Paper publications details of all Staff-2019-20(Other).xlsx - M R Talware.pdf
•
0 likes•7 views
Video Analytics applications like security and surveillance face a critical problem of person re-identification abbreviated as re-ID. The last decade witnessed the emergence of large-scale datasets and deep learning methods to use these huge data volumes. Most current re-ID methods are classified into either image-based or video-based re-ID
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to Paper publications details of all Staff-2019-20(Other).xlsx - M R Talware.pdf
Similar to Paper publications details of all Staff-2019-20(Other).xlsx - M R Talware.pdf (20)
A multi-task learning based hybrid prediction algorithm for privacy preservin...

A multi-task learning based hybrid prediction algorithm for privacy preservin...
Person identification based on facial biometrics in different lighting condit...

Person identification based on facial biometrics in different lighting condit...
Attendance management system using face recognition

Attendance management system using face recognition
Face Recognition Based Attendance System using Machine Learning

Face Recognition Based Attendance System using Machine Learning
11.graphical password based hybrid authentication system for smart hand held ...

11.graphical password based hybrid authentication system for smart hand held ...
Graphical password based hybrid authentication system for smart hand held dev...

Graphical password based hybrid authentication system for smart hand held dev...
Persuasive Cued Click Based Graphical Password with Scrambling For Knowledge ...

Persuasive Cued Click Based Graphical Password with Scrambling For Knowledge ...
A Multimedia Data Mining Framework for Monitoring E-Examination Environment

A Multimedia Data Mining Framework for Monitoring E-Examination Environment
IJERD (www.ijerd.com) International Journal of Engineering Research and Devel...

IJERD (www.ijerd.com) International Journal of Engineering Research and Devel...
More from aissmsblogs
More from aissmsblogs (20)
422 3 smart_e-health_care_using_iot_and_machine_learning

422 3 smart_e-health_care_using_iot_and_machine_learning
Recently uploaded
🔝9953056974🔝!!-YOUNG call girls in Rajendra Nagar Escort rvice Shot 2000 nigh...

🔝9953056974🔝!!-YOUNG call girls in Rajendra Nagar Escort rvice Shot 2000 nigh...9953056974 Low Rate Call Girls In Saket, Delhi NCR
High Profile Call Girls Nagpur Meera Call 7001035870 Meet With Nagpur Escorts

High Profile Call Girls Nagpur Meera Call 7001035870 Meet With Nagpur EscortsCall Girls in Nagpur High Profile
young call girls in Rajiv Chowk🔝 9953056974 🔝 Delhi escort Service

young call girls in Rajiv Chowk🔝 9953056974 🔝 Delhi escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger

Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger
🔝9953056974🔝!!-YOUNG call girls in Rajendra Nagar Escort rvice Shot 2000 nigh...

🔝9953056974🔝!!-YOUNG call girls in Rajendra Nagar Escort rvice Shot 2000 nigh...
Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx

Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx
Heart Disease Prediction using machine learning.pptx

Heart Disease Prediction using machine learning.pptx
Application of Residue Theorem to evaluate real integrations.pptx

Application of Residue Theorem to evaluate real integrations.pptx
(ANVI) Koregaon Park Call Girls Just Call 7001035870 [ Cash on Delivery ] Pun...![(ANVI) Koregaon Park Call Girls Just Call 7001035870 [ Cash on Delivery ] Pun...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![(ANVI) Koregaon Park Call Girls Just Call 7001035870 [ Cash on Delivery ] Pun...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
(ANVI) Koregaon Park Call Girls Just Call 7001035870 [ Cash on Delivery ] Pun...
Gfe Mayur Vihar Call Girls Service WhatsApp -> 9999965857 Available 24x7 ^ De...

