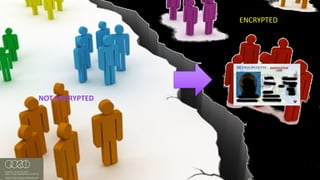
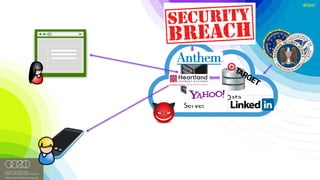
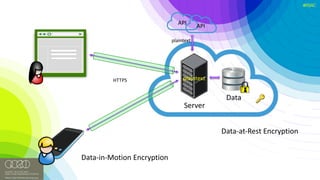
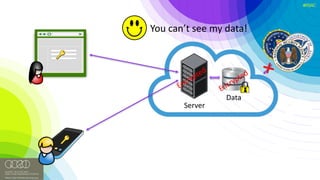
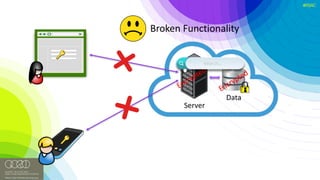
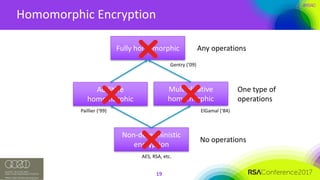
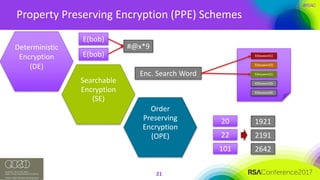
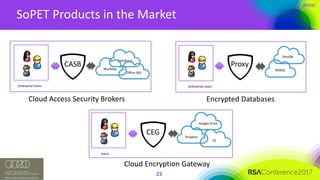
The document discusses the vulnerabilities of client-side encryption in protecting sensitive data and highlights the importance of understanding encryption's limitations. It explores various encryption algorithms, property preserving encryption (PPE) schemes, and the risks of data exposure due to weak configurations and design flaws. Additionally, it emphasizes the need for stronger defenses against adversaries, as current systems may not adequately protect against sophisticated threats.















![#RSAC
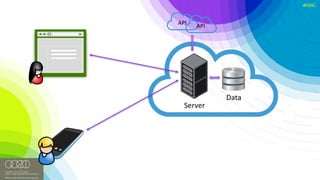
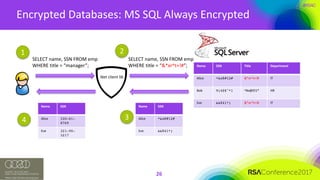
Encrypted Databases: BigQuery
27
[
{
“name”: Alice,
”SSN”: *&x@#12#,
“age”: 2345
},
{
“name”: Bob,
”SSN”: 9(4$$^*1,
”age”: 3212
},
{
“name”: Eve,
”SSN”: &&@41*),
”age”: 2110
}
…
]
Proxy
SELECT name, age FROM emp
WHERE age > 20;
1 2
34
SELECT name, age FROM emp
WHERE age > 2531;
[ {
“name”: Bob,
“age”: 3212
}]
BigQuery
[ {
“name”: Bob,
“age”: 24
}]
Any Value
OPE
RND
* CryptDB: Protecting Confidentiality with Encrypted Query Processing, Popa et. al, SOSP 2011
* Onions](https://image.slidesharecdn.com/pdac-w03-client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-170419071312/85/Client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-27-320.jpg)
![#RSAC
Inferring Encrypted Data [1/2]
29
Snapshot Passive Adversary
Based on background information/what you don’t encrypt (MS SQL)
Statistical inference on DE encrypted values (MS SQL, CryptDB)*
Sorting attack for OPE encrypted dense columns*
Cumulative (statistical and sorting) attack for OPE encrypted sparse columns*
* Inference Attacks on Property Preserving Encrypted Databases, Naveed et. al, CCS 2015](https://image.slidesharecdn.com/pdac-w03-client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-170419071312/85/Client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-29-320.jpg)
![#RSAC
Inferring Encrypted Data [2/2]
30
Persistent Passive Adversary
Monitoring access patterns and metadata to infer encrypted data*
Active Adversary
Brute-force querying
Repeated onion peeling to get to the DE encrypted values
* Breaking Web Applications Built on top of Encrypted Data, Grubbs et. al, CCS 2016](https://image.slidesharecdn.com/pdac-w03-client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-170419071312/85/Client-side-encryption-without-knowing-its-limits-is-a-ticking-time-bomb-30-320.jpg)