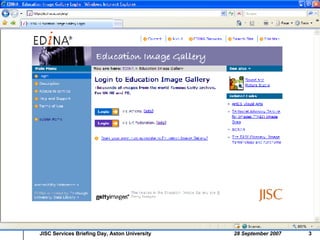
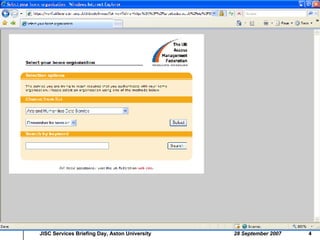
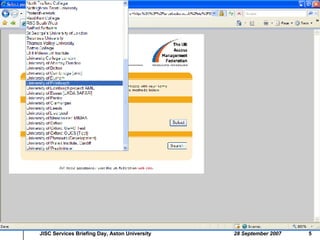
1. EDINA develops and hosts services based on licensed data content for academic institutions, using IP address authentication, Athens authentication, or UK federation authentication.
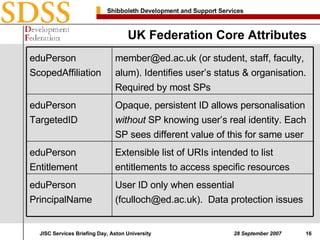
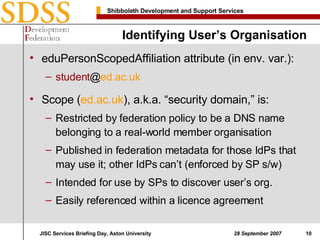
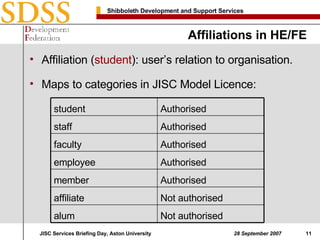
2. To determine if a user is authorized to access its services, EDINA checks the eduPersonScopedAffiliation attribute to identify the user's organization and matches it to a file mapping subscriber organizations to authorized services.
3. EDINA initially generated these mapping files manually but now automatically generates them from an existing database of subscription information keyed by organization codes, cross-referenced with organization DNS names in federation metadata.







![Contacts http://www.ukfederation.org.uk/ http://shibboleth.internet2.edu/ [email_address]](https://image.slidesharecdn.com/1345-1400-fiona-cullock-edina-case-study927/85/1345-1400-Fiona-Cullock-Edina-Case-Study-15-320.jpg)