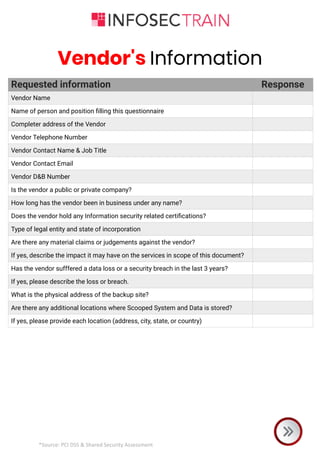
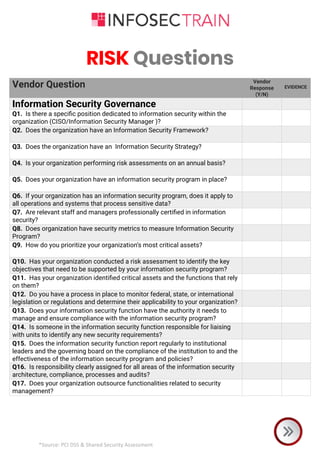
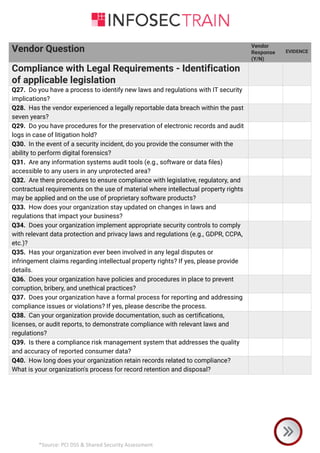
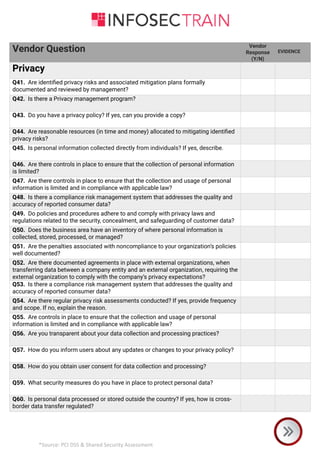
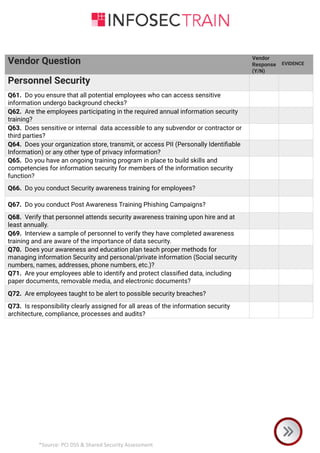
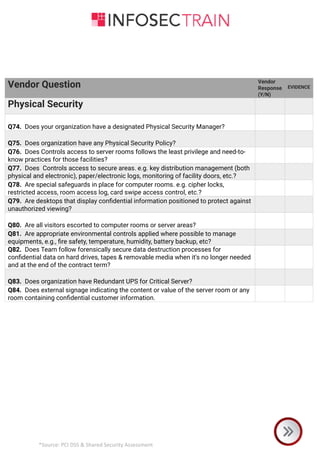
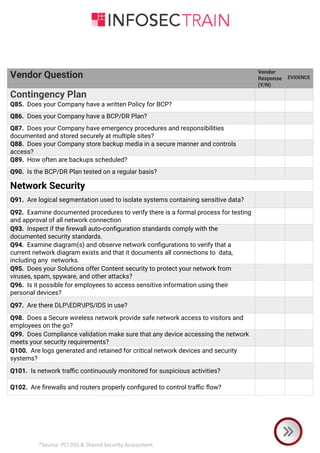
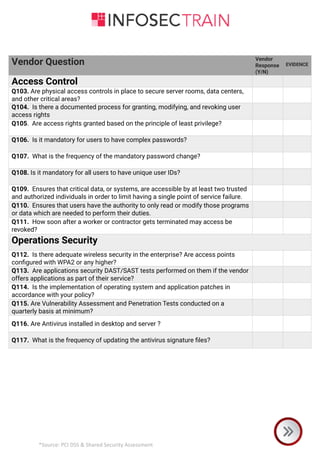
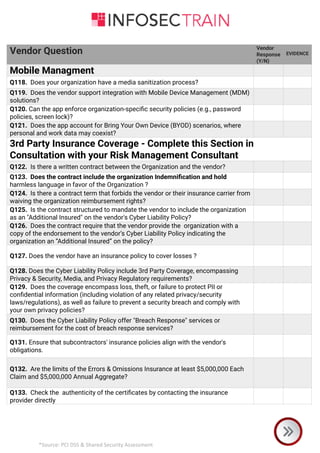
The document is a comprehensive checklist for assessing a vendor's compliance with PCI DSS and shared security requirements, covering various aspects like information security governance, policies, legal compliance, privacy, personnel security, physical security, contingency planning, network security, access control, and third-party insurance. Each section includes specific vendor questions with binary response options (yes/no) and evidence requirements to ensure thorough evaluation. The document emphasizes the vendor's responsibilities in maintaining data security and compliance with applicable laws and regulations.