The document discusses several types of errors found using static analysis on the NetXMS open source project codebase. It describes 4 examples of 64-bit errors where pointers are incorrectly cast to 32-bit types. It also mentions errors handling unsigned types like sockets, half-cleared buffers due to misunderstanding string sizes, copy-paste errors, uninitialized variables, null pointer dereferences, and incorrect variable type usage with variadic functions. The author encourages the NetXMS developers to use the static analysis tool to find and address these kinds of issues in their code.




![{
size_t i;
uint8_t *in = (uint8_t*) data;
for( i=len-1; i>=0; i-- ) {
if ( in[i] == '0' ) {
return snprintf( str, size, "%s", in );
}
}
....
}
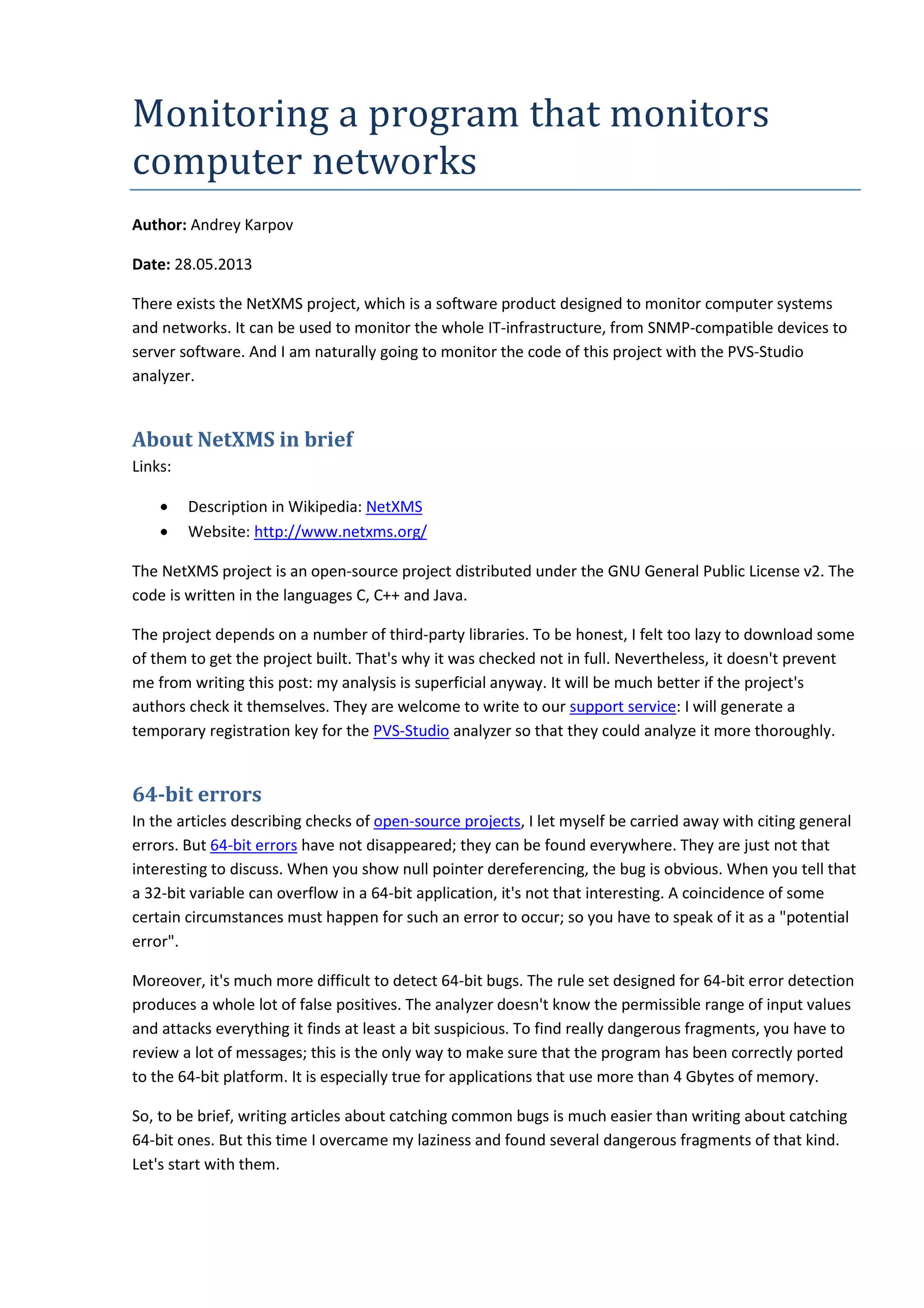
V547 Expression 'i >= 0' is always true. Unsigned type value is always >= 0. ipfix.c 488
The 'i' variable has the size_t type. It means that the check "i>=0" is pointless. If zero is not found on the
stack, the function will start reading memory far outside the array's boundaries. Consequences of this
may be very diverse.
