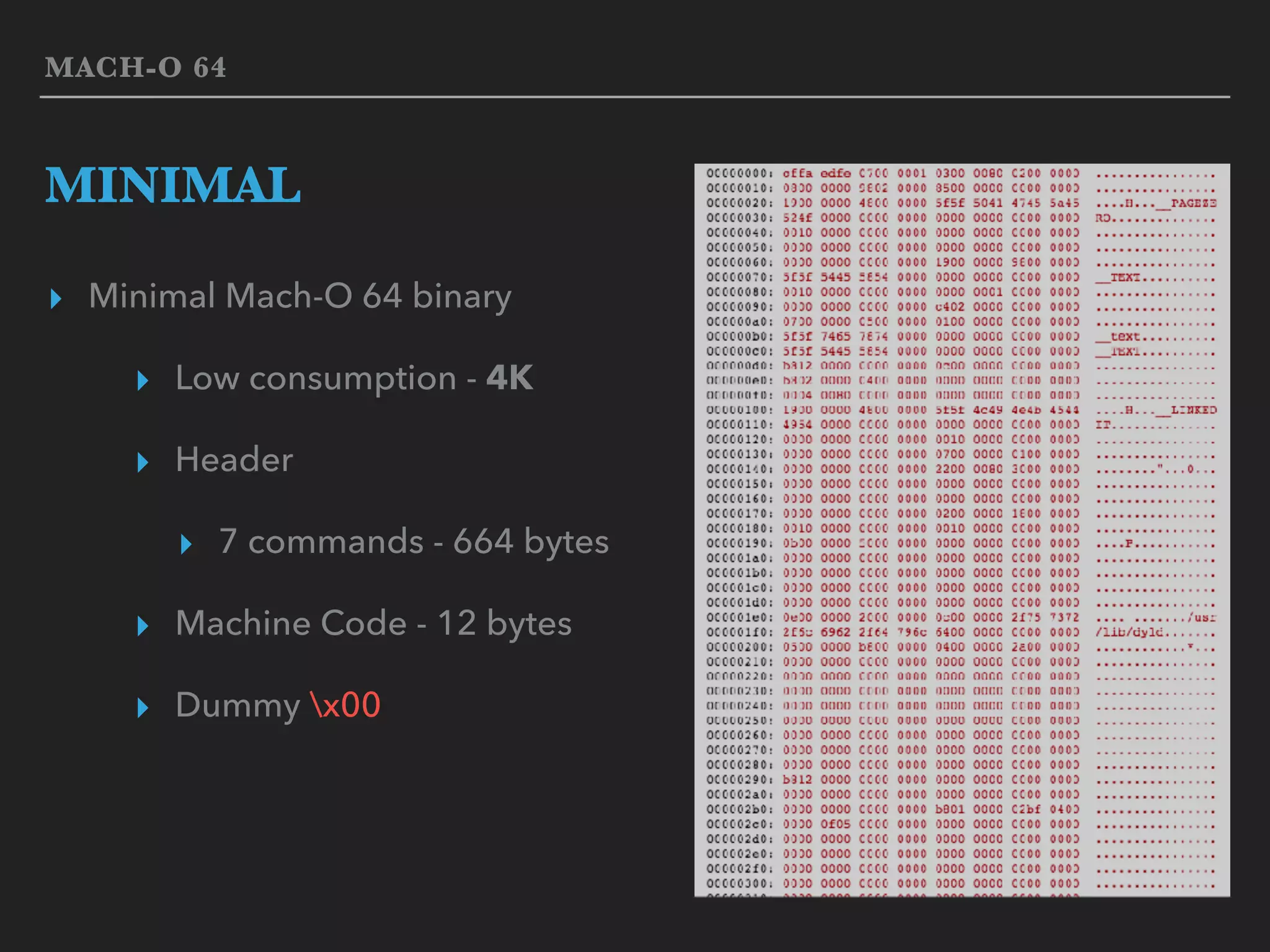
The document provides an overview of binary formats and machine code. It discusses the Mach-O binary format used on Mac OS X, including the header, commands, segments, and sections. It also covers x86-64 machine code layout and opcodes. A minimal Mach-O 64 binary is listed as an example, containing a header, commands, and 12 bytes of machine code while consuming only 4K of space.






