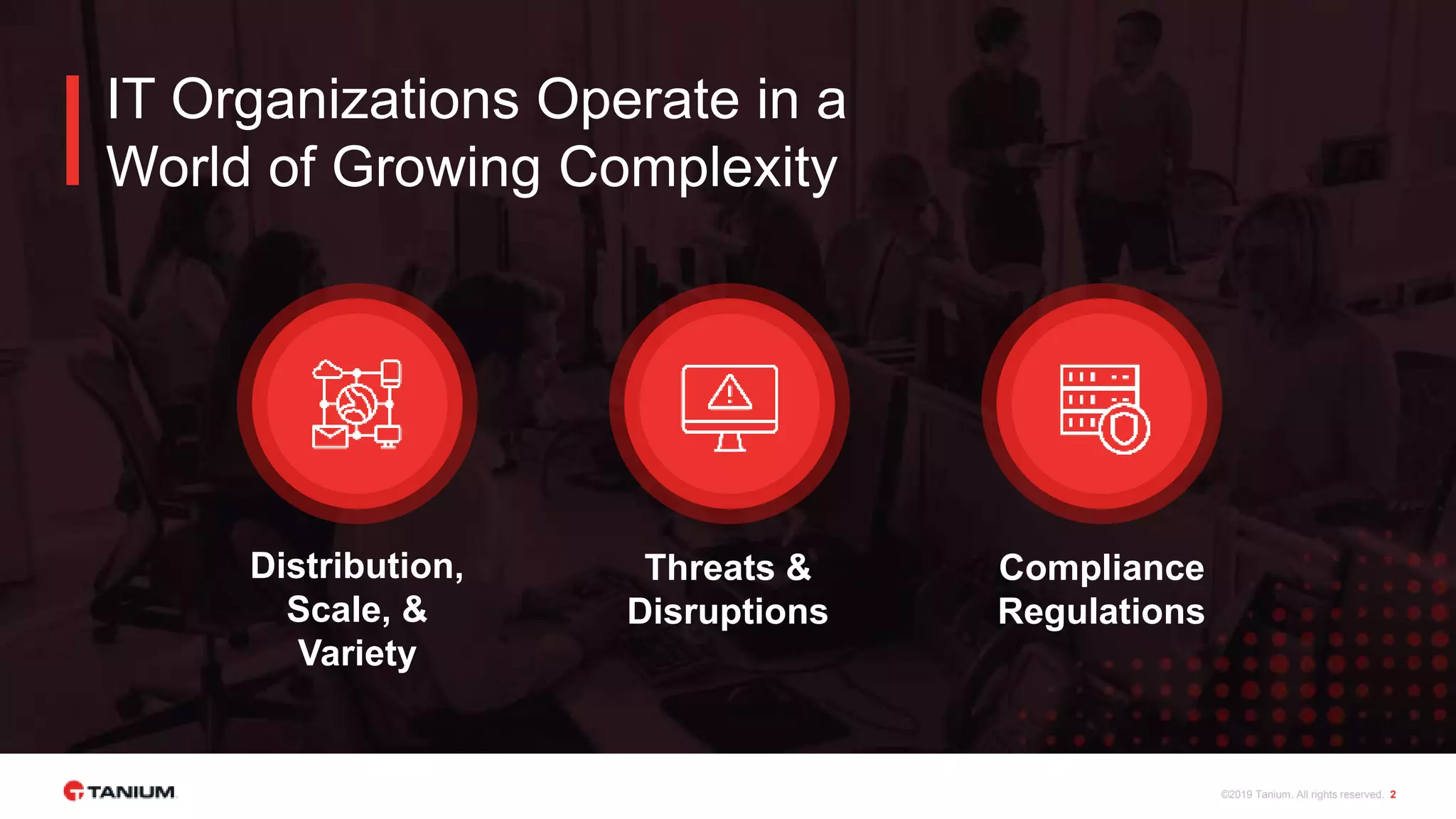