One more error when handling unsigned types
bool CatalystDriver::isDeviceSupported(....)
{
DWORD value = 0;
if (SnmpGet(snmp->getSnmpVersion(), snmp,
_T(".1.3.6.1.4.1.9.5.1.2.14.0"),
NULL, 0, &value, sizeof(DWORD), 0)
!= SNMP_ERR_SUCCESS)
return false;
// Catalyst 3550 can return 0 as number of slots
return value >= 0;
}
V547 Expression 'value >= 0' is always true. Unsigned type value is always >= 0. catalyst.cpp 71](https://image.slidesharecdn.com/0201netxms-130729070042-phpapp02/75/Monitoring-a-program-that-monitors-computer-networks-6-2048.jpg)
![Half-cleared buffers
One of the most common error patterns is confusion of WCHAR strings' sizes. You can find quite a
number of examples in our bug database.
typedef WCHAR TCHAR, *PTCHAR;
static BOOL MatchProcess(....)
{
....
TCHAR commandLine[MAX_PATH];
....
memset(commandLine, 0, MAX_PATH);
....
}
V512 A call of the 'memset' function will lead to underflow of the buffer 'commandLine'. procinfo.cpp
278
The TCHAR type is expanded into the WCHAR type. The number of characters in the array
'commandLine' equals the value MAX_PATH. The size of this array is 'MAX_PATH * sizeof(TCHAR). The
'memset' function handles bytes. It means that the mechanism needed to correctly clear the buffer
should look like this:
memset(commandLine, 0, MAX_PATH * sizeof(TCHAR));
An even better way is to make it like this:
memset(commandLine, 0, sizeof(commandLine));
The CToolBox class is sick in the same way:
typedef WCHAR TCHAR, *PTCHAR;
#define MAX_TOOLBOX_TITLE 64
TCHAR m_szTitle[MAX_TOOLBOX_TITLE];
CToolBox::CToolBox()
{
memset(m_szTitle, 0, MAX_TOOLBOX_TITLE);
}
V512 A call of the 'memset' function will lead to underflow of the buffer 'm_szTitle'. toolbox.cpp 28](https://image.slidesharecdn.com/0201netxms-130729070042-phpapp02/75/Monitoring-a-program-that-monitors-computer-networks-7-2048.jpg)

![The expression (CF_AUTO_UNBIND | CF_AUTO_UNBIND) is very strange. It seems that two different
constants should be used here.
Unexpected optimization
void I_SHA1Final(....)
{
unsigned char finalcount[8];
....
memset(finalcount, 0, 8);
SHA1Transform(context->state, context->buffer);
}
V597 The compiler could delete the 'memset' function call, which is used to flush 'finalcount' buffer. The
RtlSecureZeroMemory() function should be used to erase the private data. sha1.cpp 233
In functions related to cryptography, it is an accepted practice to clear temporary buffers. If you don't
do that, consequences may be interesting: for instance, a fragment of classified information may be
unintentionally sent to the network. Read the article "Overwriting memory - why?" to find out the
details.
The function memset() is often used to clear memory. It is incorrect. If the array is not being used after
the clearing, the compiler may delete the function memset() for the purpose of optimization. To prevent
this you should use the function RtlSecureZeroMemory().
Using uninitialized variables
Many programmers are convinced that use of uninitialized variables is the most annoying and frequent
bug. Judging by my experience of checking various projects, I don't believe it's true. This bug is very
much discussed in books and articles. Thanks to that, everybody knows what uninitialized variables are,
what is dangerous about them, how to avoid and how to find them. But personally I feel that much
more errors are caused, say, through using Copy-Paste. But, of course, it doesn't mean that uninitialized
variables are defeated. Here they are.
