ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media
•
0 likes•95 views
Ce faci dacă ți-au fost sparte conturile de social media - Luna europeană a securității cibernetice 2021 Think Before U Click
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
Don't ask, don't tell the virtues of privacy by design

Don't ask, don't tell the virtues of privacy by design
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...
How to incrementally improve Sanctions Screening with AI

How to incrementally improve Sanctions Screening with AI
Similar to ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media
Similar to ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media (20)
How to Protect Yourself From Heartbleed Security Flaw

How to Protect Yourself From Heartbleed Security Flaw
How To Keep the Grinch From Ruining Your Cyber Monday

How To Keep the Grinch From Ruining Your Cyber Monday
WISE KIDS Leaflet: Junk Mail and Misleading Advertisements

WISE KIDS Leaflet: Junk Mail and Misleading Advertisements
More from One-IT
More from One-IT (20)
Centralizator întrebări și răspunsuri Digitalizare IMM.doc

Centralizator întrebări și răspunsuri Digitalizare IMM.doc
Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf

Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf
Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx

Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx
Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022

Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022
Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf

Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf
Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx

Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx
Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...

Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...
Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022

Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022
Cum te protejezi de tentativele de tip scam în business

Cum te protejezi de tentativele de tip scam în business
ECSM 2021- Informații importante despre amprenta ta digitală

ECSM 2021- Informații importante despre amprenta ta digitală
Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...

Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...
Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...

Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...
One-IT - prezentare GDPR-ul si Protectia datelor personale

One-IT - prezentare GDPR-ul si Protectia datelor personale
Recently uploaded
Recently uploaded (20)
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Unlocking the Potential of the Cloud for IBM Power Systems

Unlocking the Potential of the Cloud for IBM Power Systems
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media
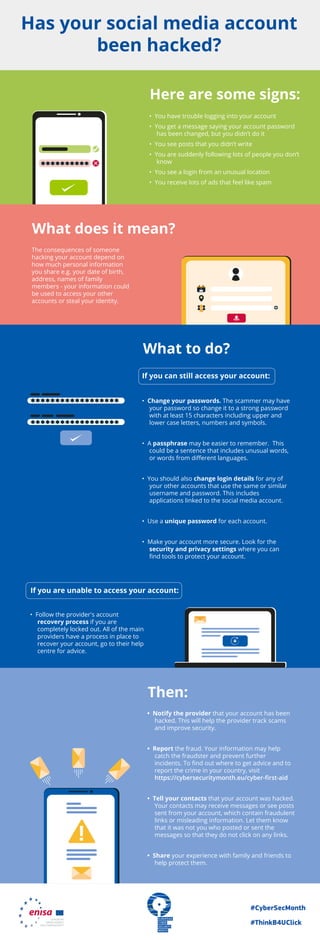
- 1. #CyberSecMonth #ThinkB4UClick ! ********** ****************** ****************** The consequences of someone hacking your account depend on how much personal information you share e.g. your date of birth, address, names of family members - your information could be used to access your other accounts or steal your identity. • You have trouble logging into your account • You get a message saying your account password has been changed, but you didn’t do it • You see posts that you didn’t write • You are suddenly following lots of people you don’t know • You see a login from an unusual location • You receive lots of ads that feel like spam • Change your passwords. The scammer may have your password so change it to a strong password with at least 15 characters including upper and lower case letters, numbers and symbols. • A passphrase may be easier to remember. This could be a sentence that includes unusual words, or words from different languages. • You should also change login details for any of your other accounts that use the same or similar username and password. This includes applications linked to the social media account. • Use a unique password for each account. • Make your account more secure. Look for the security and privacy settings where you can find tools to protect your account. Here are some signs: What does it mean? What to do? • Notify the provider that your account has been hacked. This will help the provider track scams and improve security. • Report the fraud. Your information may help catch the fraudster and prevent further incidents. To find out where to get advice and to report the crime in your country, visit https://cybersecuritymonth.eu/cyber-first-aid • Tell your contacts that your account was hacked. Your contacts may receive messages or see posts sent from your account, which contain fraudulent links or misleading information. Let them know that it was not you who posted or sent the messages so that they do not click on any links. • Share your experience with family and friends to help protect them. Then: If you can still access your account: • Follow the provider's account recovery process if you are completely locked out. All of the main providers have a process in place to recover your account, go to their help centre for advice. If you are unable to access your account: Has your social media account been hacked?
