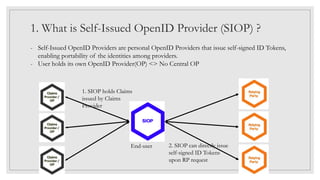
The document discusses the concept of Self-Issued OpenID Providers (SIOP), which allow users to issue self-signed ID tokens, enhancing identity portability. It outlines SIOP requirements, including requests and responses, privacy protection, claims binding, and deployment architectures. Additionally, it raises discussion points regarding challenges such as wallet identification and integration with decentralized identifiers.