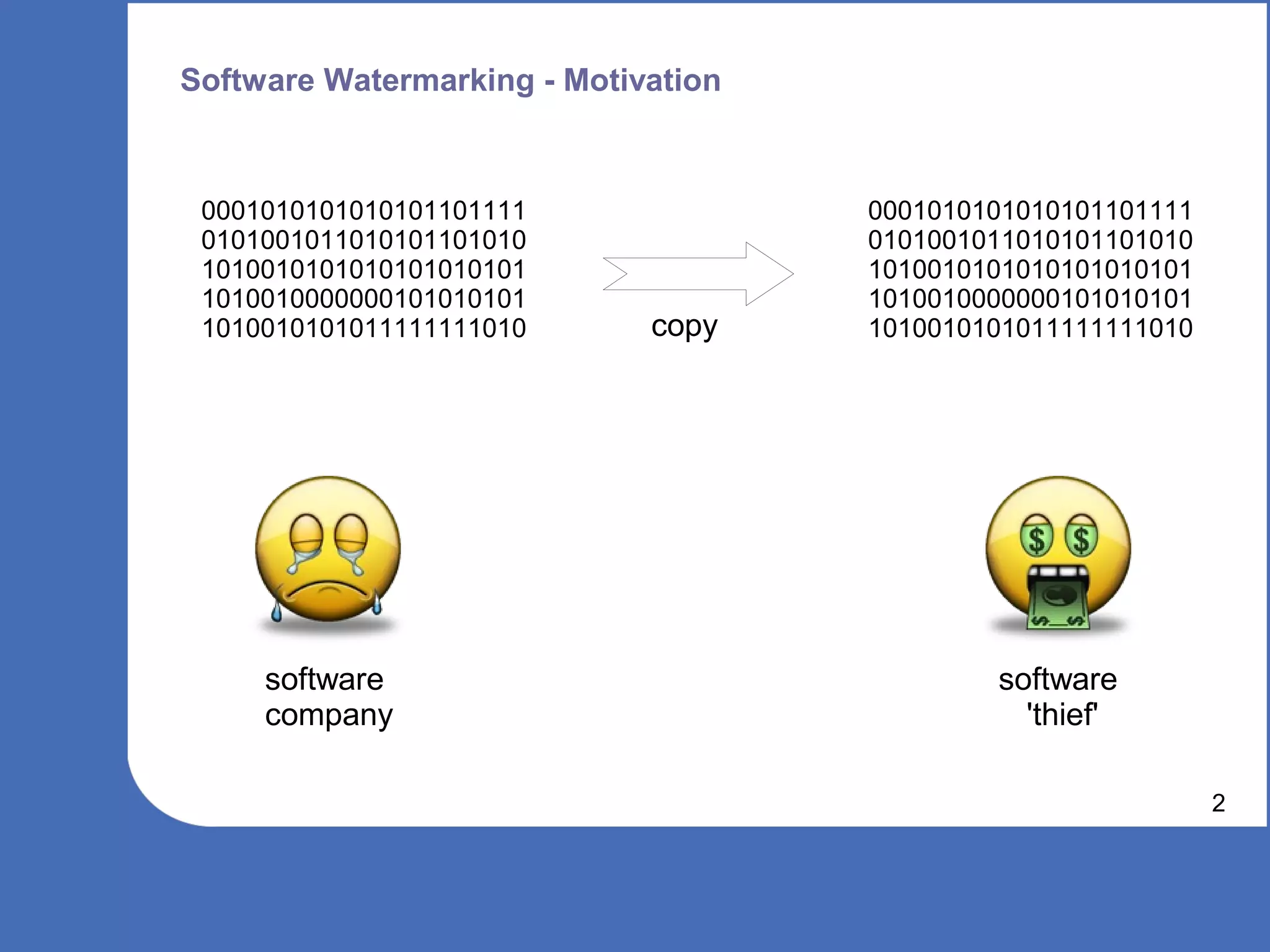
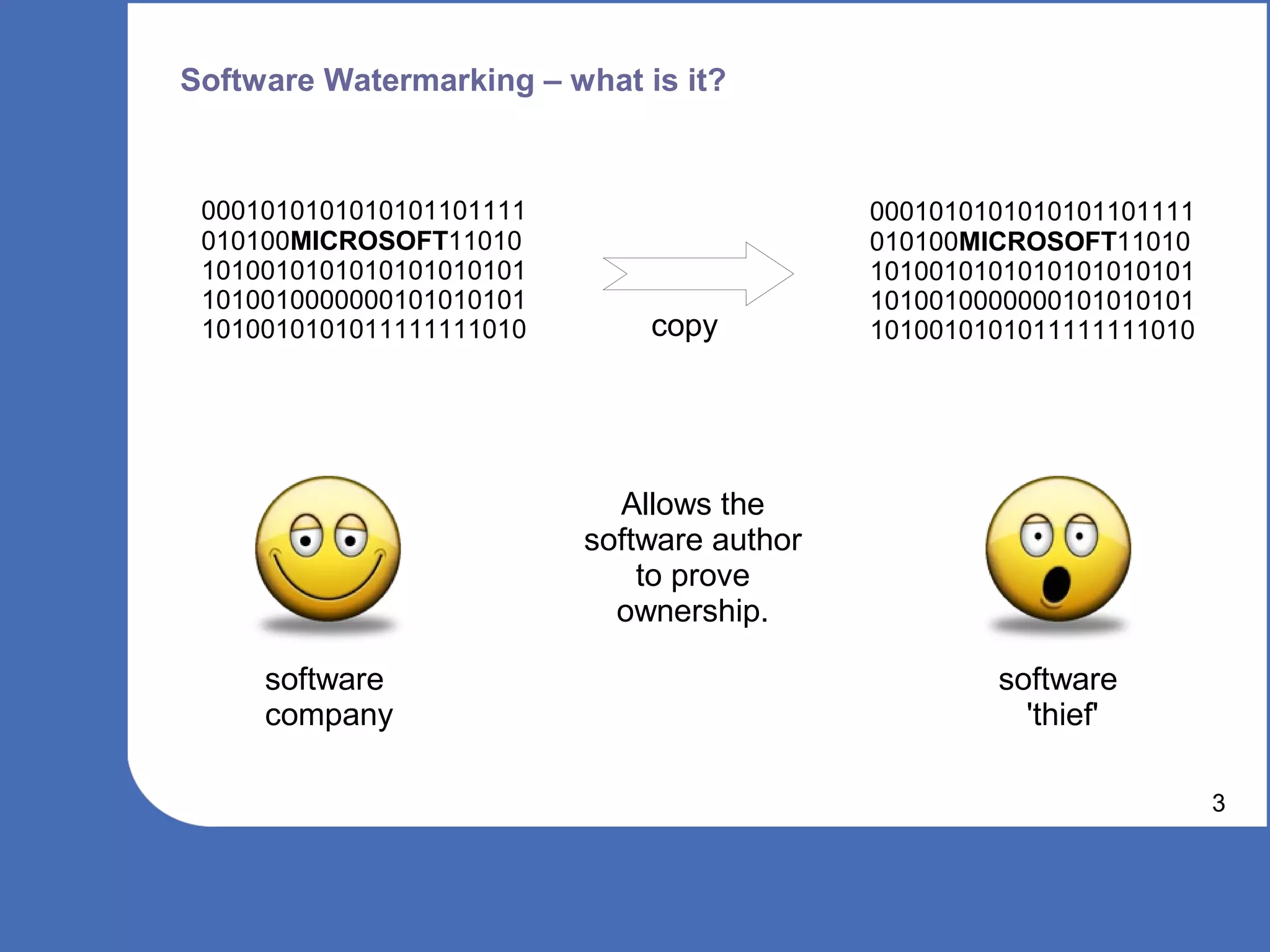
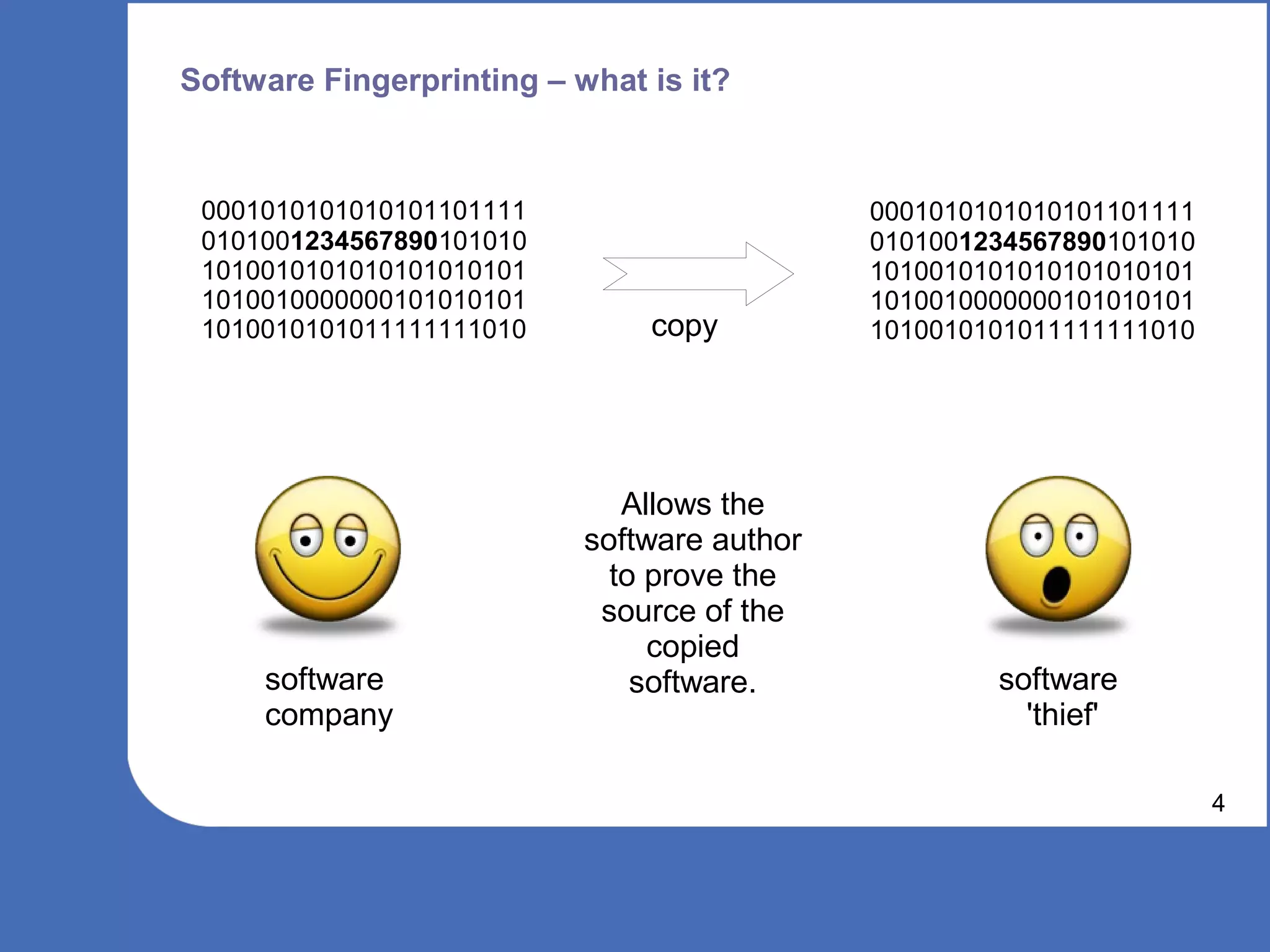
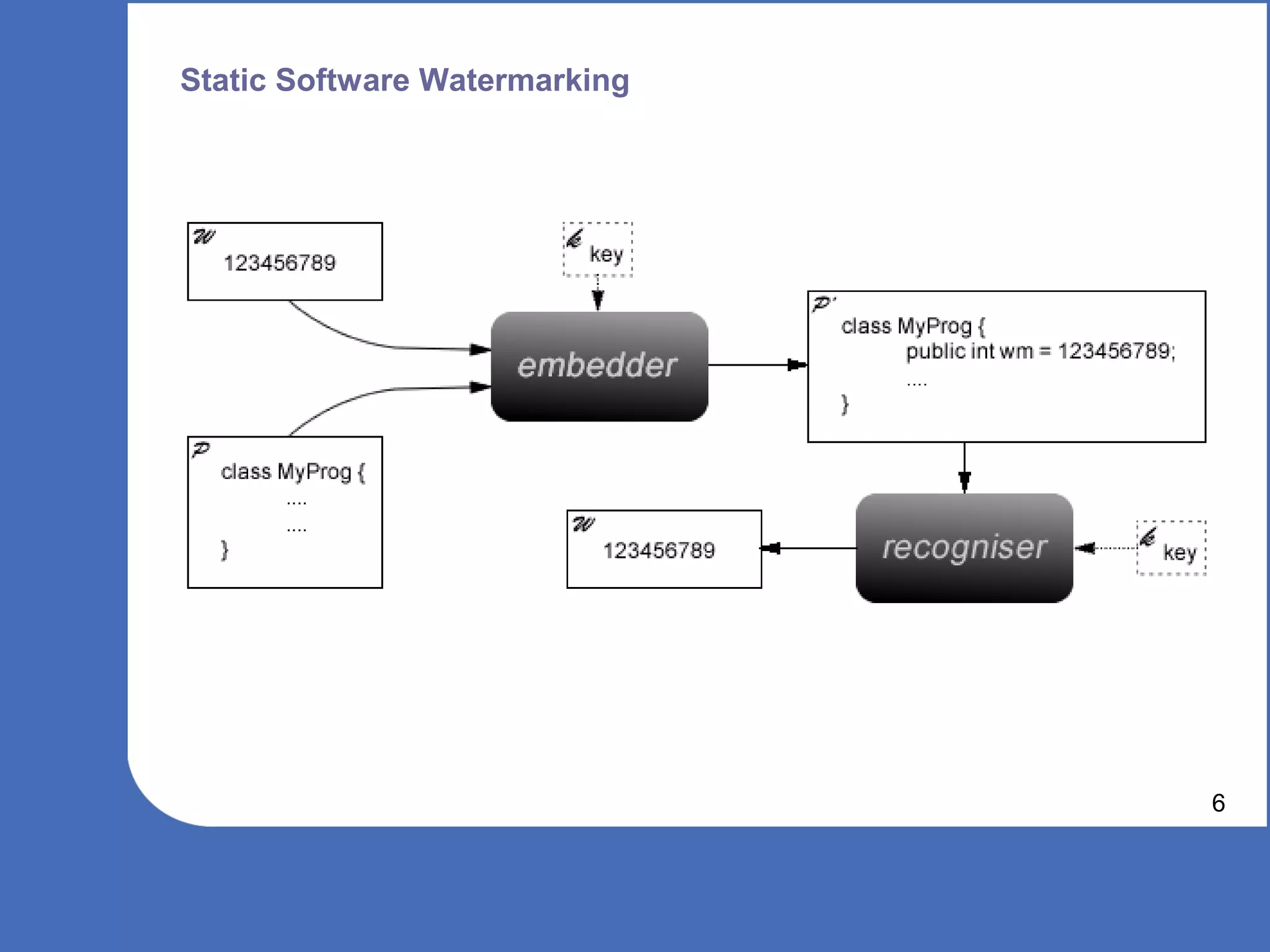
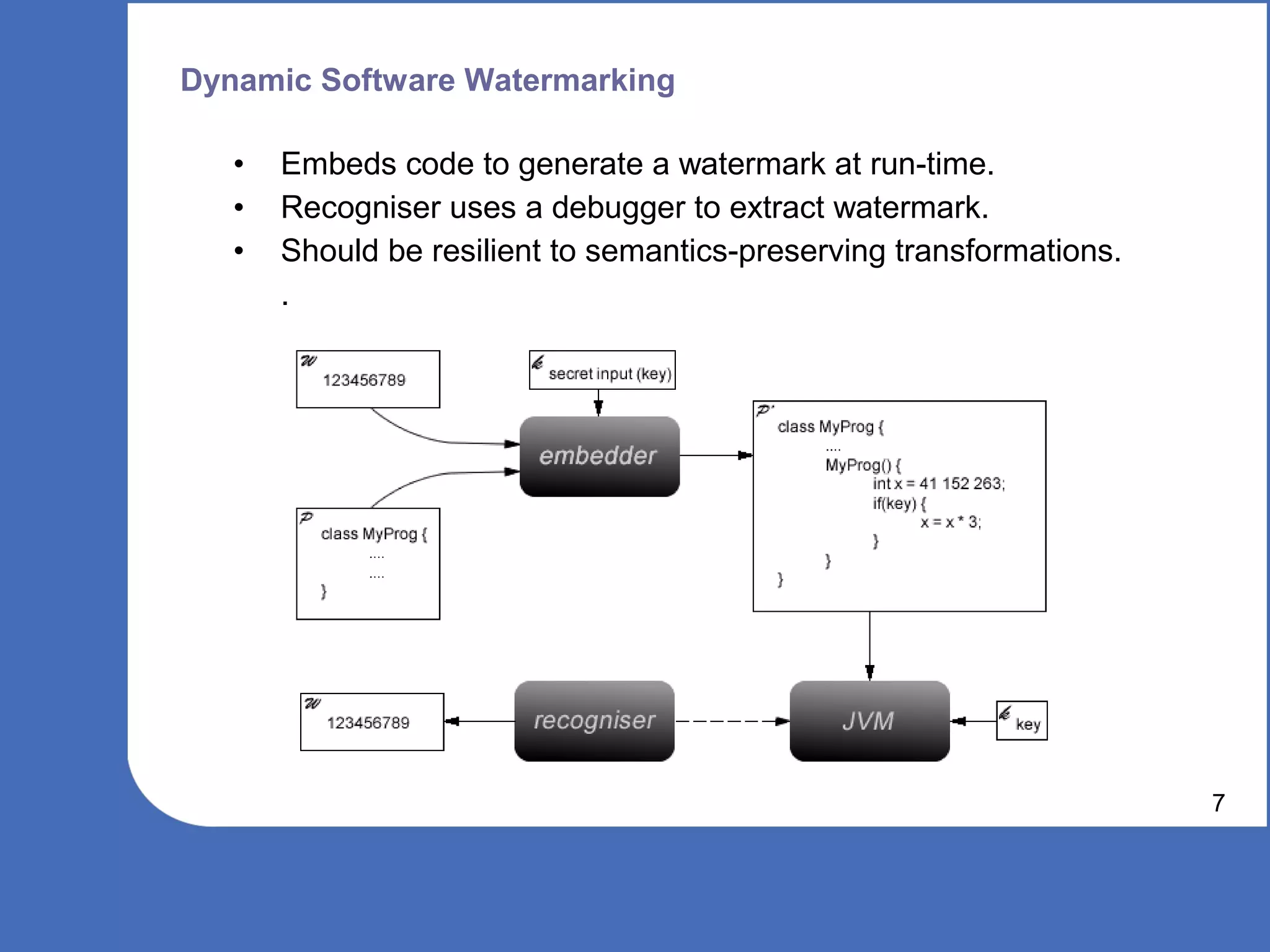
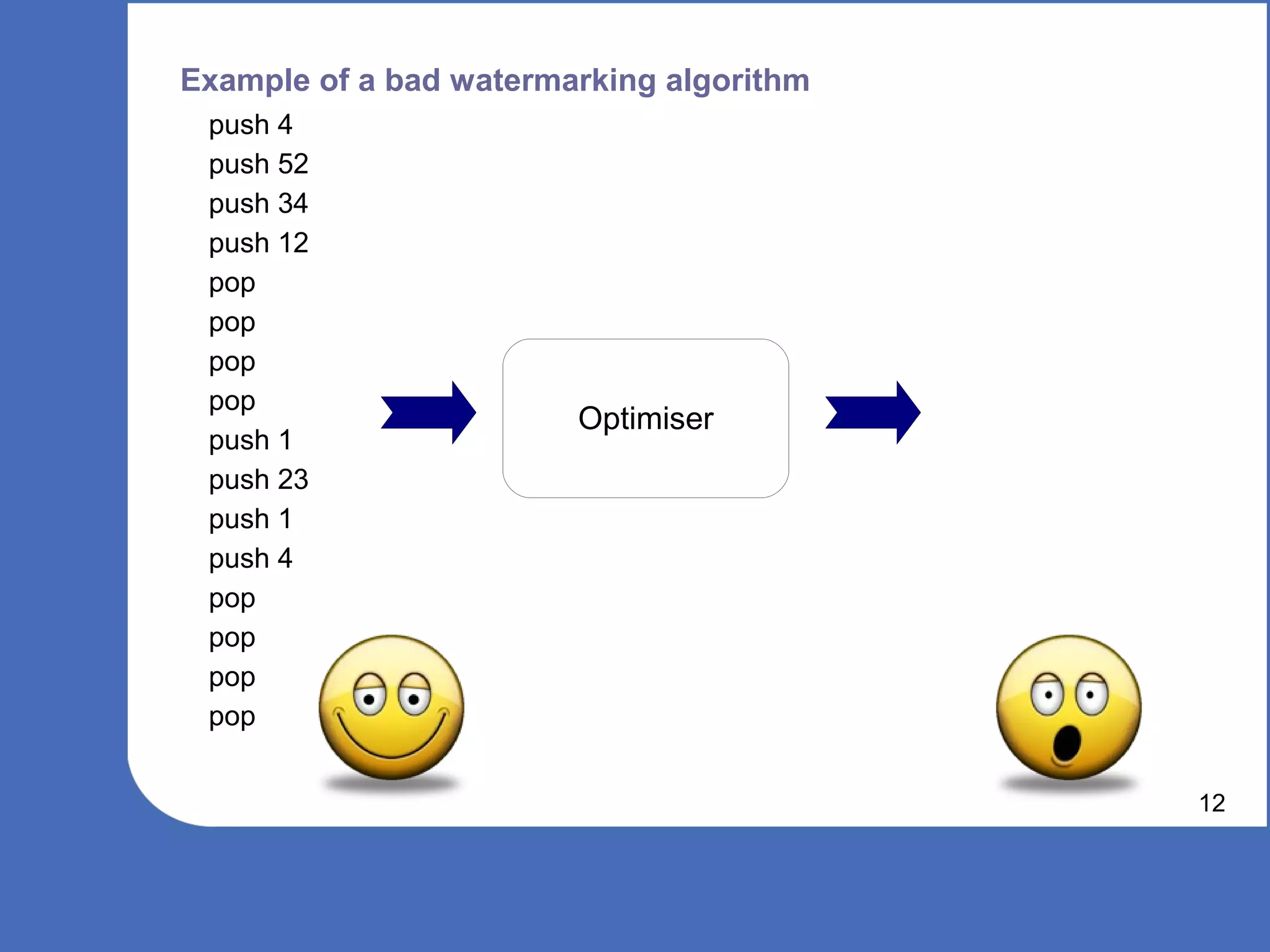
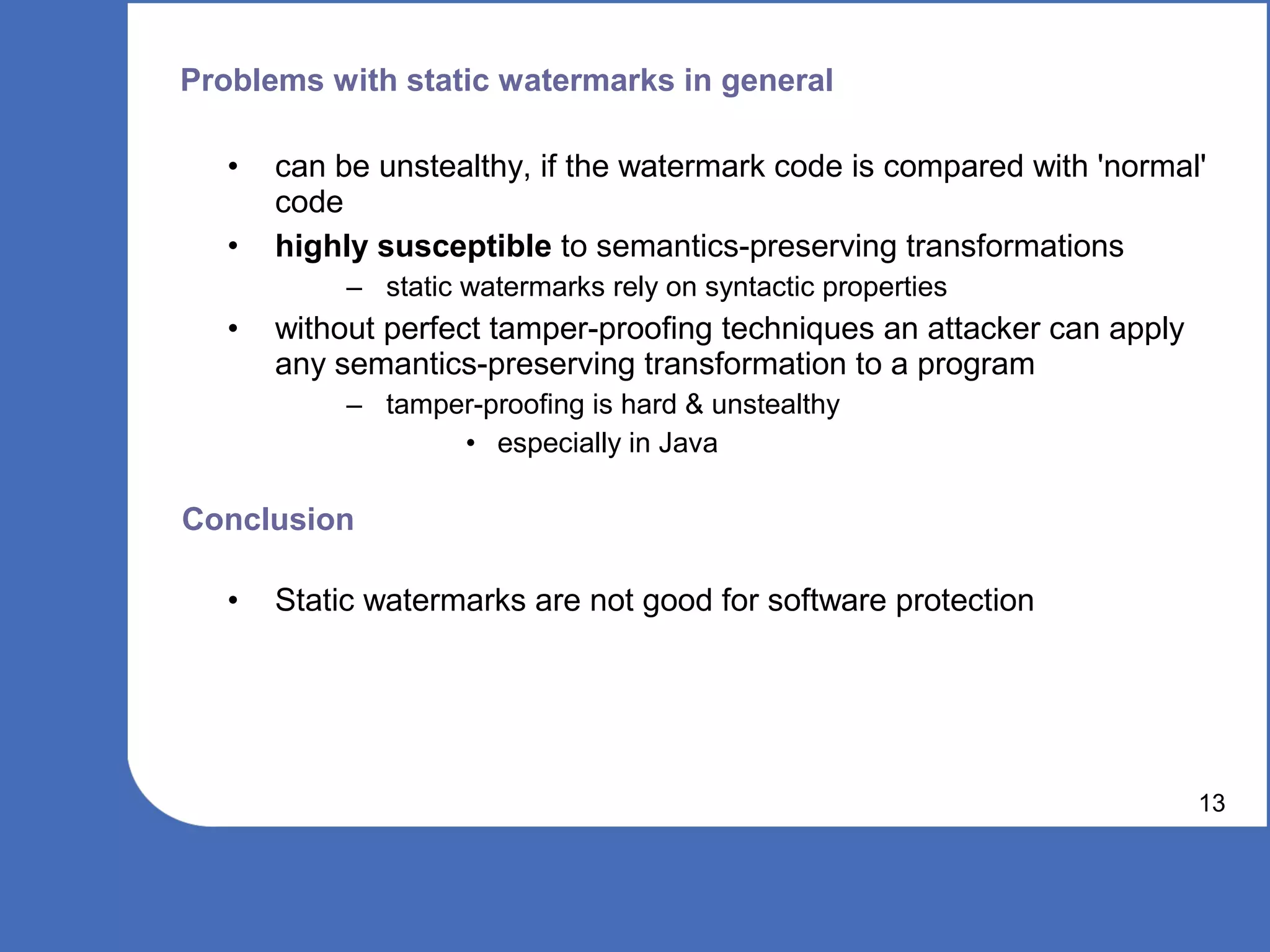
The document discusses software watermarking, explaining its purposes, types (static and dynamic), and the limitations of each. It highlights the