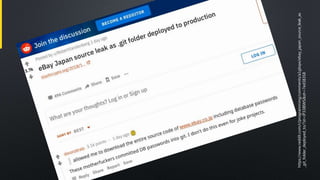
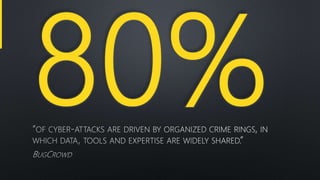
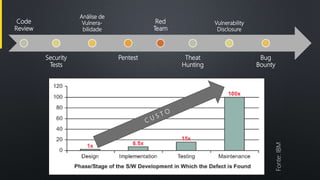
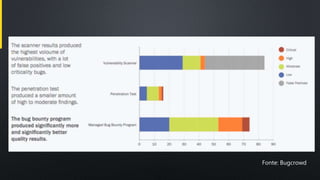
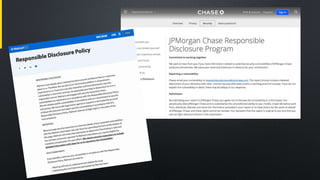
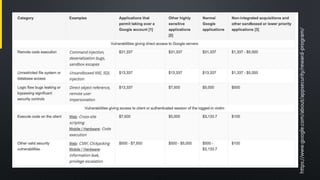
The document discusses various aspects of cybersecurity, particularly focusing on vulnerability assessment and penetration testing methodologies. It references multiple sources, including articles on bug bounty programs and the collaboration between red and blue security teams. Key terms include vulnerability disclosure, security tests, and resources from established security standards and platforms.