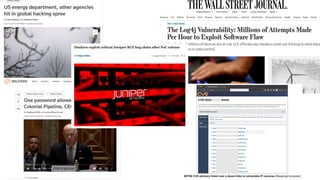
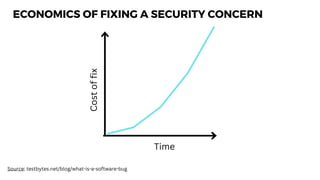
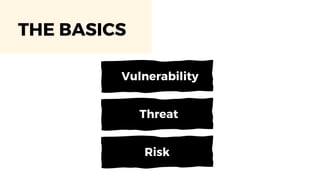
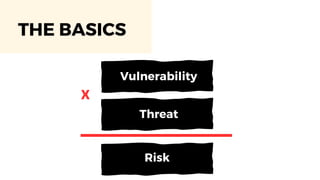
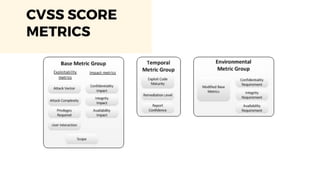
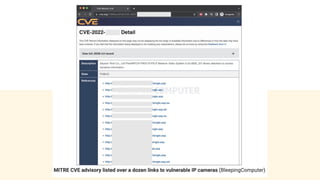
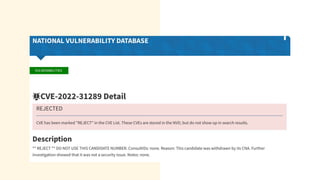
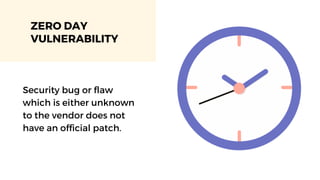
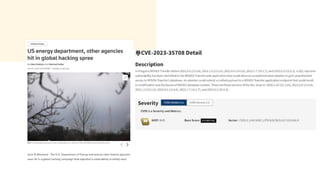
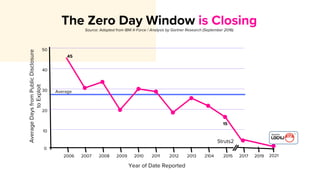
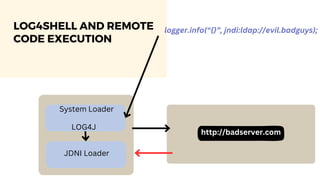
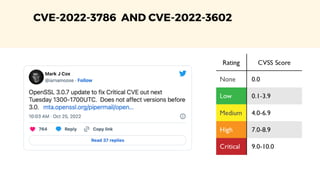
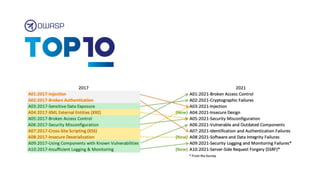
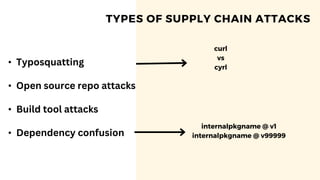
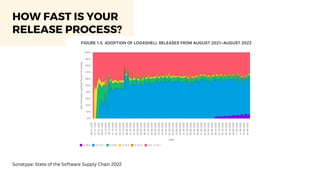
The document discusses cybercrime costs predicted to reach $8 trillion annually by 2023. It defines insider threats, software vulnerabilities, and the economics of fixing security issues. It also covers common vulnerability and exposure identifiers, zero-day vulnerabilities, and the responsible disclosure process. The need for adequate security staffing and practices for developers like dependency management and a fast release cycle are also addressed.