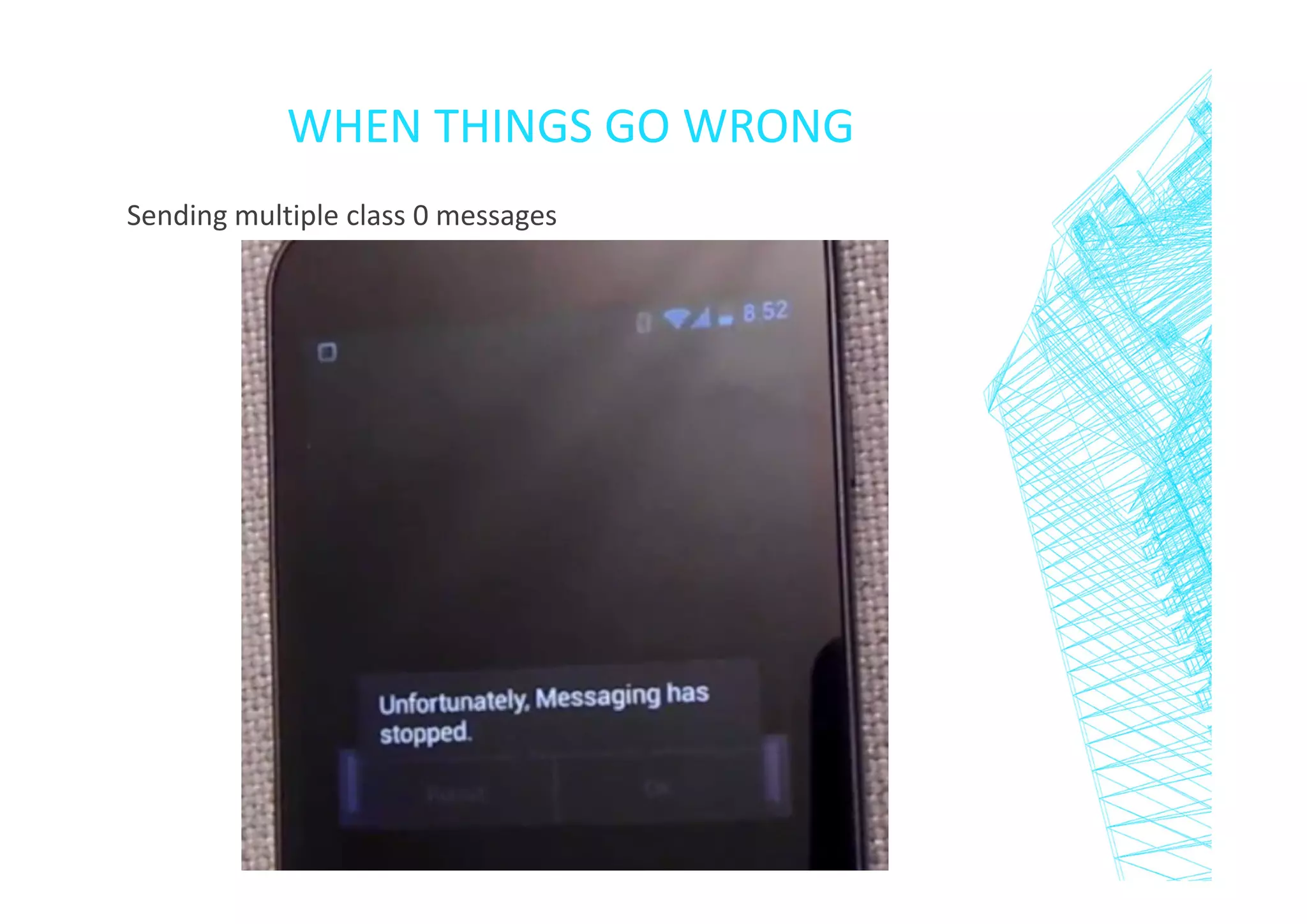
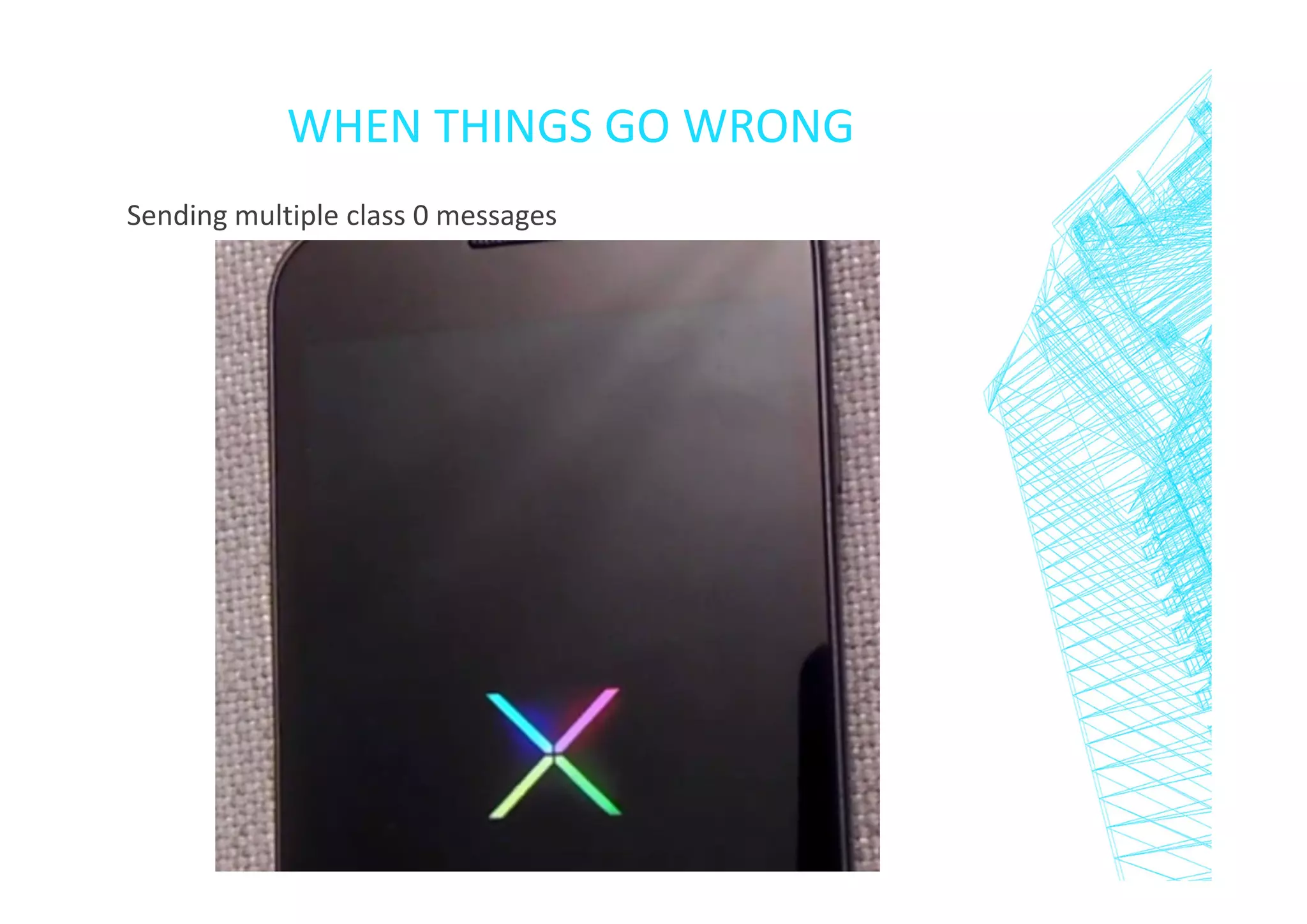
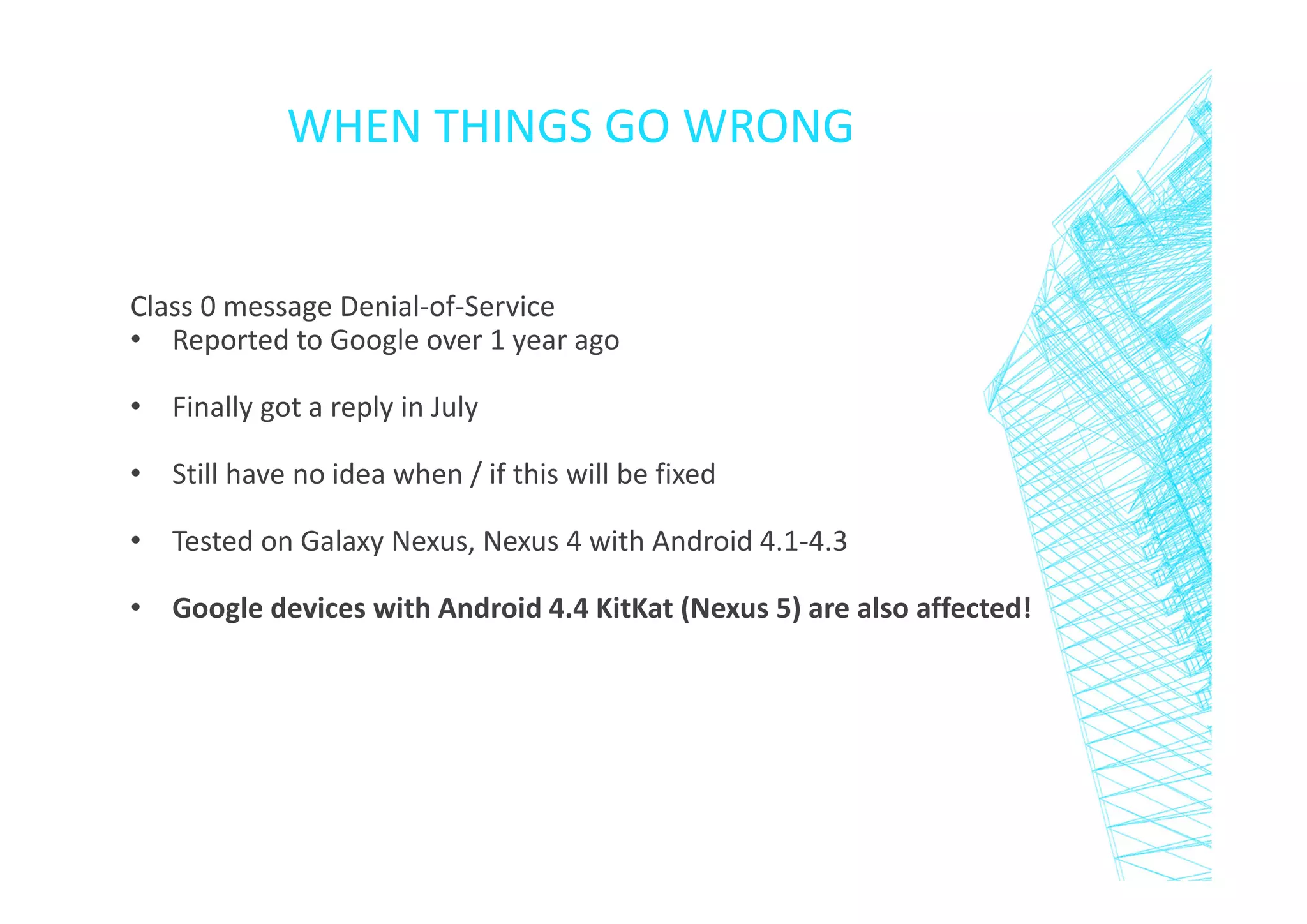
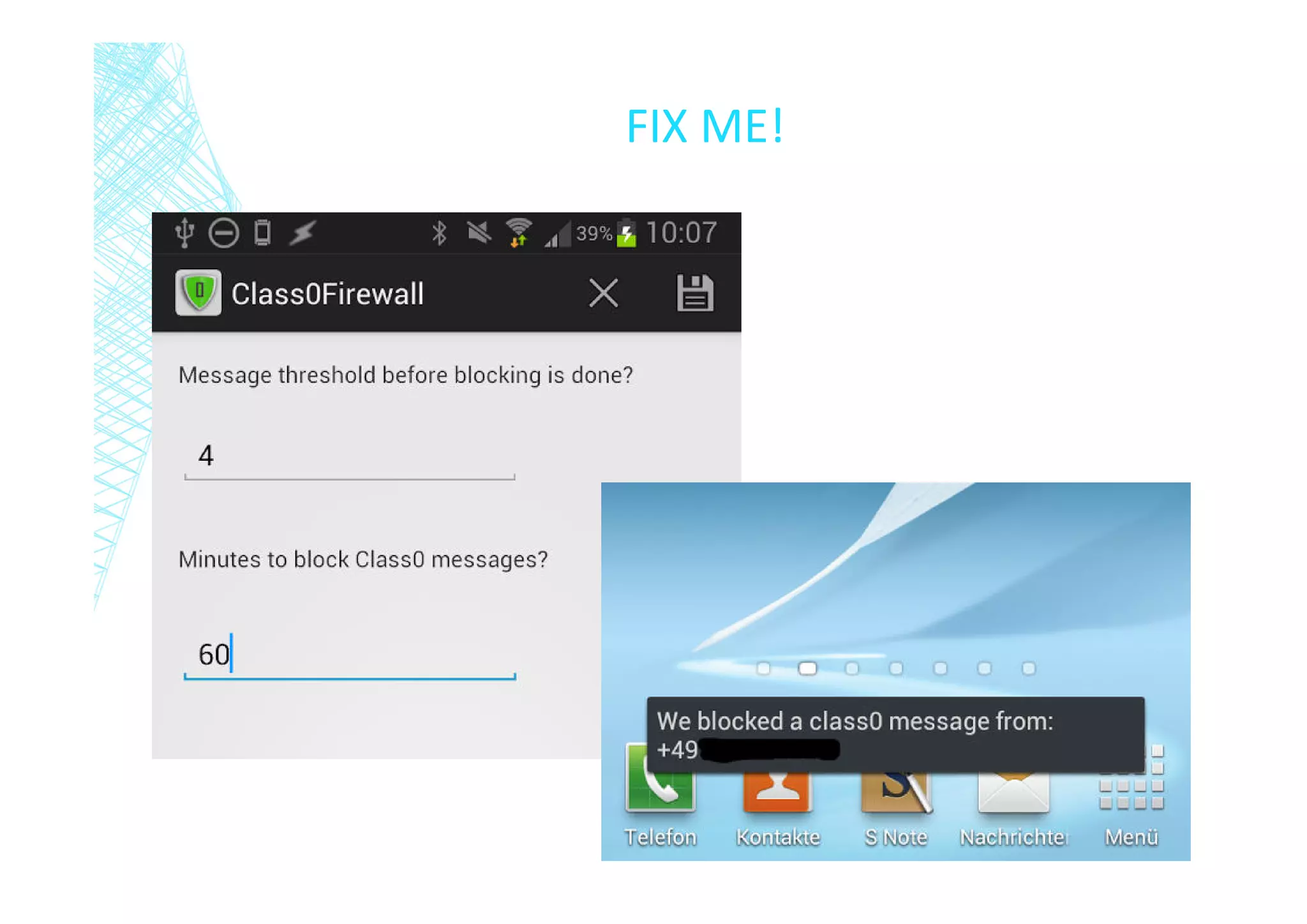
This document discusses short message service (SMS) and issues that can arise from improper SMS implementation. It begins with an introduction to SMS and how it works. It then describes ways to send different SMS message types for fun or malicious purposes, including "silent messages", service loads, and denial of service attacks using "flash messages". The document concludes by emphasizing the importance of thoroughly testing SMS implementations and provides an example of an Android application that helps prevent flash message attacks.










