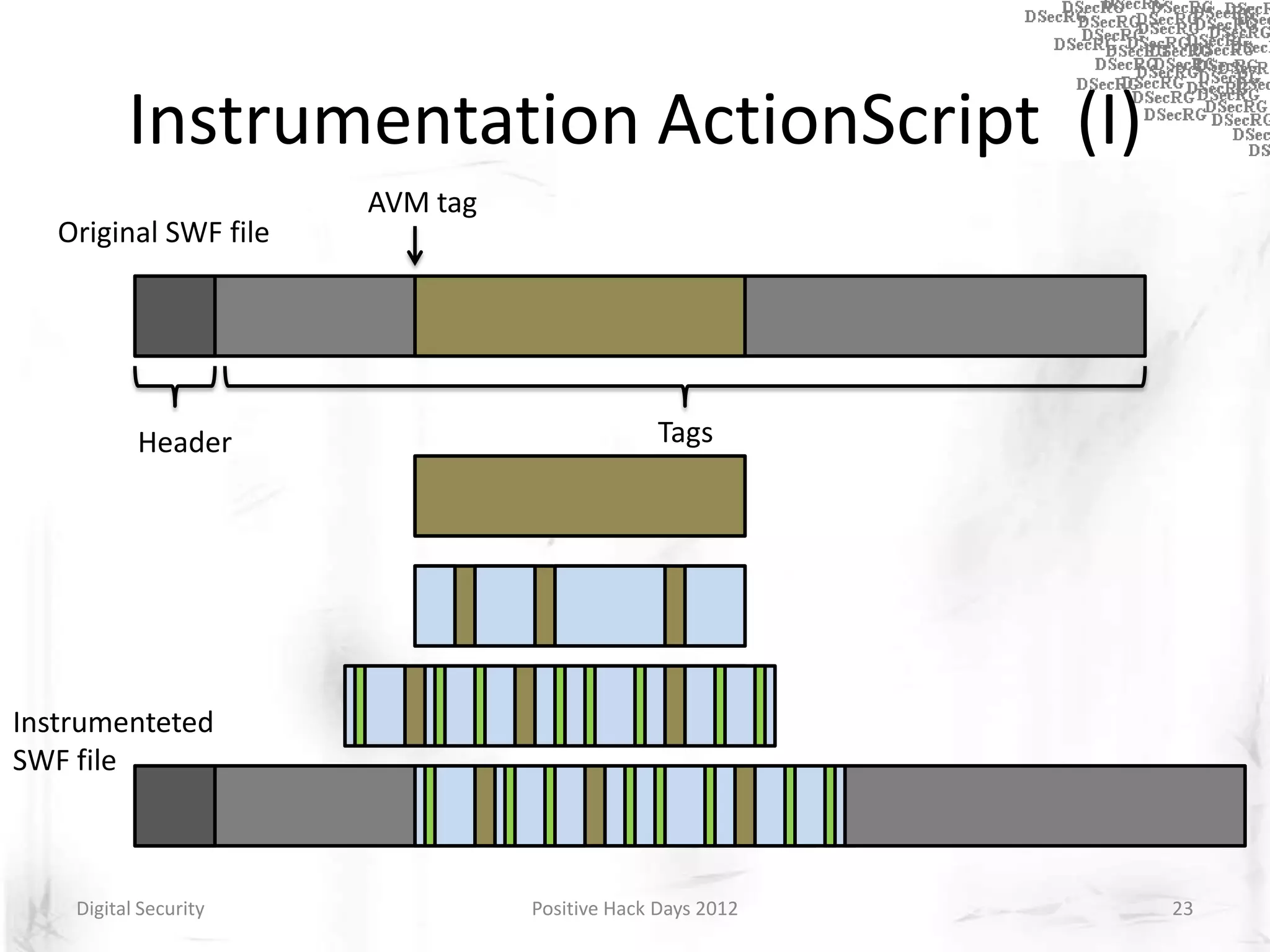
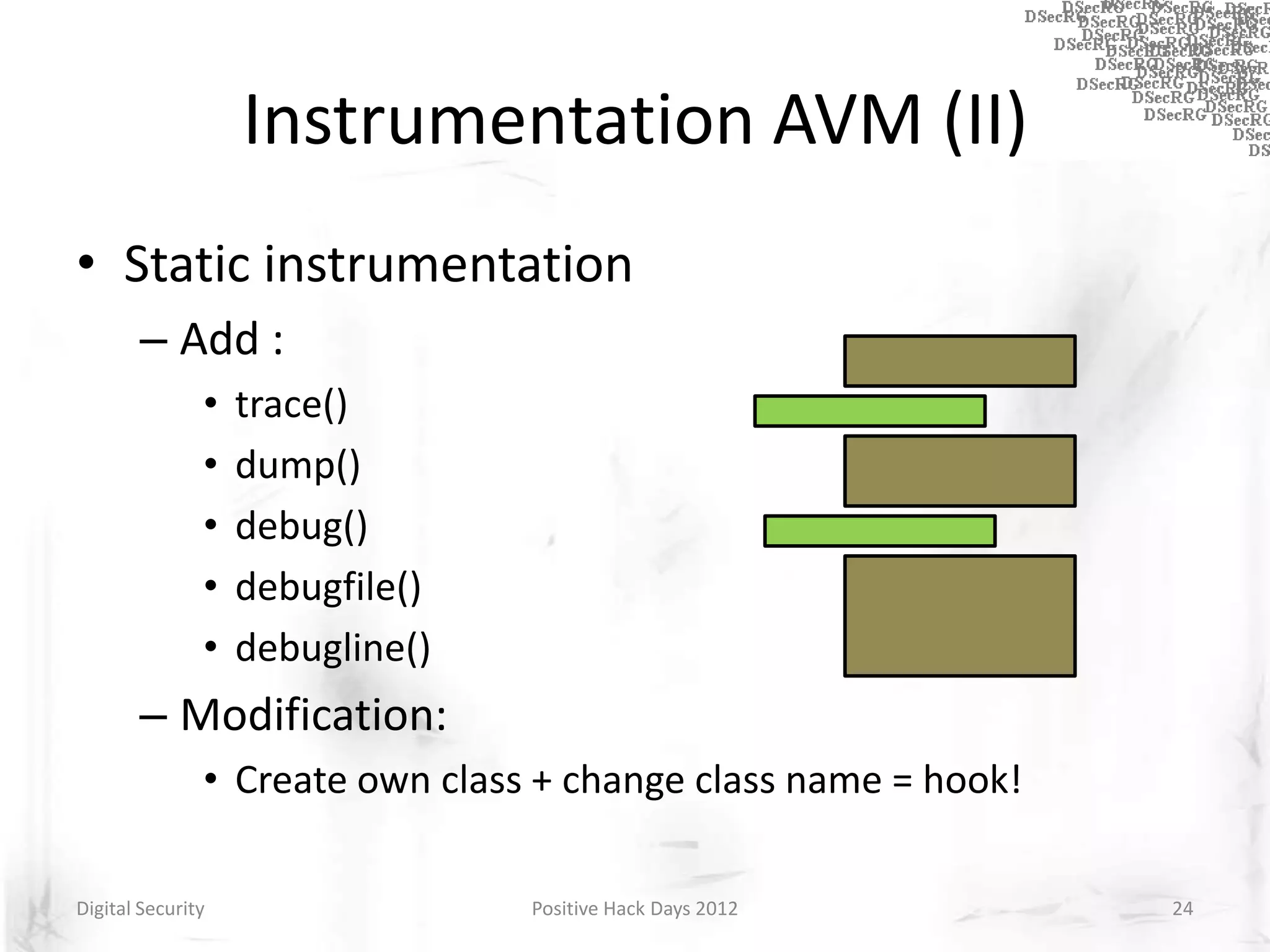
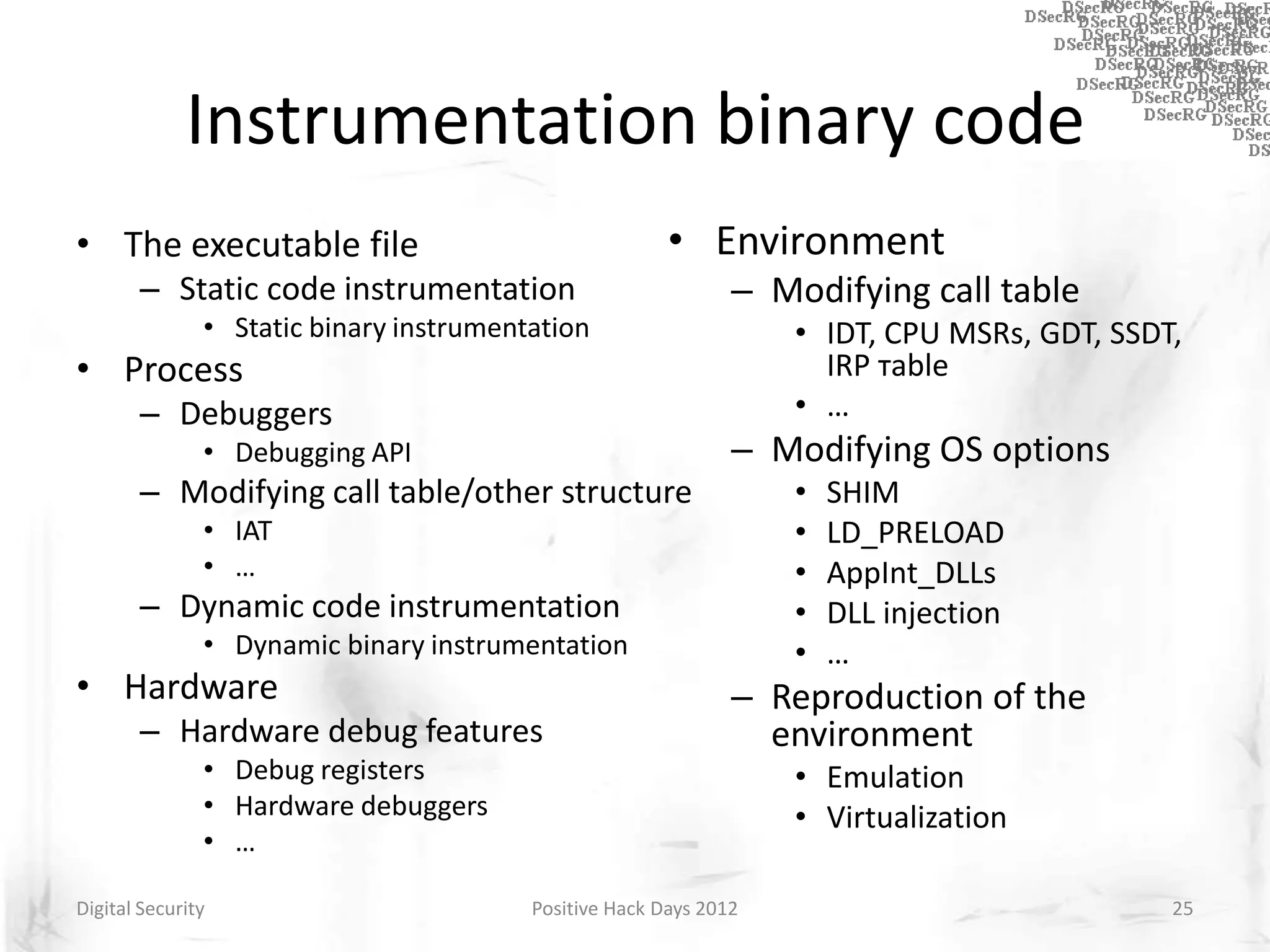
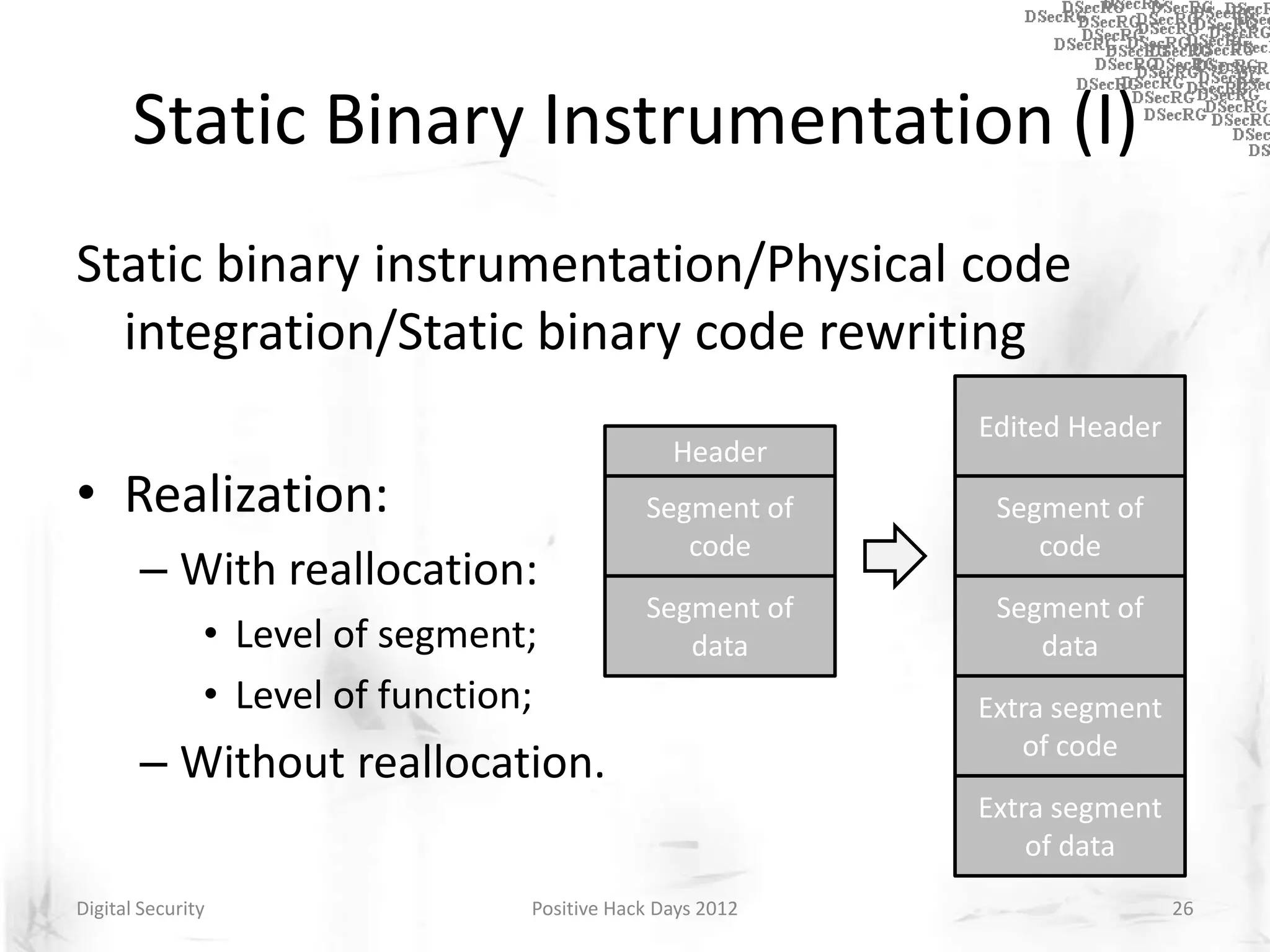
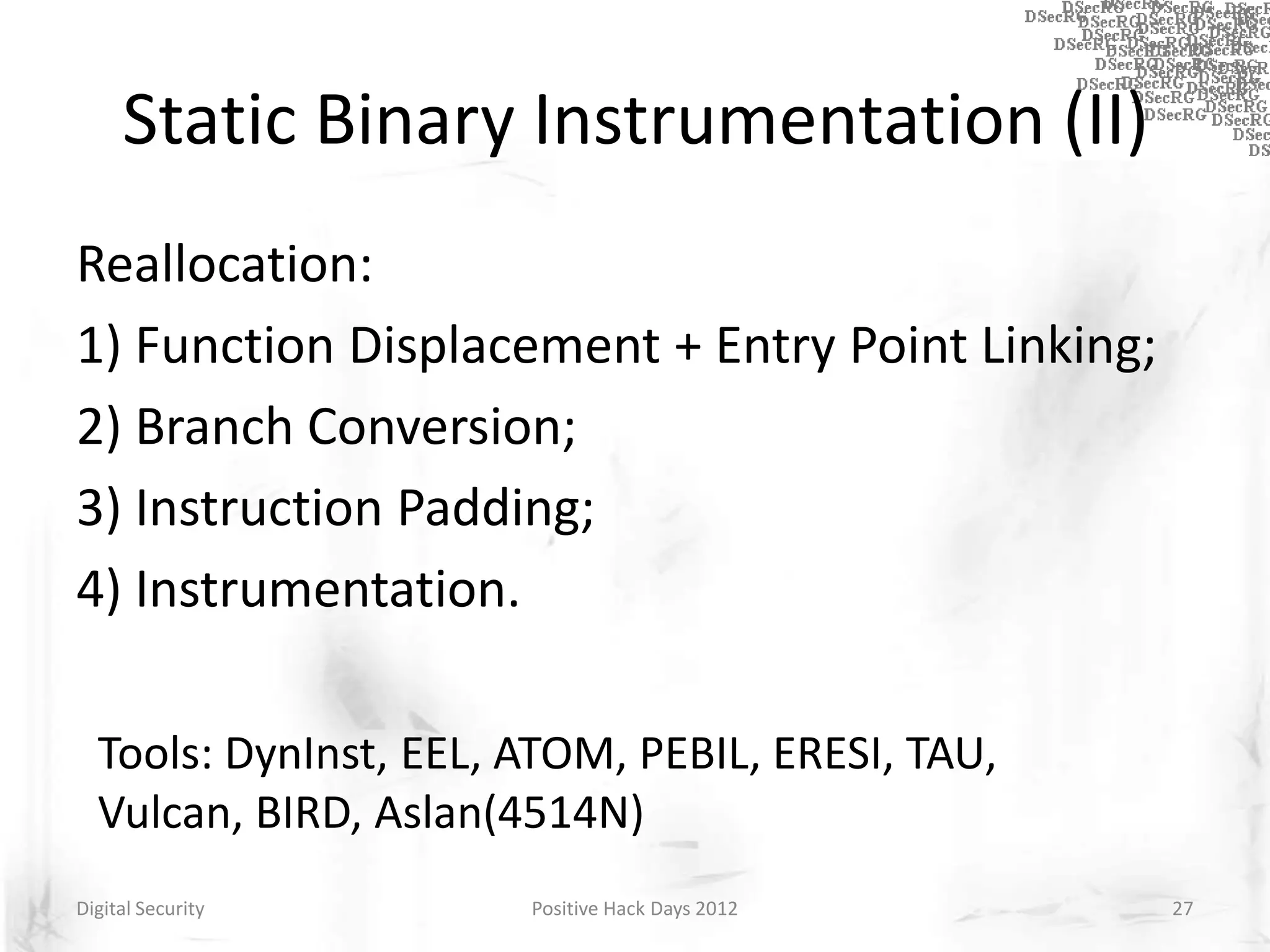
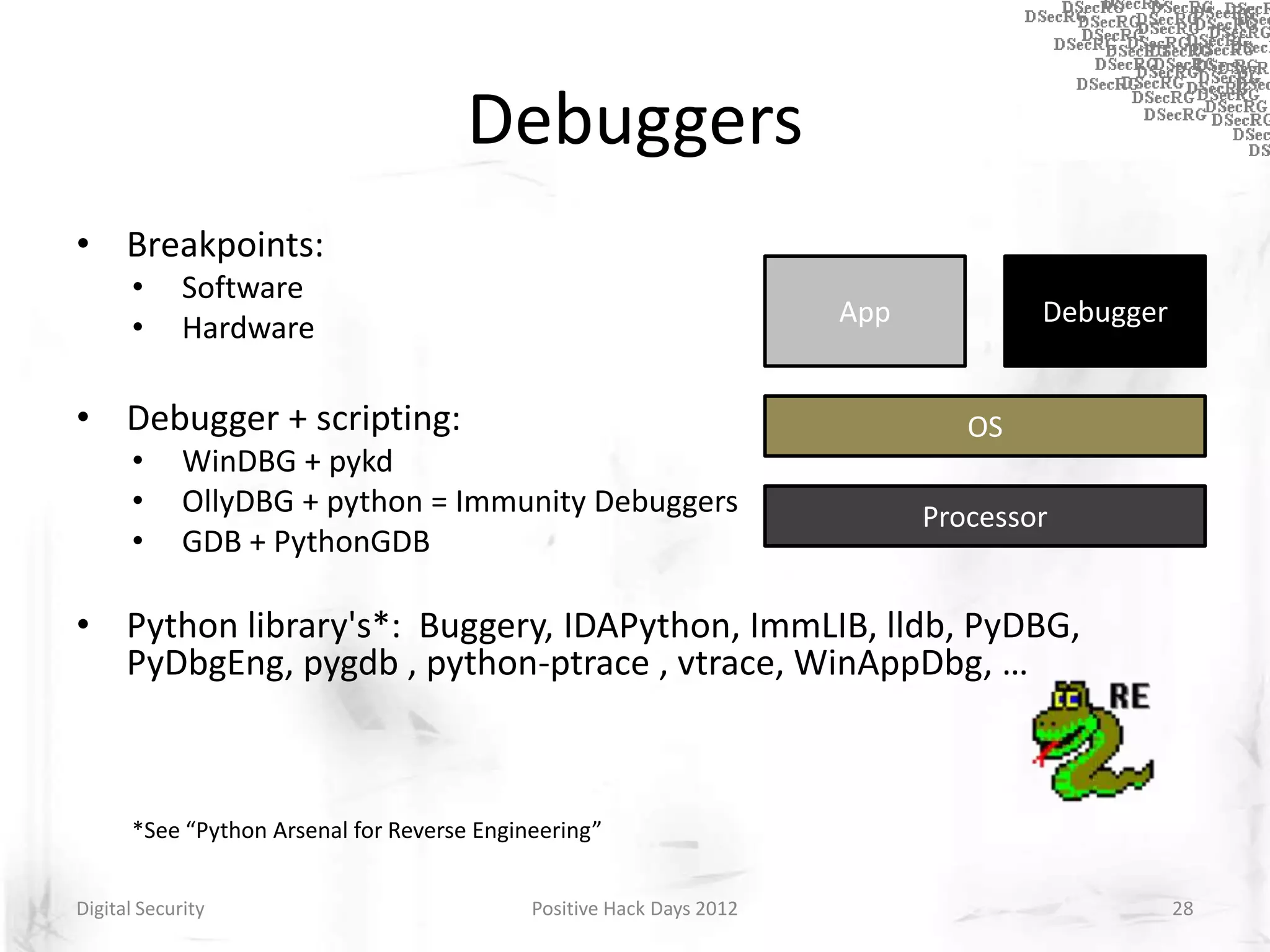
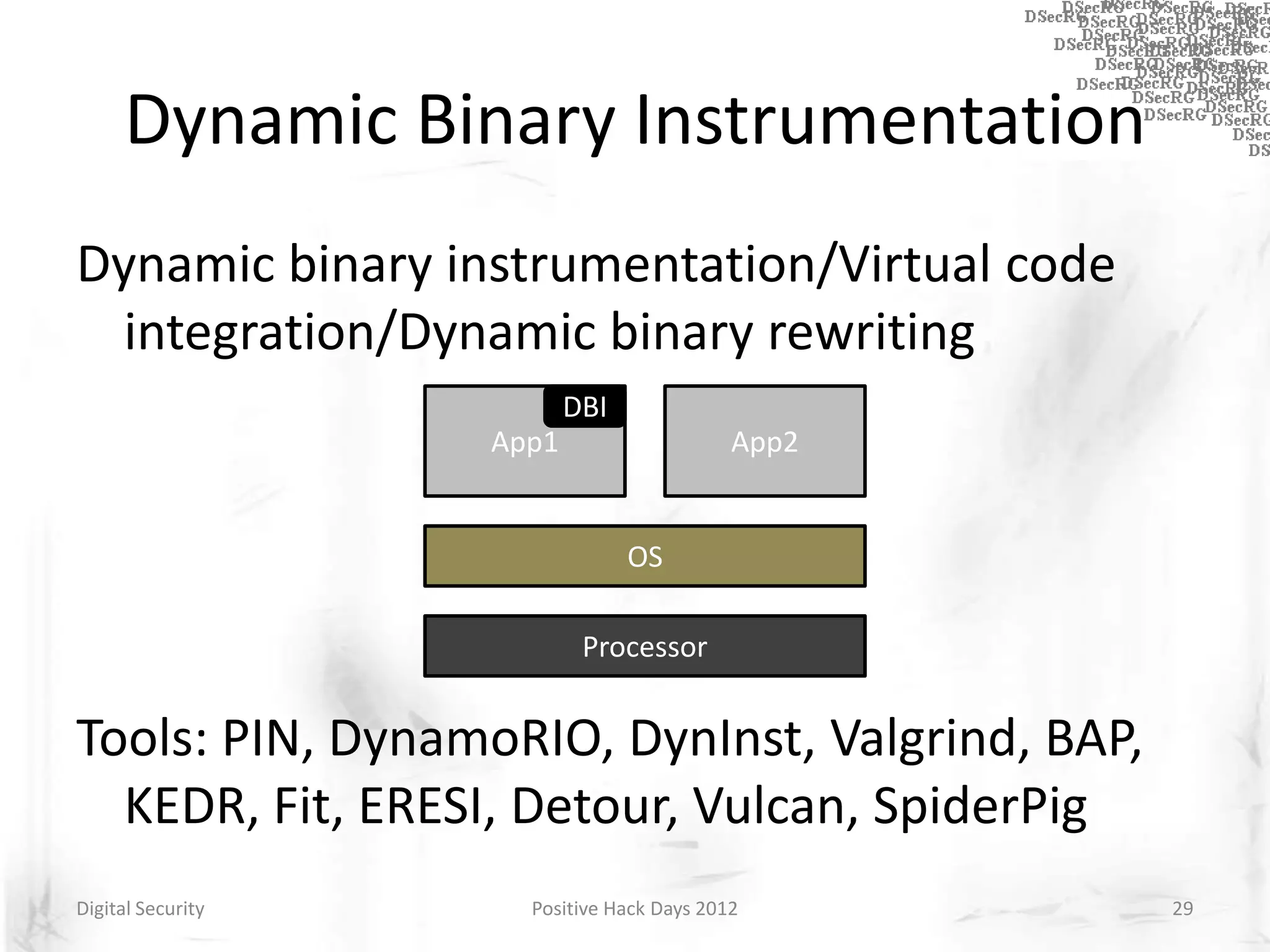