vulnerabilities to semantics-preserving transformations and the challenges of using watermarks as proof of ownership. Ultimately, the conclusion questions the effectiveness and necessity of watermarking in software protection.

![Software Watermarking – what is it not?
• It does not prevent copying software.
• It does not prevent decompilation or program understanding.
• But it could be used in-conjunction with obfuscation (need to be
careful the obfuscation doesn't remove the watermark).
public class HelloWorld {
public String wm = “Microsoft”;
public static void main(String[] args) {
System.out.println(“Hello World”);
Decompile }
}
Obfuscate
5](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-5-2048.jpg)
![Code Replacement & Addition
• Very basic, early algorithms simply replaced sections of code, or
data, with watermark code.
• Susceptible to collusive attacks if the watermarks are placed in the
same location in every copy of a program.
• Monden et al. [1] encode the watermark as a sequence of bytecode
sequences which replace instructions in a dummy method.
– difficult to generate code which is similar to the original program
– easily remove by semantics-preserving transformations
8
[1] A. Monden, H. Iida, K.-ichi Matsumoto, K. Inoue, and K. Torii, “A practical method for watermarking java programs,” Computer
Software and Applications Conference, 2000. COMPSAC 2000. The 24th Annual International, Washington, DC, USA: IEEE, 2002,
p. 191–197.](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-8-2048.jpg)
![Code Re-Ordering
• The watermark is encoded as the
nth permutation of some set
• Davidson and Myhrvold [1]
encode the watermark as the nth
permutation of the set of basic
blocks in a method.
– higly unstealthy due to a
greater ratio of goto
instructions [2]
• Another option, in Java, is to re-
order the constant pool (Gong et
al.)
• Requires the original program
from comparison
9
[1] R.I. Davidson and N. Myhrvold, “Method and system for generating and auditing a signature for a computer program,” US
Patent 5,559,884, Sep. 1996.
[2] Myles, G. et al., 2005. The evaluation of two software watermarking algorithms. Softw. Pract. Exper., 35(10), 923–938.
