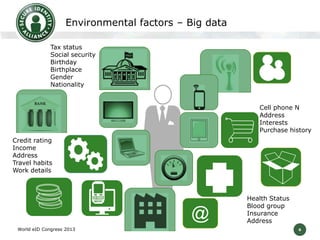
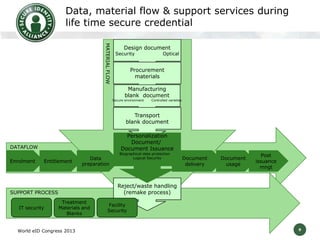
The Secure Identity Alliance is committed to helping governments deliver e-government services through secure identity technologies. It was founded in 2013 by leading document and service companies. The Alliance aims to accelerate e-government services by sharing best practices, promoting standardization, and providing guidance on security, identity, and privacy challenges. It has workgroups focused on digital identity and e-document security to define best practices and a security awareness model. The model will assess security solutions and provide recommendations to help members improve.