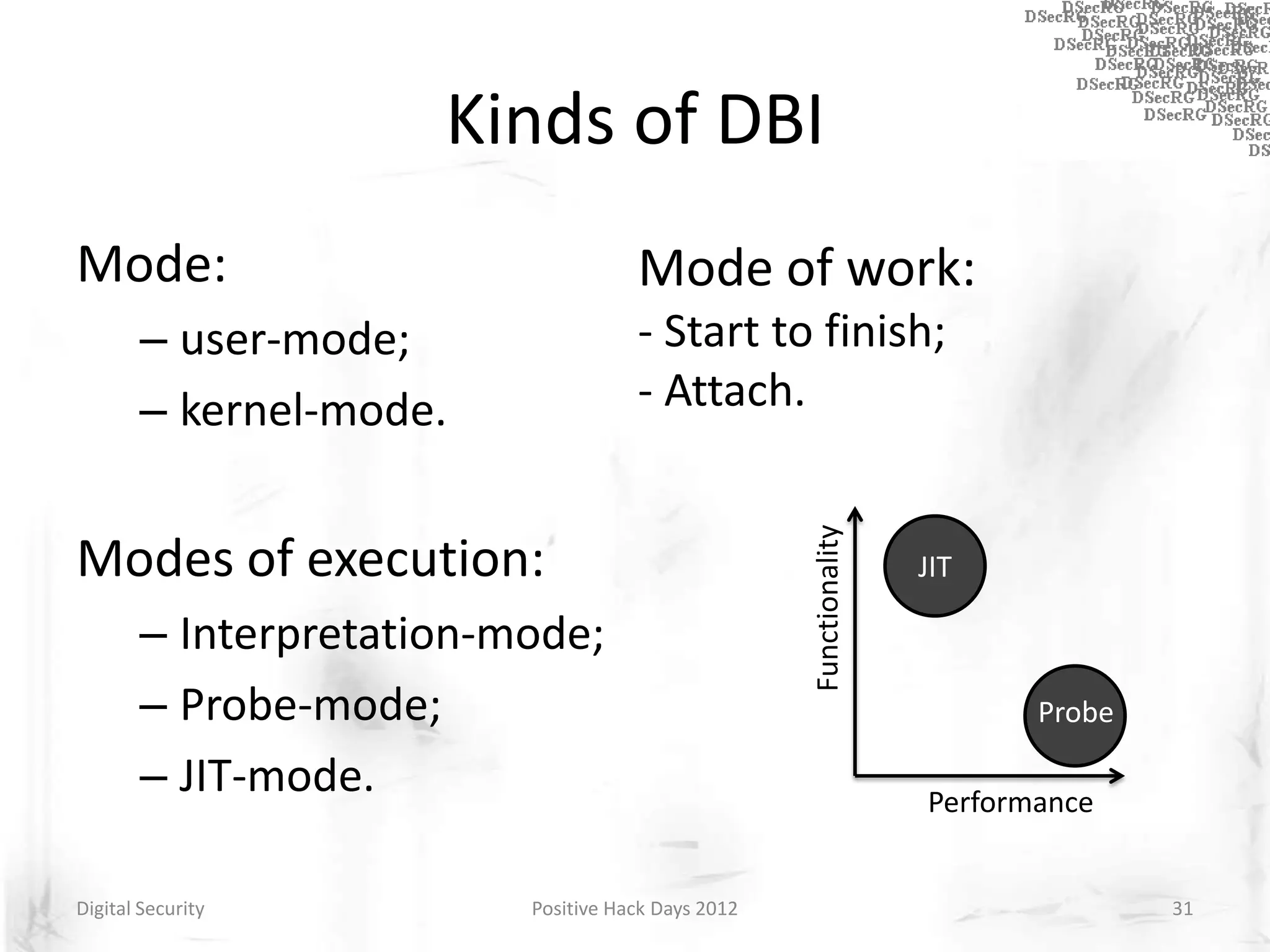
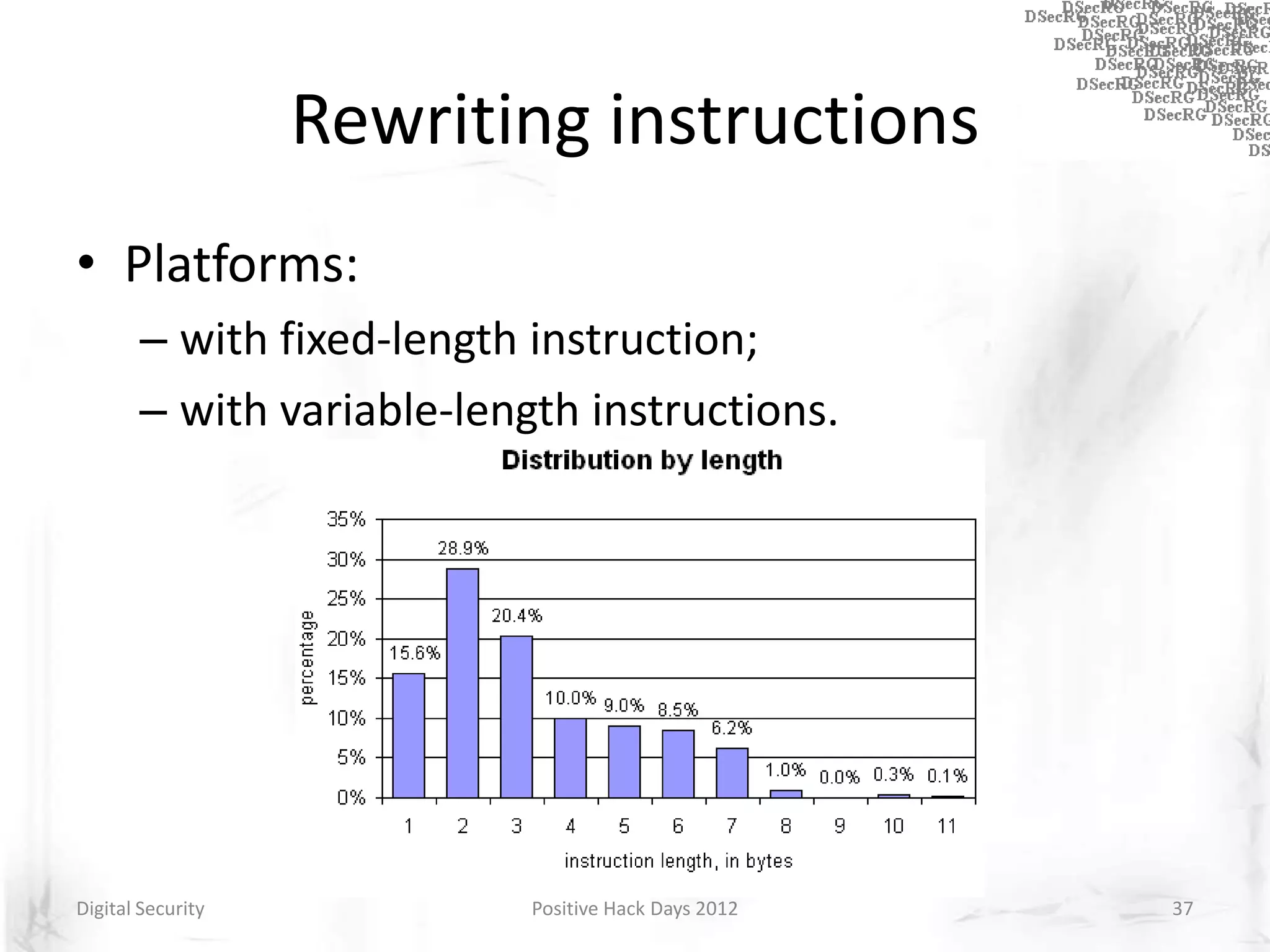
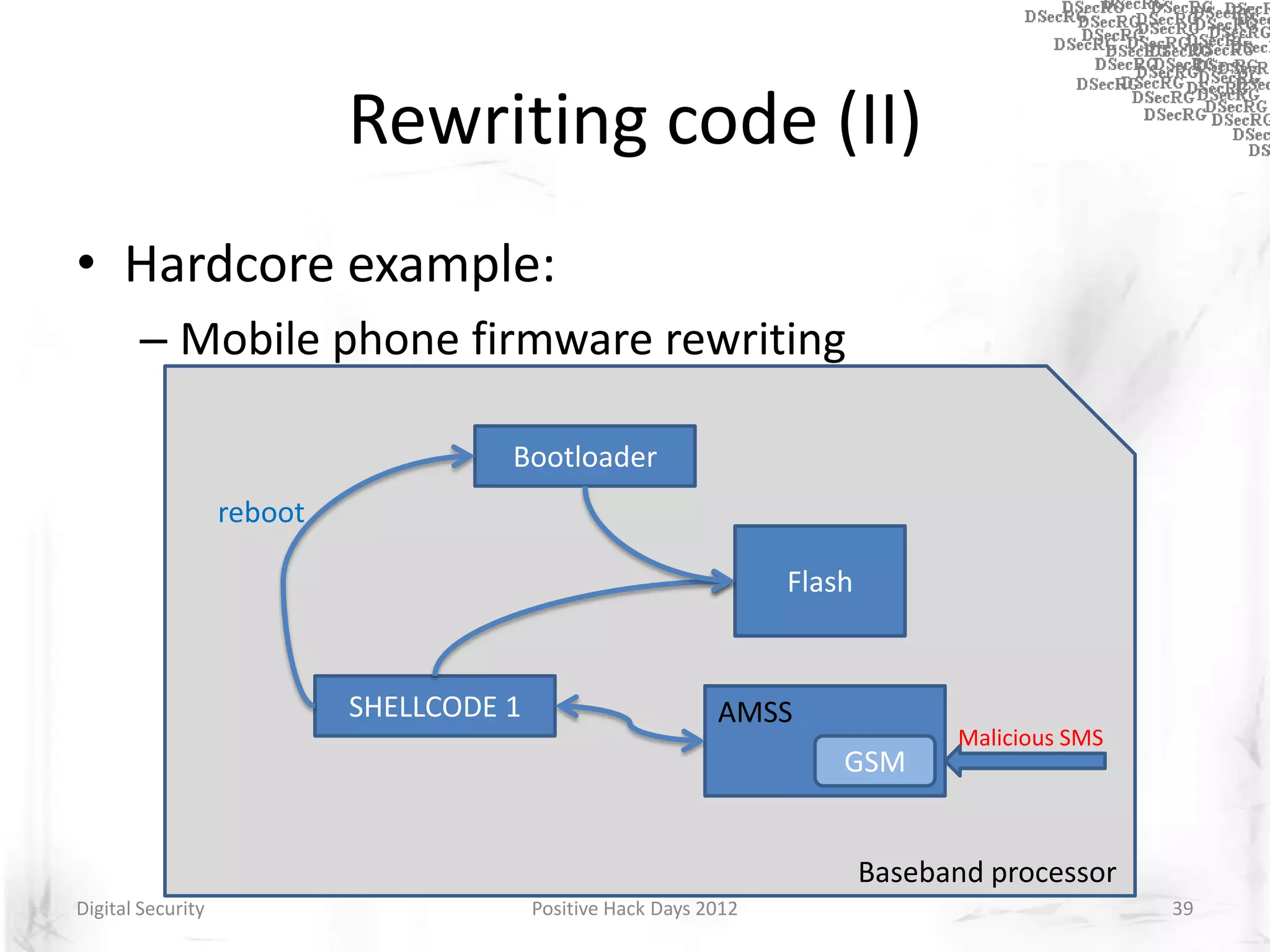
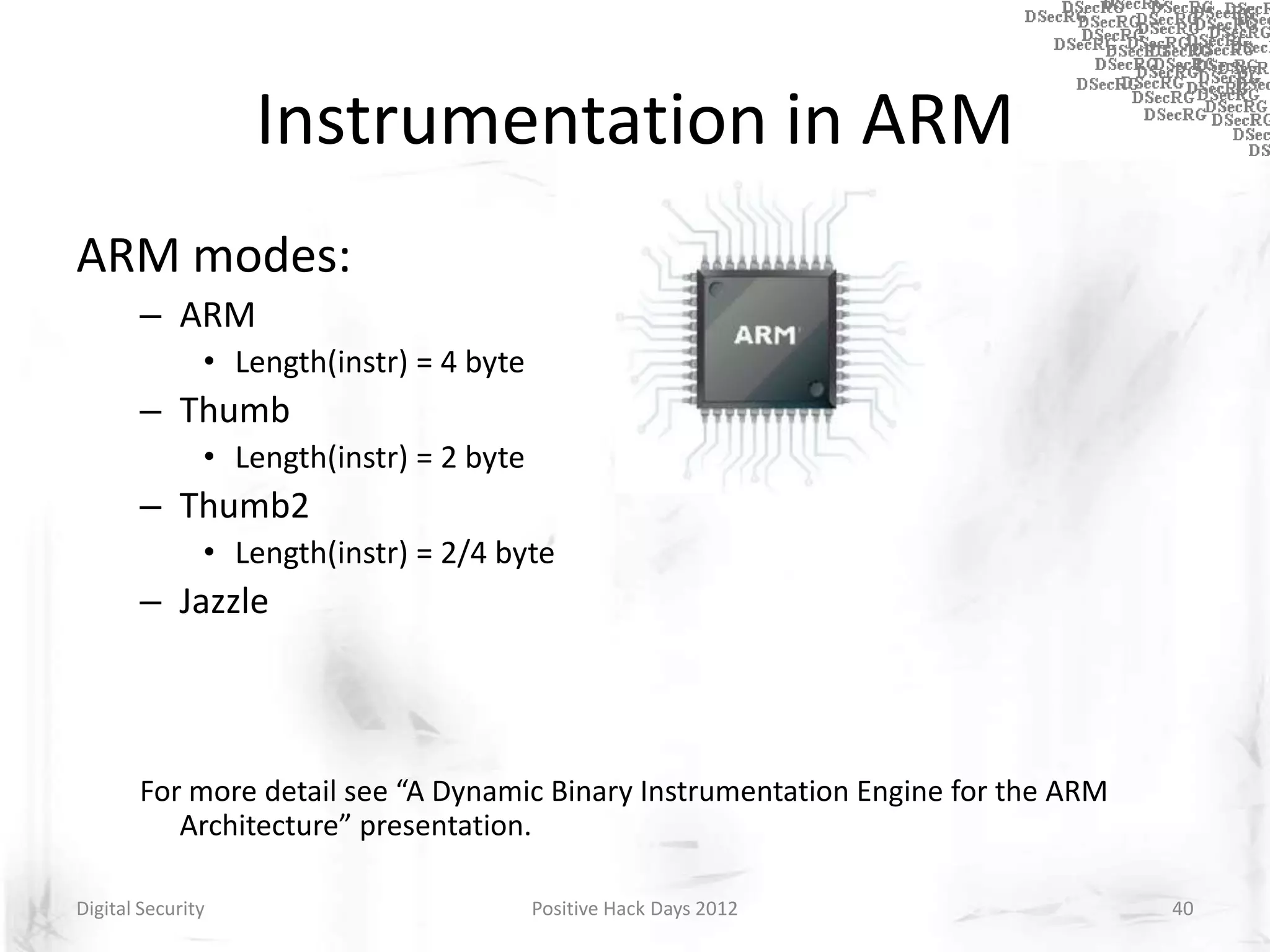
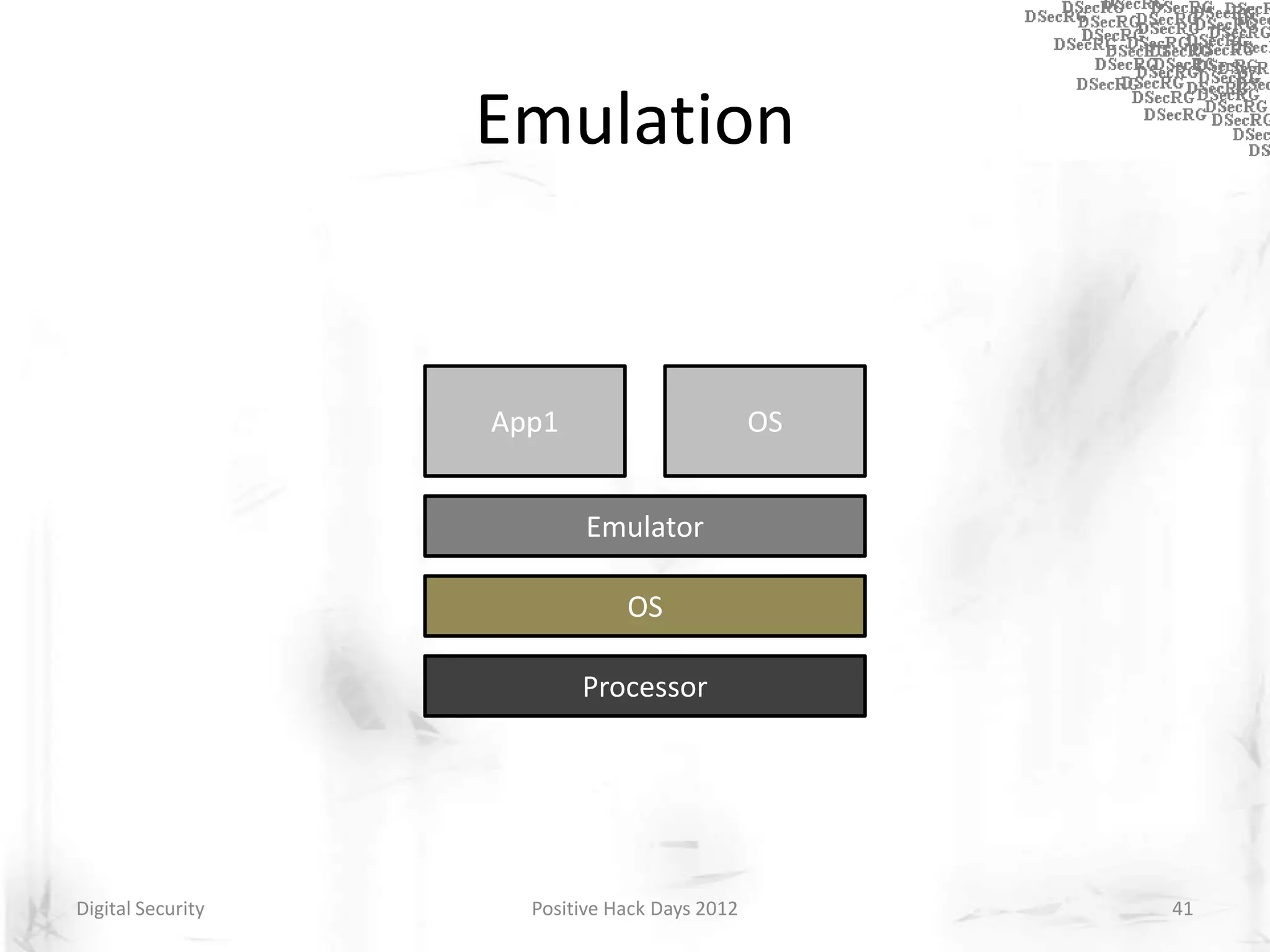
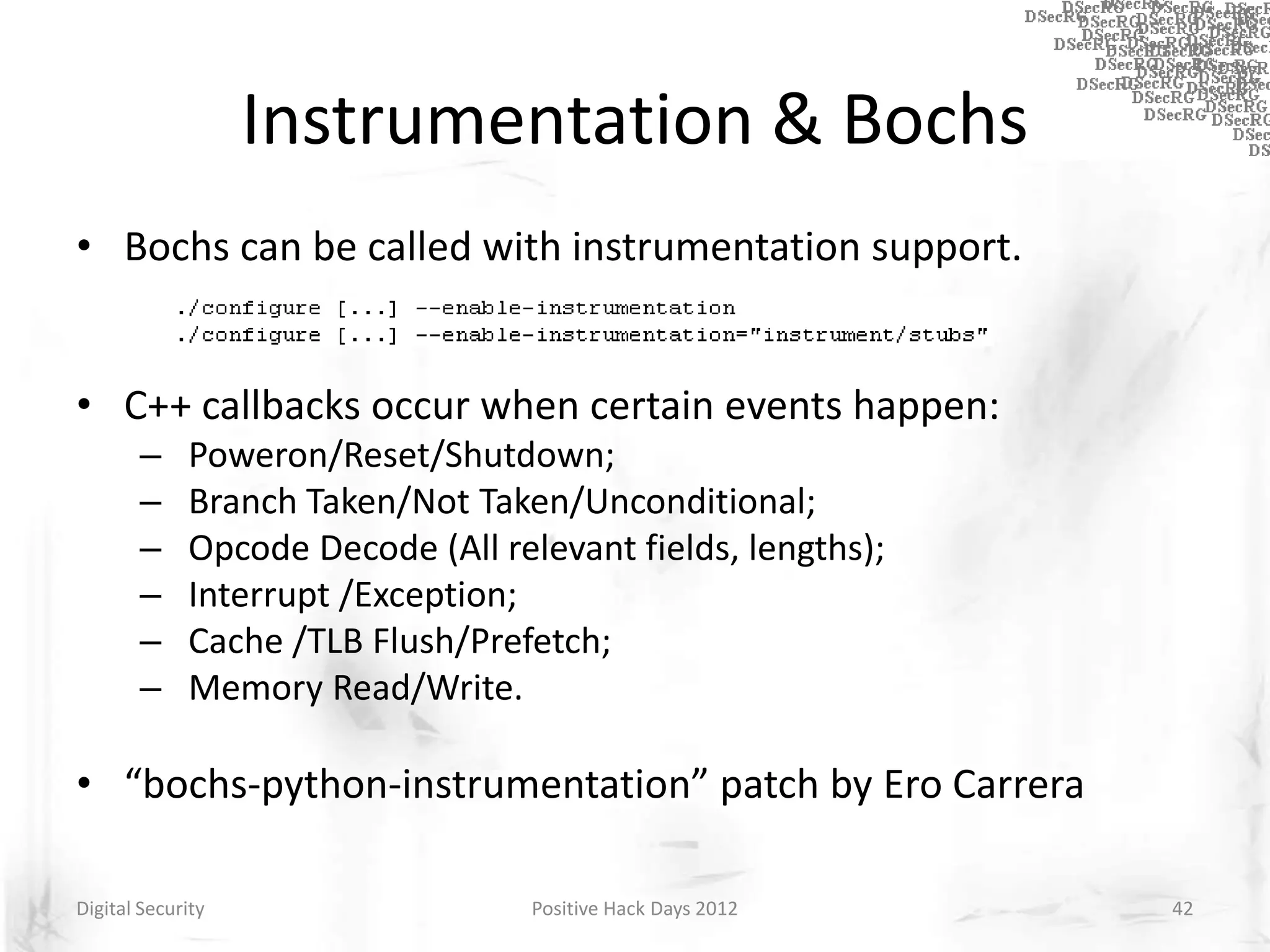
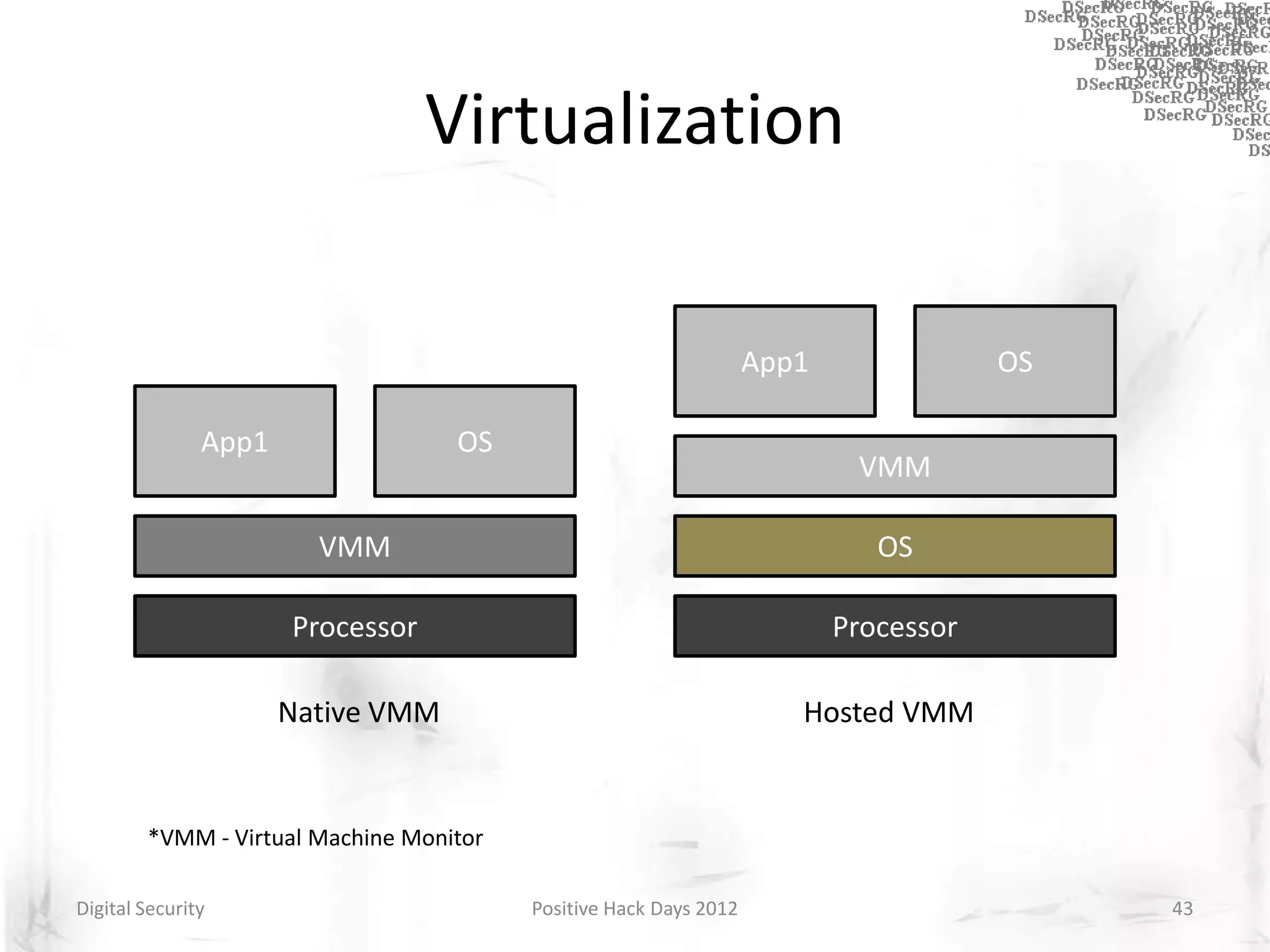
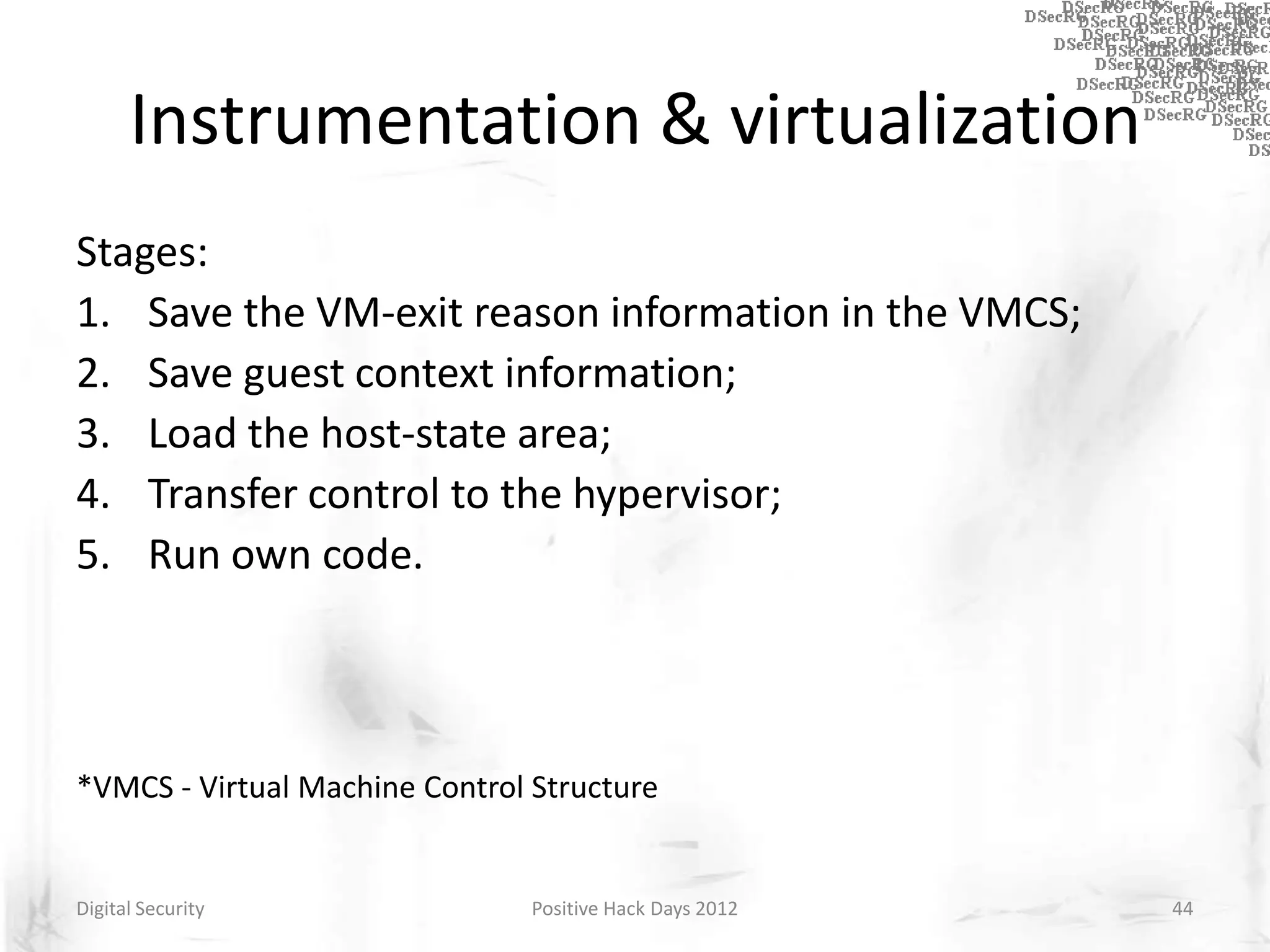
