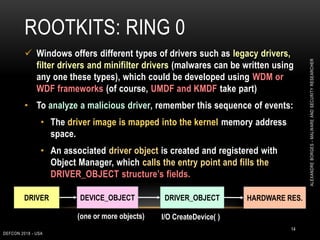
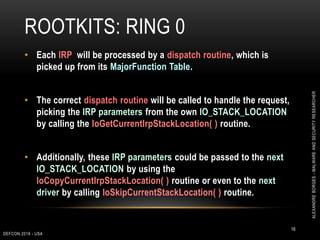
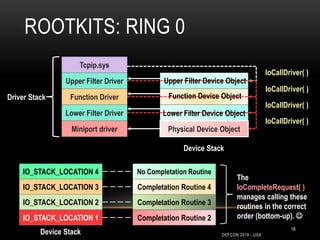
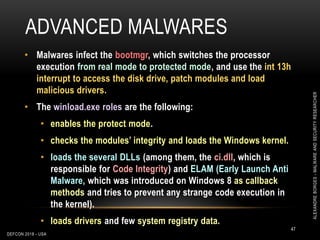
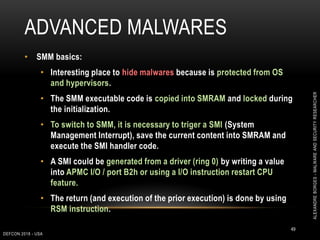
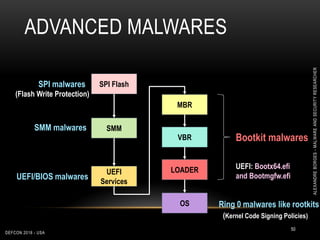
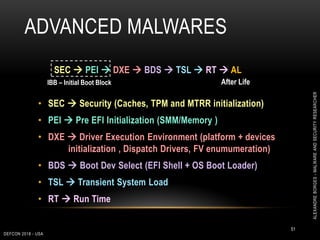
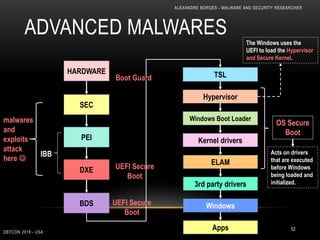
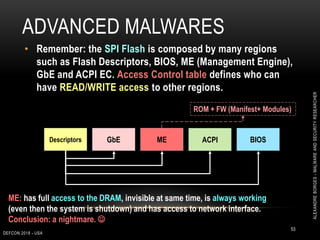
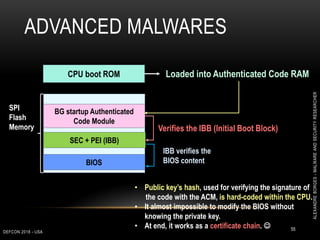
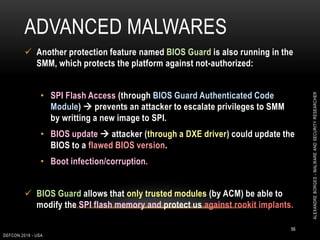
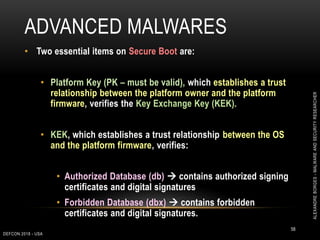
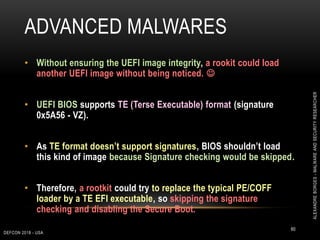
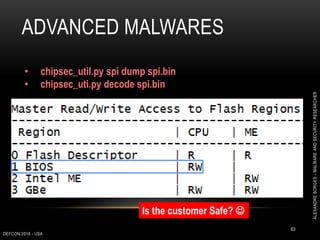
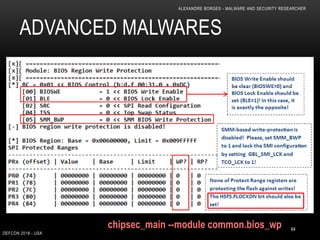
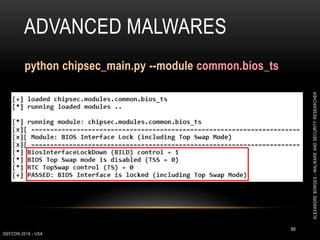
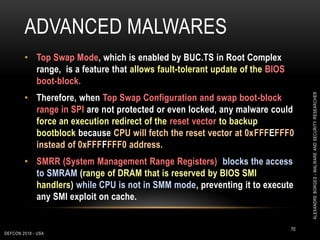
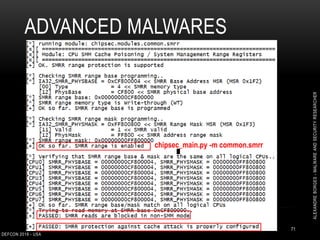
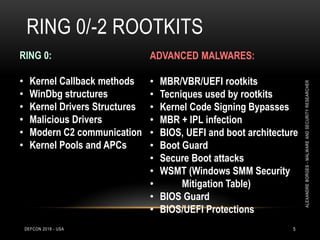
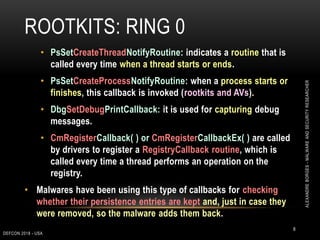
This document outlines a presentation given by Alexandre Borges at Defcon 2018 focused on rootkits and advanced malware techniques. It covers the functionality and evasion tactics of ring 0 and ring -2 rootkits, including kernel callback methods, driver types, and the interaction between malicious drivers and the Windows operating system. The presentation also discusses various methods utilized by malware to maintain persistence and evade detection, addressing both theoretical concepts and practical implications for cybersecurity professionals.