![WHEN THINGS GO WRONG
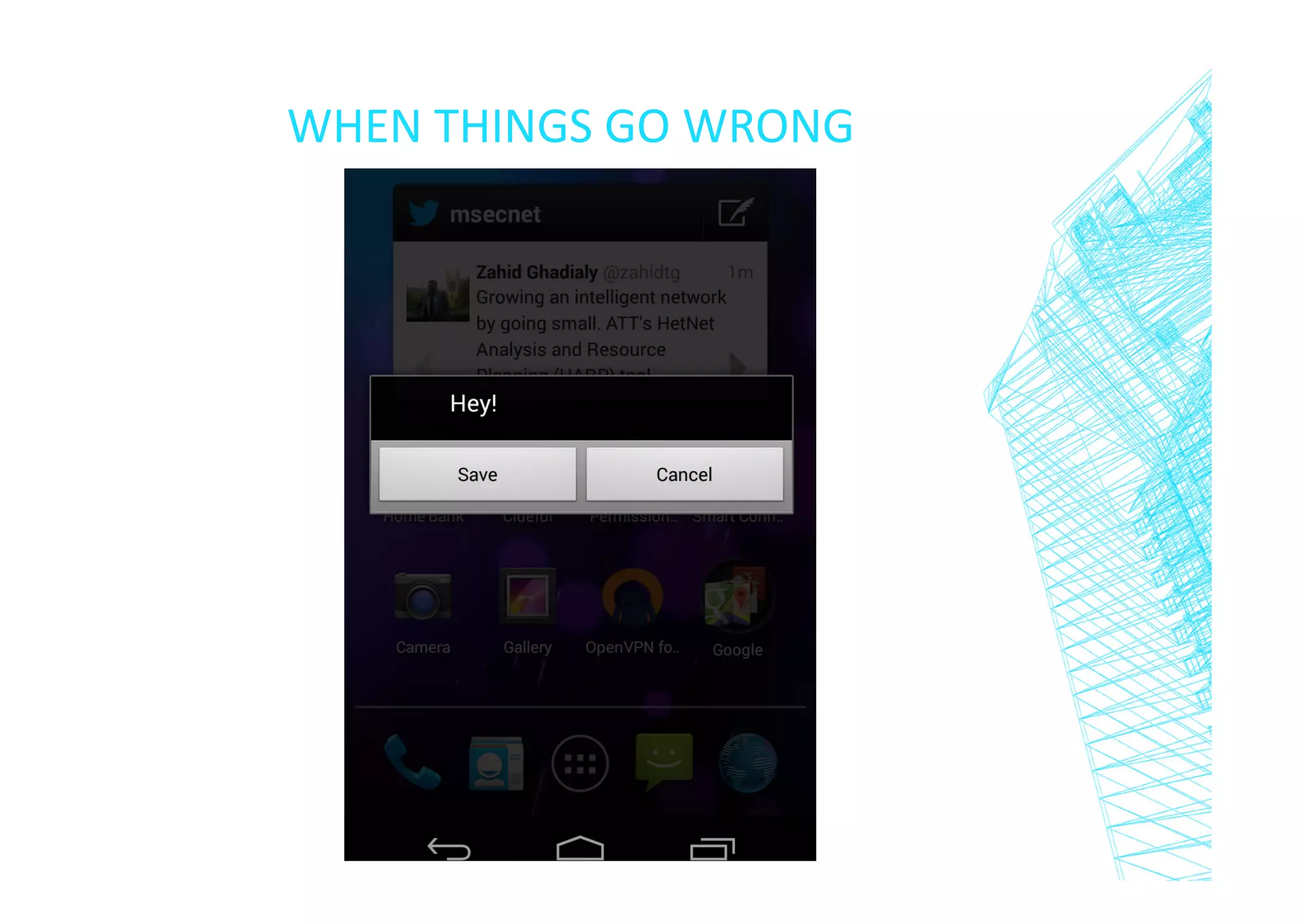
Class 0 /flash message defined in Data Coding Scheme (ETSI GSM 03.38)
DCS = 10 (hex)
When a mobile terminated message is class 0 and the MS has the
capability of displaying short messages, the MS shall display the
message immediately […]
The message shall not be automatically stored in the SIM or ME](https://image.slidesharecdn.com/0class2dos-131218121124-phpapp01/75/DefCamp-2013-0Class2DOS-14-2048.jpg)