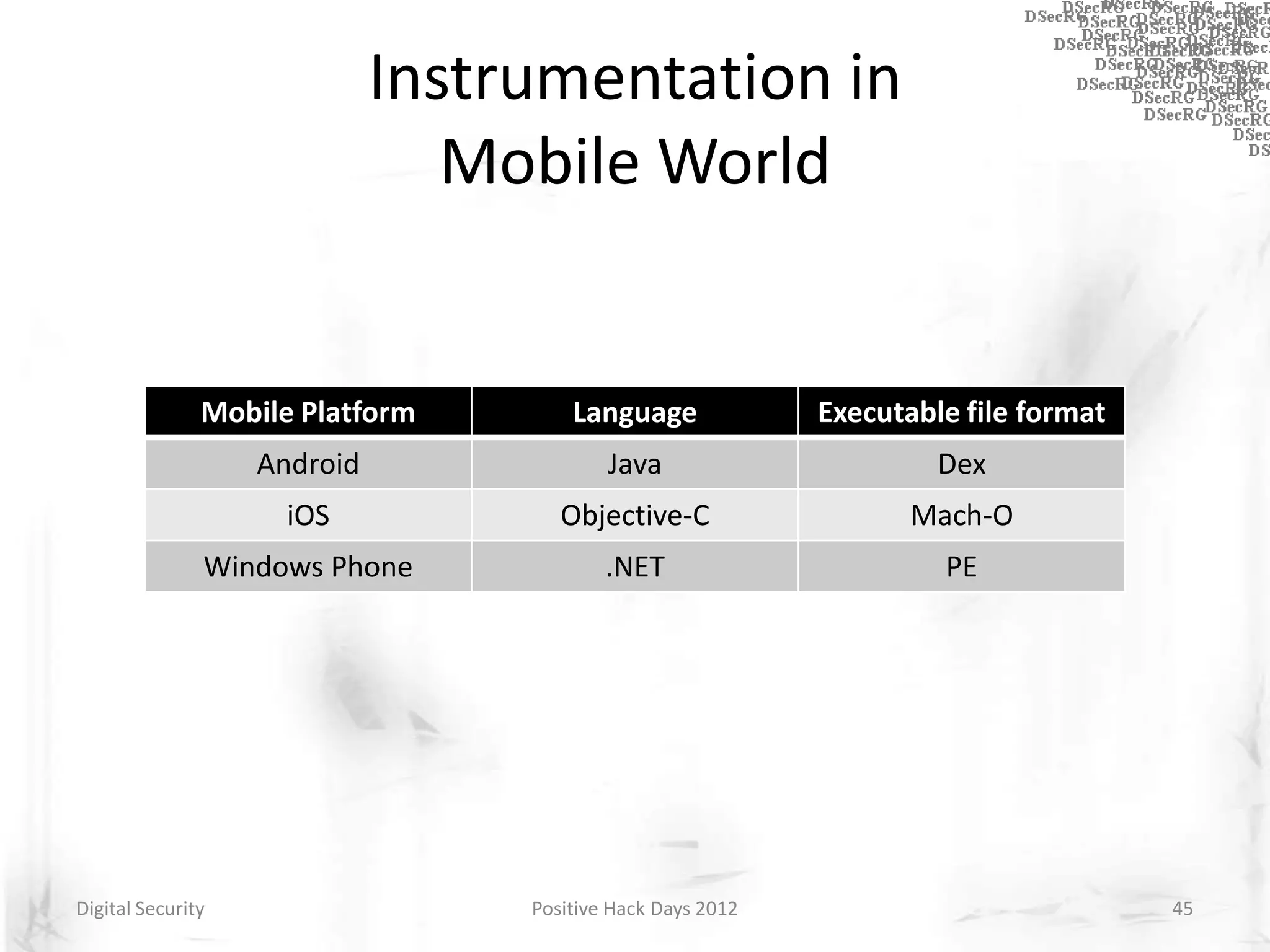
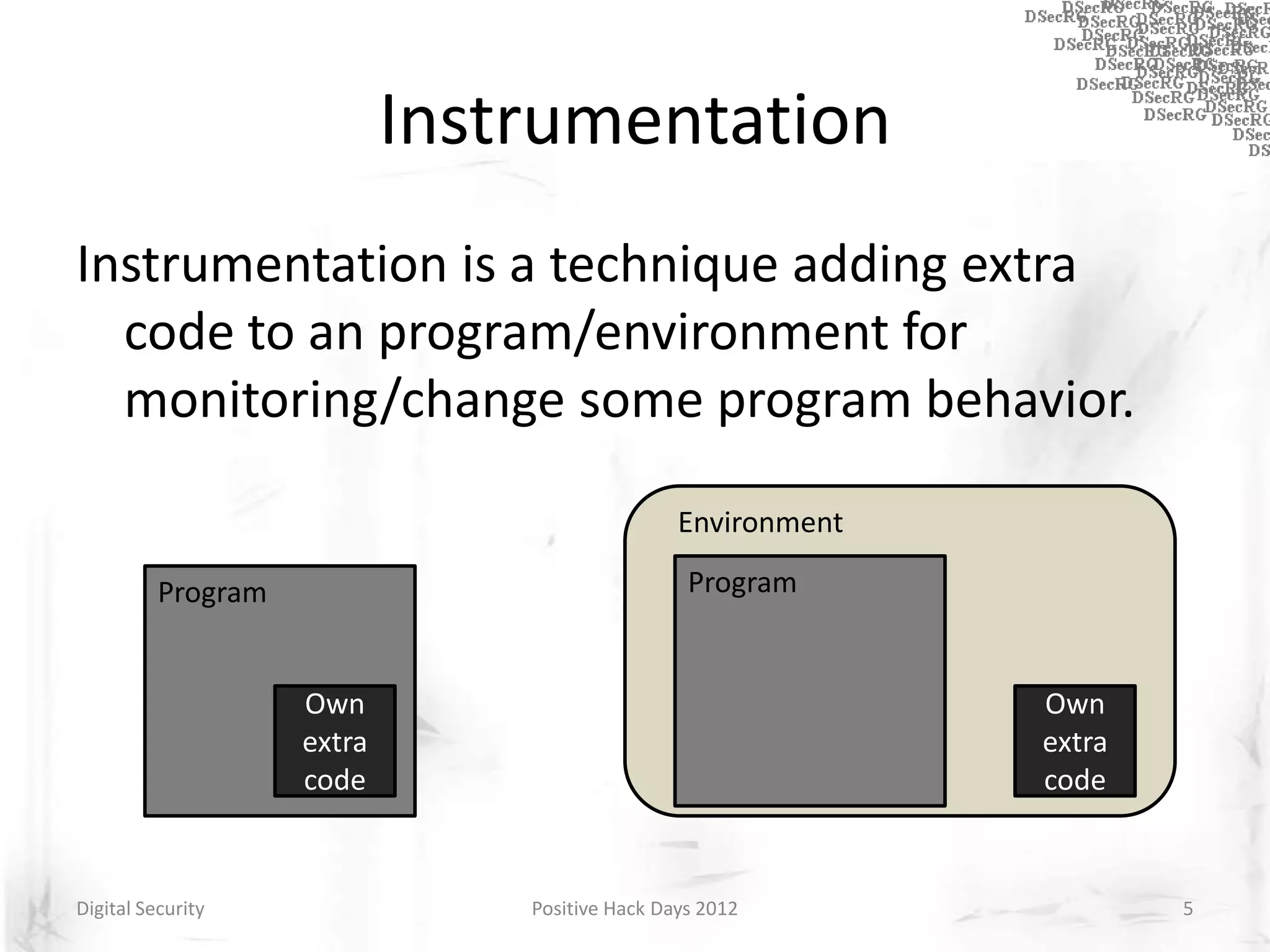
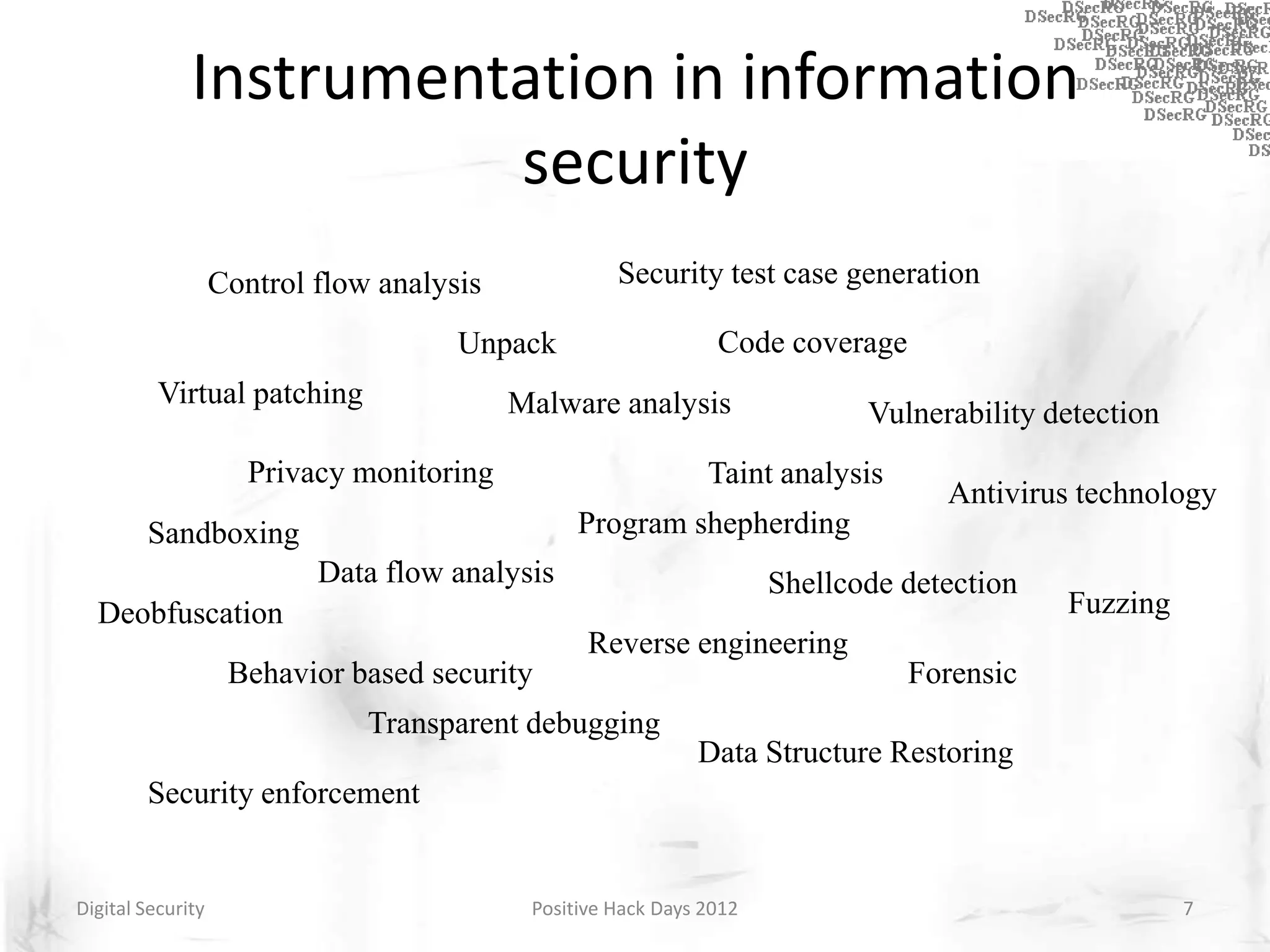
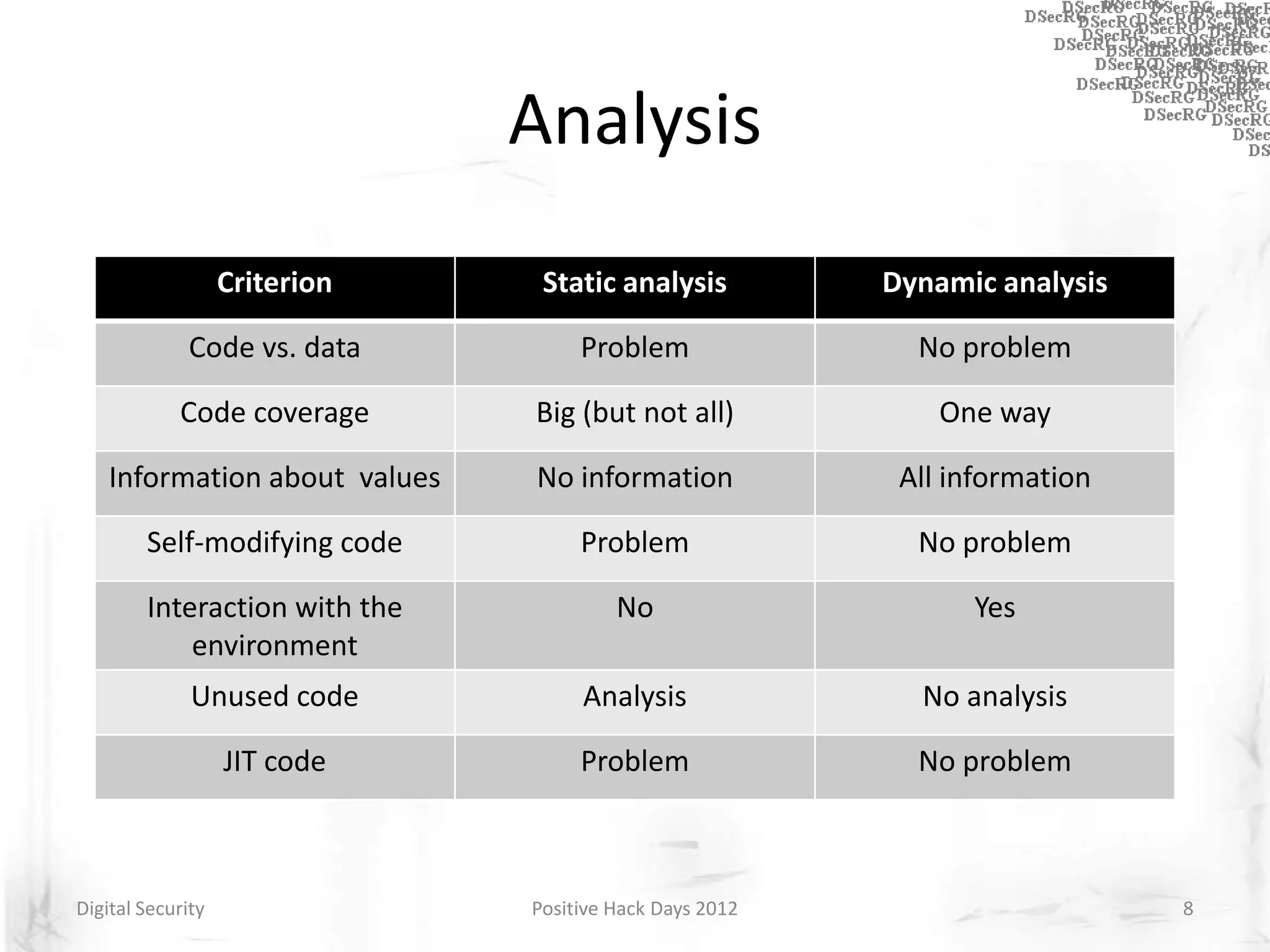
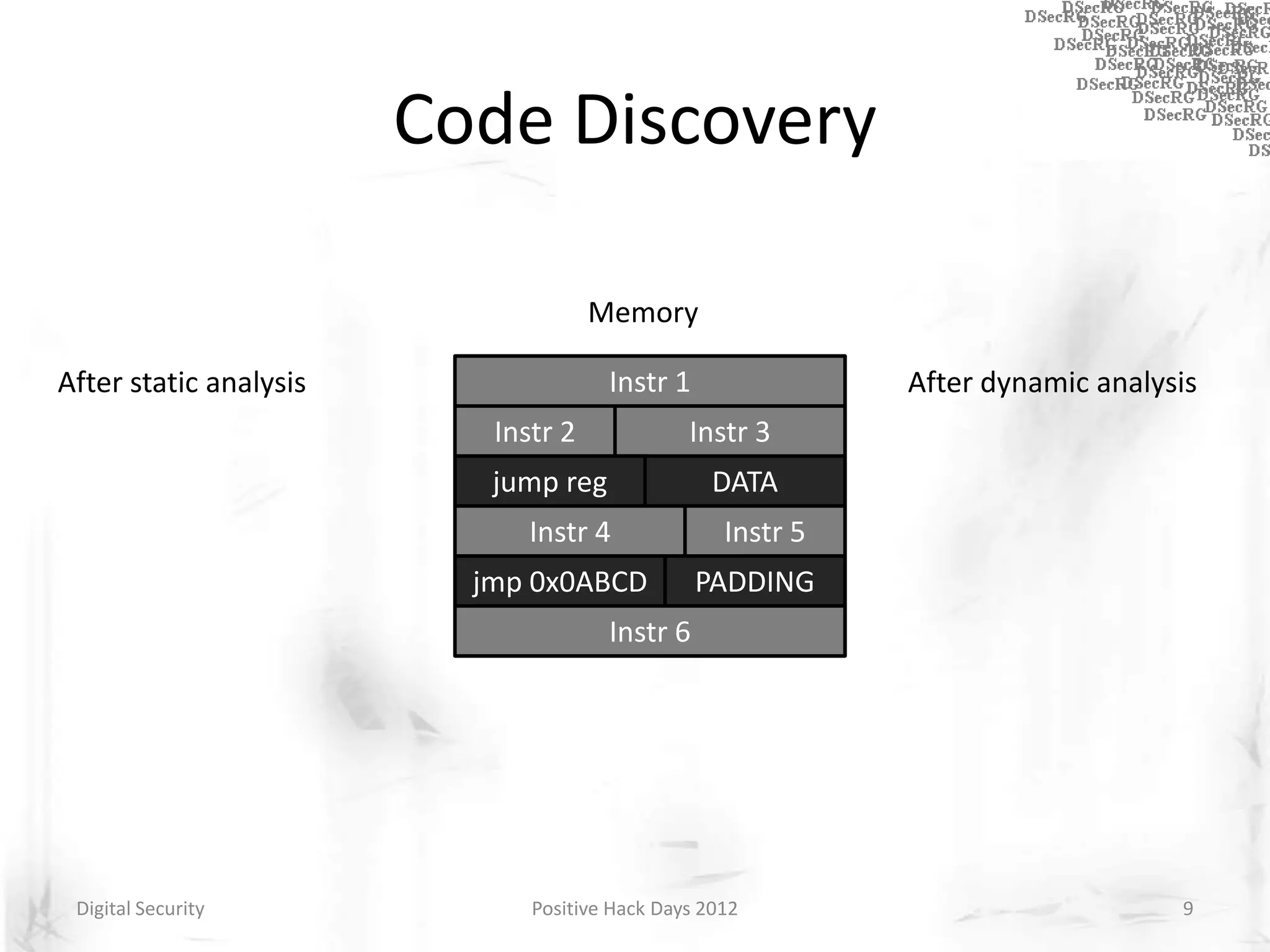
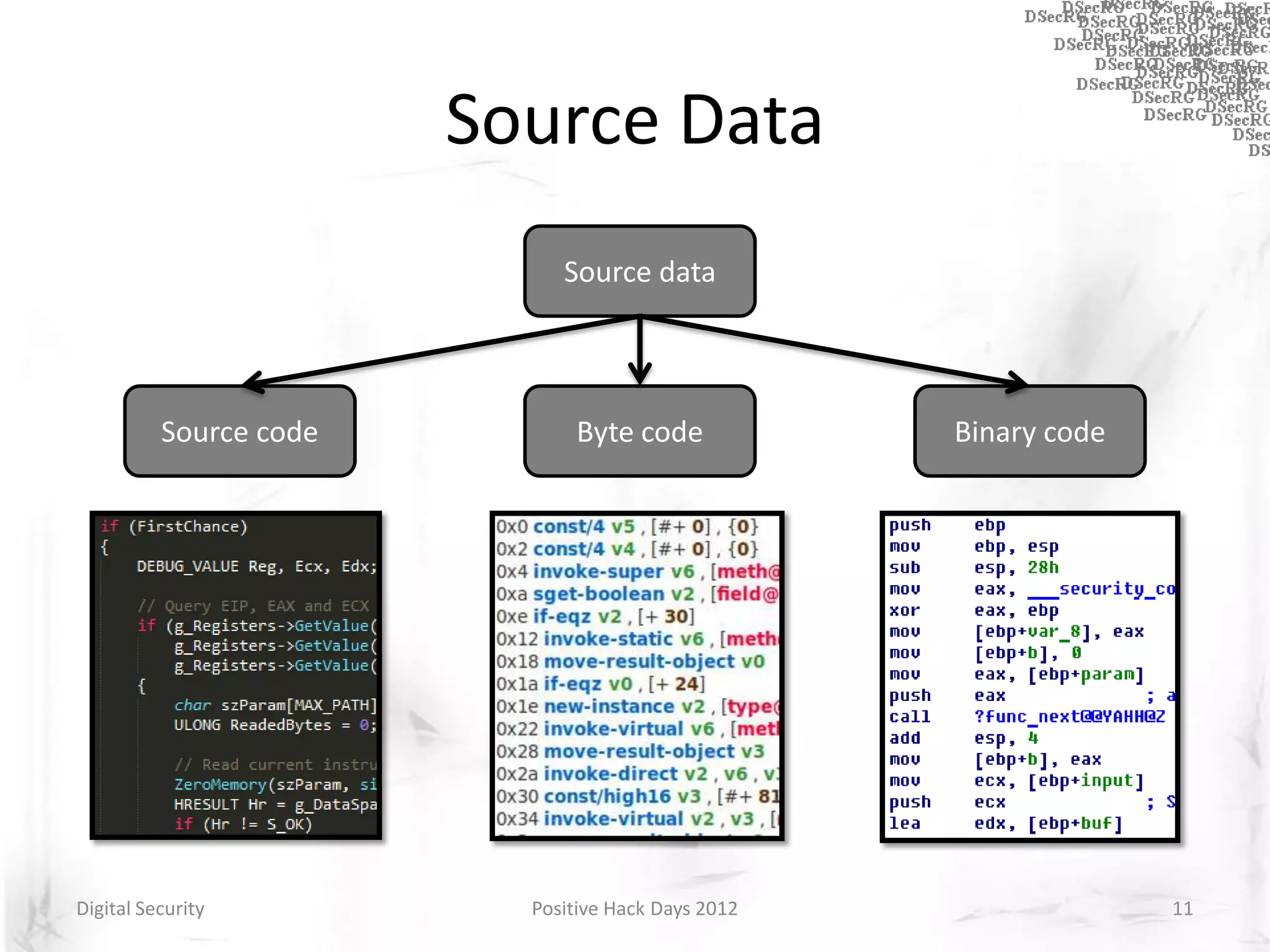
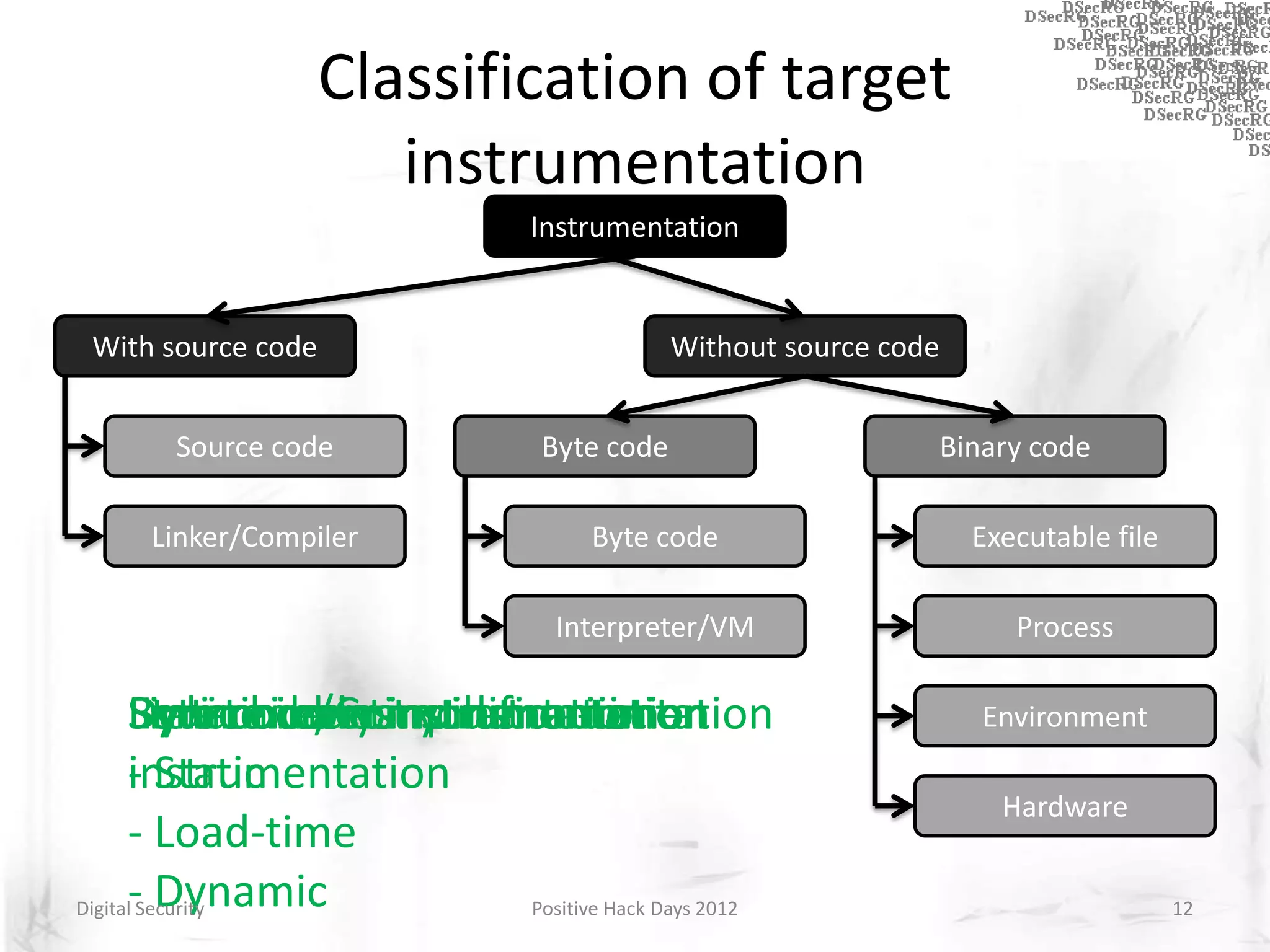
