Azure PIM Role Activation Requires MFA and Approval
•
1 like•333 views
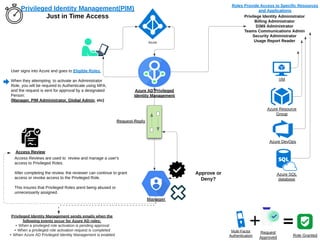
Provides a visual representation of a user requesting access to a Privileged Azure Role. Just in Time access insures that Privileged accounts are only used when absolutely needed. You can also optionally designate Approver(s) to approve or deny privileged account requests. Lastly, Access Reviews allow Administrators to Audit Privileged Access use, and then determine if access to still necessary or needs to be Revoked or tweaked.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
Building Your Roadmap Sucessful Identity And Access Management

Building Your Roadmap Sucessful Identity And Access ManagementGovernment Technology Exhibition and Conference
More Related Content
What's hot
Building Your Roadmap Sucessful Identity And Access Management

Building Your Roadmap Sucessful Identity And Access ManagementGovernment Technology Exhibition and Conference
What's hot (20)
Building Your Roadmap Sucessful Identity And Access Management

Building Your Roadmap Sucessful Identity And Access Management
Privileged Access Management - Unsticking Your PAM Program - CIS 2015

Privileged Access Management - Unsticking Your PAM Program - CIS 2015
SCCM Intune Windows 10 Co Management Architecture Decisions

SCCM Intune Windows 10 Co Management Architecture Decisions
3 Modern Security - Secure identities to reach zero trust with AAD

3 Modern Security - Secure identities to reach zero trust with AAD
Identity and Access Management (IAM): Benefits and Best Practices 

Identity and Access Management (IAM): Benefits and Best Practices
Similar to Azure PIM Role Activation Requires MFA and Approval
Similar to Azure PIM Role Activation Requires MFA and Approval (20)
SC-900 Capabilities of Microsoft Identity and Access Management Solutions

SC-900 Capabilities of Microsoft Identity and Access Management Solutions
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Unlocking the Potential of the Cloud for IBM Power Systems

Unlocking the Potential of the Cloud for IBM Power Systems
Azure PIM Role Activation Requires MFA and Approval
- 1. User signs into Azure and goes to Eligible Roles. When they attempting to activate an Administrator Role, you will be required to Authenticate using MFA, and the request is sent for approval by a designated Person: (Manager, PIM Administrator, Global Admin, etc) Roles Provide Access to Specific Resources and Applications Request-Reply Access Reviews are used to review and manage a user's access to Privileged Roles. After completing the review, the reviewer can continue to grant access or revoke access to the Privileged Role. This insures that Privileged Roles arent being abused or unnecessarily assigned. Approve or Deny? Privileged Identity Management sends emails when the following events occur for Azure AD roles: - When a privileged role activation is pending approval - When a privileged role activation request is completed - When Azure AD Privileged Identity Management is enabled Privilege Identity Administrator Billing Administrator D365 Administrator Teams Communications Admin Security Administrator Usage Report Reader Azure Azure Resource Group VM Azure AD Privileged Identity Management Manager Access Review Azure DevOps Azure SQL database Privileged Identity Management(PIM) Just in Time Access Role Granted Multi-Factor Authentication Request Approved
