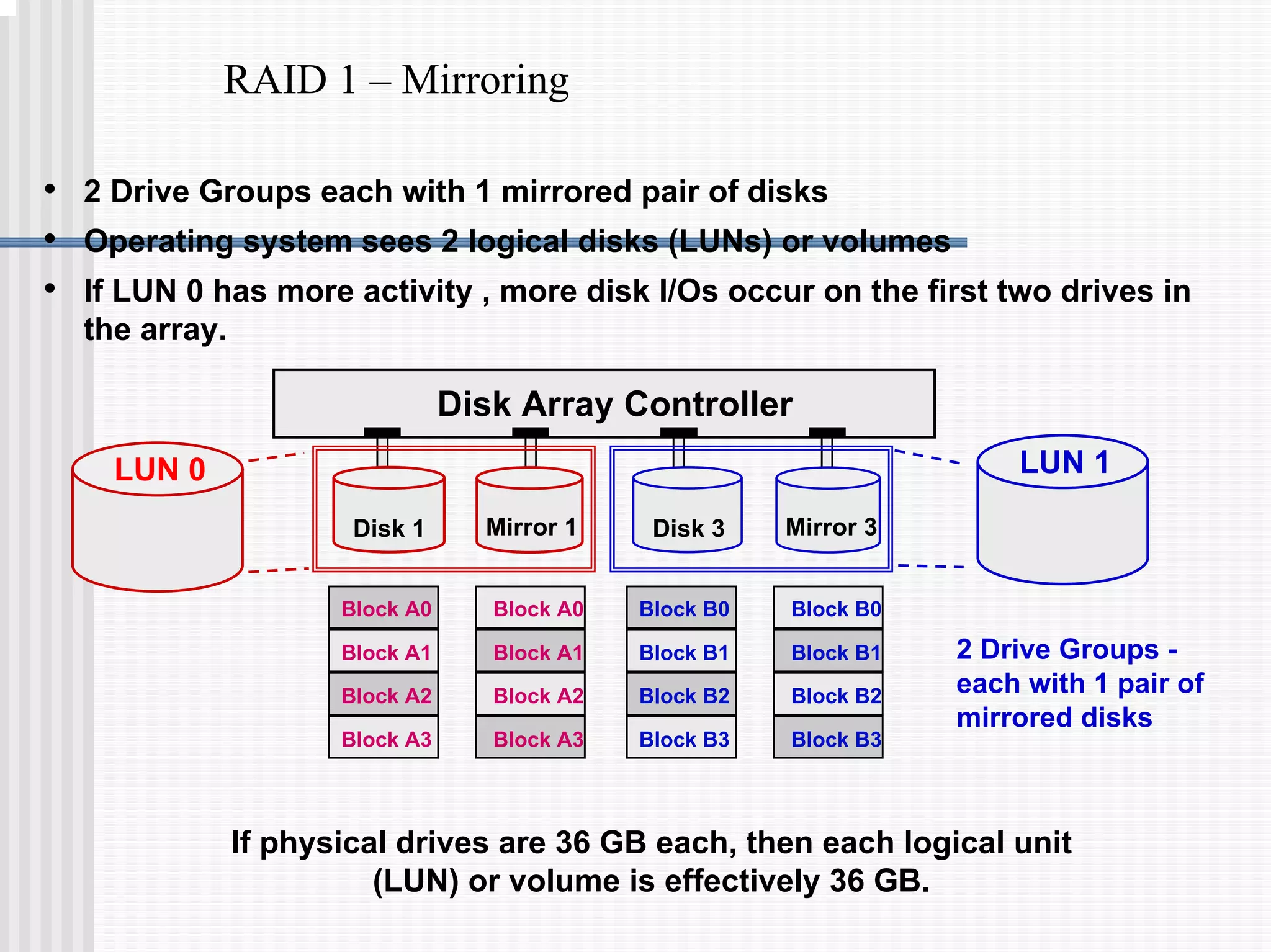
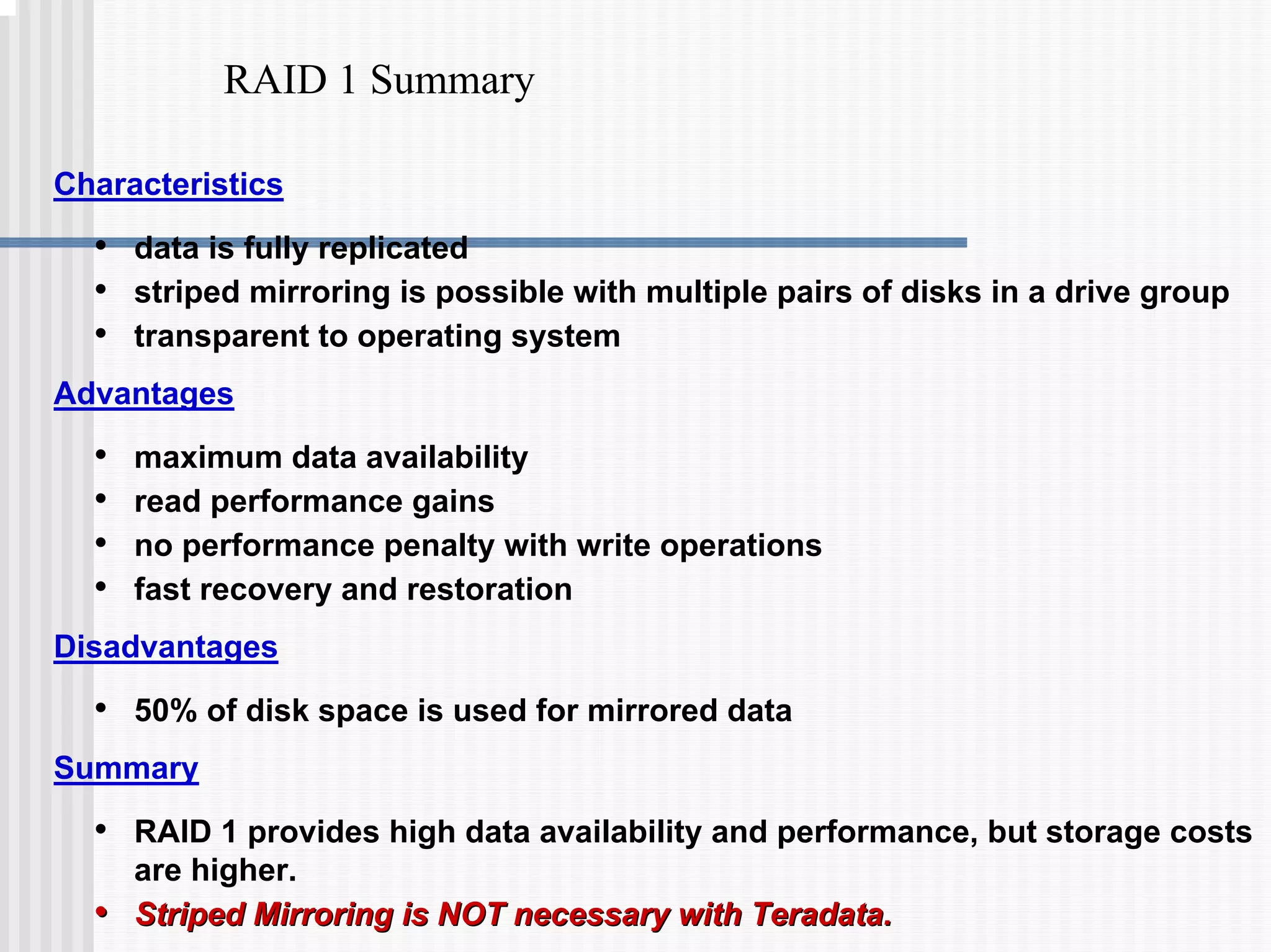
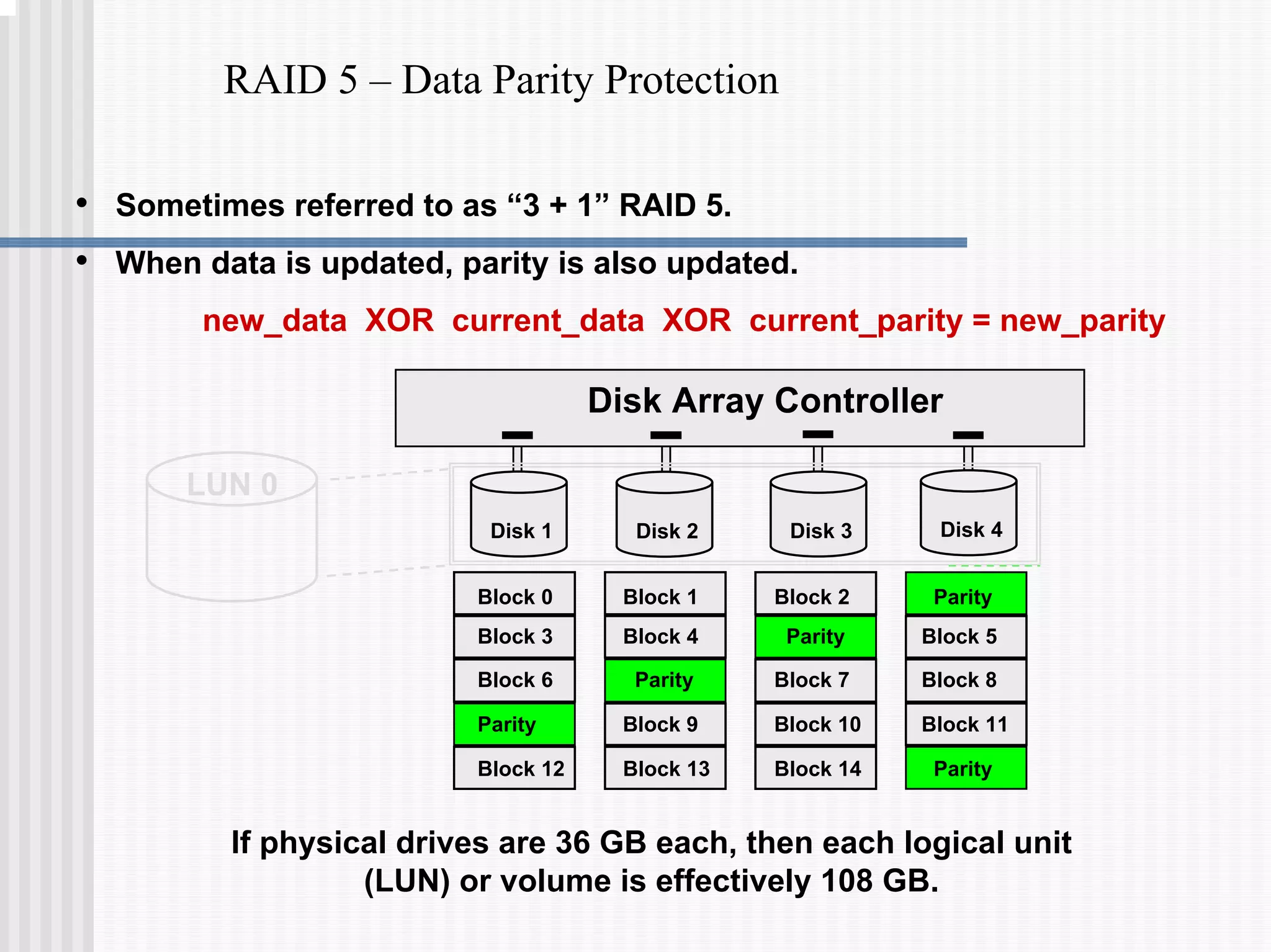
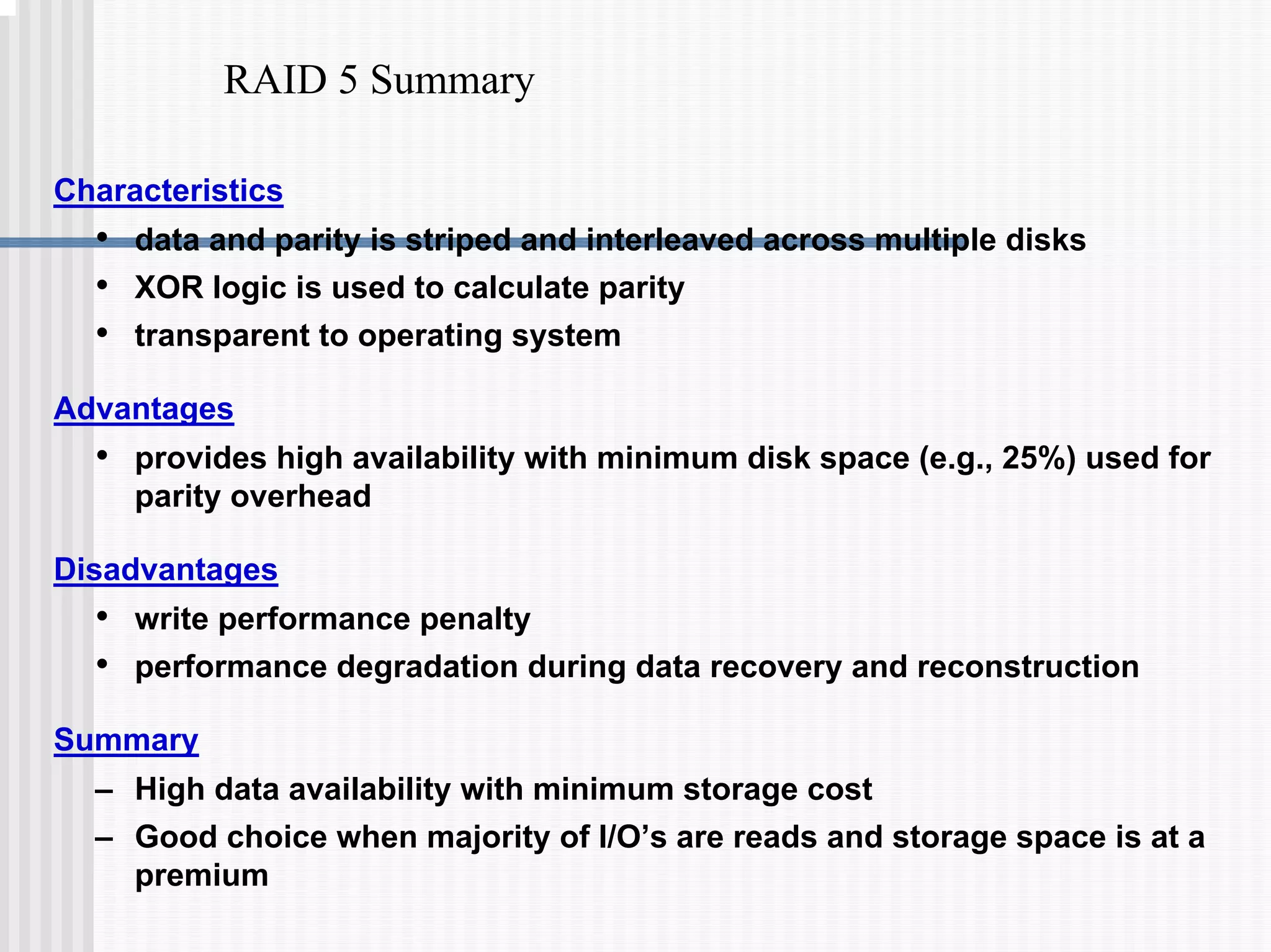