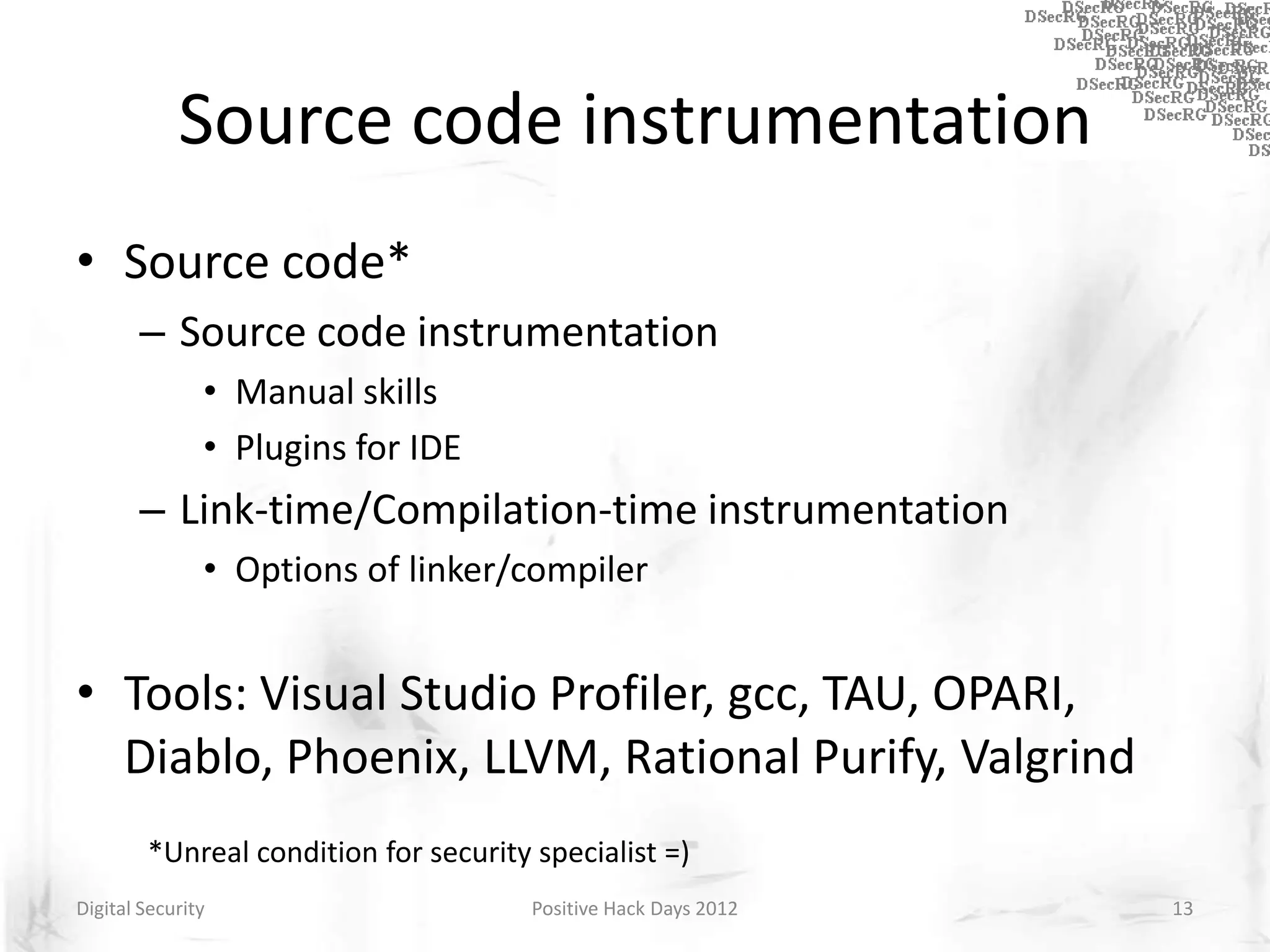
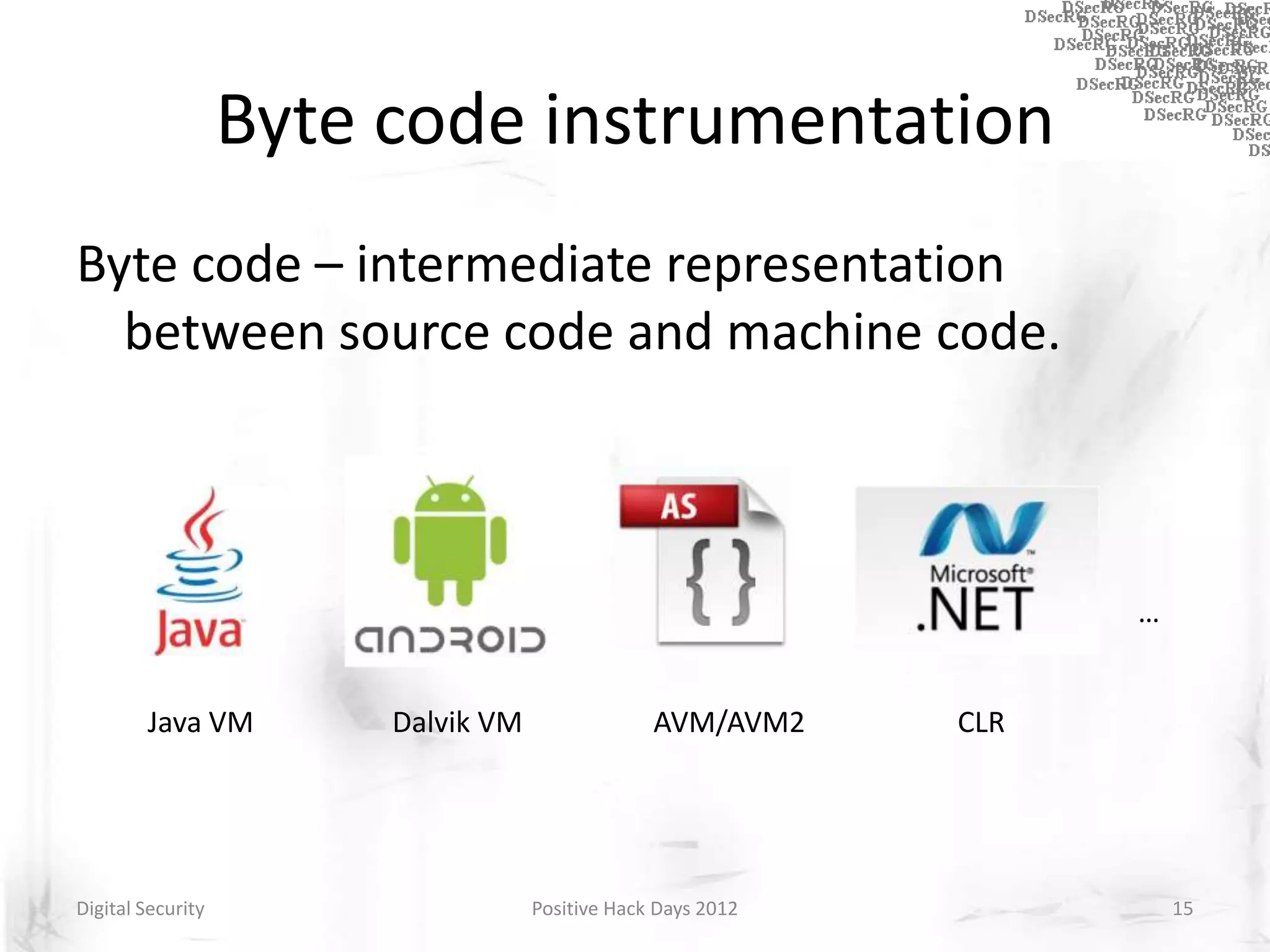
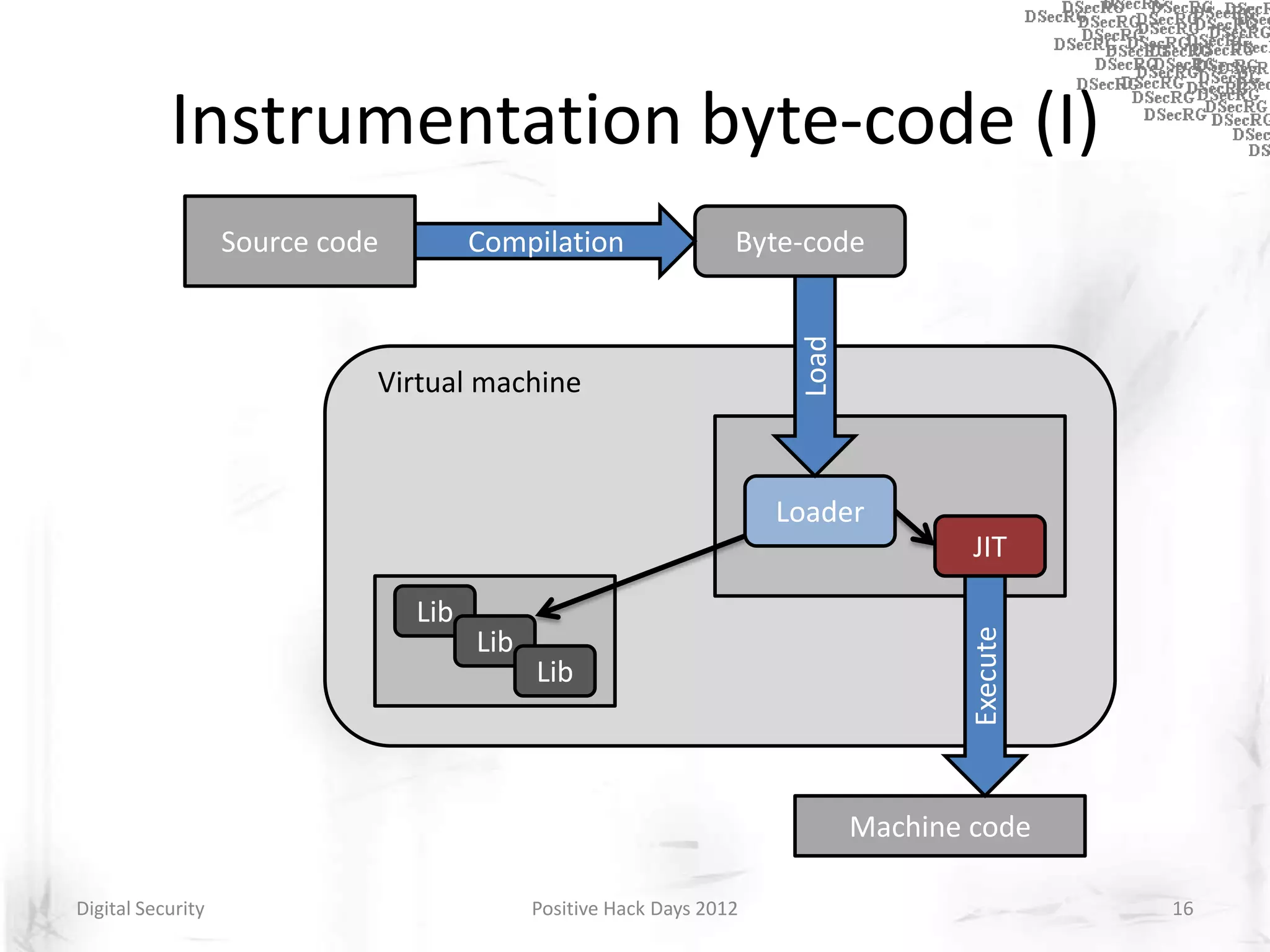
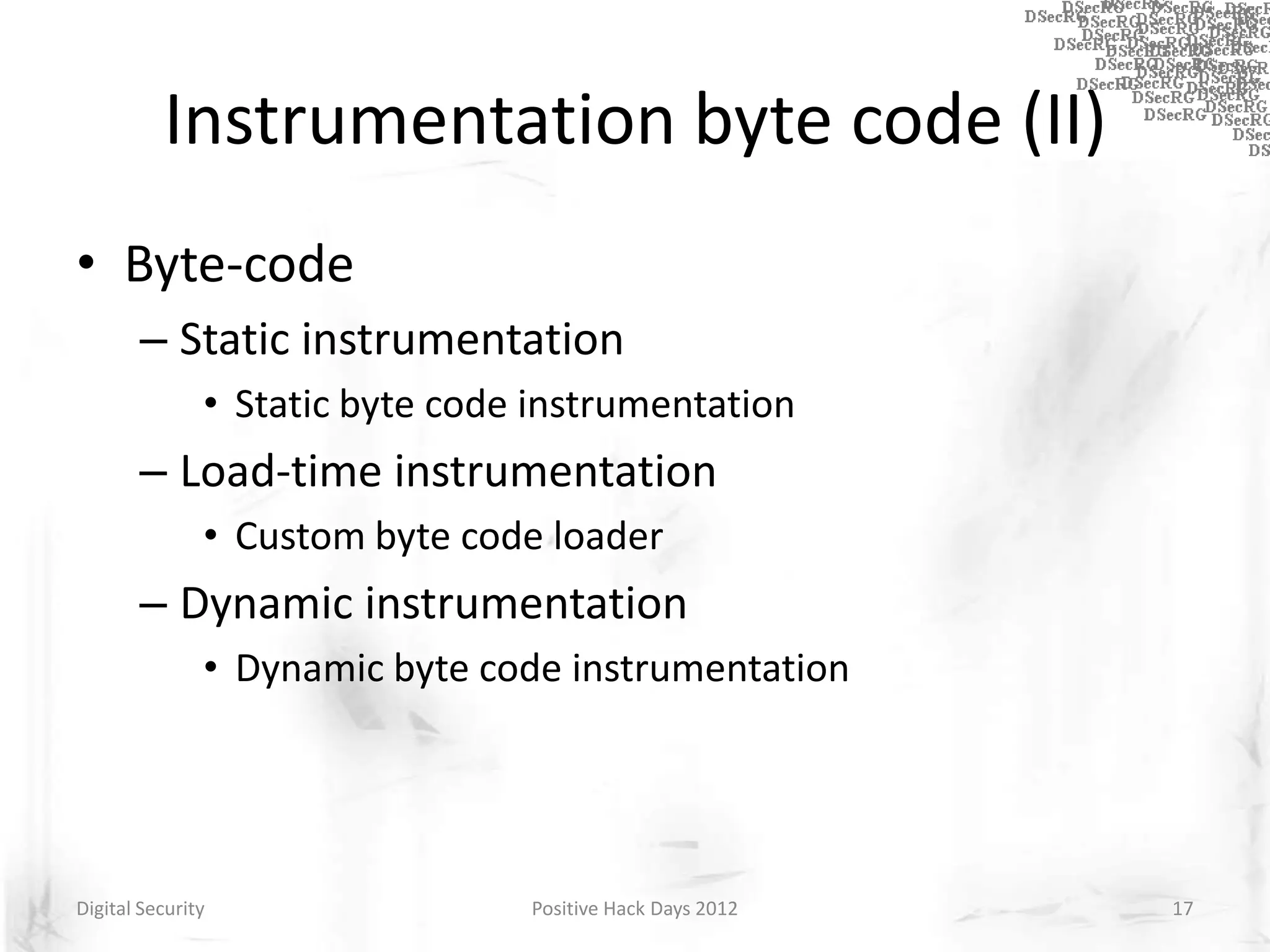
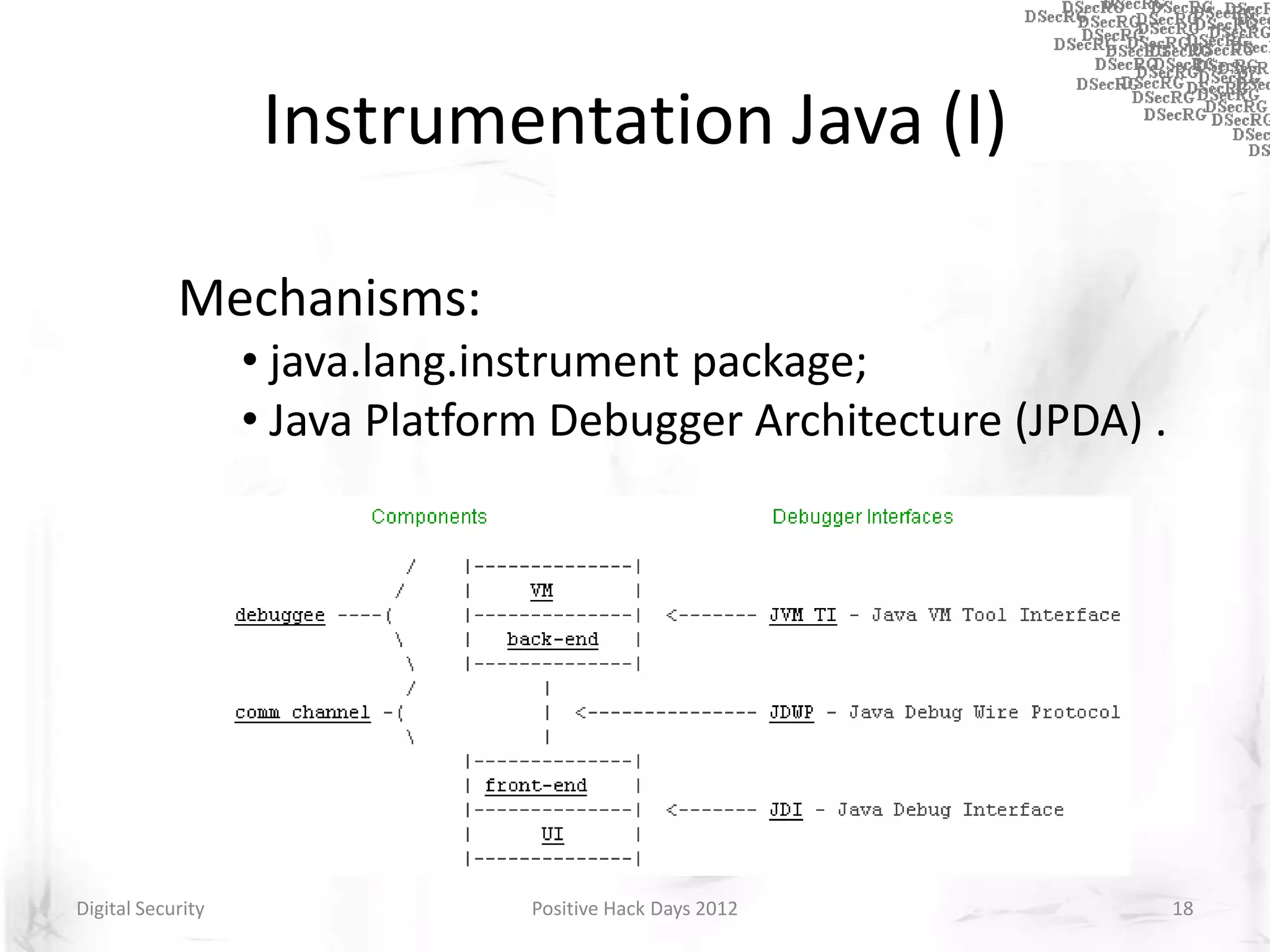
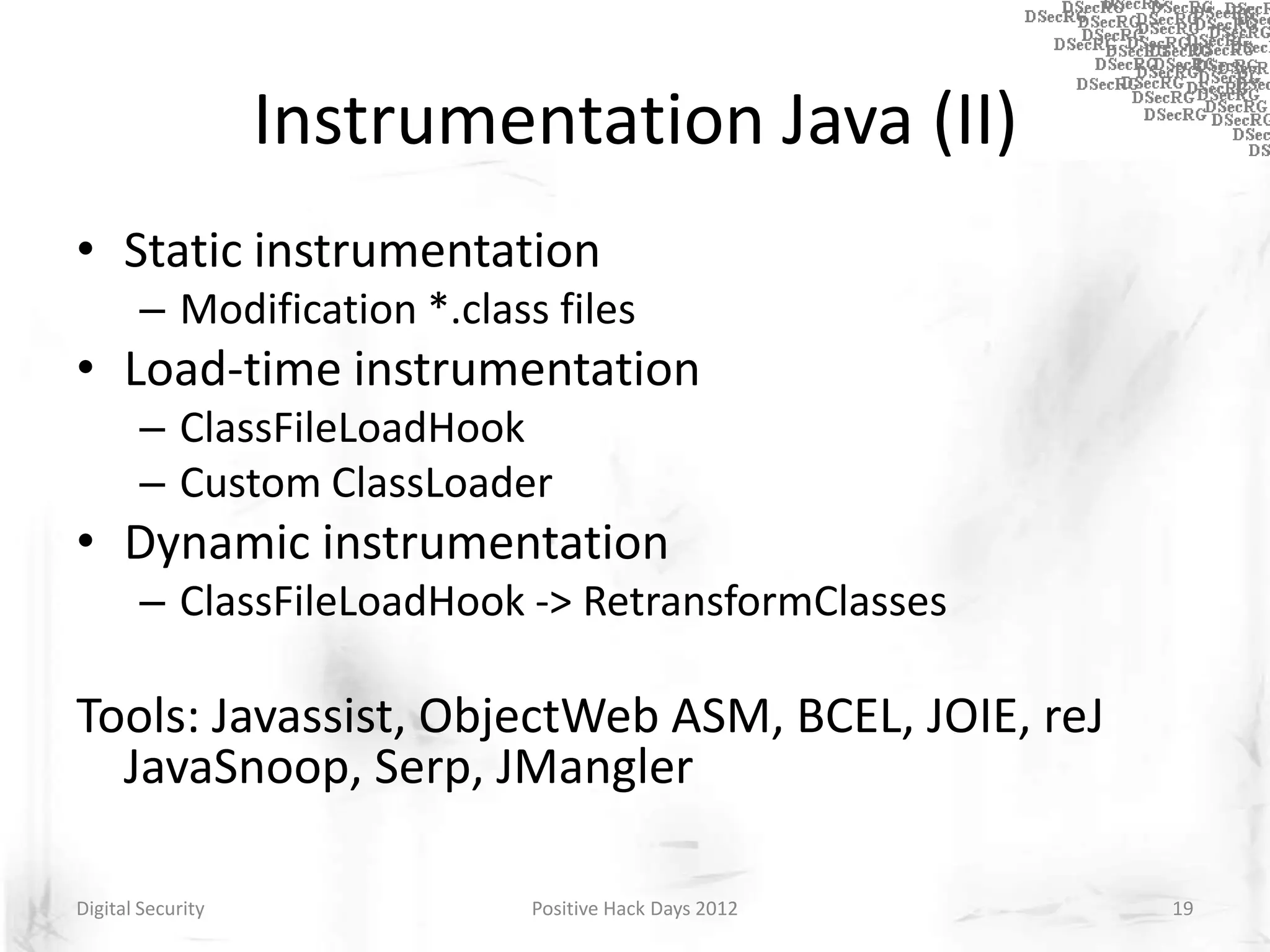
Instrumentation is a technique that adds extra