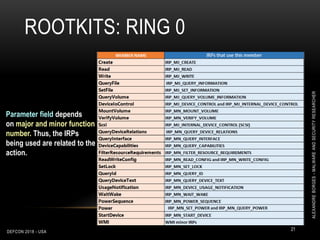
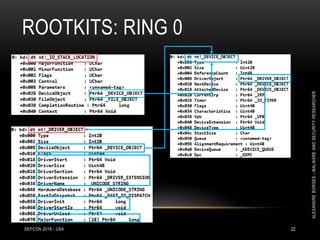
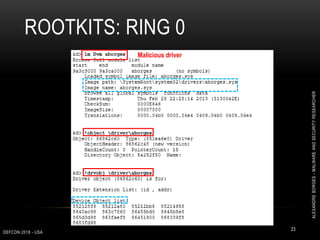
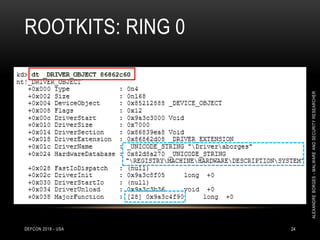
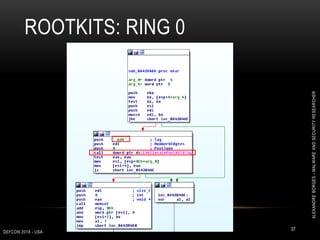
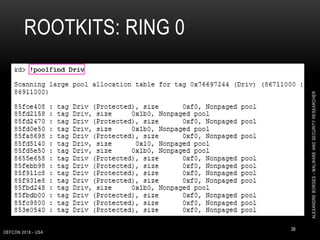
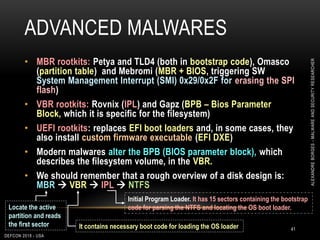
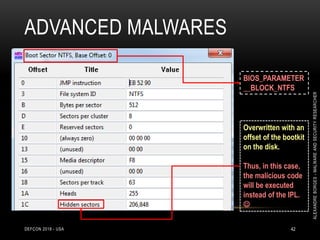
![ROOTKITS: RING 0
DEFCON 2018 - USA 9
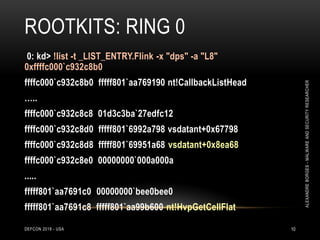
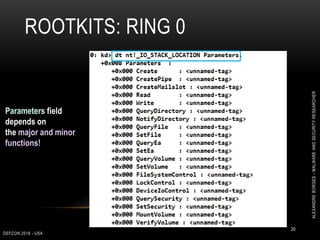
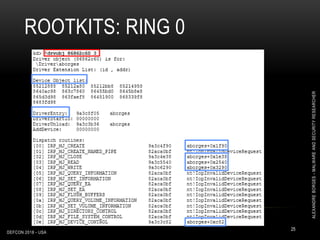
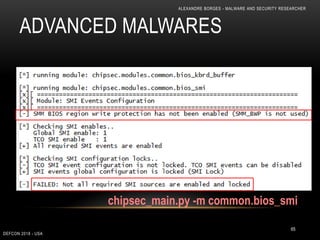
0: kd> dd nt!CmpCallBackCount L1
fffff801`aa733fcc 00000002
0: kd> dps nt!CallbackListHead L2
fffff801`aa769190 ffffc000`c8d62db0
fffff801`aa769198 ffffc000`c932c8b0
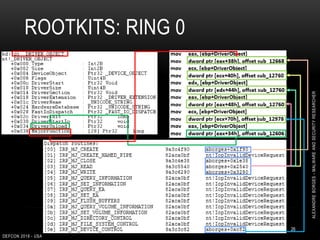
0: kd> dt nt!_LIST_ENTRY ffffc000`c8d62db0
[ 0xffffc000`c932c8b0 - 0xfffff801`aa769190 ]
+0x000 Flink : 0xffffc000`c932c8b0 _LIST_ENTRY [
0xfffff801`aa769190 - 0xffffc000`c8d62db0 ]
+0x008 Blink : 0xfffff801`aa769190 _LIST_ENTRY [
0xffffc000`c8d62db0 - 0xffffc000`c932c8b0 ]
ALEXANDREBORGES-MALWAREANDSECURITYRESEARCHER](https://image.slidesharecdn.com/11-defcon-26-alexandre-borges-ring-02-rootkits-bypassing-defenses-updated-180925050634/85/RING-0-2-ROOKITS-COMPROMISING-DEFENSES-9-320.jpg)