Gfe Mayur Vihar Call Girls Service WhatsApp -> 9999965857 Available 24x7 ^ De...
APPLICATIONS-AC/DC DRIVES-OPERATING CHARACTERISTICS

APPLICATIONS-AC/DC DRIVES-OPERATING CHARACTERISTICS
VIP Call Girls Service Kondapur Hyderabad Call +91-8250192130

VIP Call Girls Service Kondapur Hyderabad Call +91-8250192130
(MEERA) Dapodi Call Girls Just Call 7001035870 [ Cash on Delivery ] Pune Escorts![(MEERA) Dapodi Call Girls Just Call 7001035870 [ Cash on Delivery ] Pune Escorts](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![(MEERA) Dapodi Call Girls Just Call 7001035870 [ Cash on Delivery ] Pune Escorts](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
(MEERA) Dapodi Call Girls Just Call 7001035870 [ Cash on Delivery ] Pune Escorts
Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx

Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx
Call Girls Narol 7397865700 Independent Call Girls

Call Girls Narol 7397865700 Independent Call Girls
High Profile Call Girls Nagpur Meera Call 7001035870 Meet With Nagpur Escorts

High Profile Call Girls Nagpur Meera Call 7001035870 Meet With Nagpur Escorts
chaitra-1.pptx fake news detection using machine learning

chaitra-1.pptx fake news detection using machine learning
young call girls in Rajiv Chowk🔝 9953056974 🔝 Delhi escort Service

young call girls in Rajiv Chowk🔝 9953056974 🔝 Delhi escort Service
Paper publications details of all Staff-2019-20(Other).xlsx - M R Talware.pdf
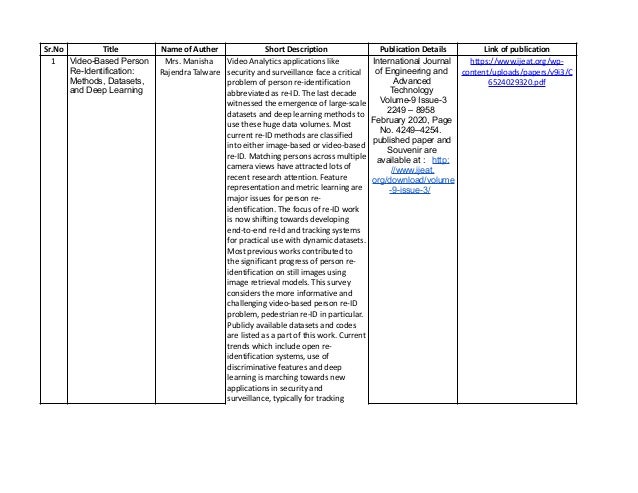
- 1. Sr.No Title Name of Auther Short Description Publication Details Link of publication 1 Video-Based Person Re-Identification: Methods, Datasets, and Deep Learning Mrs. Manisha Rajendra Talware Video Analytics applications like security and surveillance face a critical problem of person re-identification abbreviated as re-ID. The last decade witnessed the emergence of large-scale datasets and deep learning methods to use these huge data volumes. Most current re-ID methods are classified into either image-based or video-based re-ID. Matching persons across multiple camera views have attracted lots of recent research attention. Feature representation and metric learning are major issues for person re- identification. The focus of re-ID work is now shifting towards developing end-to-end re-Id and tracking systems for practical use with dynamic datasets. Most previous works contributed to the significant progress of person re- identification on still images using image retrieval models. This survey considers the more informative and challenging video-based person re-ID problem, pedestrian re-ID in particular. Publicly available datasets and codes are listed as a part of this work. Current trends which include open re- identification systems, use of discriminative features and deep learning is marching towards new applications in security and surveillance, typically for tracking International Journal of Engineering and Advanced Technology Volume-9 Issue-3 2249 – 8958 February 2020, Page No. 4249–4254. published paper and Souvenir are available at : http: //www.ijeat. org/download/volume -9-issue-3/ https://www.ijeat.org/wp- content/uploads/papers/v9i3/C 6524029320.pdf