This document discusses various data protection features in Teradata, including:
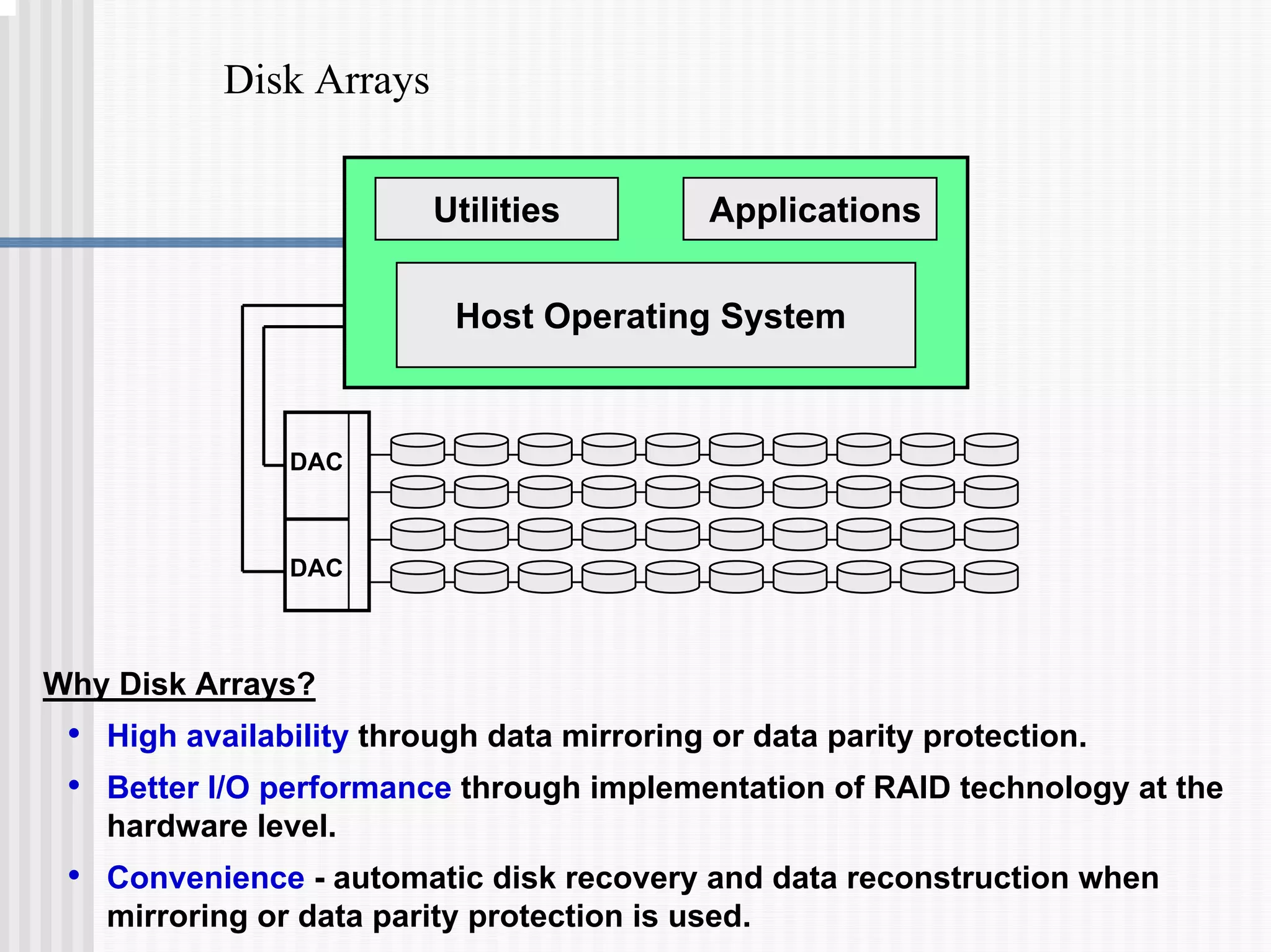
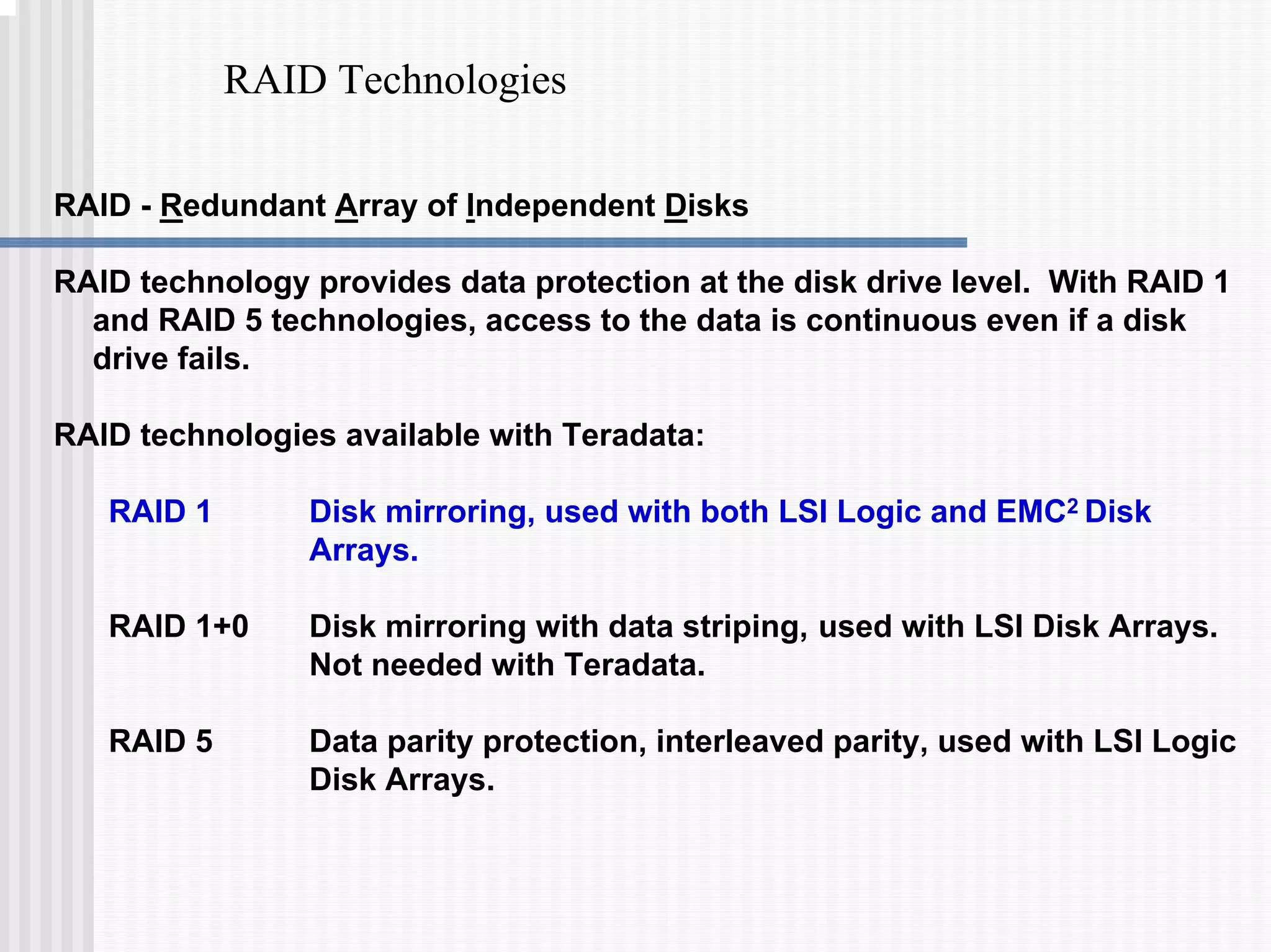
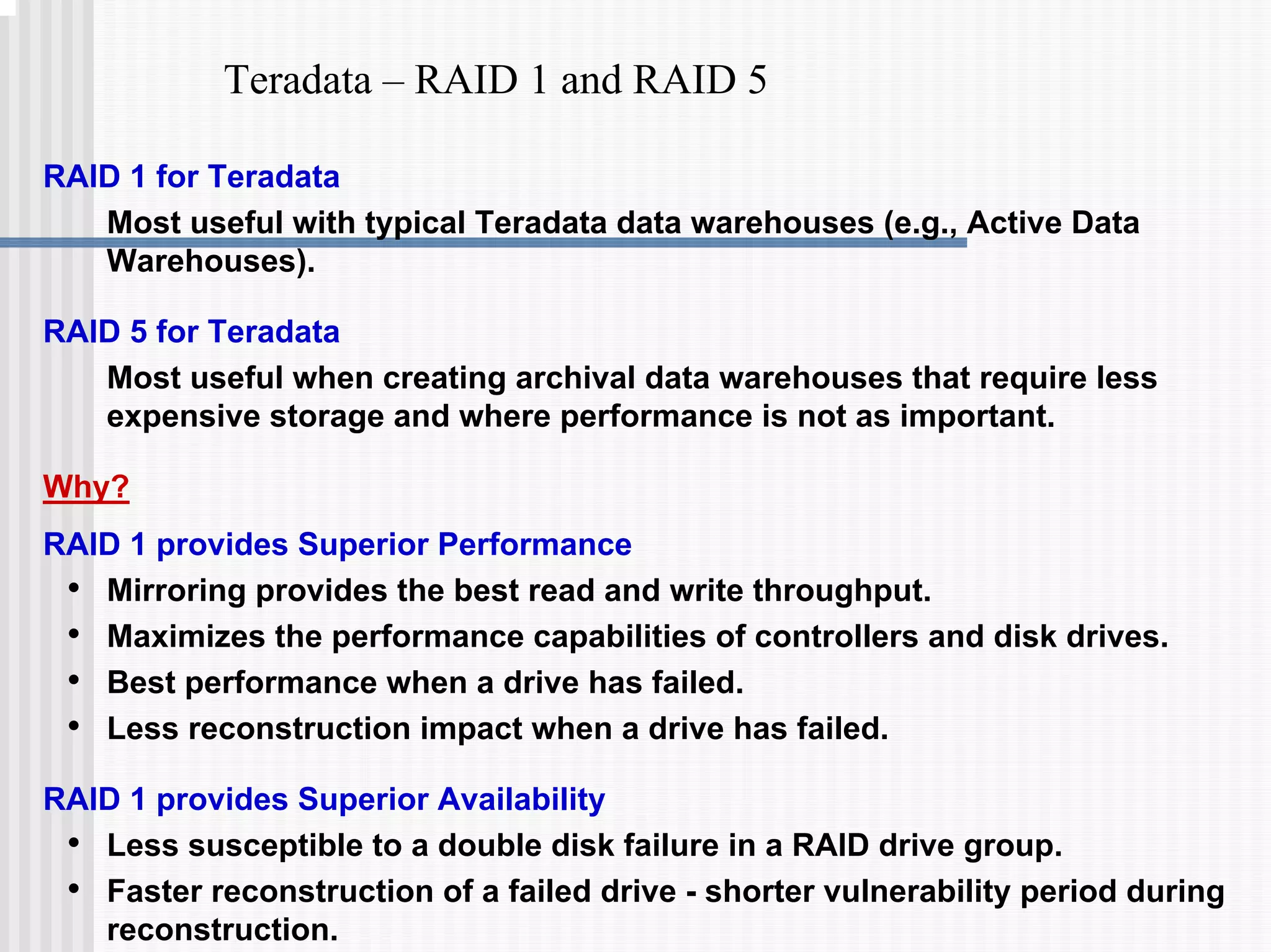