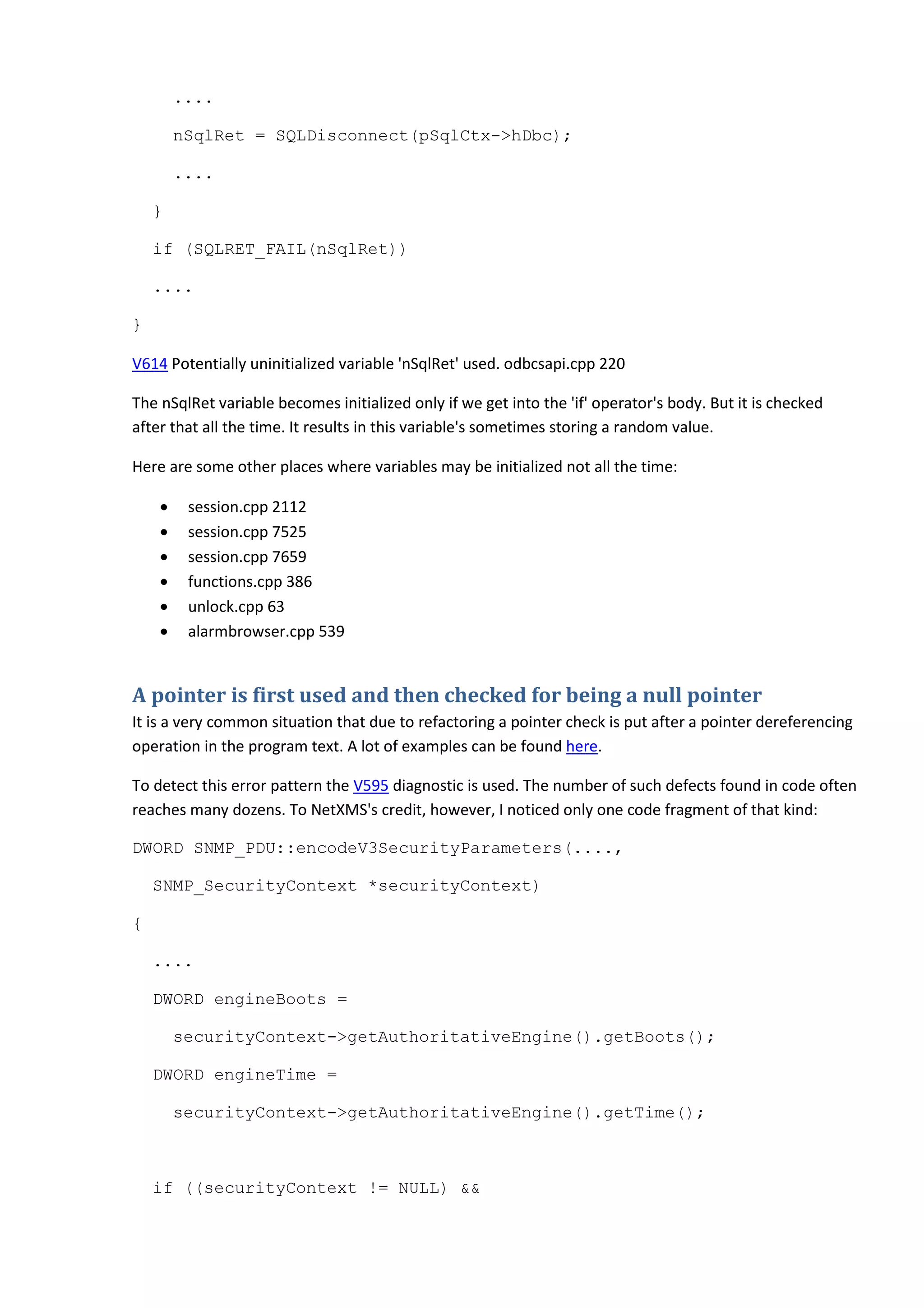
int OdbcDisconnect(void* pvSqlCtx)
{
....
SQLRETURN nSqlRet;
....
