Beyond the ones and zeros security leadership- fonts required
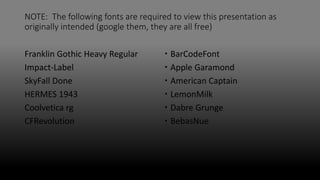
- 1. NOTE: The following fonts are required to view this presentation as originally intended (google them, they are all free) Franklin Gothic Heavy Regular Impact-Label SkyFall Done HERMES 1943 Coolvetica rg CFRevolution BarCodeFont Apple Garamond American Captain LemonMilk Dabre Grunge BebasNue
- 2. ONES AND ZEROS ALIGNING EFFECTIVE INFOSEC AND PEOPLE LEADERSHIP PRINCIPLES
- 3. What this presentation is: A discussion of leadership principles to develop better leaders, within an InfoSec context. Hopefully useful to you A lecture – I am not an expert! Or thought leader! Or RockStar (more on that later) Technical About hacking (except yourself) A How-To guide What this presentation isn’t: Just so we’re clear…
- 4. So Who Am I? Husband Dad Enterprise Security Architect Golfer Amateur Historian Runner (on occasion) Currently in Financial Sector Previously in DoD Space Traveler Co-Owner of an NFL Franchise Spartan Warrior (if I survive) But in the End…
- 5. About Me It’s Not Or You…
- 8. My why: To be a positive enabler for those around me, both personally and professionally. What’s Yours?
- 9. Values It’s not hard to make decisions when you know what your values are. -Roy Disney Mine: Authenticity Family Faith
- 10. LaaS: Leadership as a Service
- 12. Doing the right things for the right reasons: Your primary job as a leader is taking care of your people, period. Or…
- 13. TRUST Treat employees like they make a difference, and they will. -Jim Goodnight CEO, SAS
- 14. CURA TE IPSUM Take care of yourself first!
- 16. SILOS
- 17. BUSINESSES WANT AND NEED PARTNERS AND ALLIES, NOT MINDERS AND GATEKEEPERS.
- 20. Development (personal, professional, technical) + Leadership = Engaged Employees Happy Wife Engaged Employees Great Customer Experience Loyal Customers Strong Financial Results Happy Life The Principle
- 22. Our industry isn’t as binary as Some would have you believe.
- 23. In the end: Discover your Why Determine your Values Practice LaaS Get your vision checked Balance the Clock and Compass Heal yourself first
- 24. Destroy Silos Be an Ally and a Partner Be Transparent Hire for Competence not (just) technical Be a good House Band member, not a Rockstar It isn’t all about Ones and Zeros In the end:
- 25. Pwn who you are. Exploit your strengths. Mitigate your weaknesses.
- 26. Words may inspire, but only action creates change.
Editor's Notes
- What This Presentation Is/Isn’t First and foremost, I am not an expert!!! This just happens to be something that I care a lot about, and feel is important to for our industry. I am NOT a speaker. That’s it. I don’t have cool anecdote to begin, so we here we go…
- Who am I? A little about me… If anybody has any tips for a Spartan Race (besides don’t!) come see me afterwards. My background is primarily in DoD, now in financial sector – Enterprise Security Architect for First Financial Bank, 6B+ in assets, in Abilene. Lived overseas – Misawa , Japan, Moron AB, Spain while AD USAF, went to school in Scotland to get a degree in Scottish History, worked in Afghanistan with biometrics, Stuttgart, Germany, Kwajalein Atoll in the Marshall Islands – went from tropical weather to Lubbock. Then San Antonio, then back to Afghanistan, now back in Abilene. So I’ve been around, infosec in a lot of different environments and contexts. Some are more secure than others. But they all have one core commonality between them – leadership.
- It’s Not About Me Or You… It’s about how you can help, and serve, others.
- Leadership: It’s About the People Leadership is about leading people, including, but not limited to, yourself. In my experience, I have found that some of the best technical practitioners couldn’t lead a parade down main street… and that doesn’t cut it in today’s world. We are InfoSec People, but we live in a business world – a world that we didn’t build. While today we think of security as the foundation of our organizations, our lines of business most likely see it very differently… We struggle to align our goals, our values, and our efforts to those of our business. Some are decidedly better than others. But the bottom line, if you want to want to maximize your impact in your job, in your life, you have to start with why.
