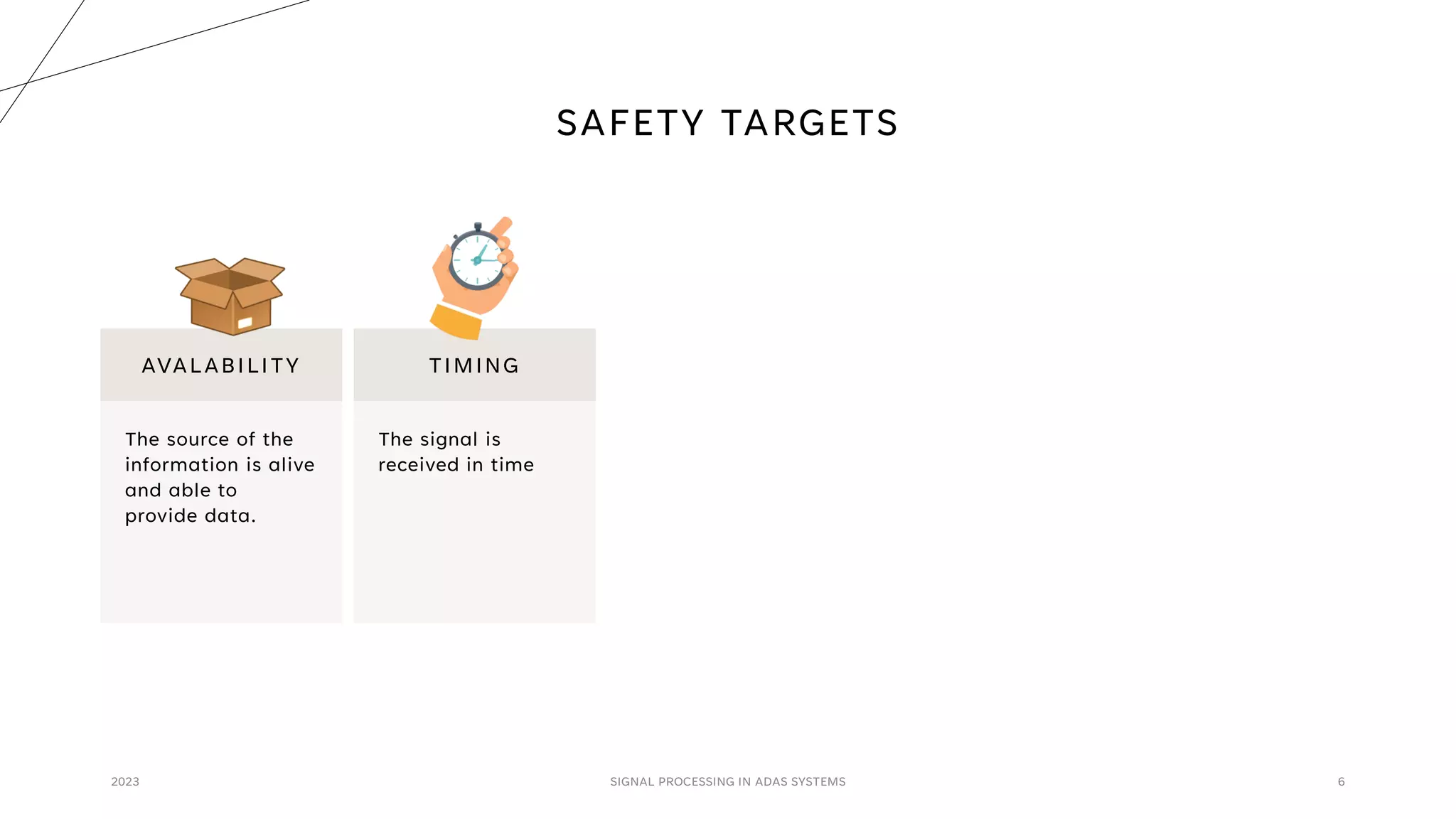
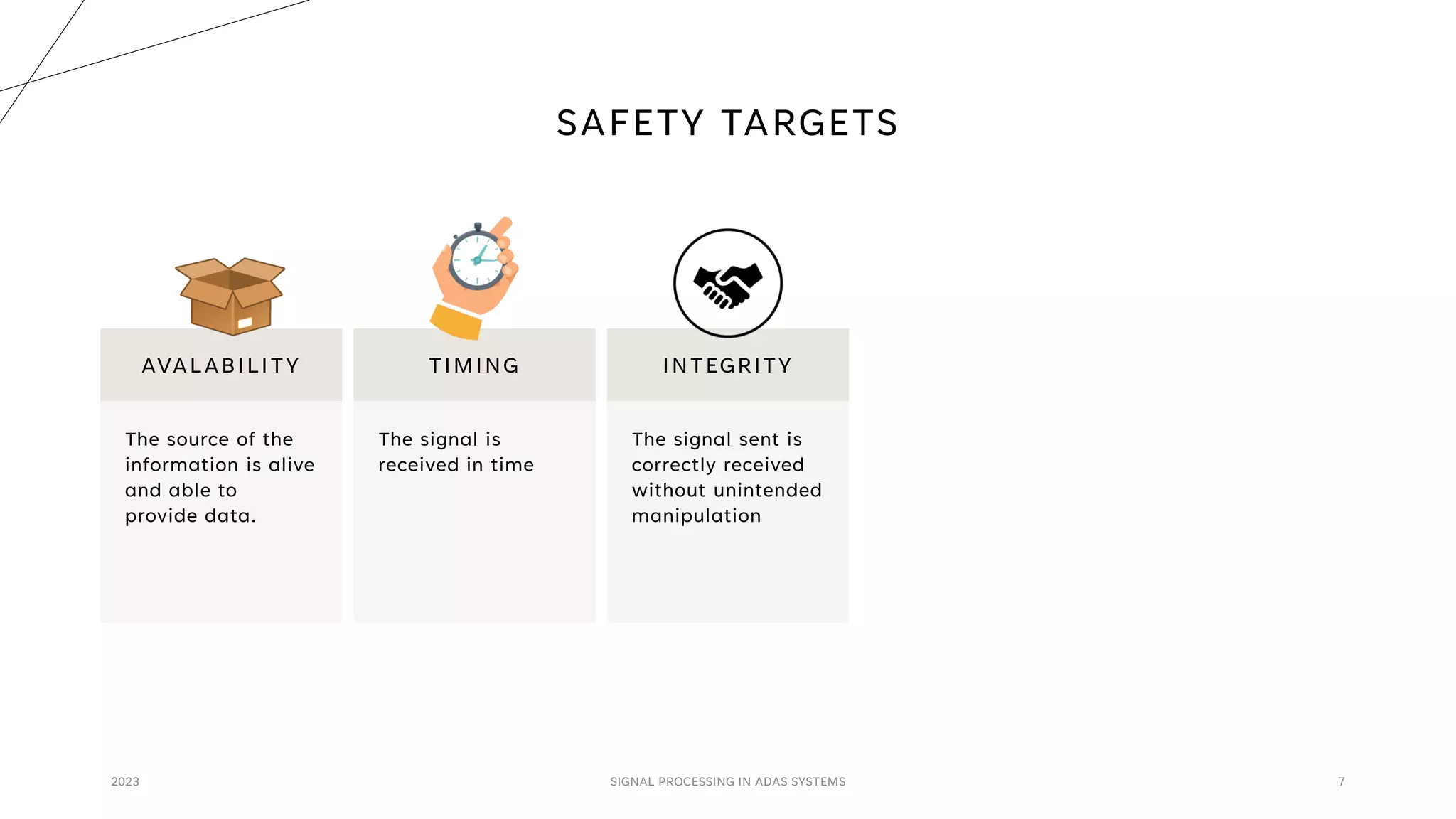
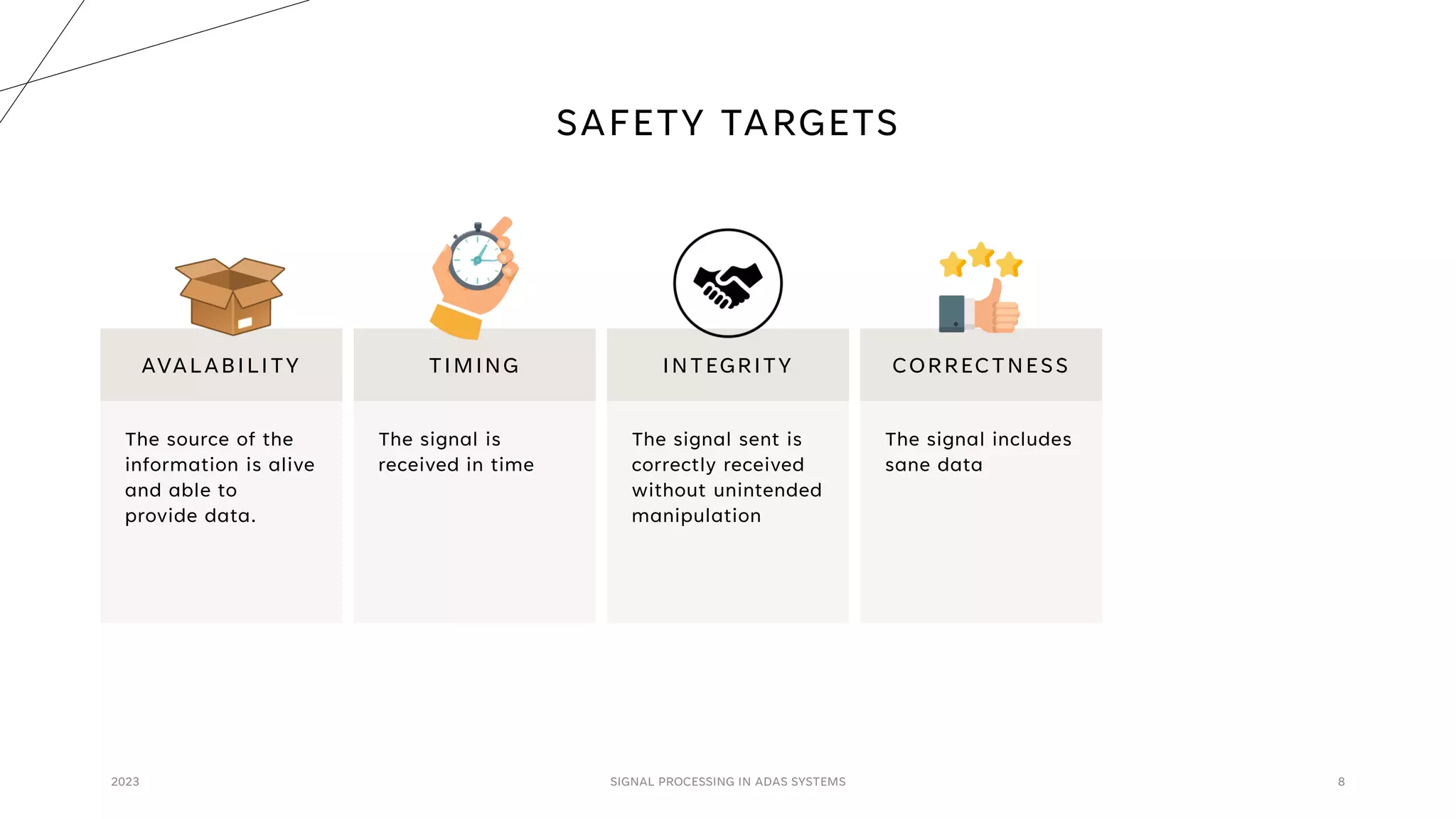