if (nRet == SUCCESS)
{](https://image.slidesharecdn.com/0201netxms-130729070042-phpapp02/75/Monitoring-a-program-that-monitors-computer-networks-9-2048.jpg)
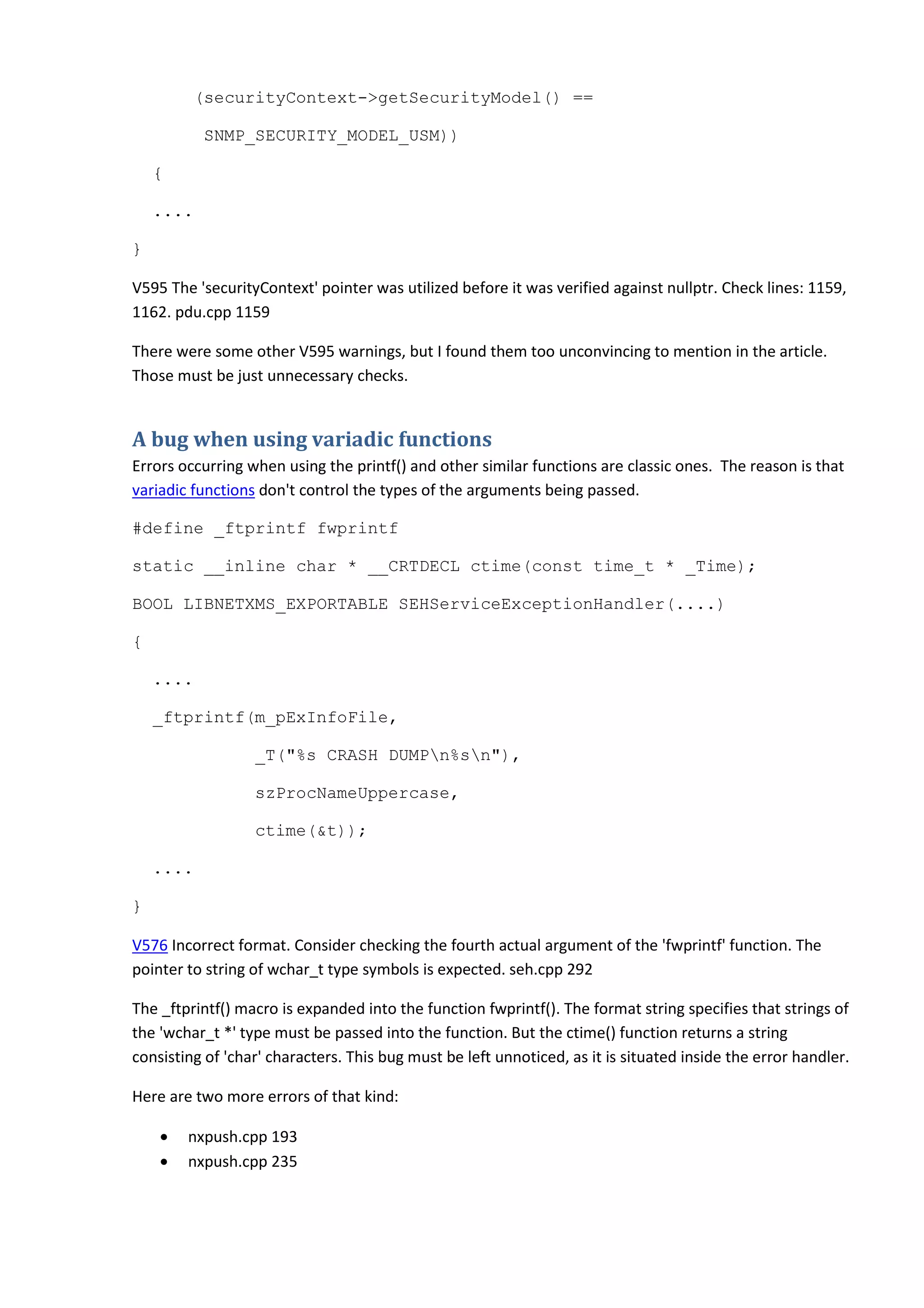
![It is not taken into account that the 'new' operator throws exceptions
when there is memory shortage
The 'new' operator earlier used to return 'NULL' when it failed to allocate memory. Now it throws an
exception. Many programs don't take this change into account. It doesn't matter sometimes, but in
some cases it may cause failures. Take a look at the following code fragment from the NetXMS project:
PRectangle CallTip::CallTipStart(....)
{
....
val = new char[strlen(defn) + 1];
if (!val)
return PRectangle();
....
}
V668 There is no sense in testing the 'val' pointer against null, as the memory was allocated using the
'new' operator. The exception will be generated in the case of memory allocation error. calltip.cpp 260
The empty object 'PRectangle' was returned earlier if memory couldn't be allocated. Now an exception
is generated when there is memory shortage. I don't know whether or not this behavior change is
critical. Anyway, checking the pointer for being a null pointer doesn't seem reasonable anymore.
We should either remove the checks or use the 'new' operator that doesn't throw exceptions and
returns zero:
val = new (std::nothrow) char[strlen(defn) + 1];
The PVS-Studio analyzer generates too many V668 warnings on the NetXMS project. Therefore I won't
overload the article with examples. Let's leave it up to the authors to check the project.
A strange loop
static bool MatchStringEngine(....)
{
....
// Handle "*?" case
while(*MPtr == _T('?'))
{
if (*SPtr != 0)
SPtr++;](https://image.slidesharecdn.com/0201netxms-130729070042-phpapp02/75/Monitoring-a-program-that-monitors-computer-networks-12-2048.jpg)