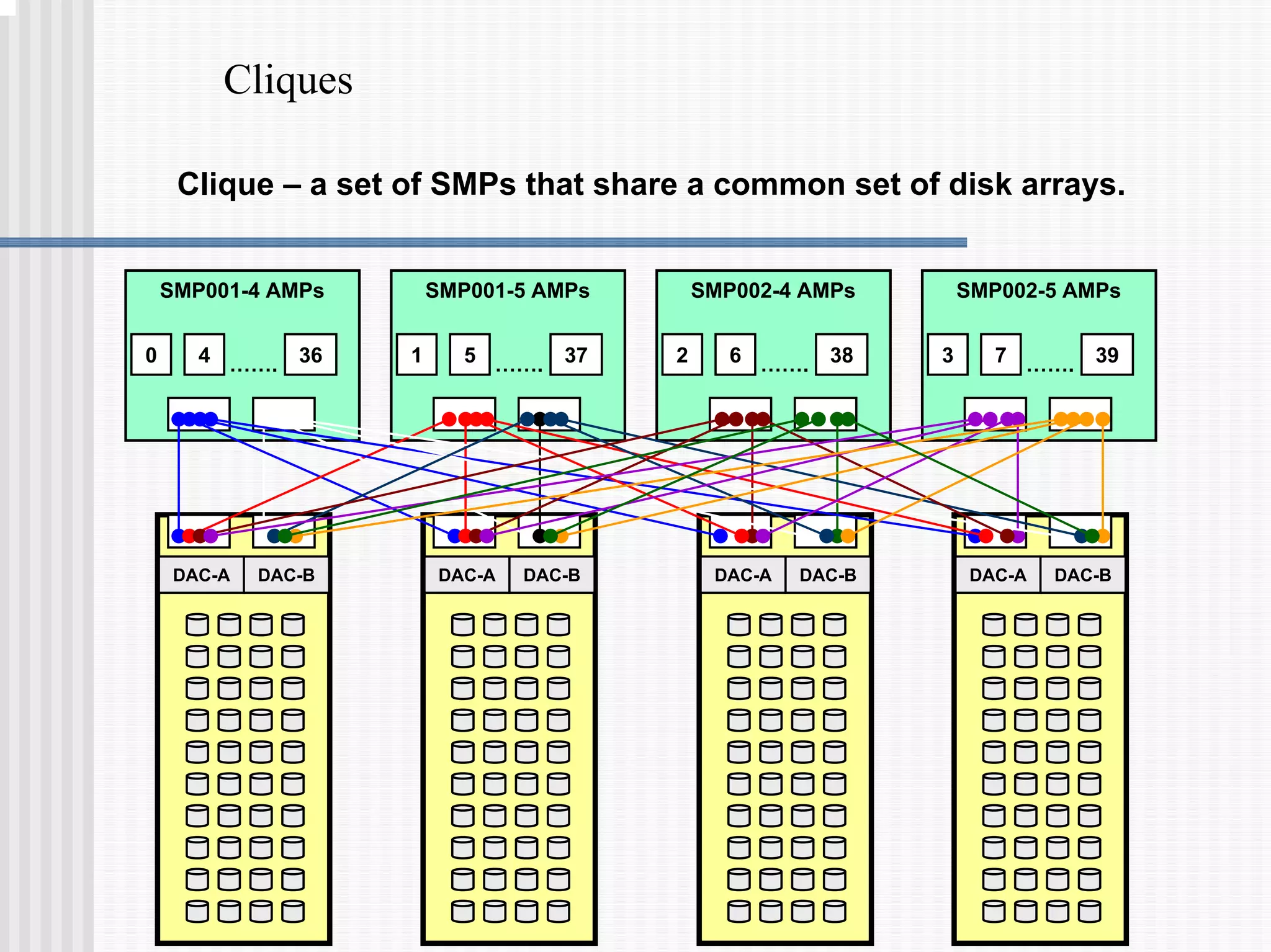
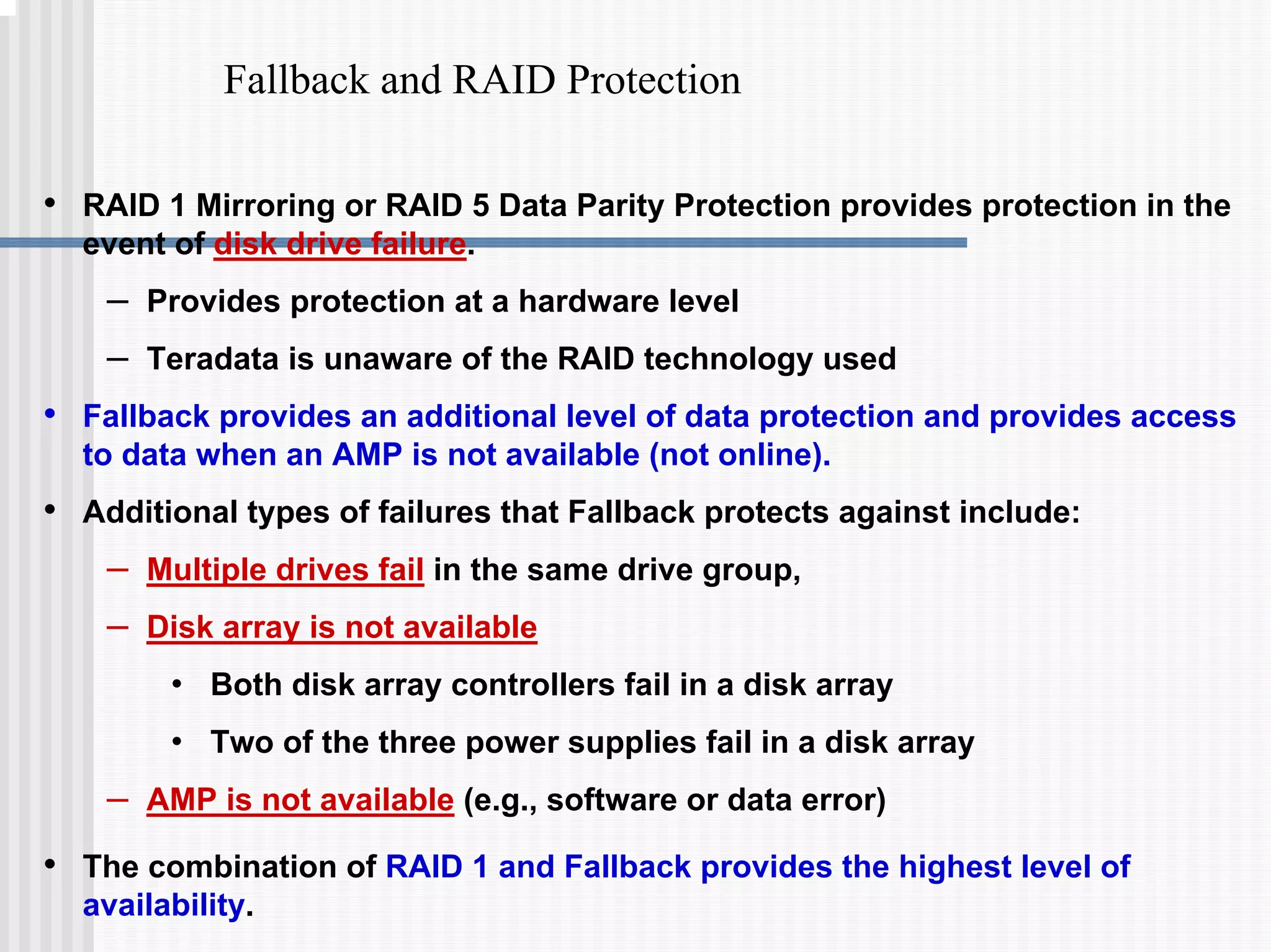
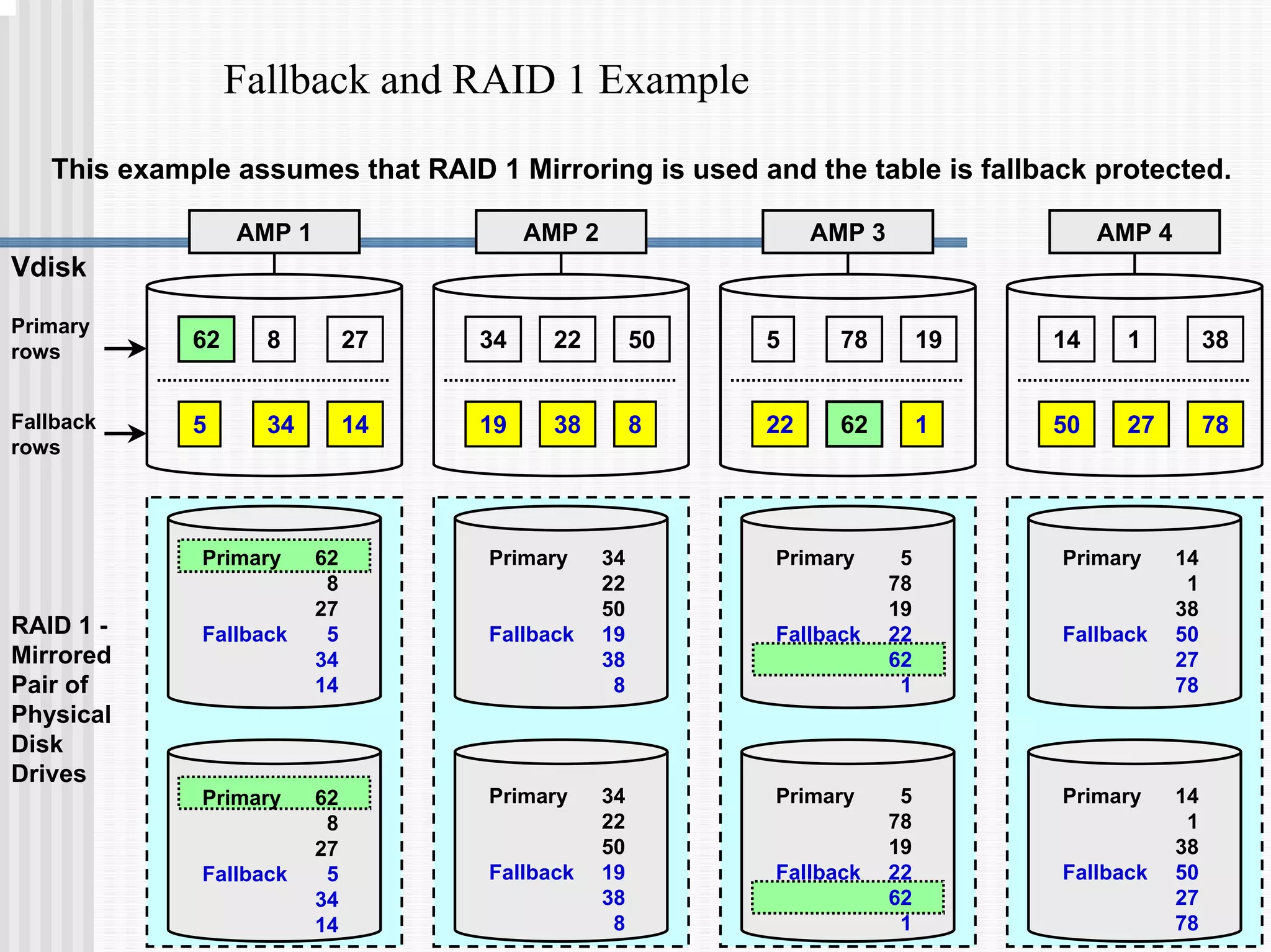
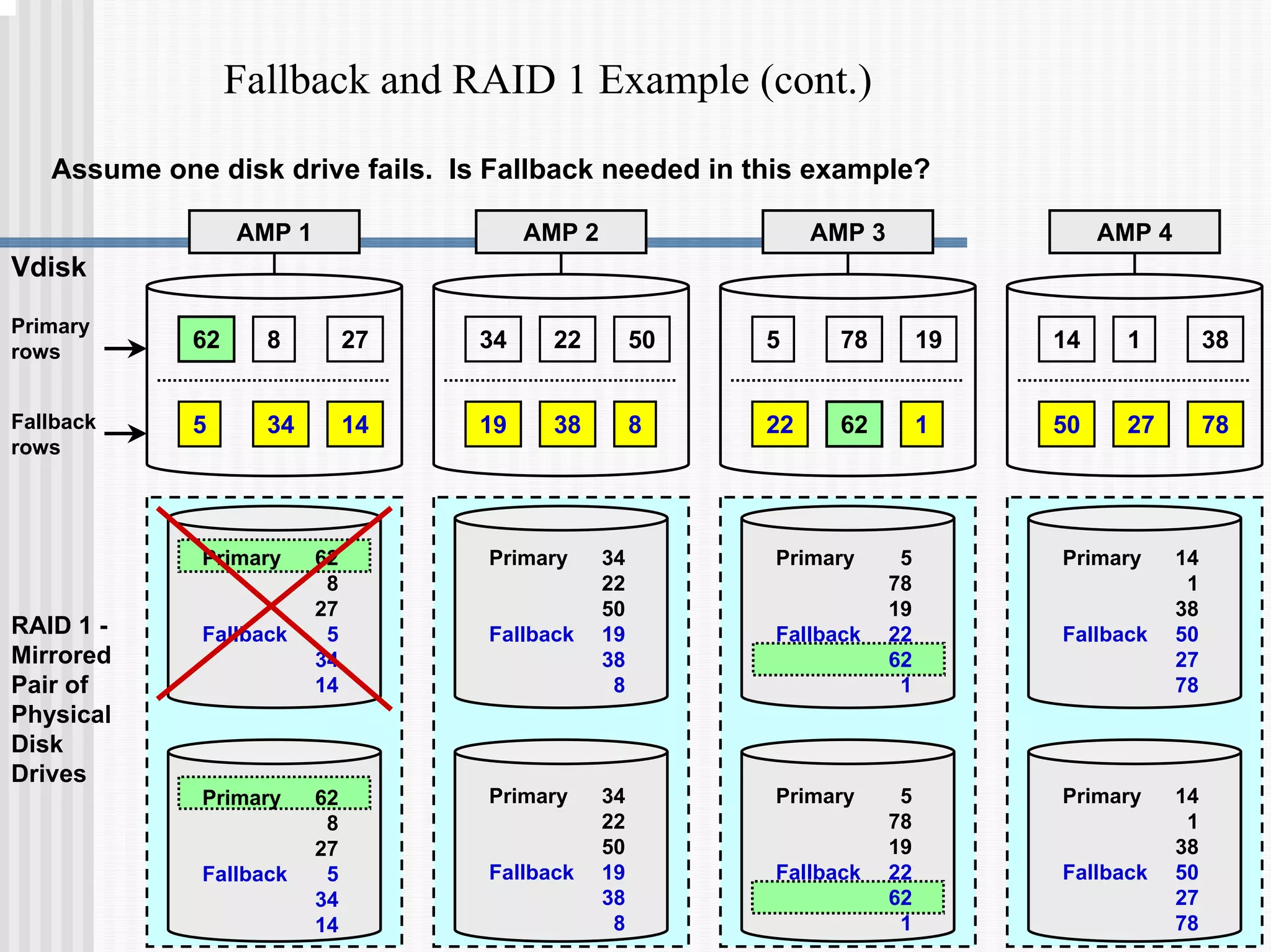
1) Disk arrays using RAID technologies