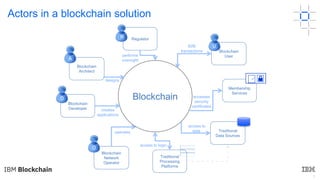
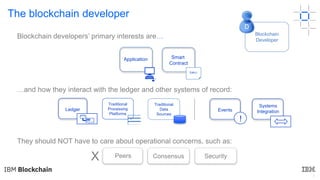
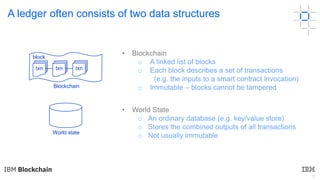
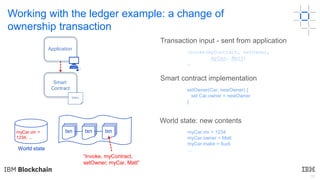
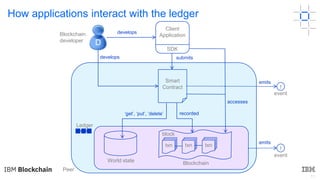
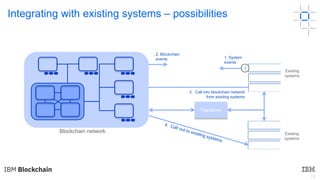
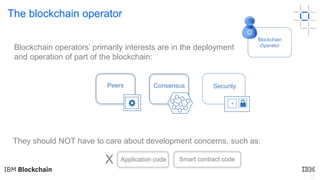
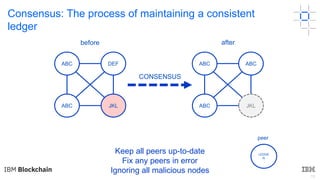
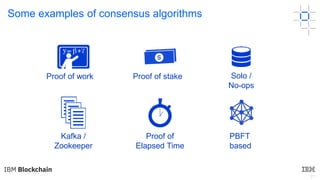
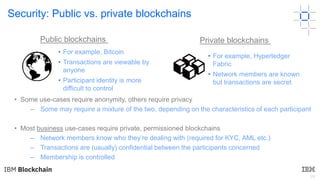
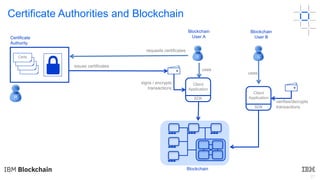
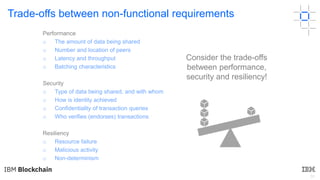
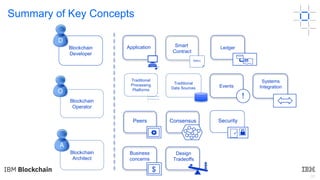
This document discusses key concepts and components related to blockchain solutions, including actors such as users, developers, operators, and architects. It describes various components that make up blockchain solutions such as ledgers, smart contracts, consensus mechanisms, and how applications interact with blockchains. It also covers considerations for blockchain developers and operators, and challenges around integrating blockchains with existing systems and achieving determinism.