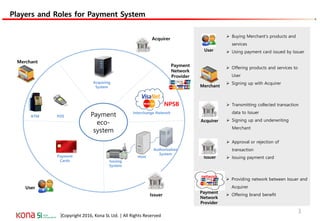
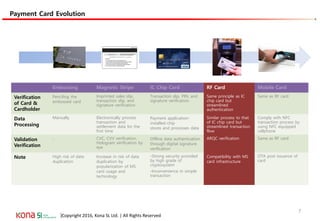
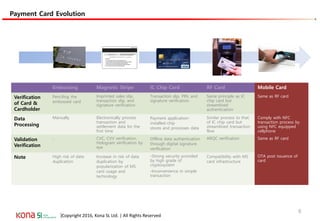
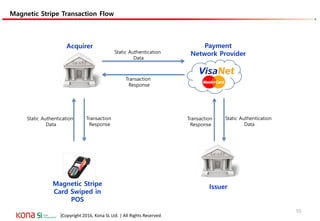
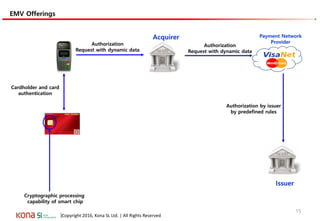
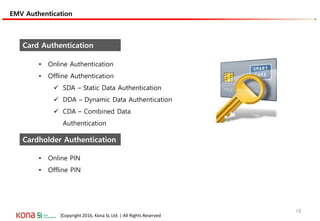
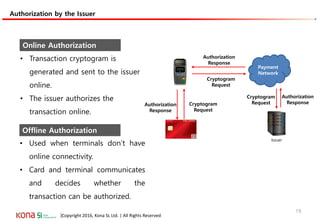
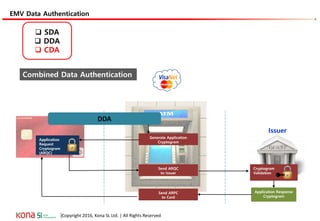
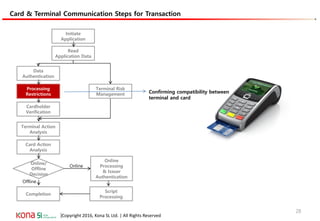
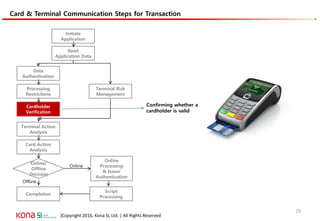
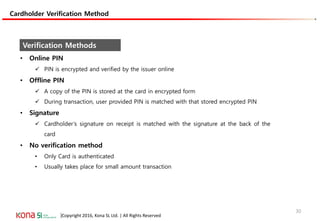
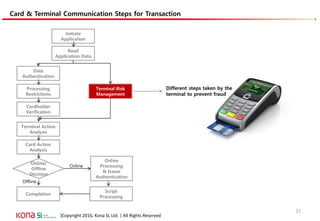
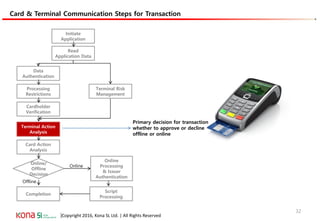
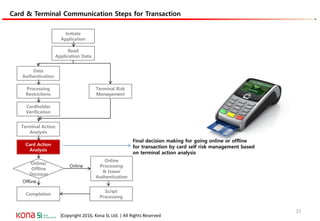
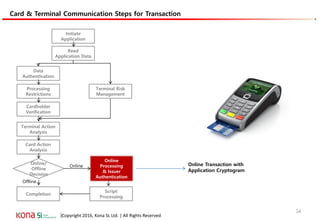
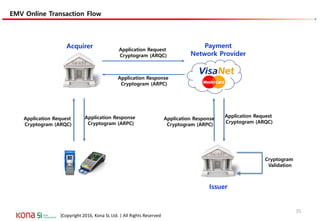
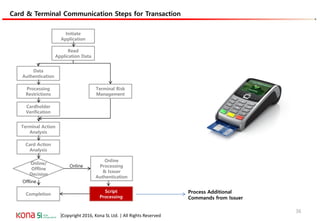
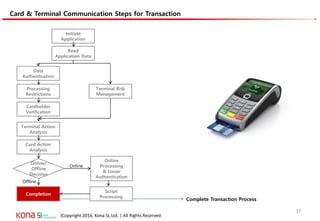
The document provides an overview of EMV (Europay, MasterCard, and Visa) standards, highlighting the roles of various players in the payment ecosystem such as issuers, acquirers, and payment network providers. It details the evolution of payment cards from magnetic stripe to chip and contactless technologies, emphasizing authentication and security features to combat fraud and data duplication risks. Additionally, the document outlines the transaction processes and risk assessment methods associated with EMV technology.