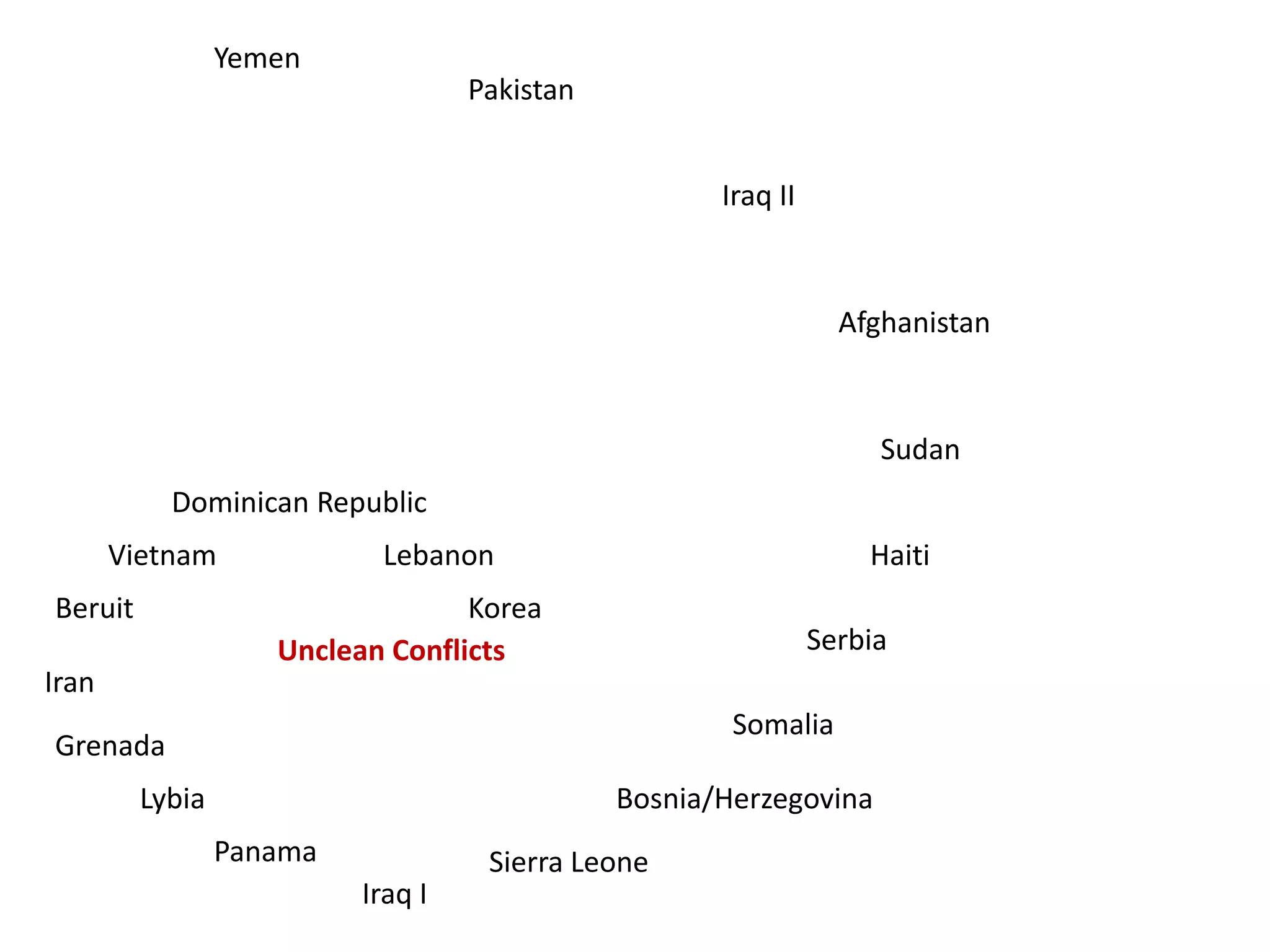
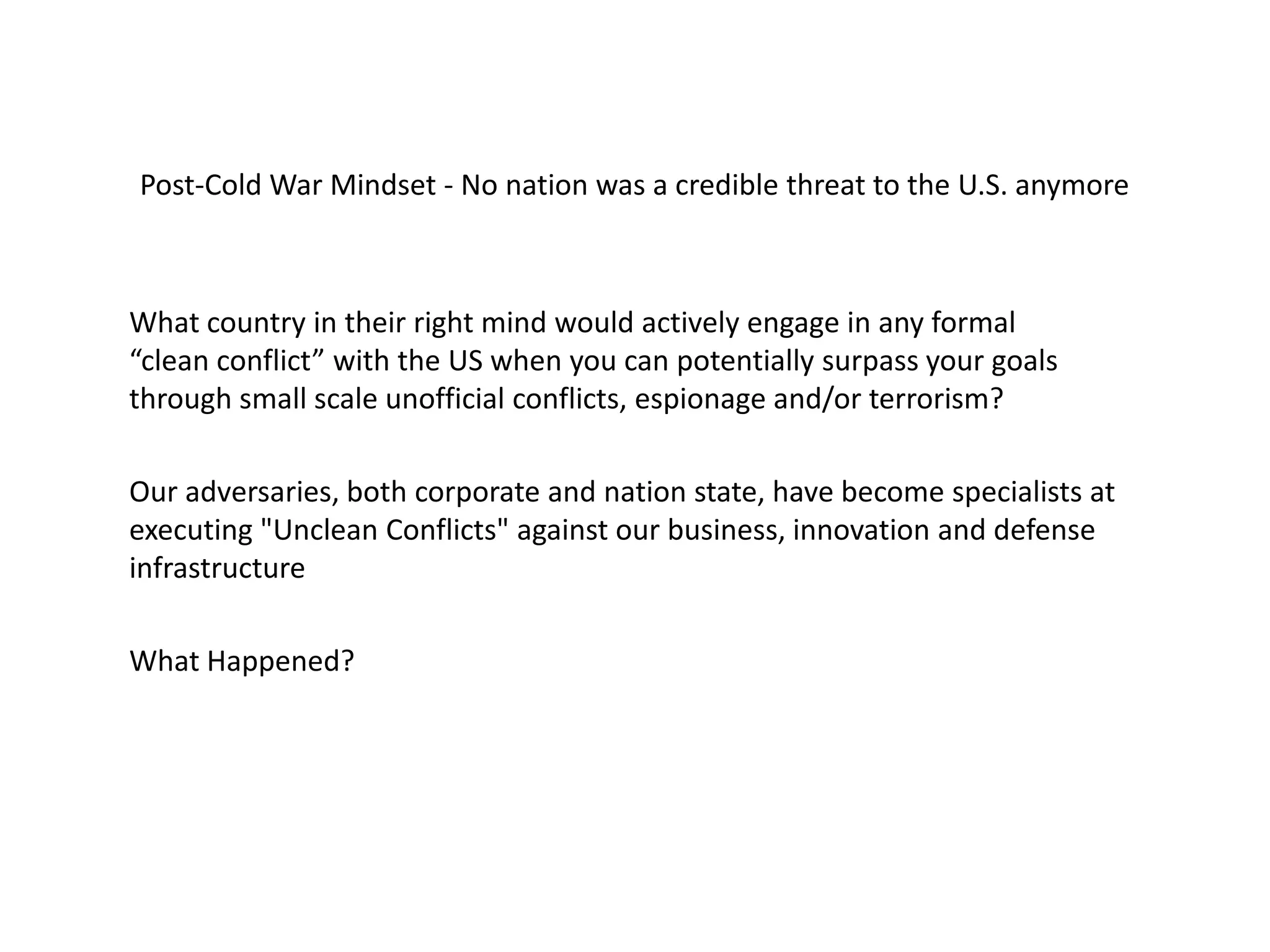
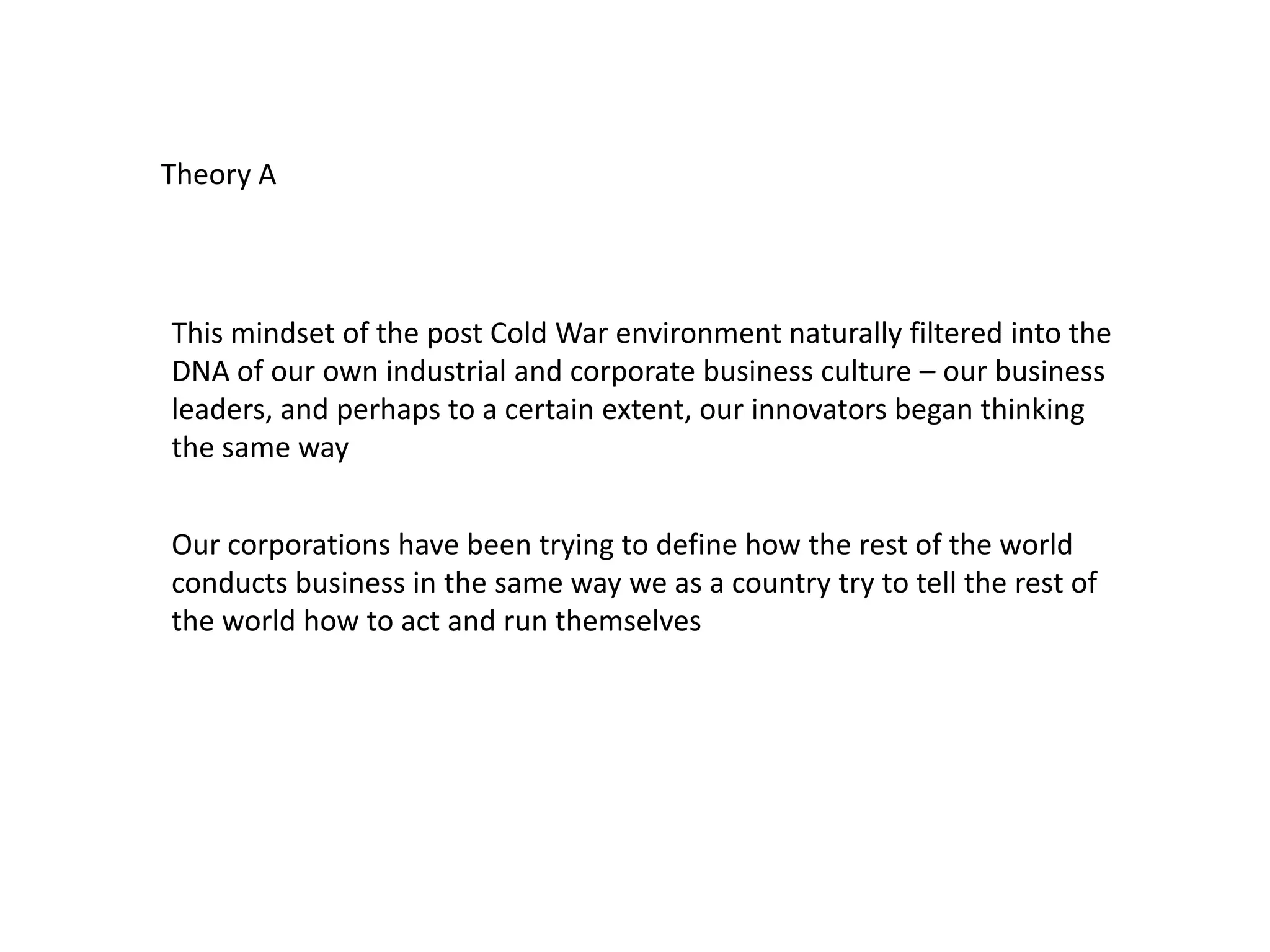
This document discusses how businesses and organizations have become less adaptable due to post-Cold War arrogance, which has led to increased risks from "unclean conflicts" like espionage and terrorism. It argues that organizations need to switch from reactive security solutions to more adaptive approaches inspired by natural systems. This includes decentralization, redundancy, uncertainty reduction, learning from failures, and promoting competition that leads to cooperation. The challenge is posed to security practitioners to consider introducing these behavioral and process changes within their own spheres of influence to help transform organizational culture.