ANDROID IEEE PAPERS – 2018 PROJECT TITLES
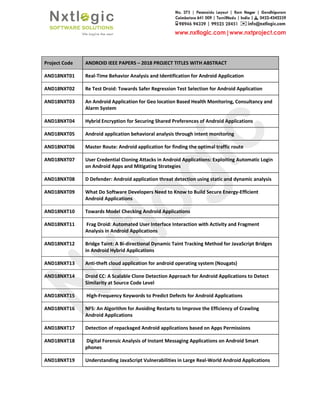
- 1. Project Code ANDROID IEEE PAPERS AND18NXT01 Real-Time Behavior Analysis and Identification for Android Application AND18NXT02 Re Test Droid: Towards AND18NXT03 An Android Application for Geo location Based Health Monitoring, Consultancy and Alarm System AND18NXT04 Hybrid Encryption for Securing Shared Preferences of Android Applications AND18NXT05 Android application behavioral analysis through intent monitoring AND18NXT06 Master Route: Android application for finding the optimal traffic route AND18NXT07 User Credential Cloning Attacks in Android Applications: Exploiting Automatic Login on Android Apps and Mitigating Strategies AND18NXT08 D Defender: Android application threat detection using static and dynamic analysis AND18NXT09 What Do Software Developers Need to Know to Build Secure Energy Android Applications AND18NXT10 Towards Model Checking Android Applications AND18NXT11 Frag Droid: Automated User Interface Interaction with Activity and Fragment Analysis in Android Applications AND18NXT12 Bridge Taint: A Bi-directional Dynamic Taint Tracking Method for JavaScript B in Android Hybrid Applications AND18NXT13 Anti-theft cloud application for android operating system (Nougats) AND18NXT14 Droid CC: A Scalable Clone Detection Approach for Android Applications to Detect Similarity at Source Code Level AND18NXT15 High-Frequency Keywords to Predict Defects for Android Applications AND18NXT16 NFS: An Algorithm for Avoiding Restarts to Improve the Efficiency of Crawling Android Applications AND18NXT17 Detection of repackaged Android applications based on Apps Permi AND18NXT18 Digital Forensic Analysis of Instant Messaging Applications on Android Smart phones AND18NXT19 Understanding JavaScript Vulnerabilities in Large Real ANDROID IEEE PAPERS – 2018 PROJECT TITLES WITH ABSTRACT Time Behavior Analysis and Identification for Android Application Re Test Droid: Towards Safer Regression Test Selection for Android Application An Android Application for Geo location Based Health Monitoring, Consultancy and Hybrid Encryption for Securing Shared Preferences of Android Applications Android application behavioral analysis through intent monitoring Master Route: Android application for finding the optimal traffic route User Credential Cloning Attacks in Android Applications: Exploiting Automatic Login on Android Apps and Mitigating Strategies D Defender: Android application threat detection using static and dynamic analysis What Do Software Developers Need to Know to Build Secure Energy- Android Applications Towards Model Checking Android Applications Frag Droid: Automated User Interface Interaction with Activity and Fragment Analysis in Android Applications directional Dynamic Taint Tracking Method for JavaScript B in Android Hybrid Applications theft cloud application for android operating system (Nougats) Droid CC: A Scalable Clone Detection Approach for Android Applications to Detect Similarity at Source Code Level Frequency Keywords to Predict Defects for Android Applications NFS: An Algorithm for Avoiding Restarts to Improve the Efficiency of Crawling Android Applications Detection of repackaged Android applications based on Apps Permissions Digital Forensic Analysis of Instant Messaging Applications on Android Smart Understanding JavaScript Vulnerabilities in Large Real-World Android Applications Time Behavior Analysis and Identification for Android Application Safer Regression Test Selection for Android Application An Android Application for Geo location Based Health Monitoring, Consultancy and Hybrid Encryption for Securing Shared Preferences of Android Applications Master Route: Android application for finding the optimal traffic route User Credential Cloning Attacks in Android Applications: Exploiting Automatic Login D Defender: Android application threat detection using static and dynamic analysis -Efficient Frag Droid: Automated User Interface Interaction with Activity and Fragment directional Dynamic Taint Tracking Method for JavaScript Bridges Droid CC: A Scalable Clone Detection Approach for Android Applications to Detect Frequency Keywords to Predict Defects for Android Applications NFS: An Algorithm for Avoiding Restarts to Improve the Efficiency of Crawling ssions Digital Forensic Analysis of Instant Messaging Applications on Android Smart World Android Applications
- 2. AND18NXT20 QBE: Q Learning-Based Exploration of Android AND18NXT21 Droid Ensemble: Detecting Android Malicious Applications With Ensemble of String and Structural Static Features AND18NXT22 Forensic analysis of encrypted instant messaging applications on Android AND18NXT23 A review of cloned AND18NXT24 Bypassing DRM protection in e AND18NXT25 Detecting third-party libraries in Android applications with high precision and recall Based Exploration of Android Applications Droid Ensemble: Detecting Android Malicious Applications With Ensemble of String and Structural Static Features Forensic analysis of encrypted instant messaging applications on Android A review of cloned mobile malware applications for android devices Bypassing DRM protection in e-book applications on Android party libraries in Android applications with high precision and recall Droid Ensemble: Detecting Android Malicious Applications With Ensemble of String Forensic analysis of encrypted instant messaging applications on Android party libraries in Android applications with high precision and recall