- Start with Why The Concept of Start with Why originated with Simon Sinek, and has become one of the most-viewed TED Talks ever, with almost 22 million views to date. His theory focuses on defining 3 things: WHAT you do you, HOW you do it, and most importantly, WHY you do it. The fundamental premise of Start with why, are these questions: What is your fundamental cause, or belief – what human problem are you working to solve? Why are you here? Why are you in the position that you are in? What drives you to get out of bed in the morning? What greater cause are you promoting? It’s really easy to answer the first one: WHAT you do. In InfoSec, we provide secure technology solutions to allow our businesses to function at its desired level within its specified risk tolerance. (More or less) From a business perspective, a company’s what may be ‘We make widgets.’ Or something very similar to that; define what works best for you. How you do it – this is a little more complicated than the what. The How is the support for the why. It is the movers and shakers of the infrastructure – the things (and people) that translate WHY we do , into WHAT we do. The WHY is what is critical. And the hardest to define. Why are you here? Why do you do, what you do? - This goes WAY beyond InfoSec. Why do you show up every day? Why do you show up here, instead of somewhere else, in some other occupation? Paychecks and recognition – those are results of WHY you do what you do, not they WHY itself.
- My Why: My personal why: To be a ‘positive enabler’ for those around me, both personally and professionally. My why isn’t specific to Information Security – I’d like to think that I’m at a minimum marginally successful and good at what I do, and I LIKE infosec, but if I ever did switch gears to something else, My Why will always be the same. It doesn’t depend on external factors. Figuring this out for me really was a ‘lightbulb’ moment. For My Why, this means giving others the tools, resources, and inspiration so THEY can succeed, at work and in life in general. This is what makes me happy; this is what I feel gives me meaning. What are your motivations? Everyone in a leadership role is there by choice, to some degree. We are ALL Leaders – and ALL leaders start by leading themselves. It isn’t about ability, but responsibility.
- Values What motivates you to be a leader? Is it a desire to see a change in your organization, in your community, in your industry? . Values – What standards do you have? My top three values: Authenticity, Family, and Faith Authenticity: Being authentic is one of the biggest indicators of success, however you measure it… it’s like pencil-whipping an audit or accreditation report: You’ll eventually be found out. True authenticity opens doors, establishes healthy relationships, and the best part: you don’t have to keep up propping yourself up. Family: My family keeps me going. I’d really suck at being me, without them. Faith: My beliefs keep me rooted, and influences my other values, and My Why. Knowing your values simplifies decision making; and being open to change doesn’t necessarily mean you have to give up your values. I encourage you think about what yours are, and how they influence you day in and day out.
- LaaS There’s already been a lot written on what I call LaaS, also known as Servant Leadership. Most of it is really good! One of the US Air Force’s core values is Service Before Self. That is LaaS; that is Servant Leadership; that is Authentic Leadership summed up in three words. This embodies in a nutshell what servant leadership is: you are essentially a connector of dots; a matchmaker, a doer of untold deeds. What is servant leadership to you – how do YOU define it? To me: Servant Leadership is Authentic. It requires: Listening (empathize, understand and relate) Requires Selflessness – putting others first Requires Trust – those above you, and those below you – note I said below, not beneath. HUGE difference. What it isn’t: Micromanaging – trust and control must be given, AND earned. Don’t play the blame game when mistakes are made. Servant leaders take ownership, not credit. Servant leadership is one of the most powerful concepts you can ever use as a leader.
- ‘The Vision Thing’ What is vision? It can be defined as a set of goals or attributes that describe a future state which we work to attain and implement. Big Hairy Audacious Goals (BHAGs) are great for helping to define your InfoSec vision. Smaller, more immediate goals can also show progress towards realization of your vision. ‘Excellence is not an ‘aspiration’ – Excellence IS what you do in the next 5 minutes. –Tom Peters However, we need to expand a little broader than just InfoSec if we want to be effective and understand where we want to go, and where we need to be. How well does that vision support your organization’s business strategy? That strategy should help influence your vision (your ideal end-state or broad goal.) Conversely, does the business strategy take into account the role InfoSec will play in driving future growth and success? If the vision is blurry, get your eyes checked – you need a different vision, or a different environment. You probably only have control over how well your vision contributes to organizational success, not the other way around… life’s tough, wear a helmet. Start by leading yourself… if you look like you don’t know where you are going - a lack of vision – that’s not encouraging others to follow. And they won’t. Stevie Wonder’s the only blind man to lead a parade.
- A Clock or a Compass? Steven R. Covey once gave an example about prioritizations, and asked people do decide which was more important to have as a representation of how they lived their life: a clock or a compass. If you say clock, you tend to deal with short-term issues day in and day out, and tomorrow is like Groundhog Day – you fight the same fires and battles the next day in a never-ending cycle. It is efficient, and produces results, but you really don’t make any progress toward satisfying your vision, and in turn, your why. Essentially, what you are doing – efficiency. The Compass signifies that direction and trajectory are more important than the essentially mundane, day-to-day chaff we all get caught up in. Essentially, where you are going – effectiveness. Which one is more important to you? You have to find the right balance between the two.