![⽂字
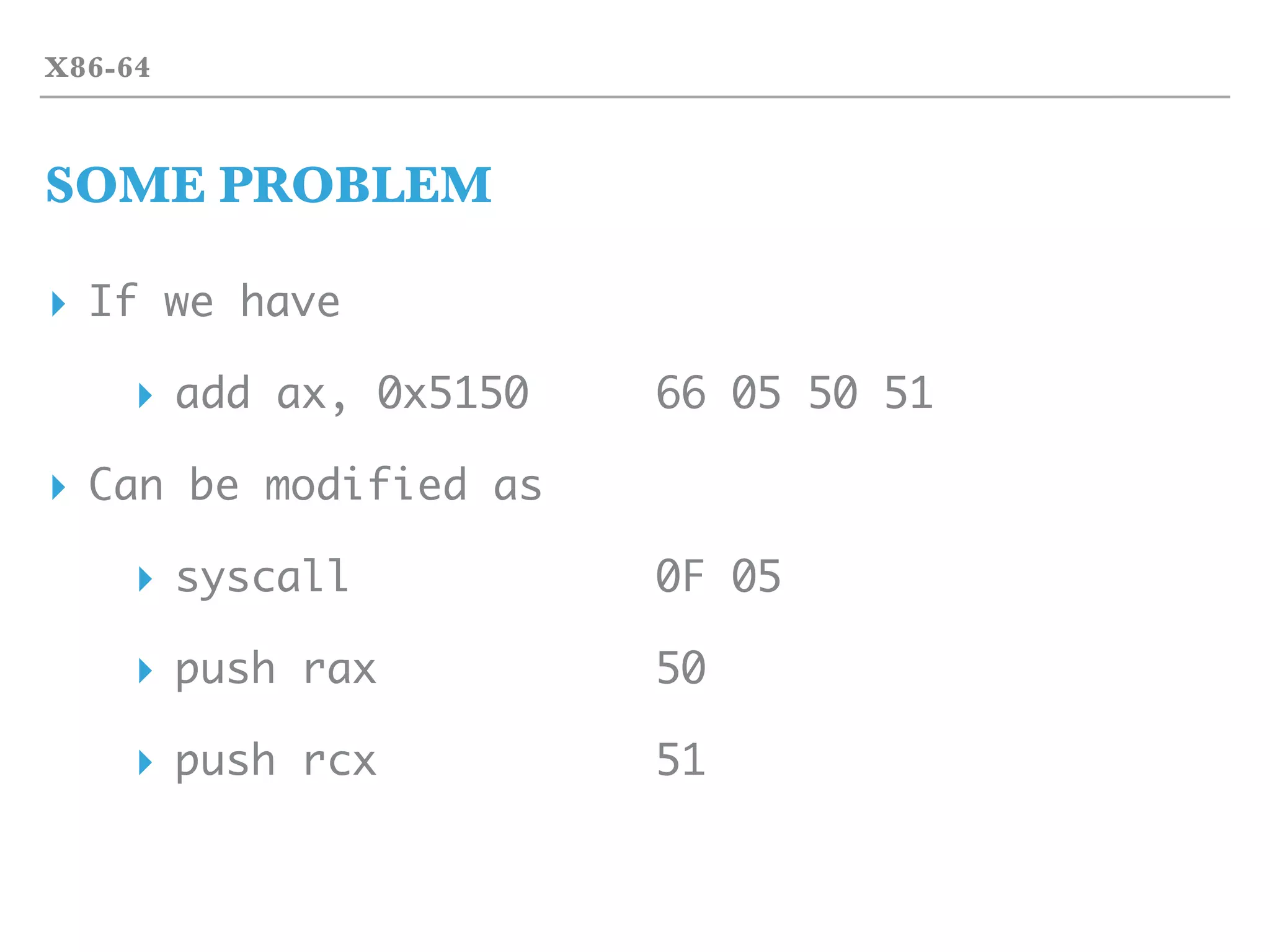
MOV
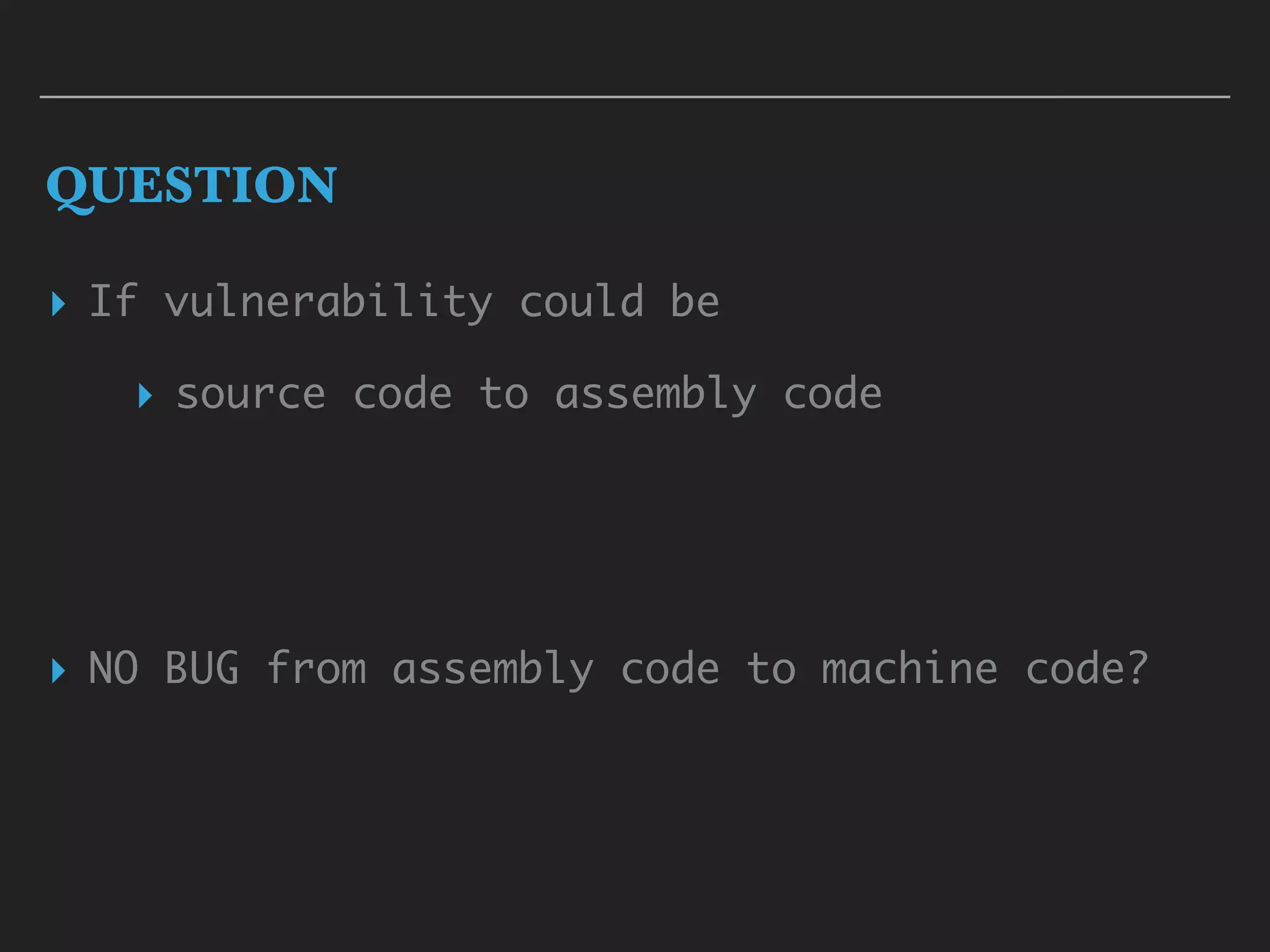
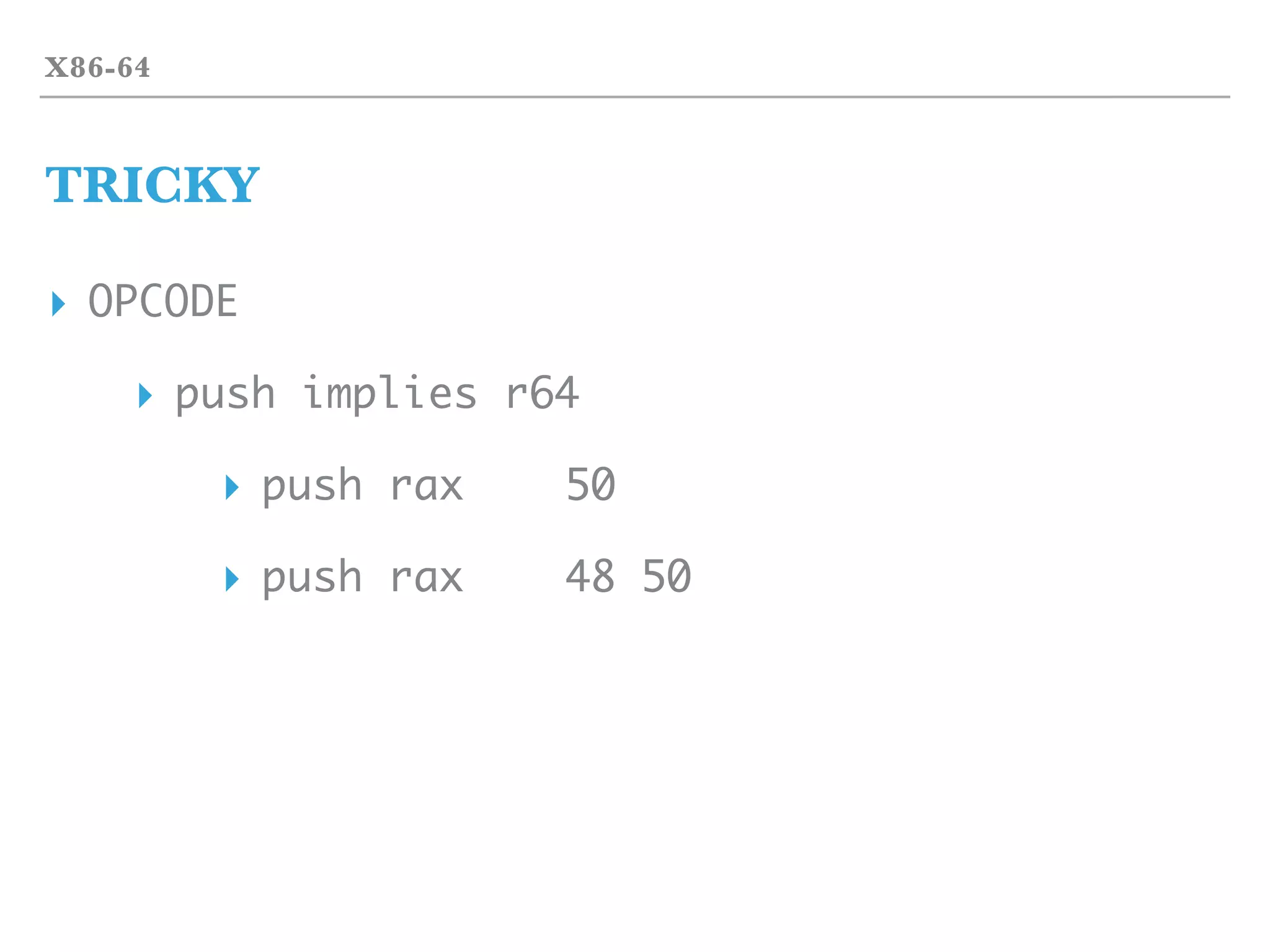
▸ In x86-64 opcodes
▸ lots of opcodes are MOV
▸ move from/to memory are frequently used actions
▸ mov ch, dl
▸ mov rax, [rax-0x10]
▸ mov [r8], rsp
▸ lea cx, [rbx]
▸ But there are difference opcode!](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-18-2048.jpg)
![AGE
SAVE DATA
▸ Save 18 as age into program
▸ mov rax, 18 ; save as register
▸ mov [rax], 18 ; save into memory