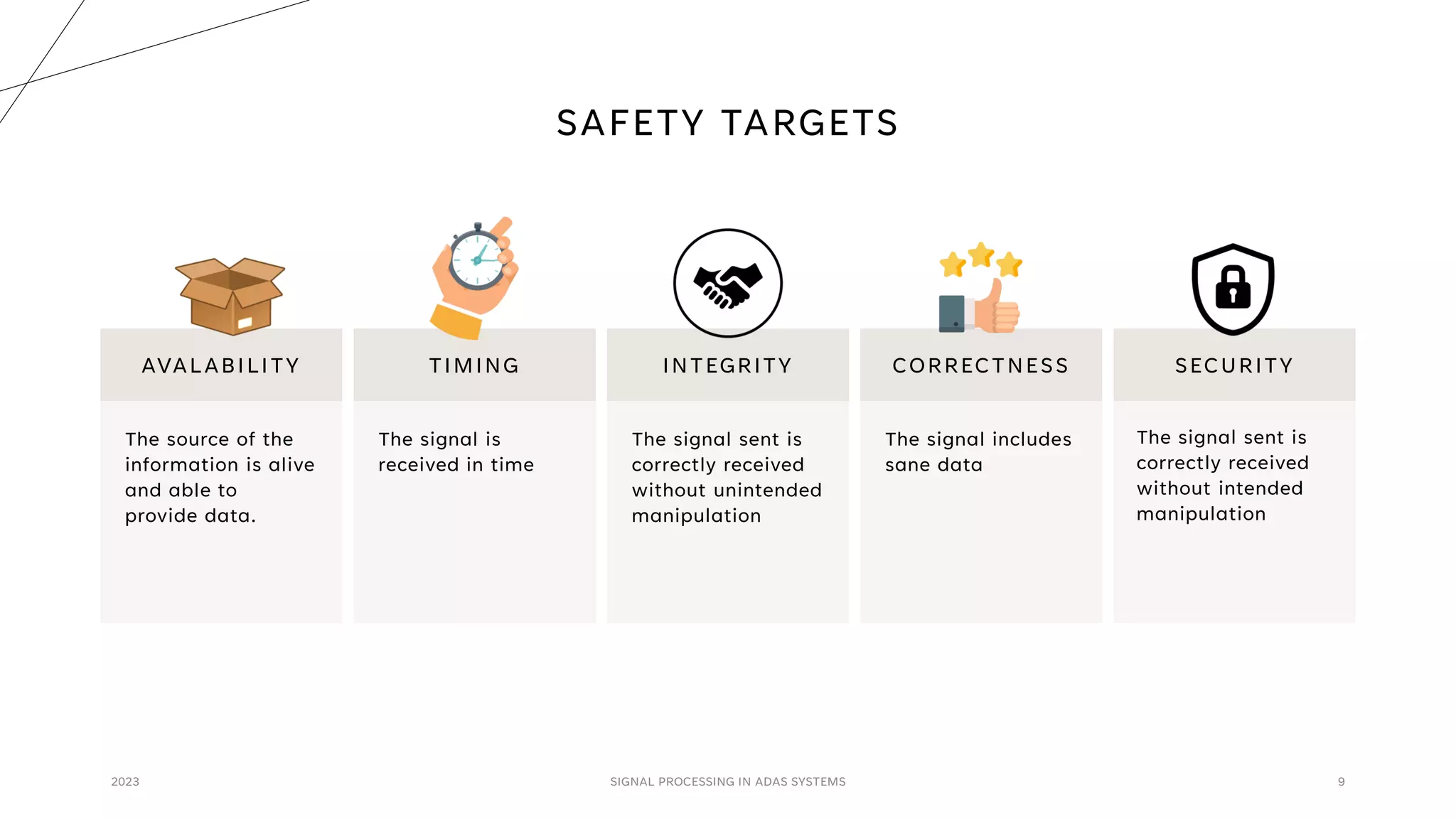
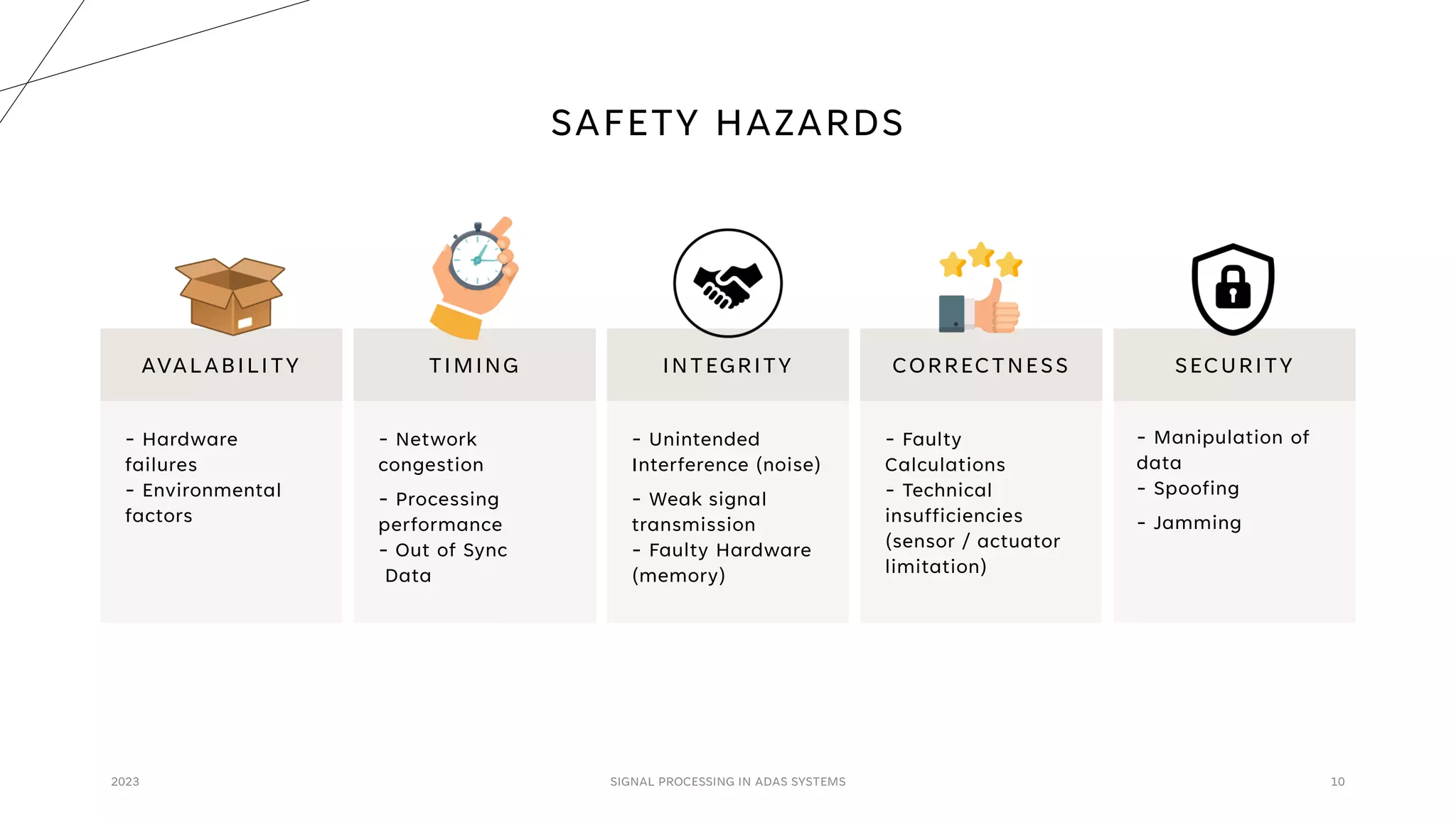