- Trust This is probably the most clichéd slide out there for leadership: Trust. While I was in the Air Force, my first Squadron Commander at Misawa, Japan shared a principle that really stuck with me. Traditional military doctrine says ‘The mission comes first.’ i.e., before self, before family, etc., that the mission is so important that nothing can be allowed to get in the way of executing your role in the mission. Maj Collat had a different take on that principle: People come first. Take care of your people (your family, yourself) first, THEN you will be in the right mindset – free of distractions – to take care of the mission. If you don’t truly care about those you are leading, you are in the wrong position. (This ties back into LaaS/Servant leadership) And you can’t solve problems by throwing more bodies at a problem – you have to spend time building relationships and trust to empower the people you already have. Empowerment builds trust, and trust build empowerment. You had better be prepared to back up your words with actions if you want to maintain trust. Help your team to trust each other. Consistency is one of the most fundamental building blocks of trust. ‘Great leaders and great organizations are good at seeing what most of us can’t see. They are good at giving us things we never think of asking for.’ -Simon Sinek
- Cura Te Ipsum: Heal Yourself First Self-development is critical, including business, people-skills (including leadership skills), AND technical skills. Soft skills can make or break your career. Jack Welch said, ‘In real life, strategy is very straightforward. Pick a general direction… and IMPLEMENT LIKE HELL. Advancing your own career and adding value to your organization don’t have to be mutually exclusive agendas, and a lot of times, that’s how we treat them. Growth is just as important as execution, for yourself just as much as your team When oxygen masks deploy, you put yours on first… Leaders go first – and Leaders eat last. You have to know your strengths, and lead from them Bottom line: GET AFTER IT, and set the tone for your people All of these slides and points can be used in both your personal life, AND in making our industry better… but you still have to start with you.
- InfoSec Leadership So let’s switch gears a bit… these are more infosec-oriented.
- Silos Have you ever ran Cat5? How much of a pain would it be, if each strand was independent of each other, and had to be run independently? We have siloed ourselves away from the day-to-day realities of our business, and have convinced ourselves that security is the most important thing in the history of EVER, and it’s not. We have to become contextual enablers. We need to move away from the mindset of security first, to secure business first. You can’t do that without input and feedback from the business to determine where they are going (vision) and then determining what you can do to support that. When’s the last time you asked someone, ‘How can I (securely) enable you to do your job better? How can I add value to you, from a security context?’ Too many are focusing on the technical solutions, without regard for actual business need. The end result? Users actively undermine you and work around you, so they can accomplish what THEY feel is important. (shadow IT) We can’t just focus on technology and ignore building and developing ourselves, our teams, and our organizations. Communication skills are, far and away, the most important skills you need to have in your tool box. And InfoSec people are great are NOT communicating – ‘the less I reveal, the more secure I am.’ We have to break out of this mindset and recognize that we can’t function effectively in our own silo – we have to become partners with the business.
- Businesses want and need allies and partners, not minders and gatekeepers. To paraphrase Albert Einstein: Do you want to be successful, or add value? The former doesn’t always lead to the latter. You can (arguably) be successful, while not provide any value to your organization. This is where the concept of aligned vision really matters. There is a fundamental lack of effective leadership to develop our people to interact positively with the business side, and understand their needs. Some of that is the inherent difference between technology and business; some is that we haven’t grasped that, like it or not, we are all in marketing. If you can’t sell (i.e., define) a problem to your executive leadership, and how it solves a particular problem for them - that you have persuaded them to care about - they won’t be persuaded to invest in your solution. (Seth Godin calls this ‘Pitchcraft.’) Some of the most successful InfoSec people are awesome story tellers, and that’s not a coincidence. Initiatives like the Analogies Project help us tell our stories in meaningful ways. It’s a bit of a chicken and egg proposition as well – it’s hard to provide meaningful metrics and data without investing in the tools that provide meaningful metrics and risk data. And getting the right balance is hard! You HAVE to get the vision, and the clock/compass balance right, to be able to meet the needs of the business. In medicine, prescription prior to diagnosis is malpractice. We owe it to ourselves, and our organizations, to be effective leaders in our spheres of influence. This includes identifying/growing leaders and seeing our industry from the outside in, not just inside out. There is so much success in InfoSec that is lost when we only focus on just technical skills and talent. We have to be who our customers want, and need, us to be.