[3] D. Gong, F. Liu, B. Lu, and P. Wang, “Hiding Informationin in Java Class File,” International Symposium on Computer
Science and Computational Technology, 2008. ISCSCT ’08., IEEE Computer Society, 2008, pp. 160-164.](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-9-2048.jpg)
![Register Allocation
• the watermark is encoded in the
interference graph, which is used to
model the relationship between
variables.
• each vertex represents a variable and
an edge between the two variables
indicates that their live ranges overlap.
• we colour the graph in order to
minimise the number of registers and
ensure that two live variables do no
share a register.
• QP algorithm [1] adds edges to the
graph
• QP is flawed; QPS, QPI, CC and CP
followed with a similar idea.
10
[1] G. Qu and K. Potkonjak, “Analysis of watermarking techniques for graph coloring problem,” Computer-Aided Design, 1998.
ICCAD 98. Digest of Technical Papers. 1998 IEEE/ACM International Conference on, San Jose, California, United States: IEEE,
2005, p. 190–193.](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-10-2048.jpg)
![Graph Watermarking
• Venkatesan et al. [1] encode the watermark in a CFG and 'connect'
it to the original program.
11
[1] R. Venkatesan, V. Vazirani, and S. Sinha, “A graph theoretic approach to software watermarking,” Information Hiding,
Springer, 2001, p. 157–168.](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-11-2048.jpg)


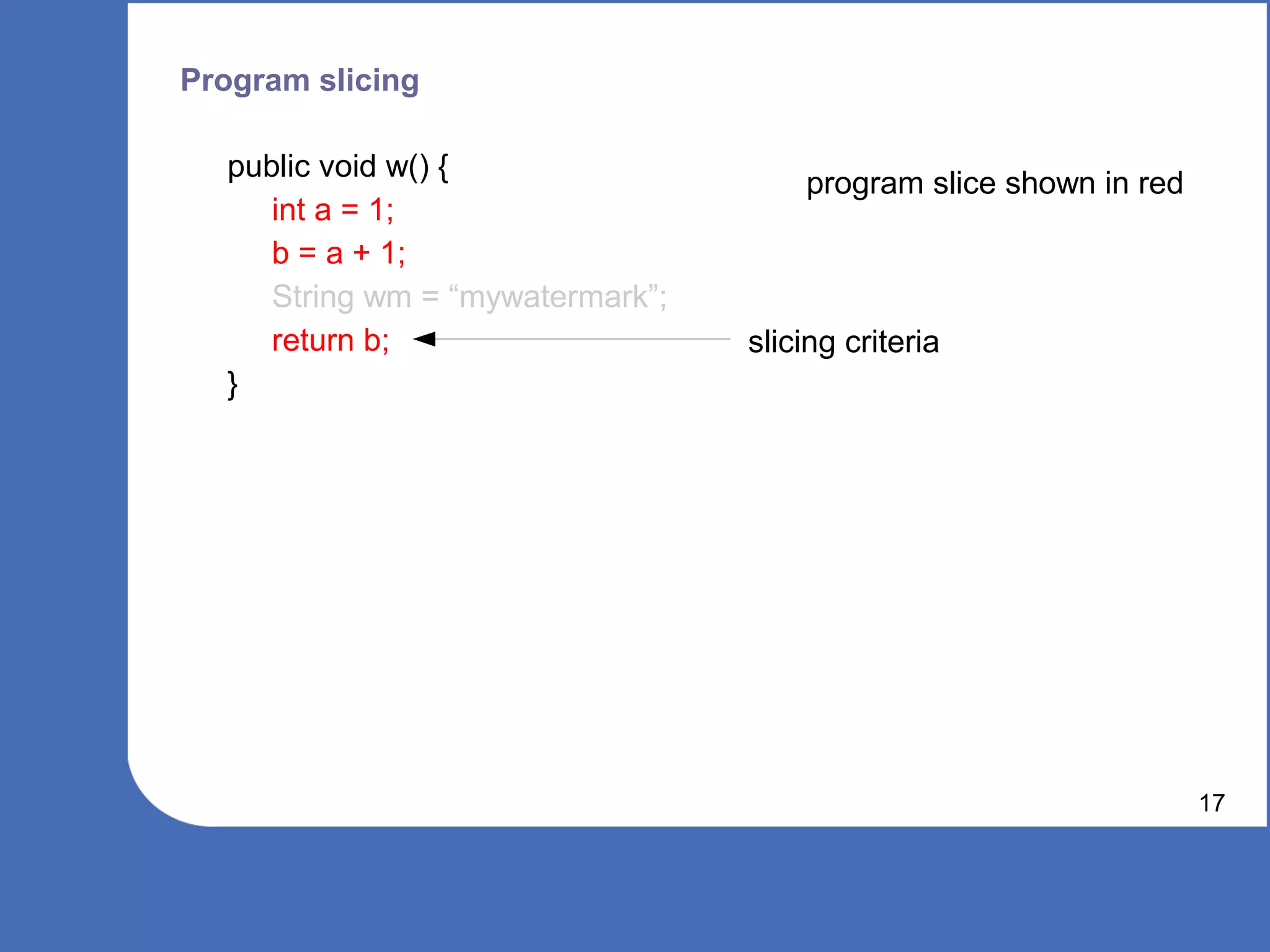
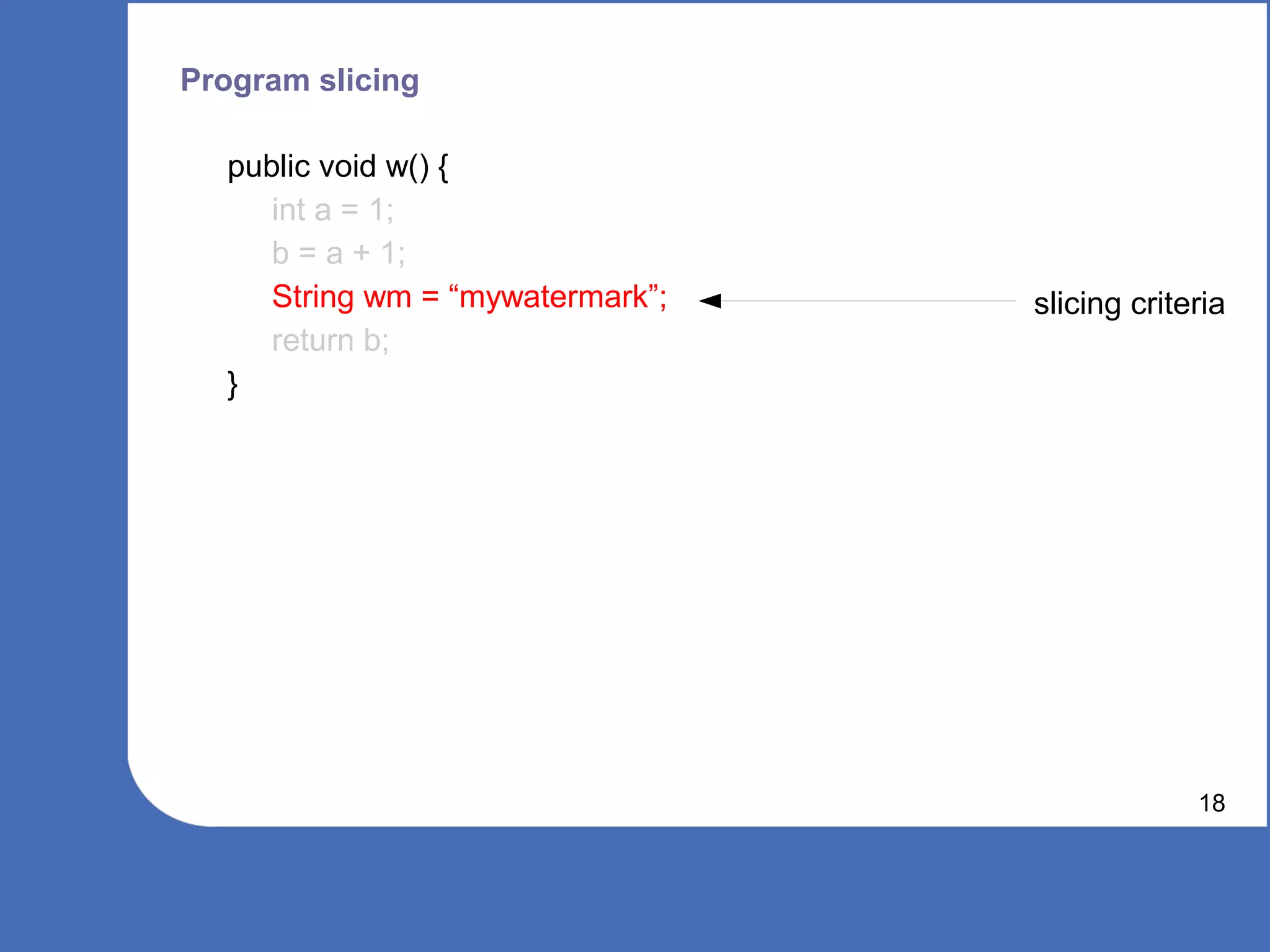
![Program slicing
public void w() {
int a = 1;
b = a + 1;
String wm = “mywatermark”;
return b; slicing criteria
}
Program Slice [1]: An independent program guaranteed to faithfully
represent the original program within the domain of the specified subset of
behaviour
16
[1] Weiser, M., 1981. Program slicing. In ICSE '81: Proceedings of the 5th international conference on Software engineering.
Piscataway, NJ, USA: IEEE Press, p. 439―449.](https://image.slidesharecdn.com/wcis2011-110226071902-phpapp02/75/Static-Software-Watermarking-16-2048.jpg)