▸ push 18 ; save into stack](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-19-2048.jpg)
![GENDER
SAVE DATA
▸ Save ‘F’ (0x46) as gender into program
▸ mov rax, 0x46 ; save as register
▸ mov [rax], 0x46 ; save into memory
▸ push 0x46 ; save into stack](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-20-2048.jpg)
![GENDER
SAVE DATA
▸ Save ‘Female’ as gender into program
▸ mov [rax], 0x46656D61
▸ mov [rax+0x04], 0x6C650000
▸ push 0x46
▸ push 0x65
▸ push …](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-21-2048.jpg)



![IN C LANGUAGE
ASSUMPTION
▸ Struct in C
struct foo {
int age;
char gender[8];
char email[128];
};
‣ What happen if overflow in gender
‣ email is corrupt / age is corrupt
age
gender
email
0x1230
0x12B9](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-25-2048.jpg)
![IN ASM
ASSUMPTION
[0x400000] call 0x400043
…
[0x400043] mov rax 18
[0x400048] ret](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-26-2048.jpg)
![IN ASM
ASSUMPTION
[0x400000] call 0x400043
…
[0x400043] push 18
[0x400048] ret](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-27-2048.jpg)
![IN ASM
ASSUMPTION
[0x400000] call 0x400043
…
[0x400043] mov [rbp-0x10] 0x46
[0x40004E] ret](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-28-2048.jpg)
![IN ASM
ASSUMPTION
[0x400000] call 0x400043
…
[0x400043] mov r8 [rip+0x08]
[0x40004A] mov [r8] 18
[0x400051] ret](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-29-2048.jpg)
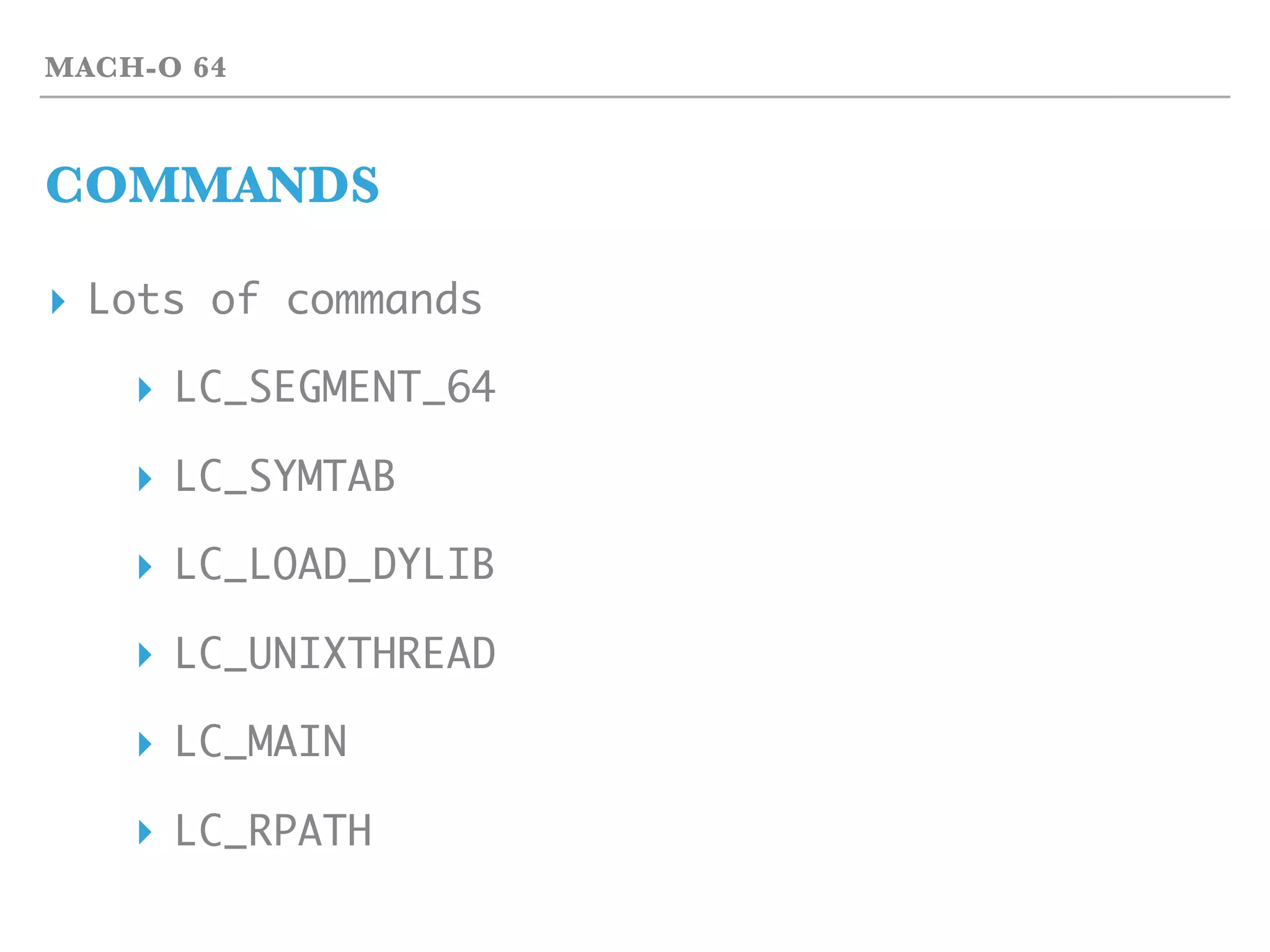
![LEGACY
CODE/DATA BOTH IN MEMORY
▸ First: call is combined from push and jump
▸ call 0x400035
1. push rip
2. jump 0x400035
‣ ret
1. pop rip
2. jump rip
‣ And more
