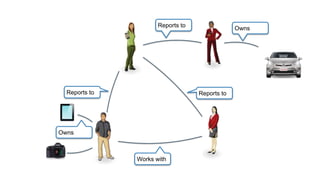
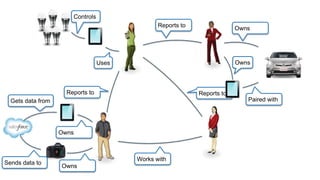
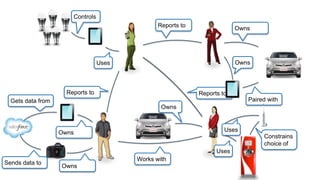
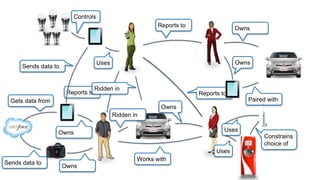
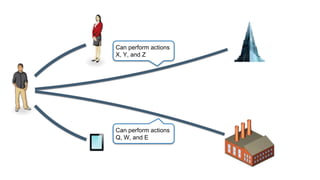
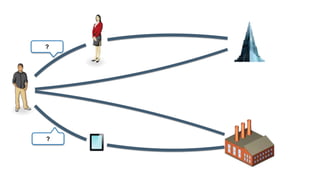
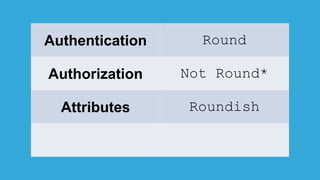
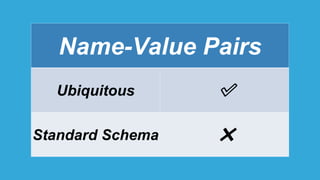
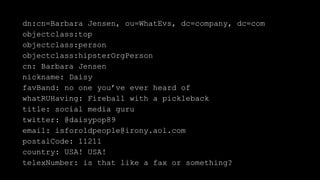
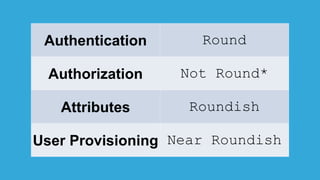
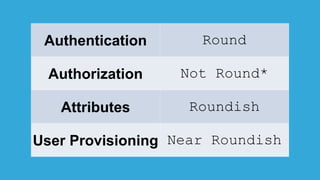
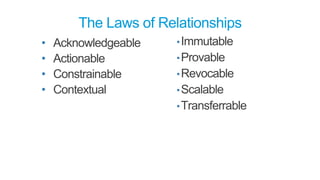
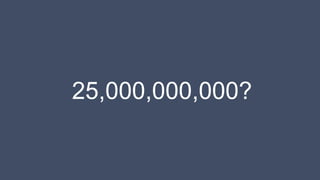The document discusses how identity management systems continually reinvent themselves as tasks and requirements change, similar to how humans reinvent the wheel. It examines how authentication, authorization, attributes, and user provisioning have evolved through multiple standards and protocols. While progress has been made, opportunities remain to adopt modern standards, help others adopt standards, demand standards from technology and service providers, and establish identity relationship management to connect organizations and services in a standards-based way. The goal is to develop interoperable, round wheels that can effectively handle the loads of relating people, devices, and things.