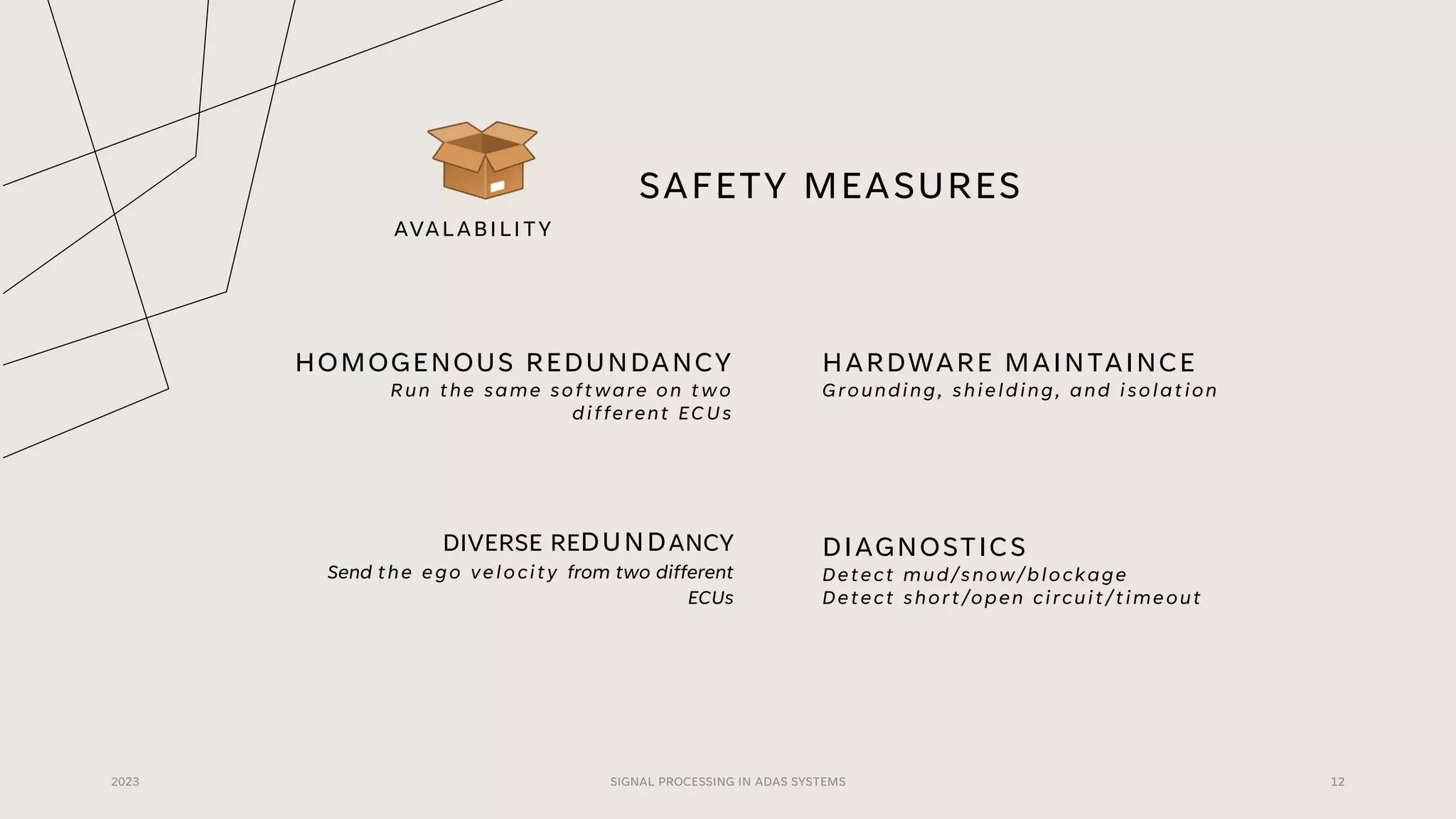
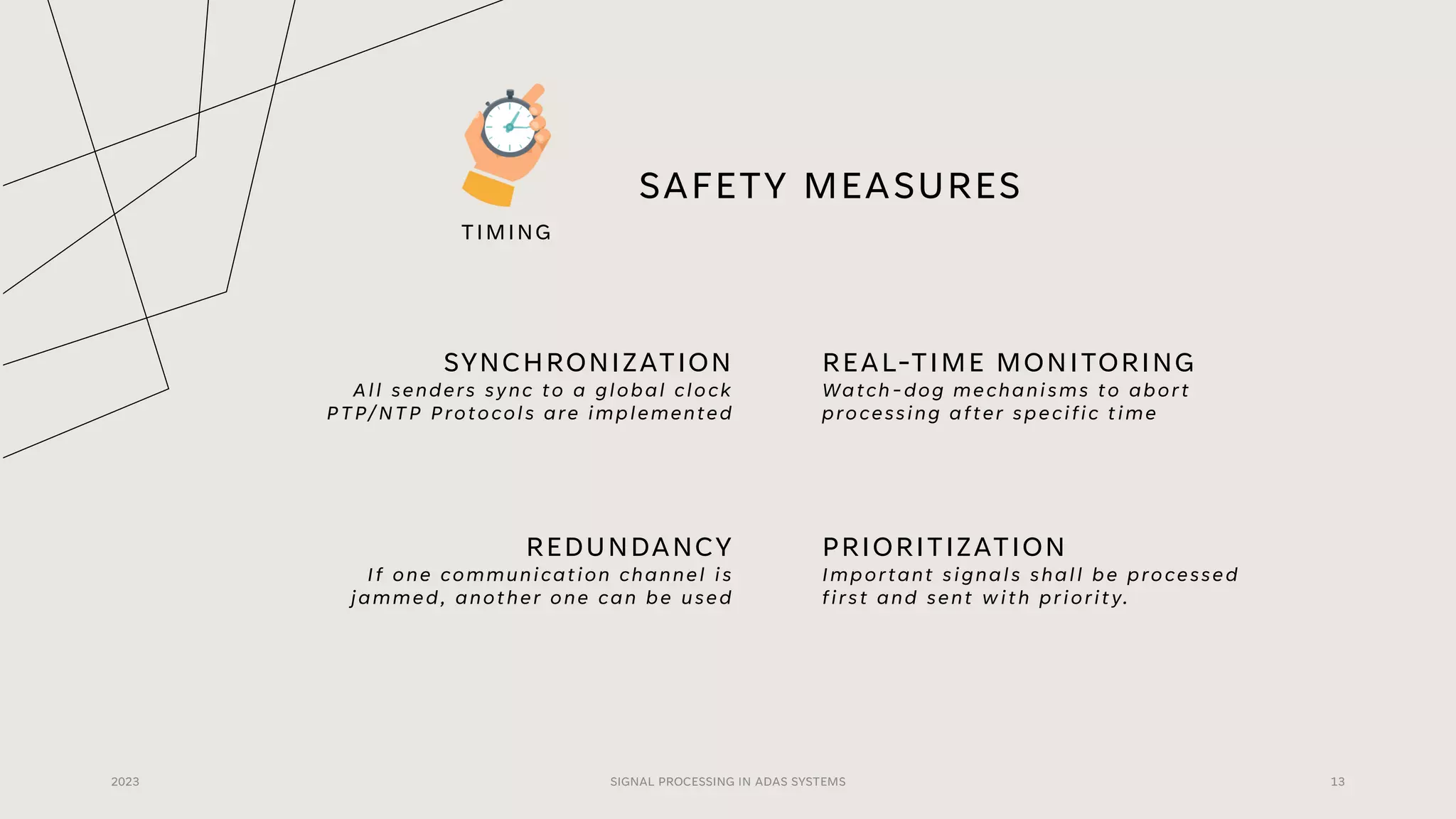
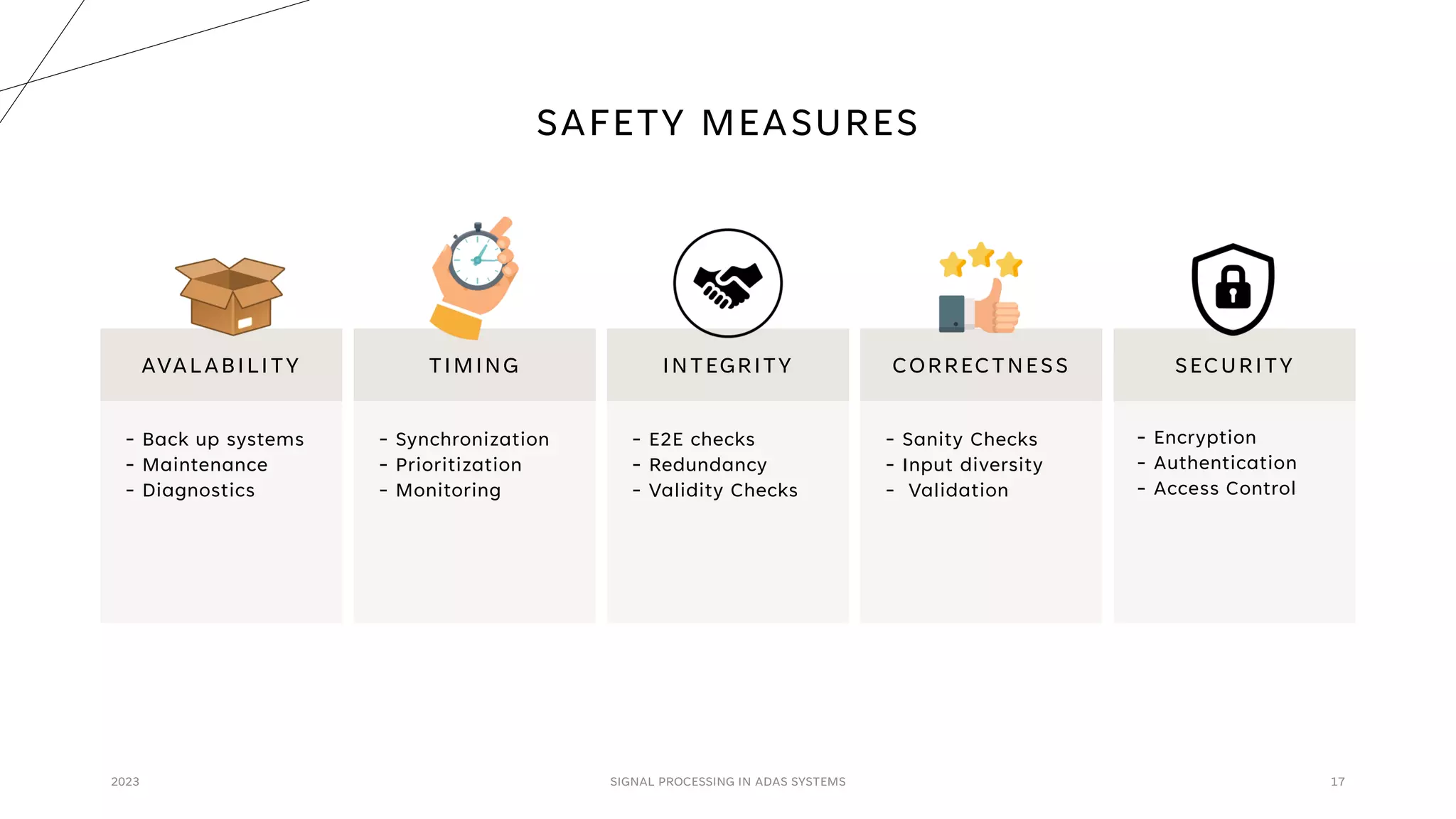
