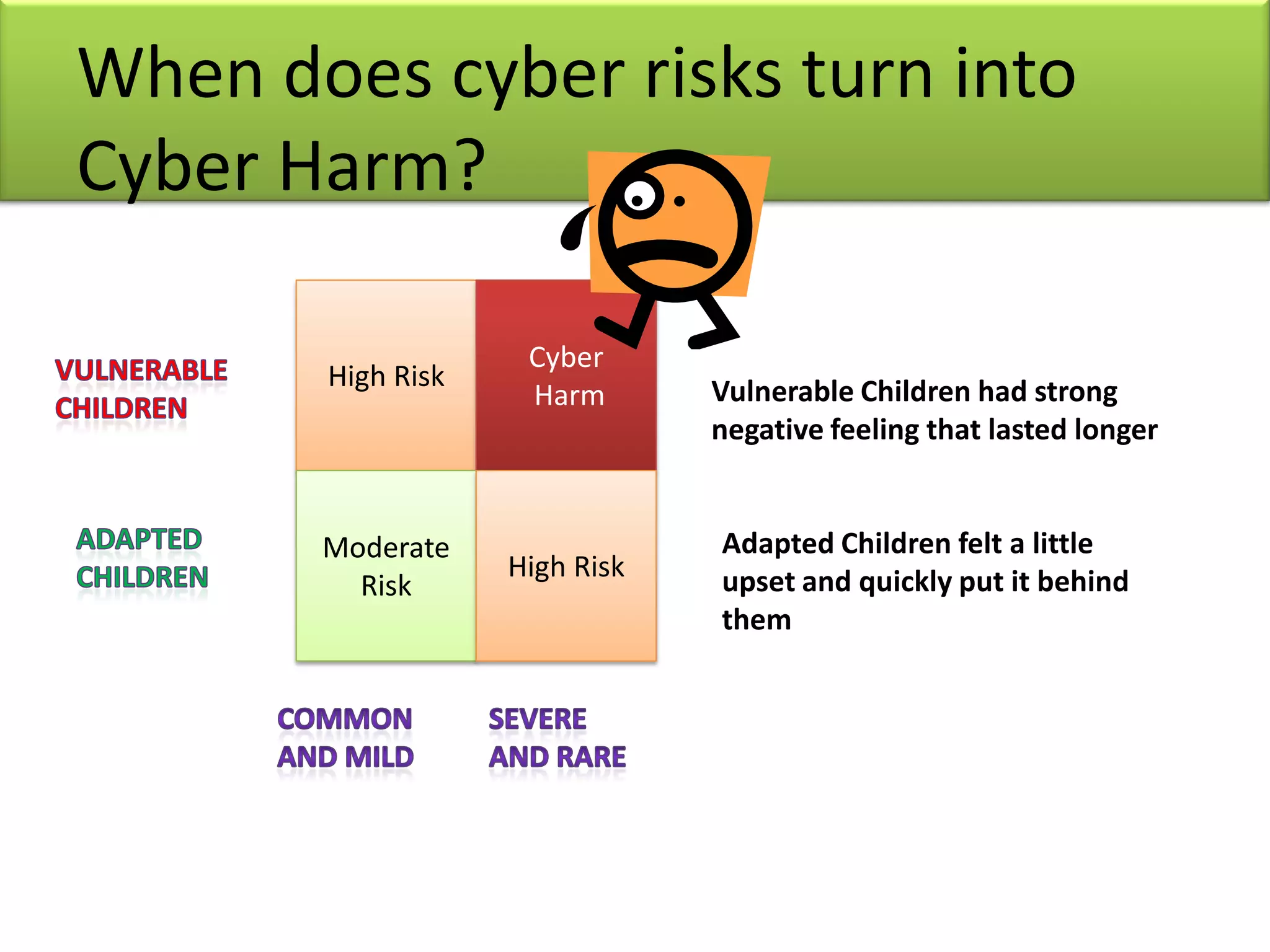
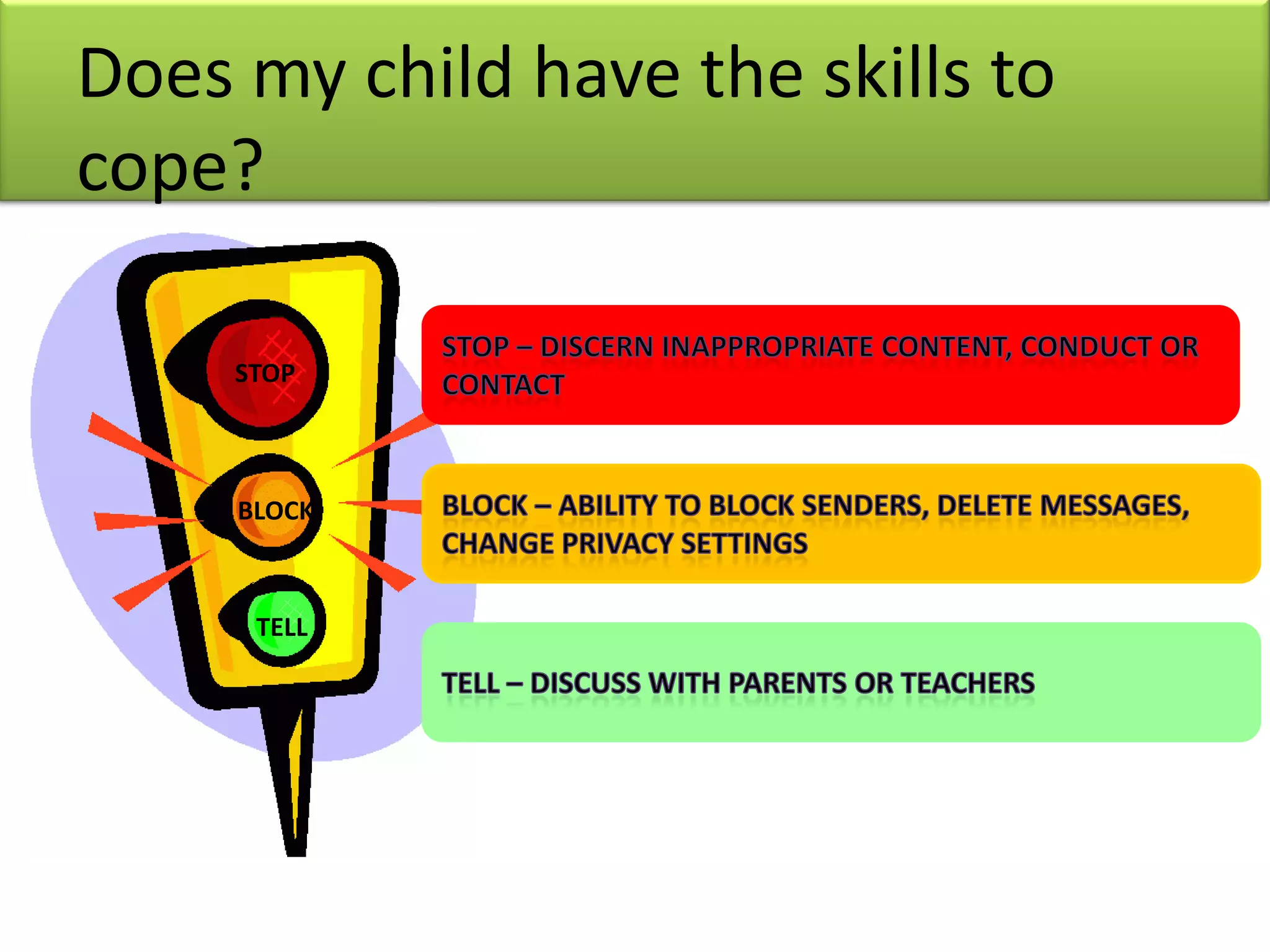
The document highlights the importance of parental awareness regarding cyber risks affecting teenage children, including exposure to inappropriate content, cyberbullying, and online predation. It provides best practices for parents, such as monitoring online activity, establishing rules regarding internet use, and discussing safety topics with their children. Additionally, it emphasizes the need for situational awareness and the use of technical controls to ensure safe internet practices.