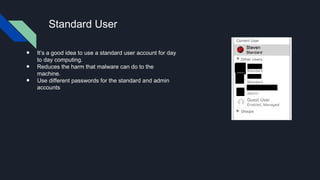
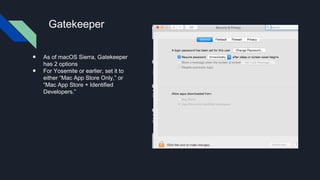
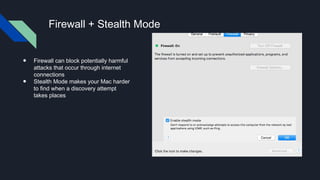
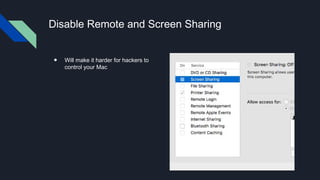
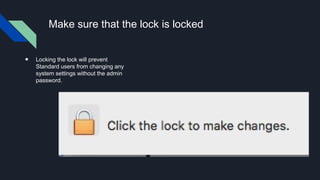
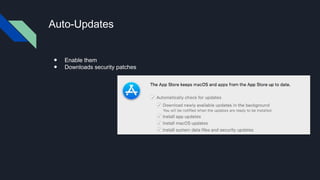
This document provides tips for protecting a Mac (macOS) computer from malware and other security threats. It recommends using a standard user account instead of an administrator account for daily use, enabling Gatekeeper to only allow apps from the Mac App Store or identified developers, using the firewall and enabling stealth mode, uninstalling Flash and Java, avoiding torrenting files, disabling remote access and screen sharing, locking the computer when not in use, enabling auto-updates, and using browser extensions for privacy and security. It also advises backing up important files to external storage and the cloud.