like RAID 1 mirroring and RAID 5 parity to provide hardware-level data protection against disk failures.
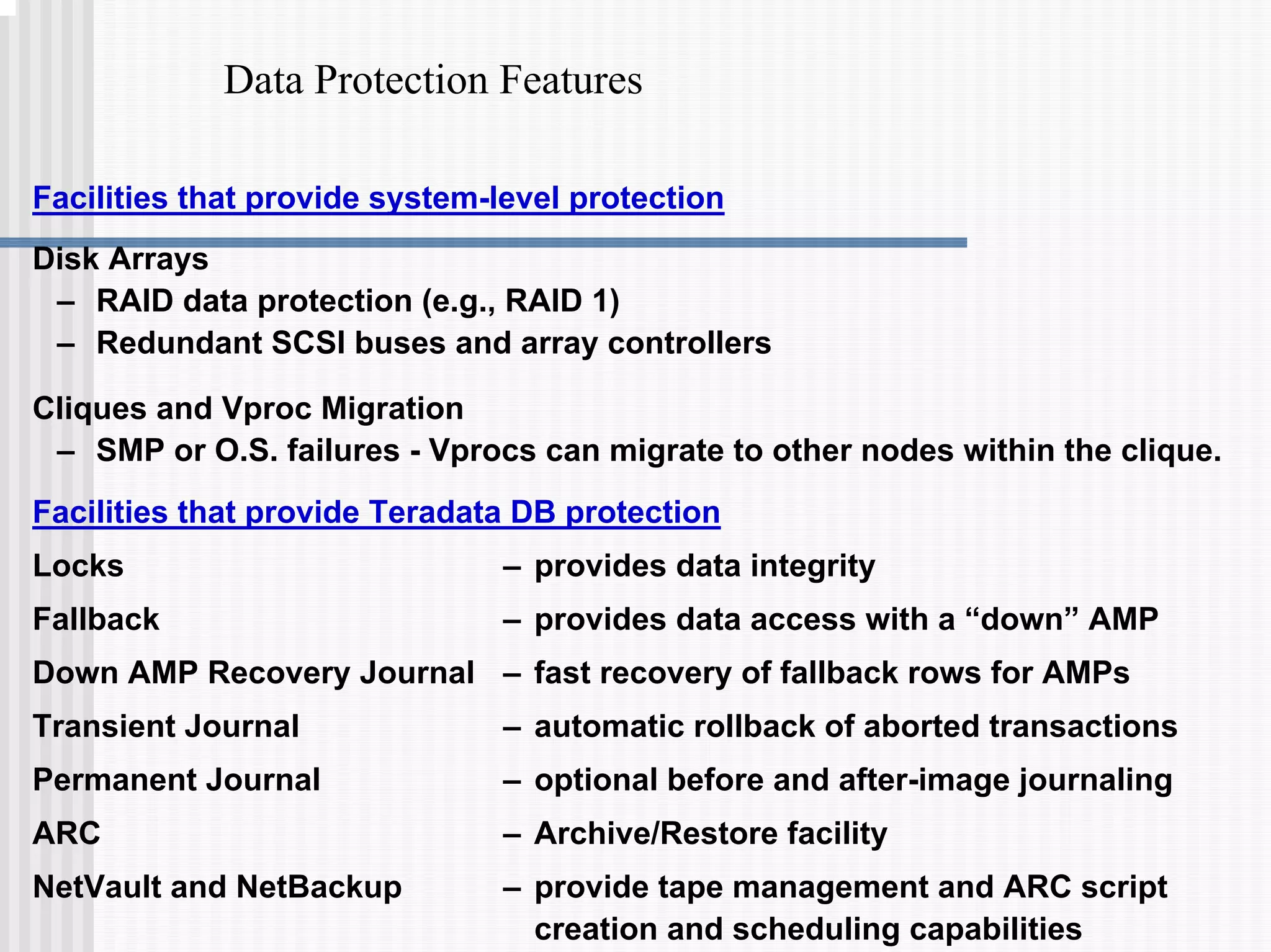
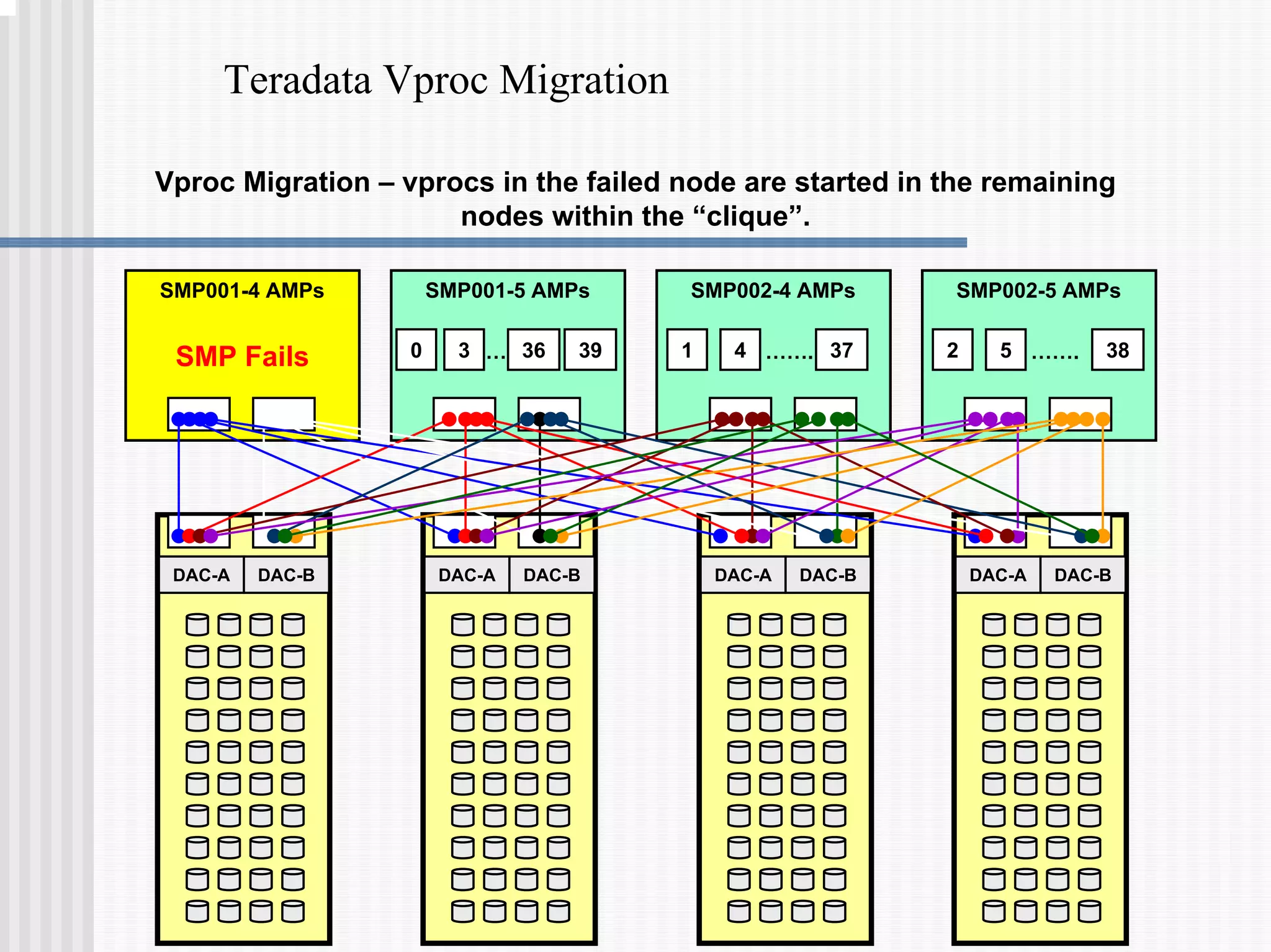