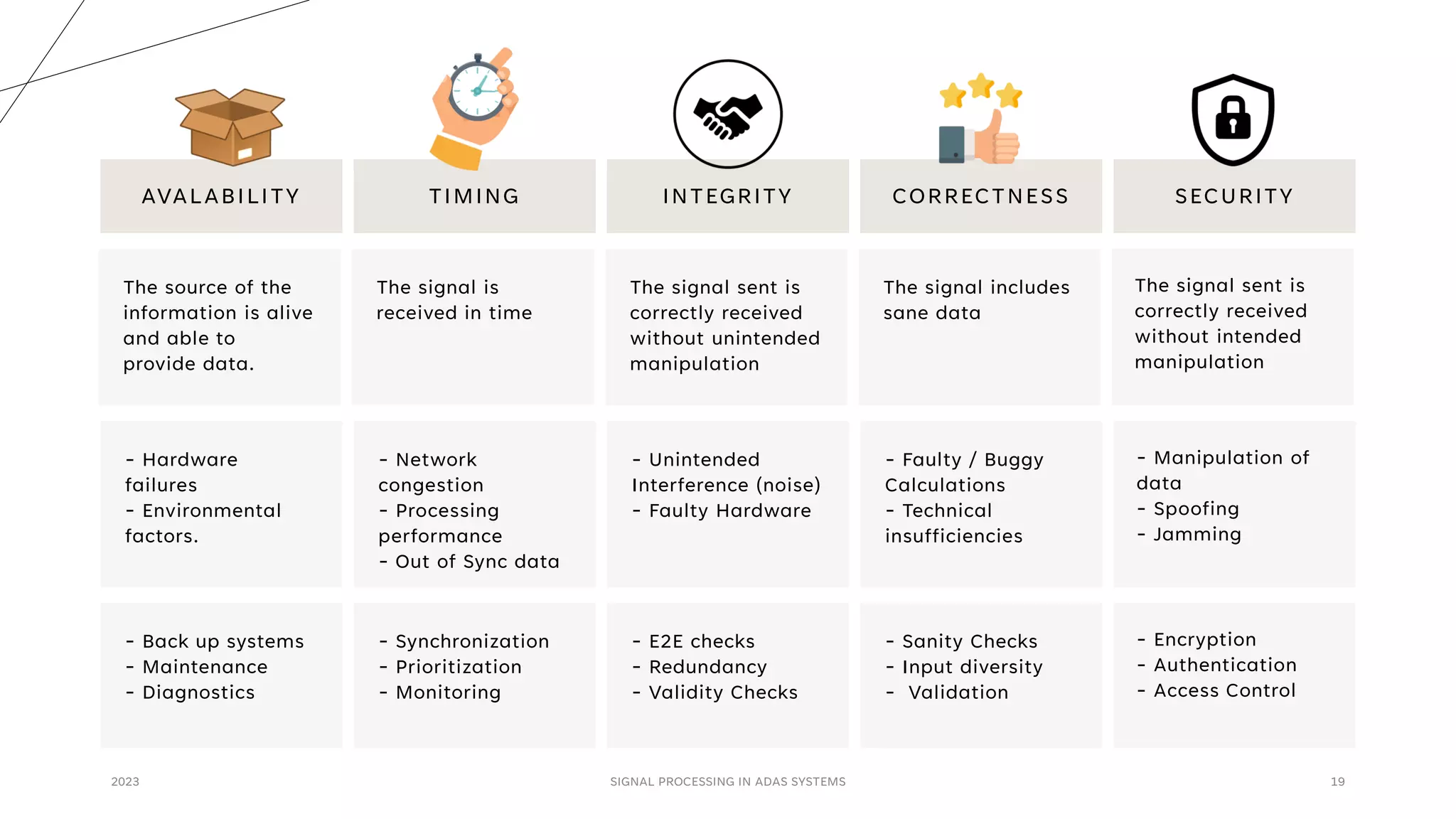
The document discusses the critical role of signal processing in Advanced Driver Assistance Systems (ADAS), emphasizing safety as a central concern in automotive development. It outlines various safety targets such as availability, timing, integrity, security, and correctness, as well as identifying safety hazards and proposing measures like redundancy and validation checks. Overall, the importance of ensuring reliable and secure data processing to prevent accidents is highlighted.