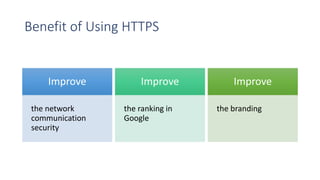
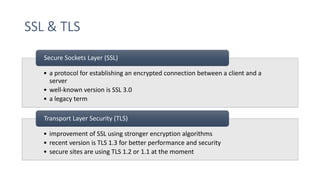
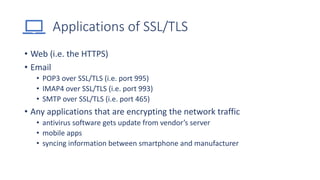
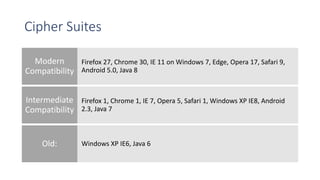
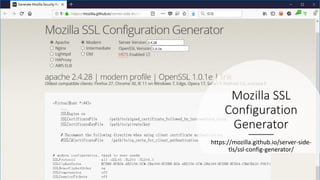
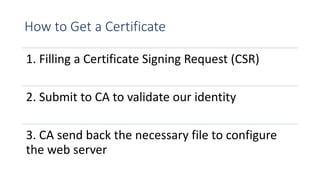
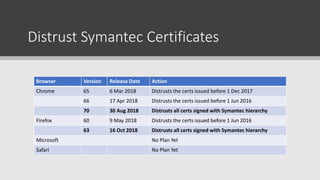
SSL/TLS are cryptographic protocols that secure network communications and establish encrypted connections between clients and servers. HTTPS ensures privacy and integrity for web browsing using SSL/TLS to encrypt communication between browsers and websites. Digital certificates issued by certificate authorities (CAs) are required for HTTPS and validate website identities. Regular testing and updates are needed to address SSL/TLS vulnerabilities and configuration issues to ensure secure encrypted connections.