More Related Content
What's hot
What's hot (20)
Multilayer Security Architecture for Internet Protocols

Multilayer Security Architecture for Internet Protocols
Similar to Week14 Pre
Similar to Week14 Pre (20)
Recently uploaded
Recently uploaded (20)
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Week14 Pre
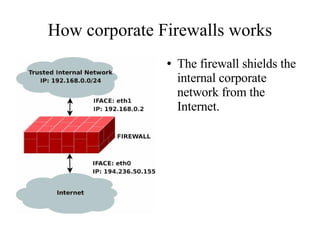
- 1. How corporate Firewalls works ● The firewall shields the internal corporate network from the Internet.
- 2. The firewall want to acsess the Internet When someone on the corporate network inside the firewall wants to access the Internet, the request and data must go through an internal screening router.
- 3. The screening certain packets The screening router allows certain packets to be sent or received, but blocks other packets. System administrators set the rules for datermining which packets to allow in and which ones to block.
- 4. A bastion host in the firewall A bastion host in the firewall is the primary point of contact for connections coming in from the Internet for services such as receiving email and allowing access to the corporation's FTP sites.
- 5. A bastion host ● The bastion host is placed in a perimeter network in the firewall, so it is not on the corporate network itself.
- 6. The exterior screening router ● An exterior screening router screens packets between the Internet and the perimeternetwork. ● This router adds an extra level of protection by screening packets.