- BE TRANSPARENT. With everything you do, and how you do it. InfoSec is not a fiefdom – it exists to secure the business, to their risk appetite level. Hoarding data, resources, etc. will hurt you and your team - and the business – in the long run. The quickest way to erode trust is to NOT be transparent. You should be able to articulate – to anyone in your organization – what your specific policies are, and more importantly, why they are that way, and where they can find those documents. You have to eat from the same trough as everyone else – follow your own policies and requirements. Don’t set up, or allow, cliques of the access ‘haves’ and the ‘have nots.’ Lead by example.
- The Happy Wife, Happy Life Principle Pro athletes have coaches who help them train to be bigger, faster, stronger, and have better technique – why shouldn’t your people? In the US, Less than 21% of employees have received ANY employer-provided training in past 5 years. Invest in them! Training, conferences, learning opportunities, etc. – builds appreciation and sense of involvement along with technical knowledge, which leads to more engaged employees. Focus on building a tribe, not just a collection of people who happen to work in the same office. Invest in your people, and they will invest in business success. What can you do to invest in your people? Align their professional growth with business growth. Give them opportunities to expand their horizons, not just stay in the same operations-centric tasks. We need to develop staff – and leaders – in our industry who can understand and see how the tactical and strategic plans and processes need to align. Facilitate a mentor program for your top performers. It can be as simple as a monthly scheduled meeting with your senior leaders, to cultivate relationships and expose them to business decisions and strategy that are not necessarily security-driven. Encourage certs, regardless of what you think of them: they are actively learning and improving themselves. Reward them for accomplishments, cert or not. They will appreciate the recognition. Just remember that Qualified and Certified are not interchangeable. And remember, we are all in marketing… sell your team’s successes to build credibility and goodwill. Keep in mind that we need to focus on the path, not just the end goal… Bruce Lee quote: Some targets are only meant to be aimed at.’ Develop a personalized roadmaps for success – plan out the position, and determine where candidates are on the map, and what they need to progress. Then, most important – give them the tools and resources to be successful!
- Do Something Different. (RockStars) We are at a turning point in our industry; we are essentially on the verge of being the emperor with no clothes (from a leadership perspective.) We have got to get away from the ‘Rock Star’ mindset… we’re really all house musicians – we’re important, provide value, and are great at what we do, but at the end of the day, it’s not about us, we’re just the supporting cast, we are roadies for our business. As far as InfoSec is concerned, we need to be working ON our industry, as much as we work IN our industry. Again… we are all in marketing. And we are the movers and shakers who will change it, not thought leaders or talking heads who aren’t managing security every day in a production environment.
- Our Industry isn’t As Binary As Some Would Have You Believe. In the most direct sense, we deal with ones and zeros everyday. We manipulate them to give us output; we analyze them to decipher them, and then repurpose the ones and zeros in different discrete configurations to alter other data sets. But our organization’s don’t deal in ones and zeros. This picture of earth encompasses everything on our planet. It’s not all black and white, and no straight lines. Leadership, and to a large degree, our industry, can’t be broken down into such concrete values. Again, we are the house band, subject to the dynamics of our organizations to determine what is important, risk-wise. Security isn’t the most important word in business language, and I am unequivocally NOT saying that we don’t have a critical role to play. But we don’t define the rules, and we have a wide variety of roles and responsibilities. There are many in our profession who only seem to focus on the binaries, and in reality, even if we wanted to, there are few that have the luxury of allowing such tunnelvision to define us, and our work. We can’t all be focused on CVEs and breaking things all of the time. It’s not all ones and zeros, and it’s not Us Against Them.
- Pwn Youself. Pretty self explanatory. Lead from your strengths. Leverage your talents and skills to help others.
- In the End: Hopefully you have found some of this useful… It is up to us, in our industry, to change our attitude, the way we are perceived, and to become true business partners, not liabilities… you don’t want to become known as the Business Prevention Department. May Inspire, but only Action Creates Change Our industry is ripe for change in how we lead ourselves, and our people. Effective leadership/security management and governance will flow outwards to our organizations, if we make a conscious effort to build bridges, instead of loosening the bolts a little every day. It’s up to us to lead our teams, our businesses, and our industry in the direction WE want it to go. Peter Drucker: If you want something new, you have to stop doing something old… so what are YOU going to do differently, to effect change in yourself, your organization, and the industry? Start with Why. Lead Yourself. Then Lead Others. And if you can’t do that… Get Out of the Way! END
- http://bit.ly/infosec_leadership http://bit.ly/colemic
