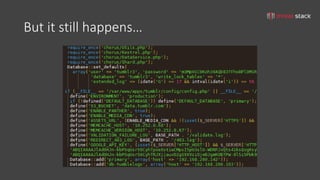
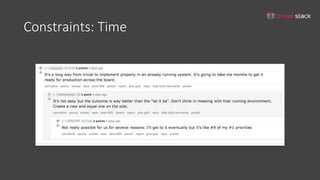
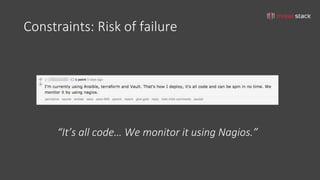
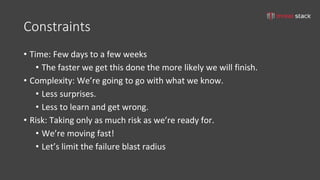
The document discusses iterative security and secrets management for organizations that may not yet be ready to implement more complex solutions like vaults. It emphasizes the importance of developing a threat model, understanding the architecture, identifying threats, and documenting risks to improve security practices. Various practical approaches for managing secrets using tools such as git-crypt, Puppet, Ansible, and S3 buckets are also presented.