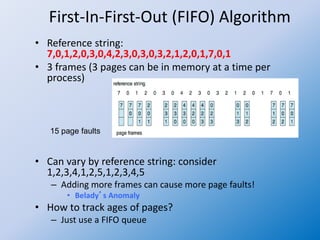
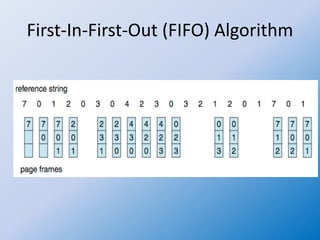
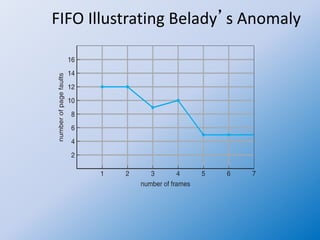
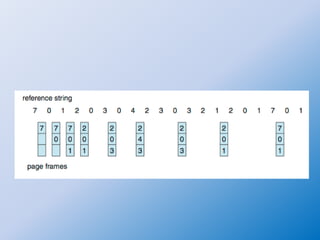
The document discusses the First-In-First-Out (FIFO) page replacement algorithm and introduces Belady's anomaly, where increasing the number of allocated frames can sometimes lead to more page faults. It highlights the optimal page-replacement algorithm, which minimizes page faults by replacing the page that will not be used for the longest time, demonstrating its superior performance compared to FIFO. The document also outlines an assignment to explain the FIFO algorithm and compare it with the optimal algorithm.