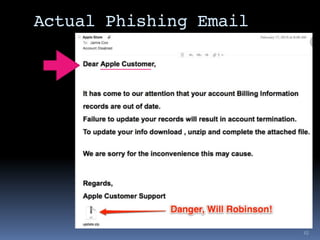
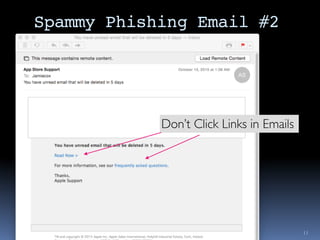
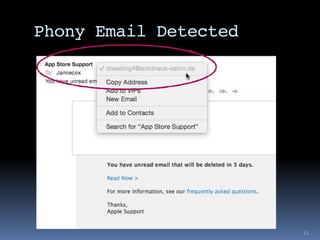
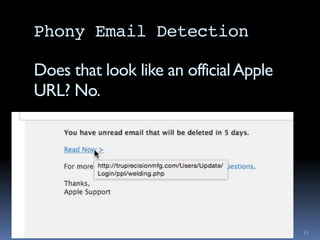
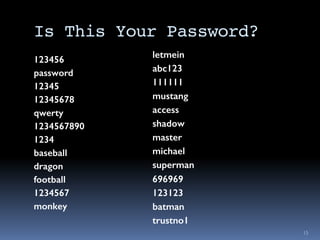
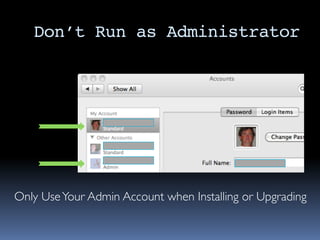
The document outlines security considerations for Macintosh users, highlighting threats like hardware failures, malware, and phishing attacks. It emphasizes the importance of regular backups, software updates, strong passwords, and two-factor authentication to mitigate risks. Common misconceptions about personal security are addressed, and practical steps for enhancing digital security are recommended.