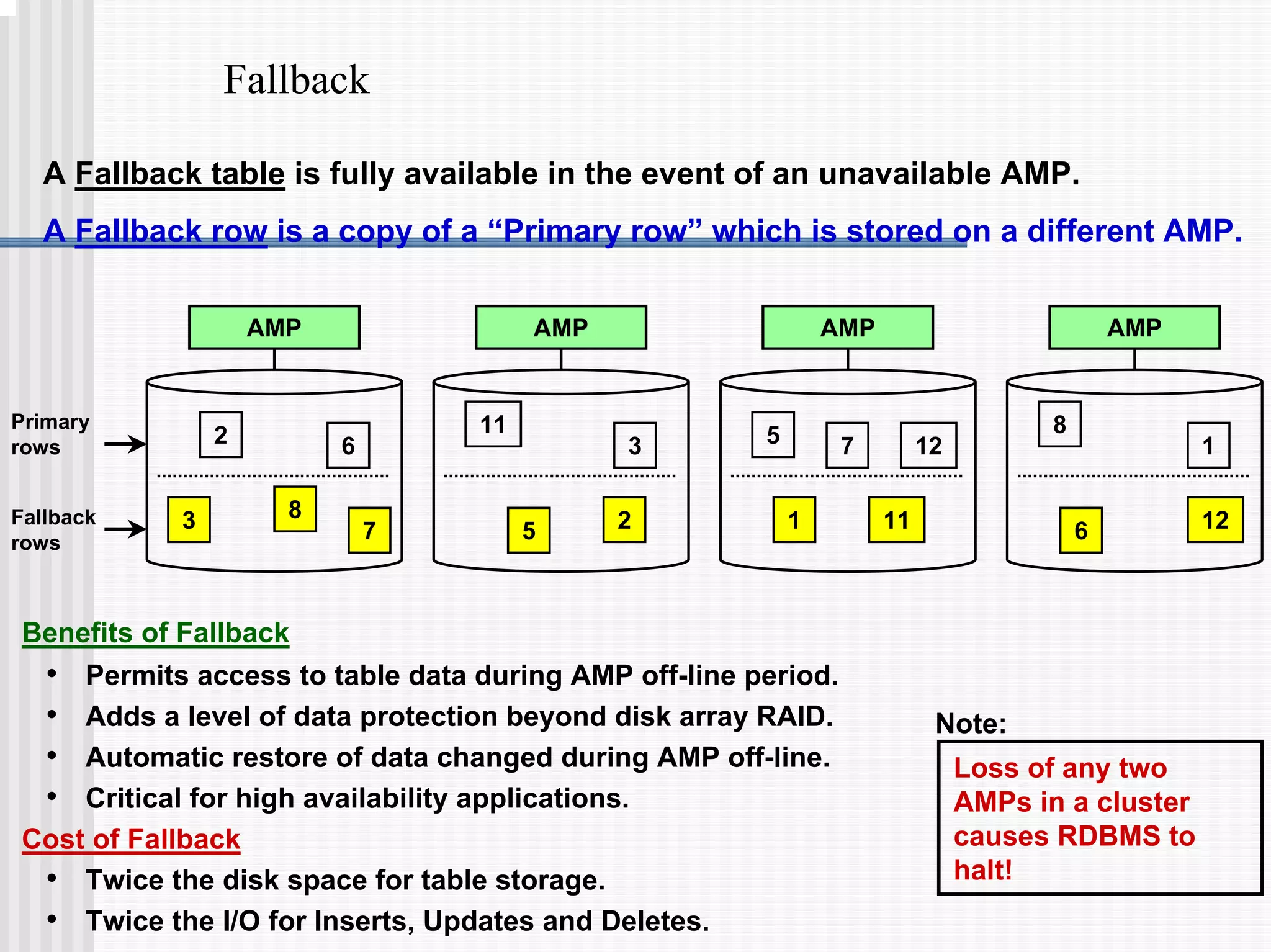
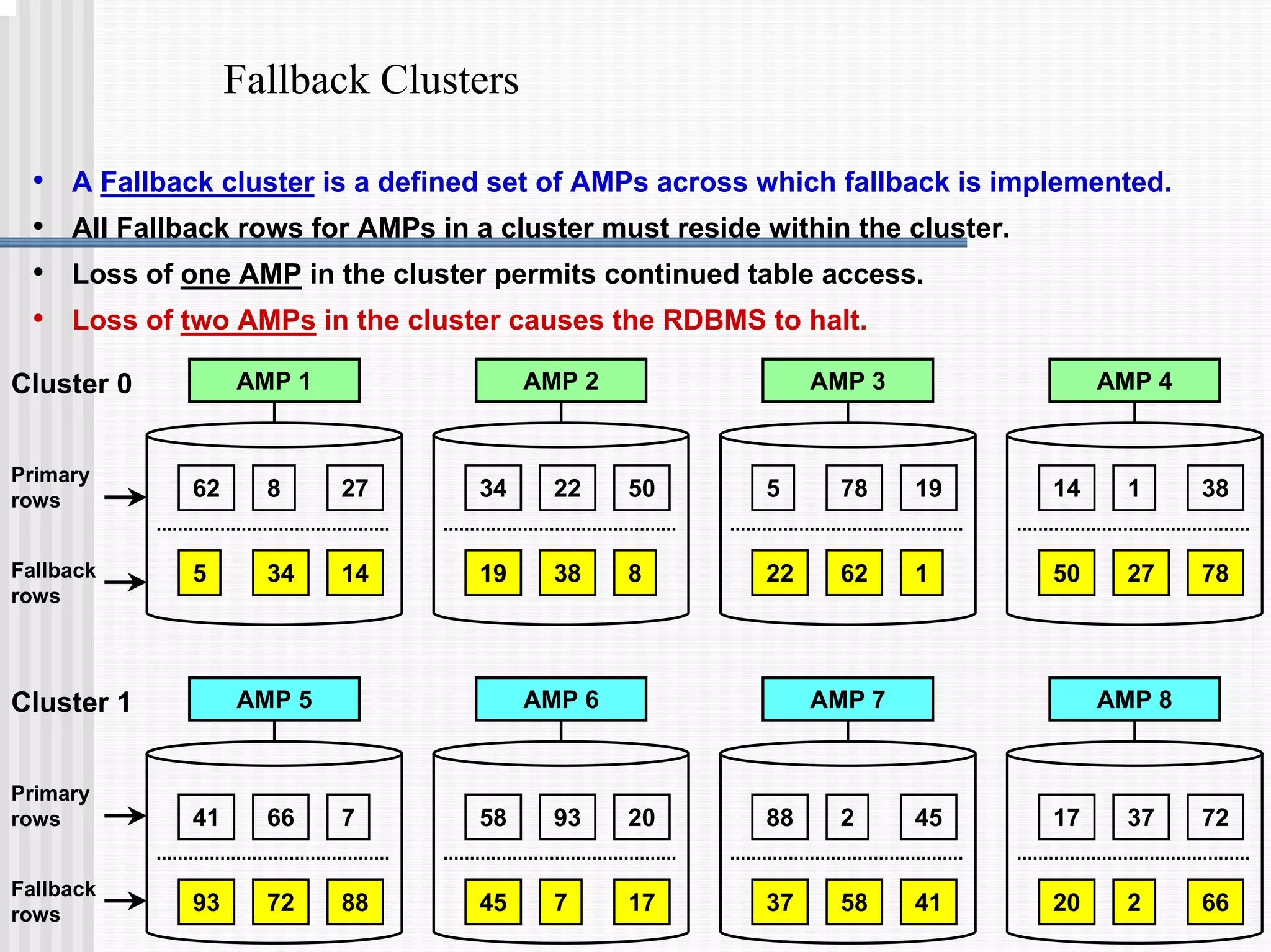
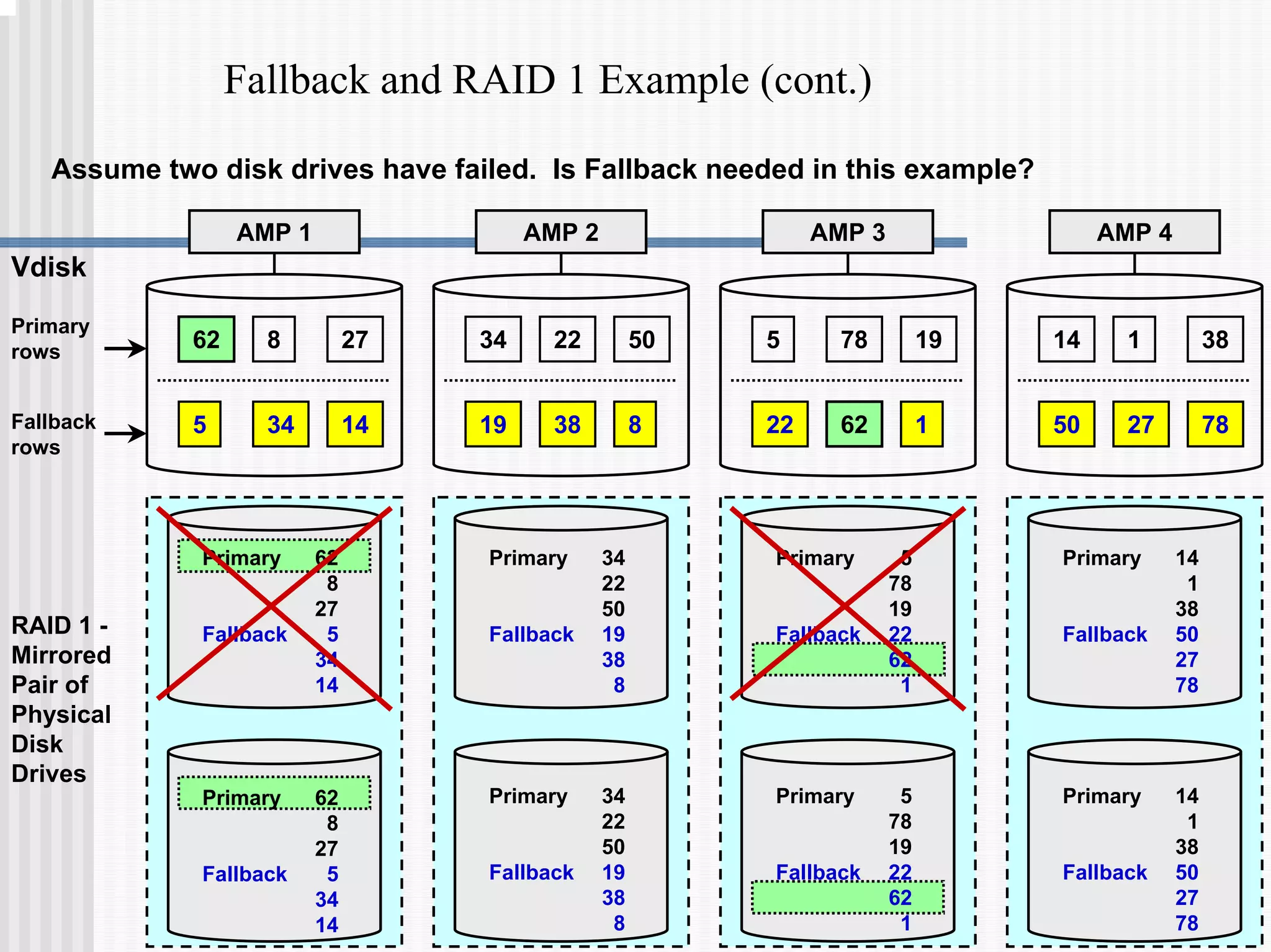
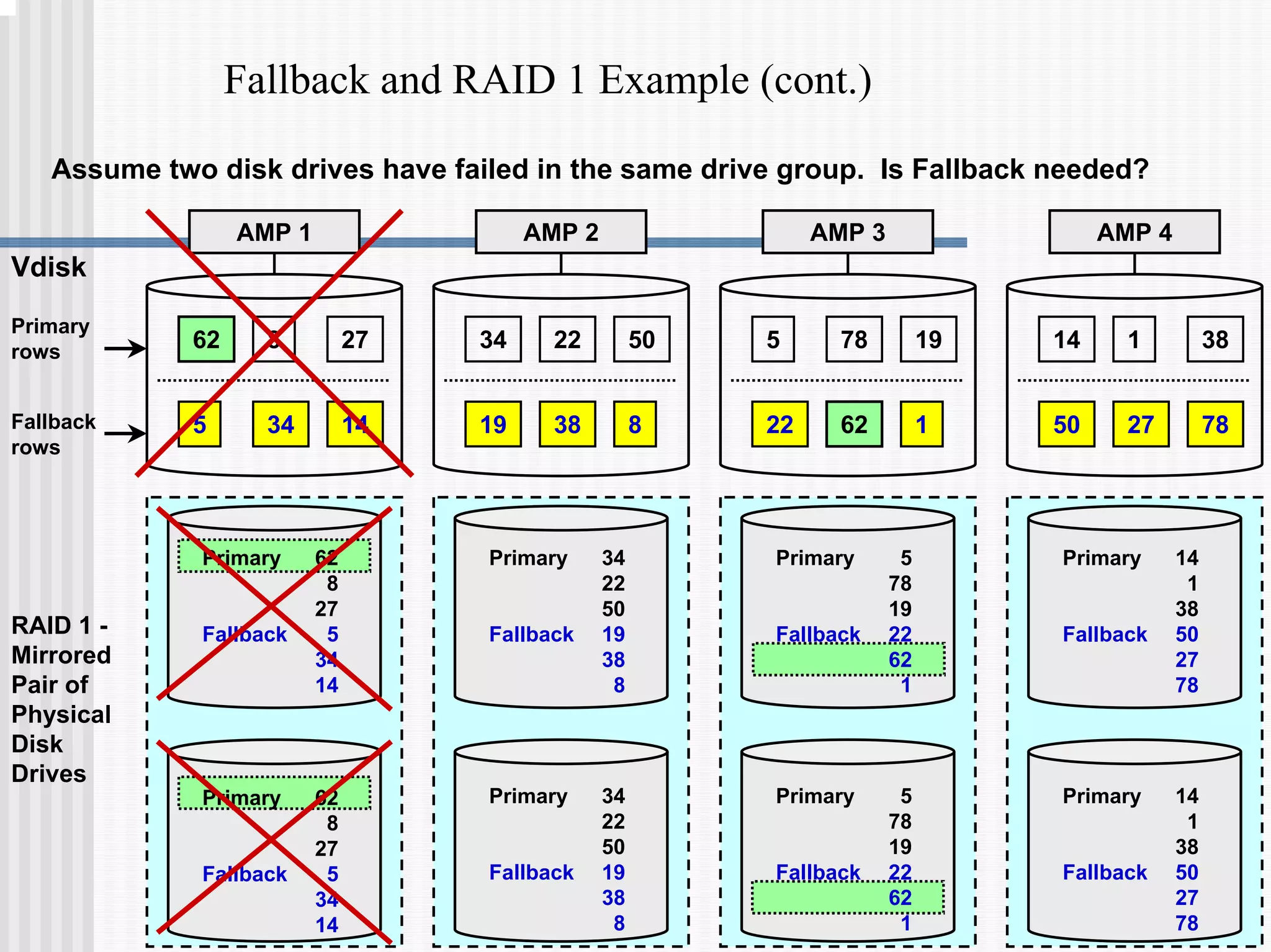