code to a program or environment for monitoring or changing program behavior. It can be used for various purposes like performance analysis, automated debugging, error detection, and security testing. Instrumentation can be applied at different levels like source code, bytecode, or binary code. Common instrumentation techniques include static analysis, dynamic analysis, load-time instrumentation, and dynamic binary instrumentation. Instrumentation is useful for tasks like control flow analysis, vulnerability detection, malware analysis, and fuzzing.







![AVM2 Architecture
AS3
.abc
function (x:int):int {
return x+10
}
.abc parser
MIR
JIT Compiler
.abc
@1 arg +8// argv
getlocal 1 Verifier
Bytecode MIR Code Generator
@2 load [@1+4]
pushint 10
@3 imm 10
add
@4 add (@2,@3)
returnvalue
Interpreter MD Code Generator
@5 ret @4 // @4:eax
(x86, PPC, ARM, etc.)
x86
Runtime System (Type System, Object Model)
mov eax,(eap+8)
mov eax,(eax+4)
add eax,10
Memory Manager/Garbage Collector
ret
Digital Security Positive Hack Days 2012 22](https://image.slidesharecdn.com/lightanddarksideofcodeinstrumentationphd-120619023342-phpapp01/75/Light-And-Dark-Side-Of-Code-Instrumentation-22-2048.jpg)