▸ call rax
▸ call [rax]](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-30-2048.jpg)


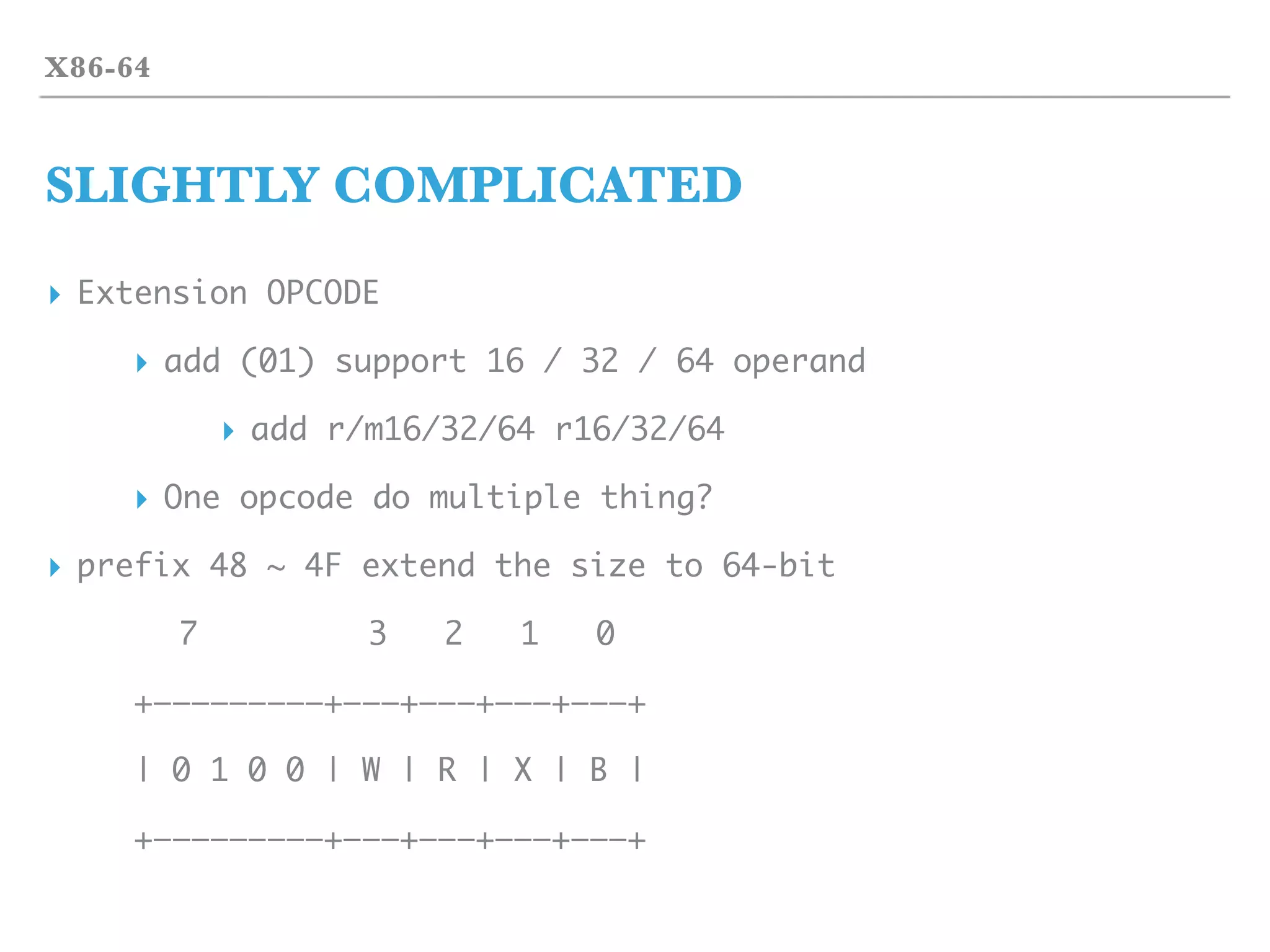
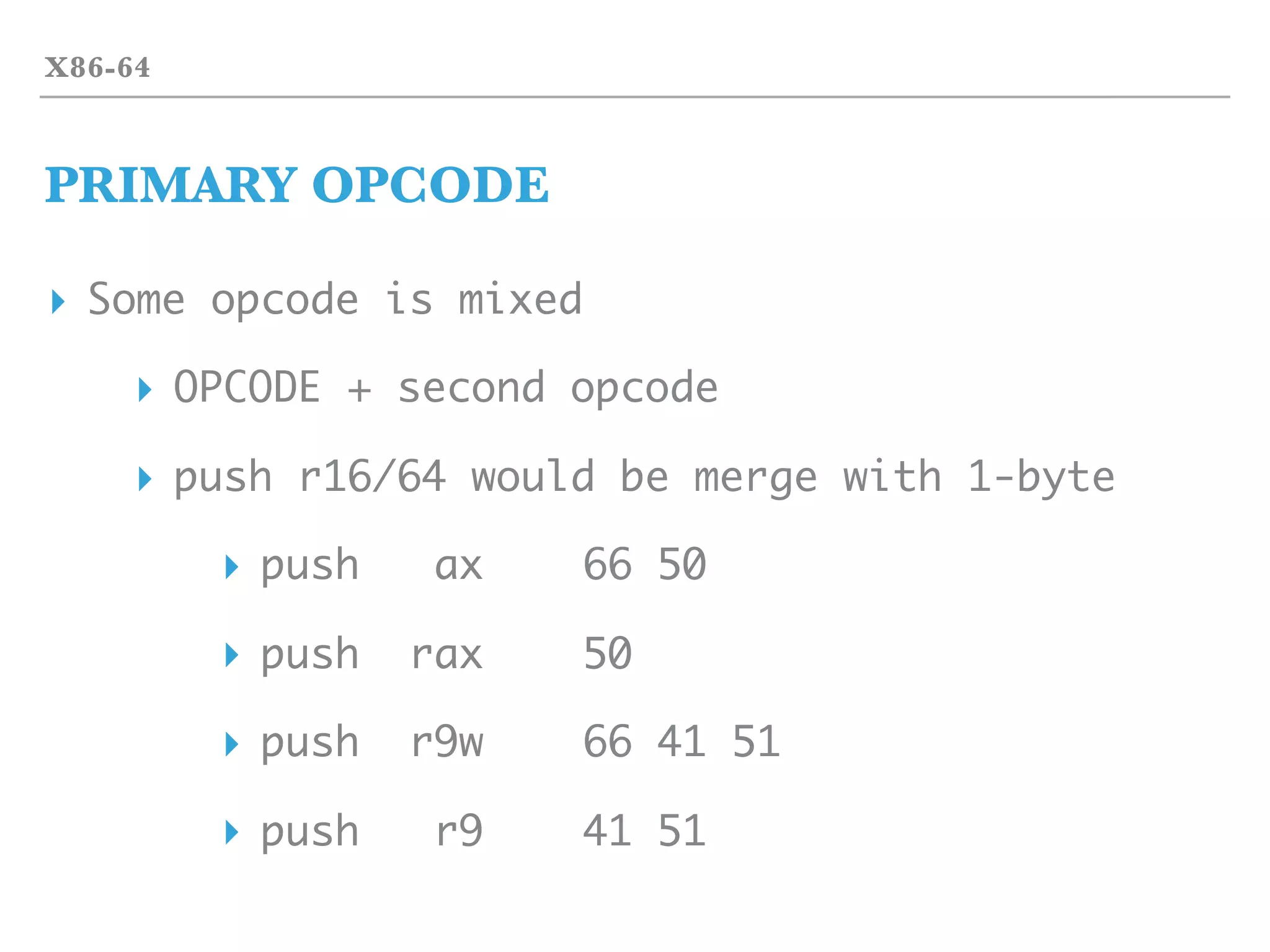
![INSTRUCTION
X86-64 MACHINE CODE
▸ X86-64 machine code layout
▸ [prefix] [opcode] [MOD] [SIB] [Displacement] [Immediate]
▸ Max to 15-bytes peer each instruction
▸ Displacement + Immediate max to 8-bytes (64-bit address)
▸ R(educed)ISC vs C(omplex)ISC](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-36-2048.jpg)
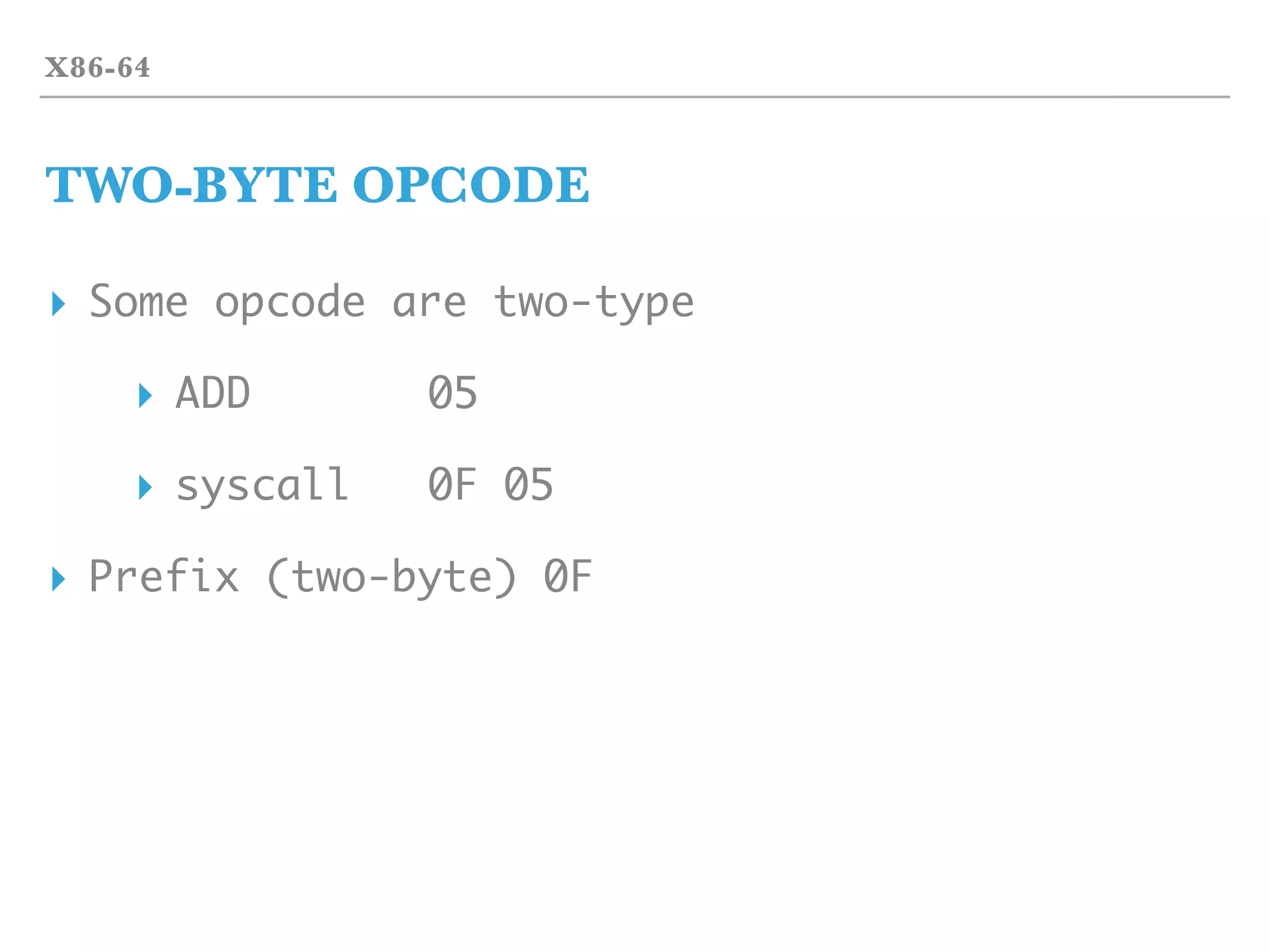