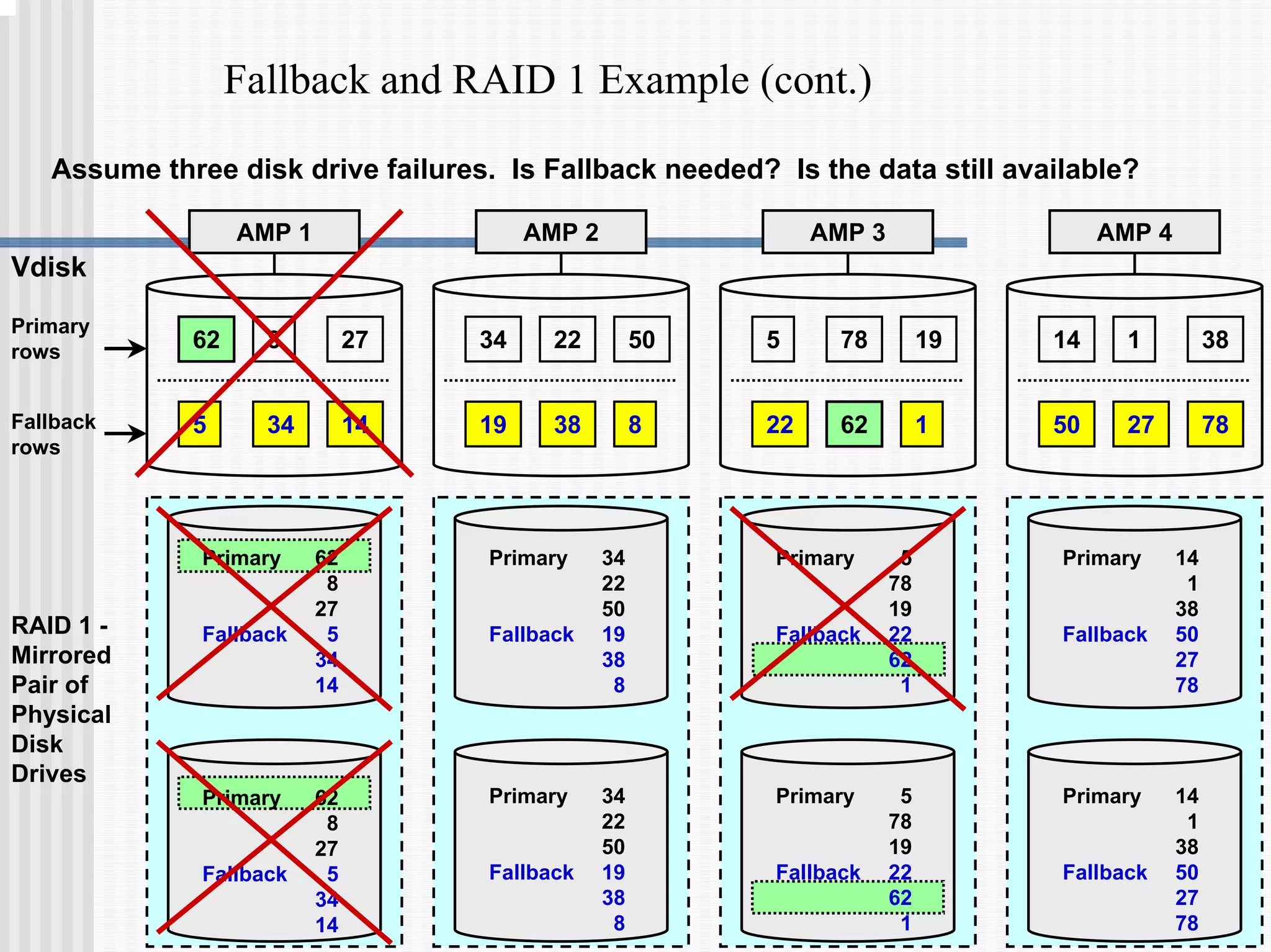
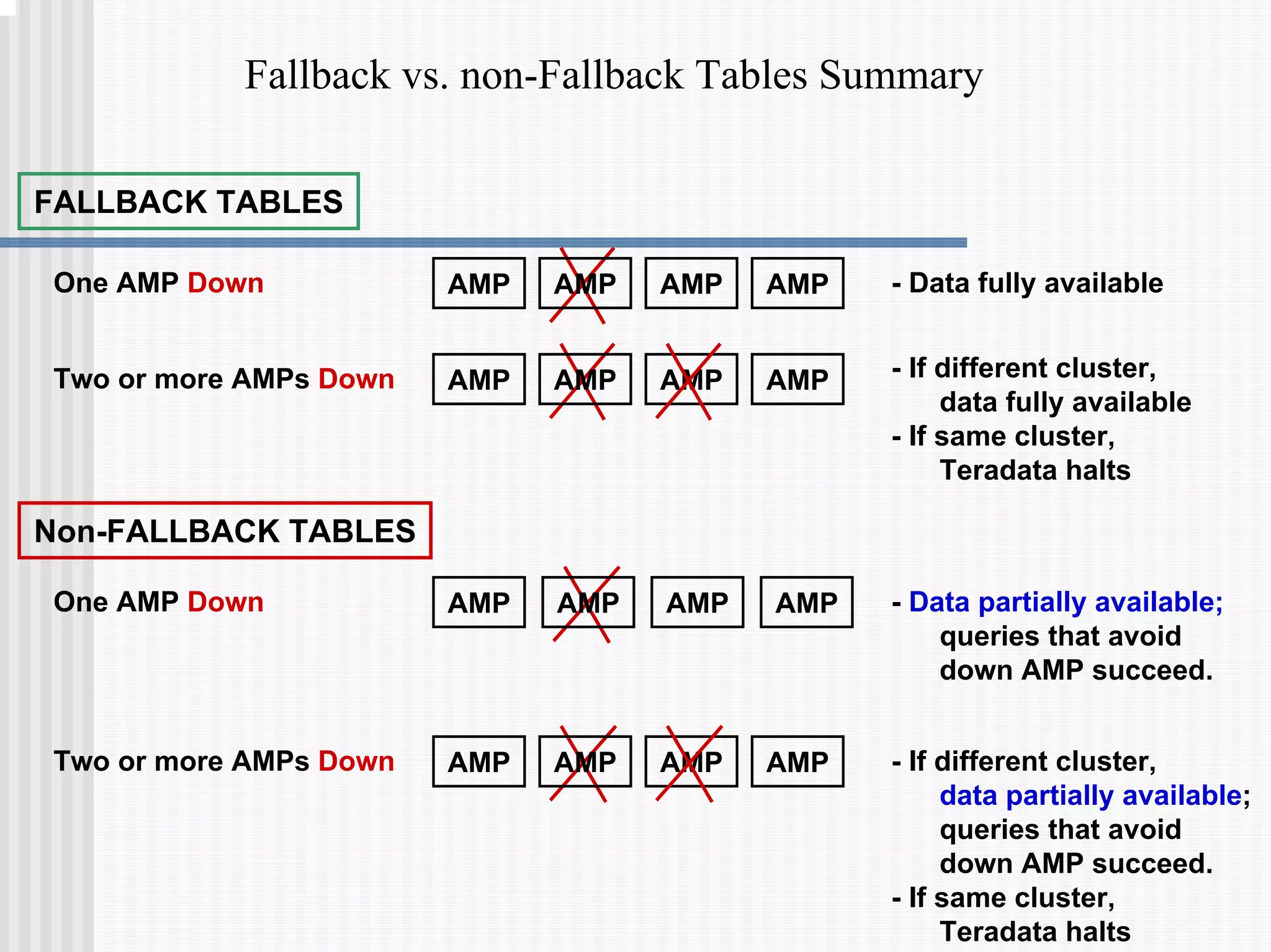
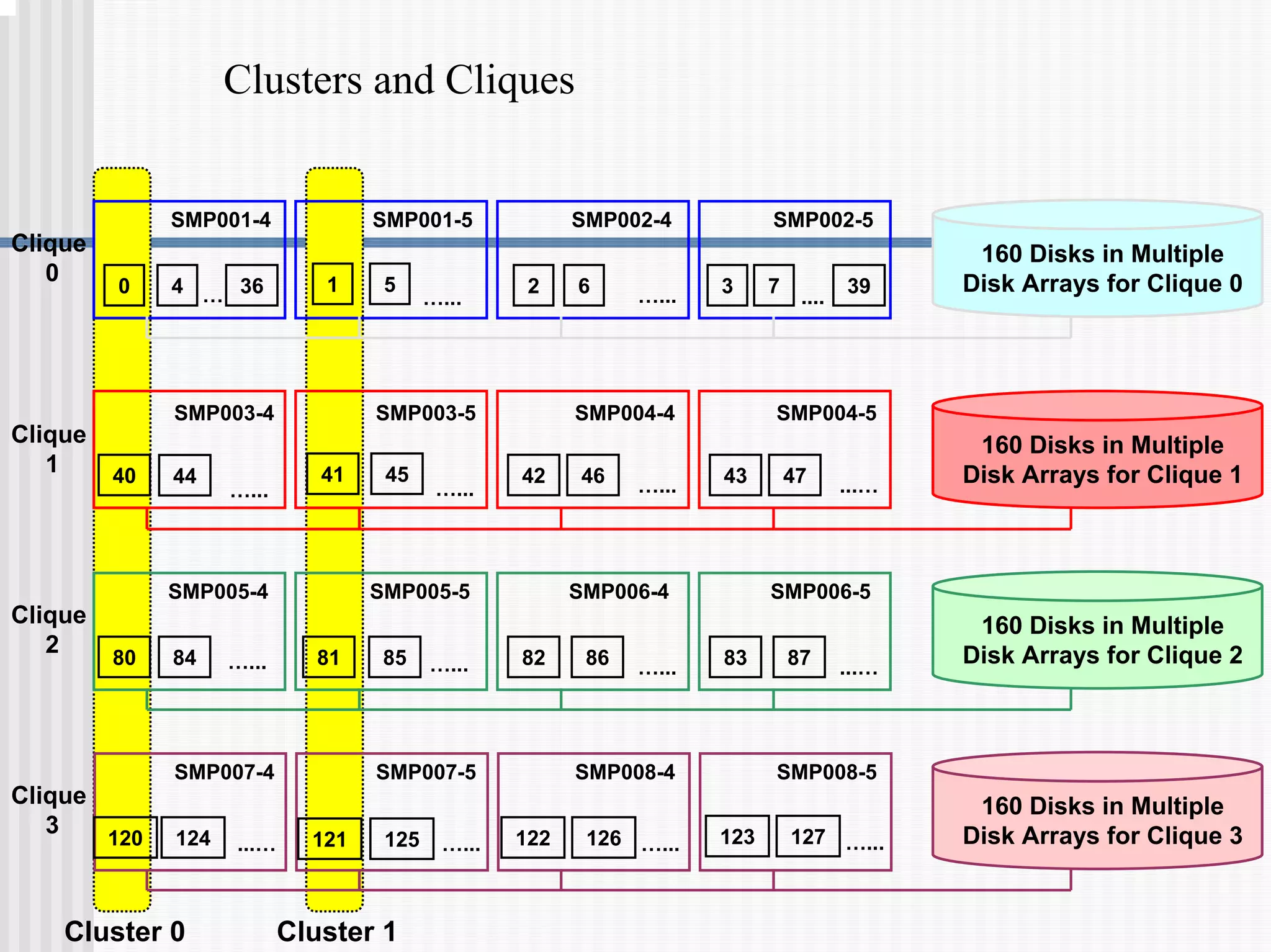
2) Fallback tables which store copies of rows on different processing nodes, allowing access if a node fails.
