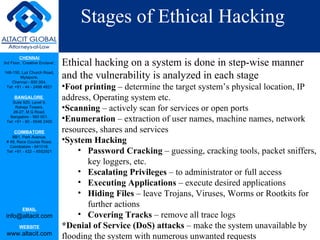
Ethical hacking involves using the same techniques as malicious hackers but in a lawful and legitimate way to test an organization's security and help improve it. An ethical hacker obtains permission, then attempts to find and report on vulnerabilities to help organizations fix security issues before criminals can exploit them. The goal is to maintain authorized access, avoid damaging systems, and respect confidentiality and privacy. Ethical hacking follows steps like reconnaissance, scanning, access, reporting results and recommending solutions. It helps balance security, functionality and ease of use.