![STFW
OPCODE
▸ X86-64 opcode
▸ Intel Manual[0]
▸ Web Resource[1]
▸ OPCODE possible 00 ~ FF
▸ Each one has possible usage or invalid
[0]: https://software.intel.com/sites/default/files/managed/ad/01/253666-sdm-vol-2a.pdf
[1]: http://ref.x86asm.net/coder64.html](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-37-2048.jpg)
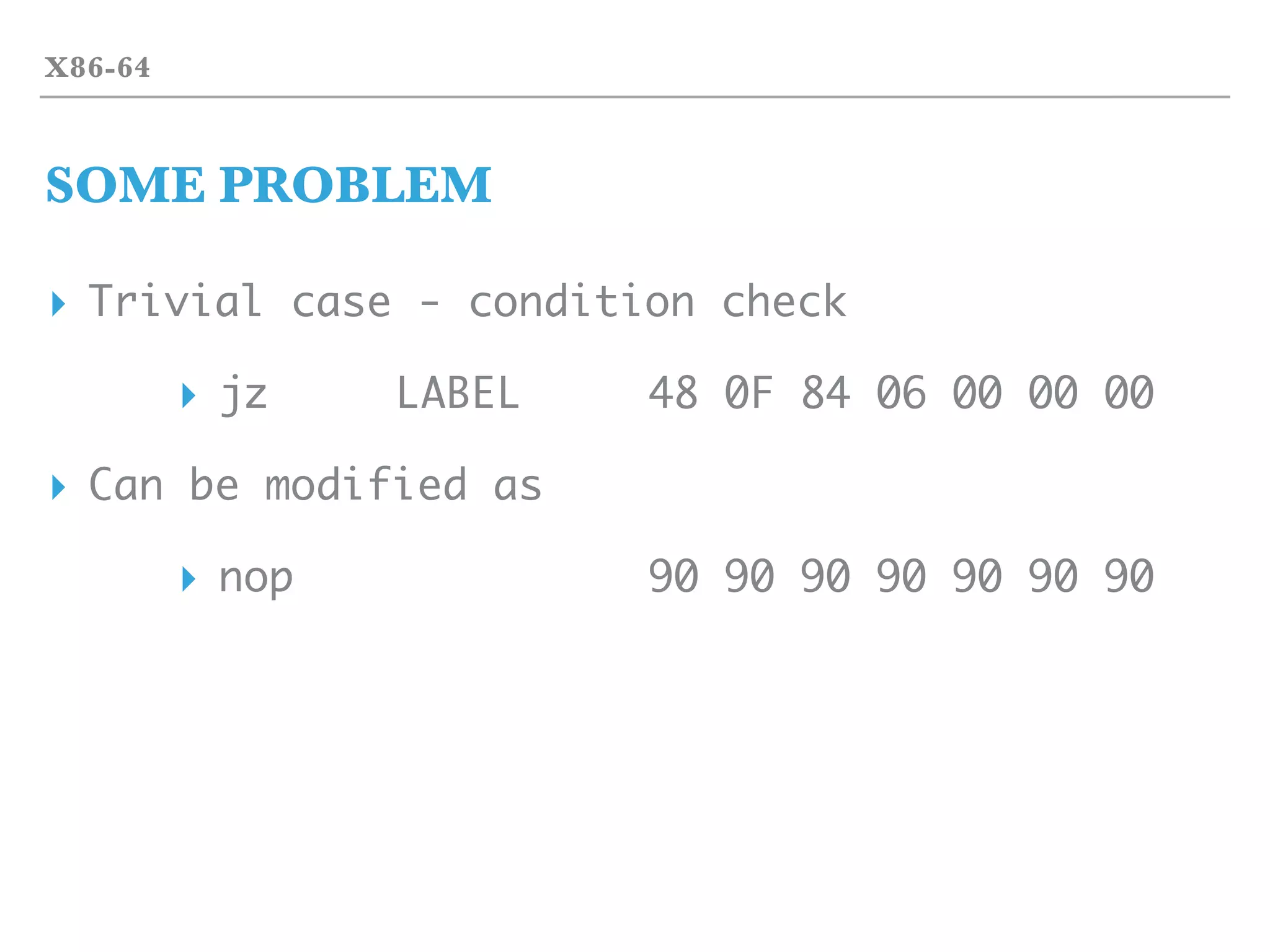
![SIMPLE LIFE
OPCODE
▸ Simple (frequently-used) opcode
▸ No-OPeration
▸ NOP 90 (maybe xchg eax, eax)
▸ NOP 0F 0D
▸ FNOP D9 D0 (FPU nop)