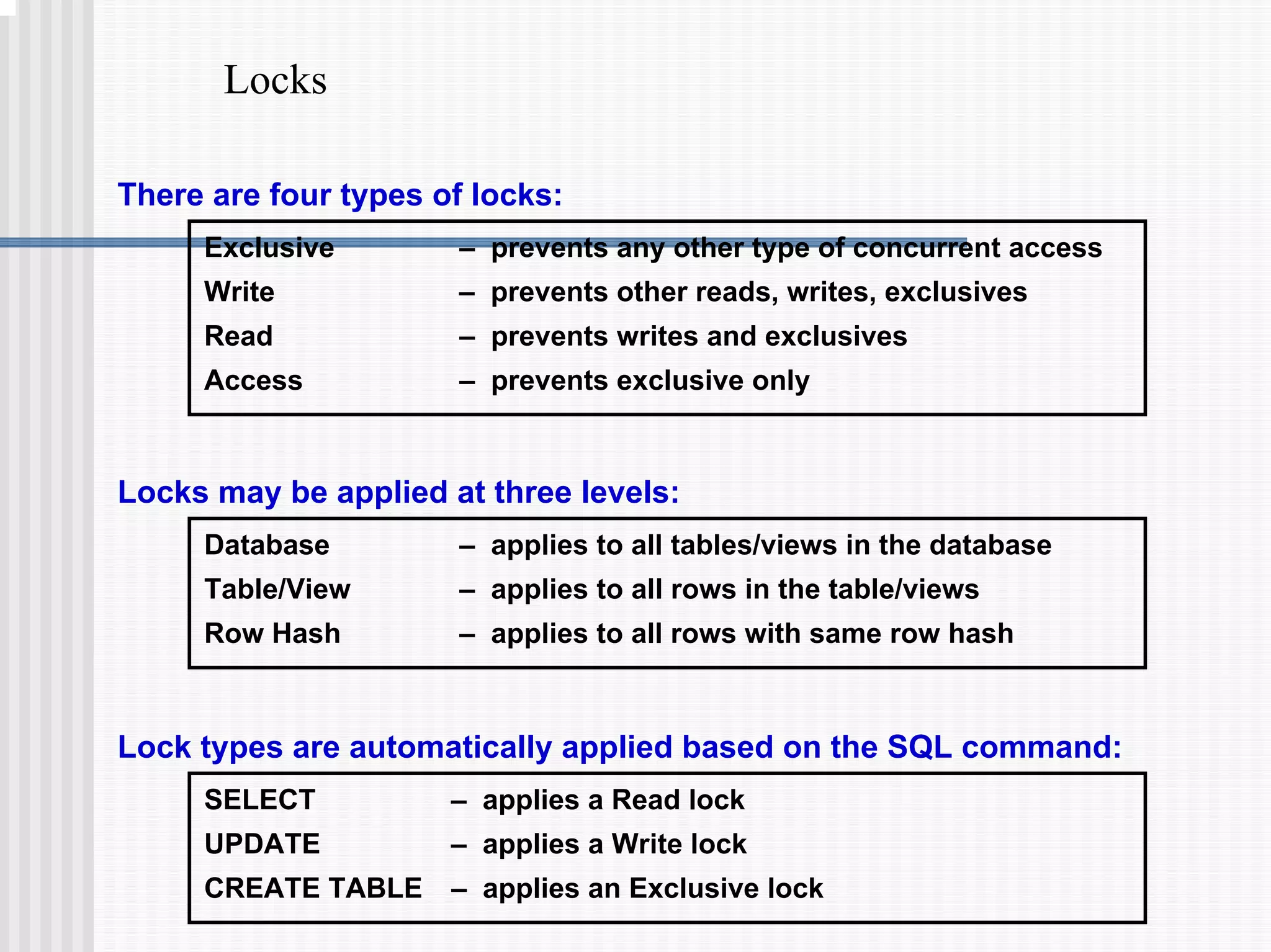
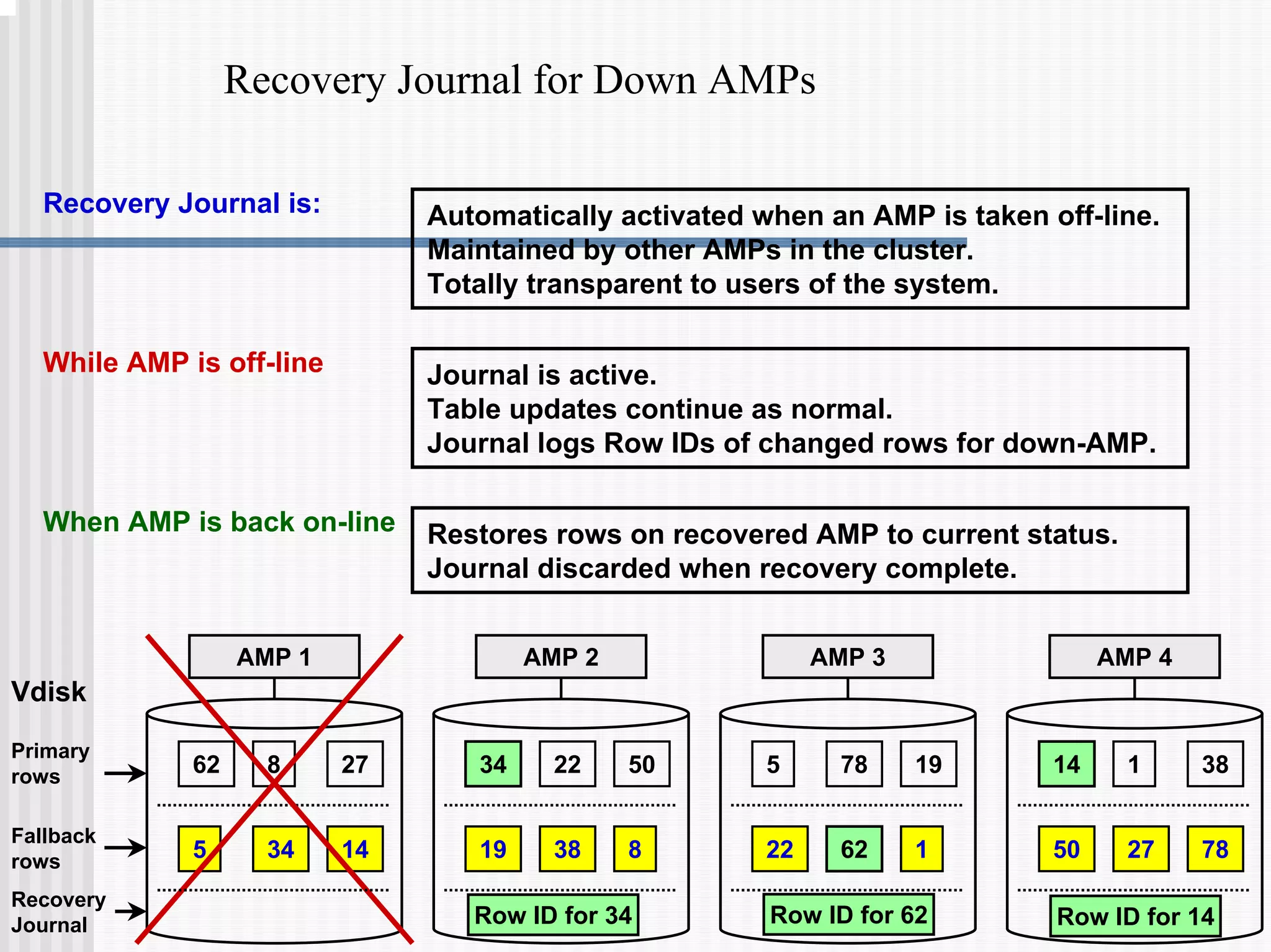
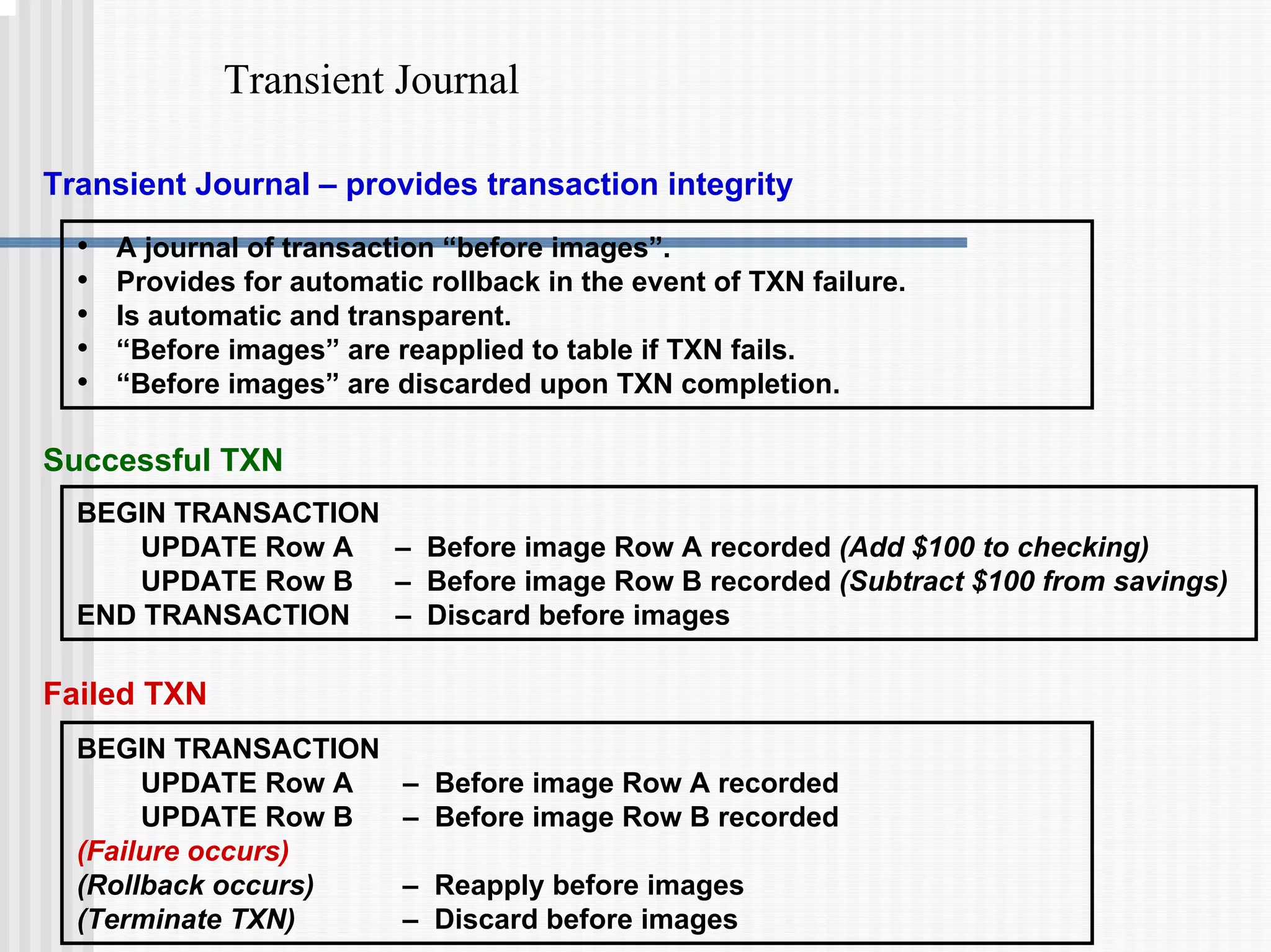
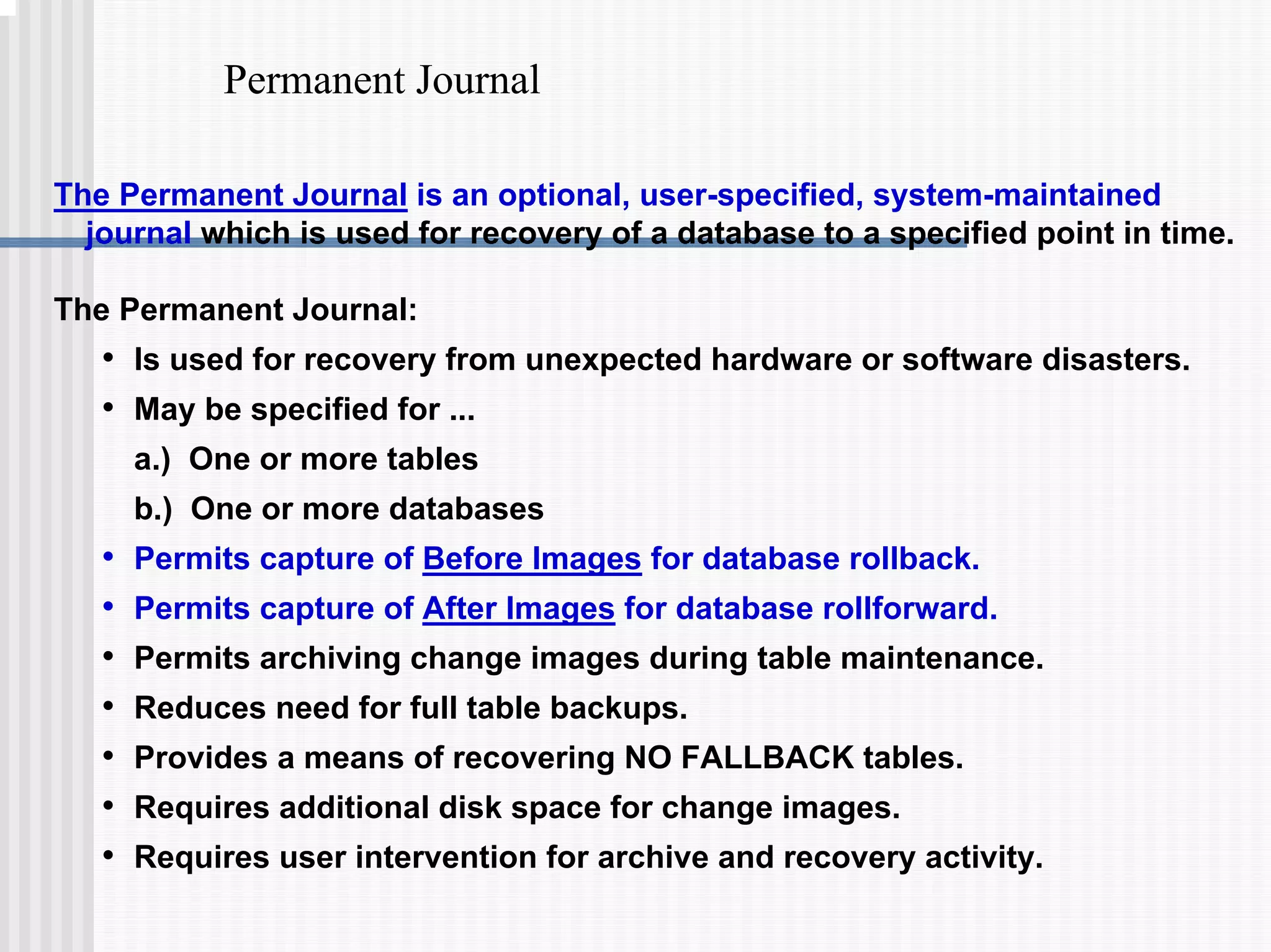
3) Transaction logging facilities like journals which allow rolled-back of aborted transactions or recovery after a failure.
4) Utilities for archiving and recovering data like ARC scripts.