[0]: http://stackoverflow.com/questions/25008772/whats-the-difference-between-the-x86-nop-and-fnop-
instructions](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-38-2048.jpg)
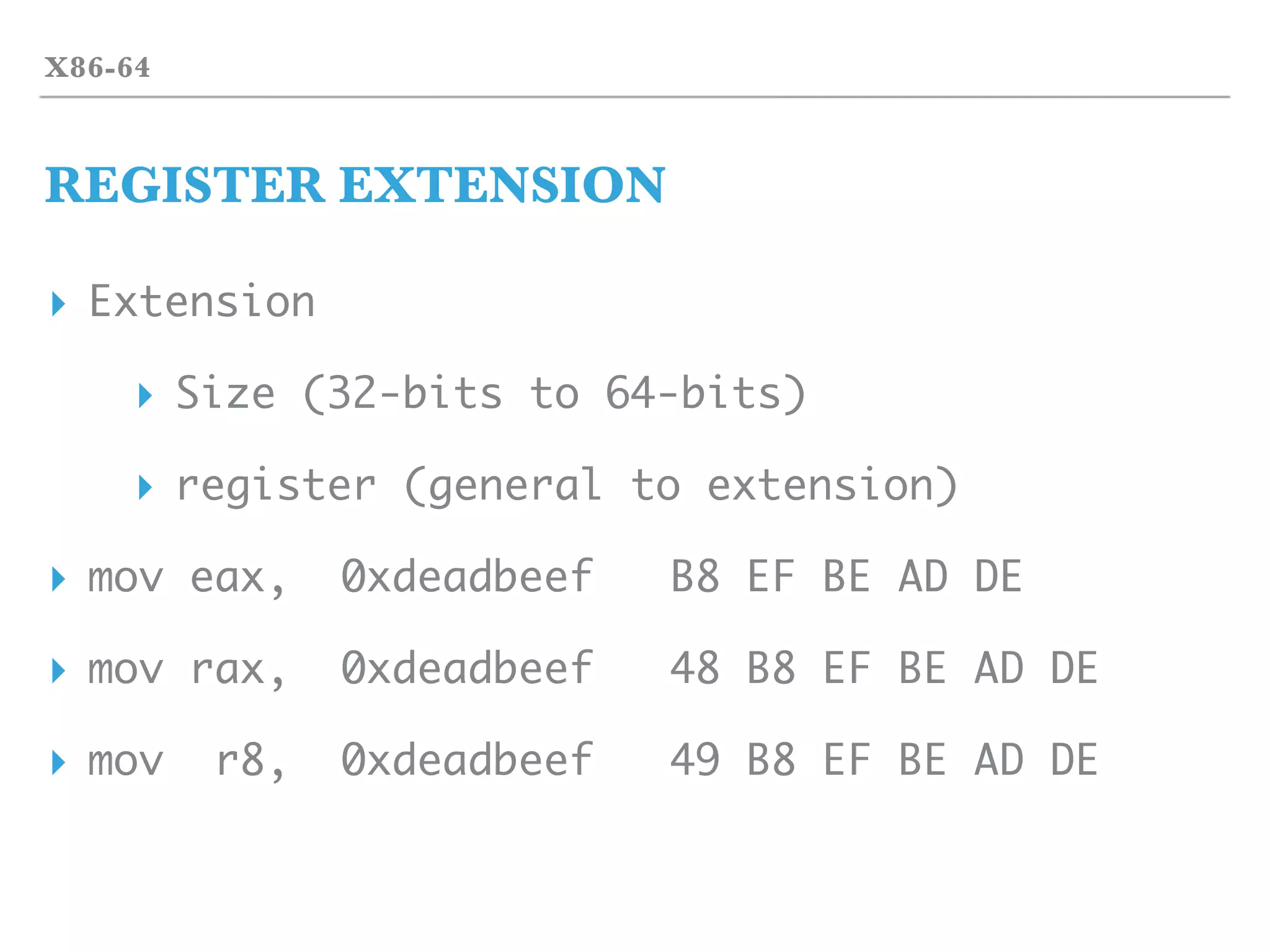


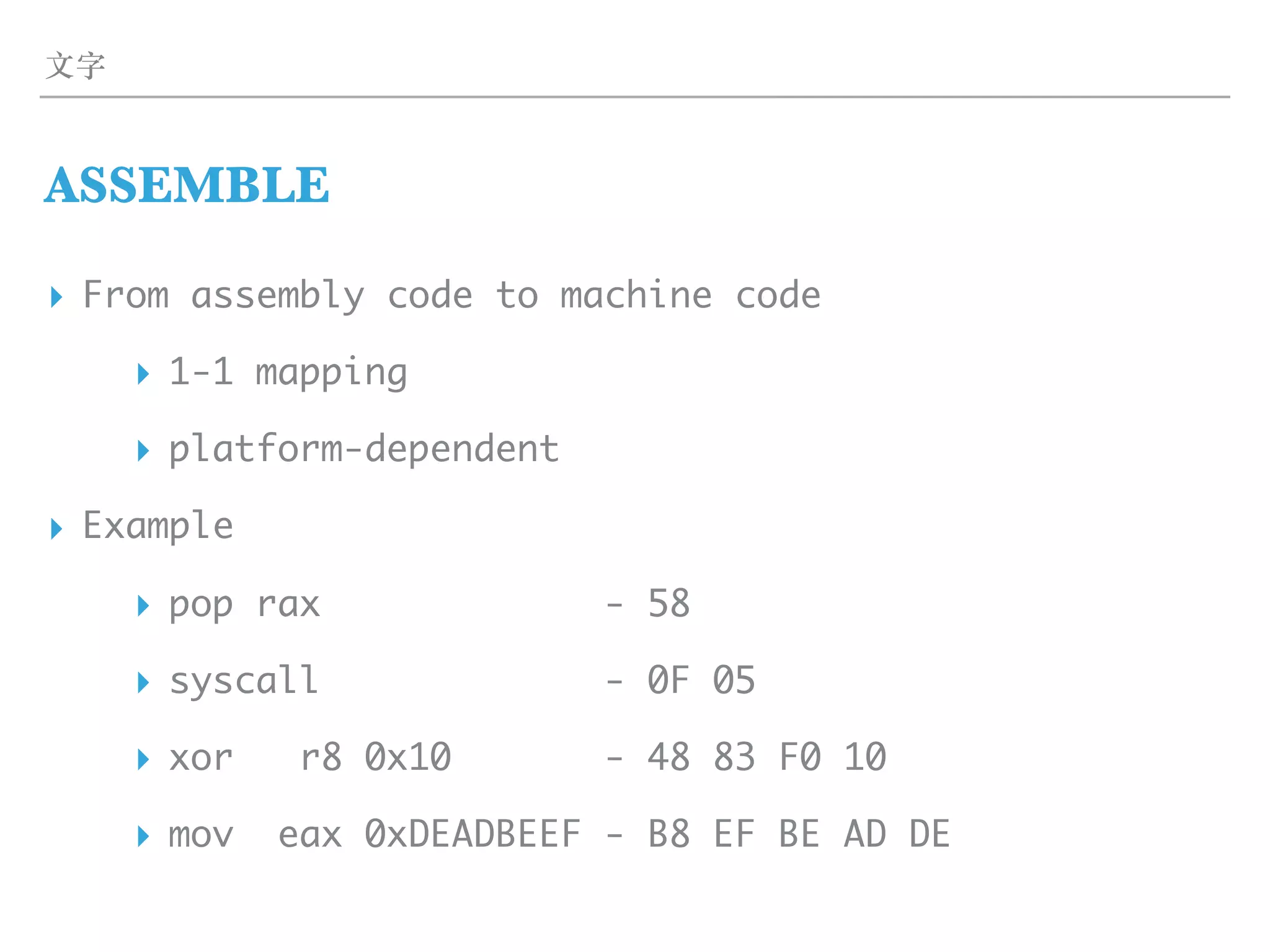
![ZASM
ASSEMBLER
▸ Assembler
▸ From assembly language to machine code
▸ Target format (ELF / Mach-O / …)
▸ Target platform (x86-64 / ARMv8 / …)
▸ Generator
[0]: https://github.com/cmj0121/Zerg/tree/master/src/zasm](https://image.slidesharecdn.com/2017-170324055826/75/2017-03-18-hst-binary-training-part-1-53-2048.jpg)