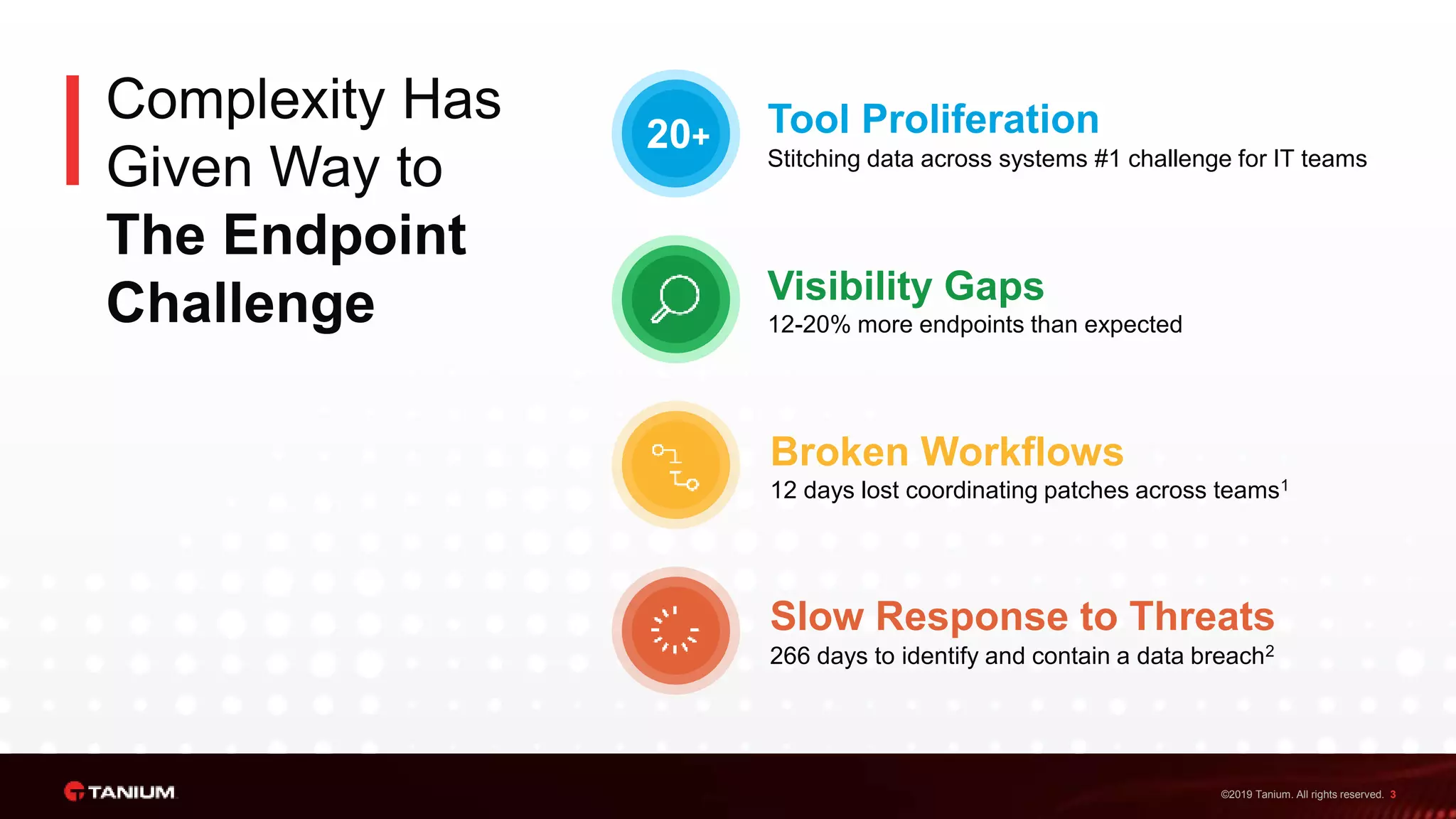
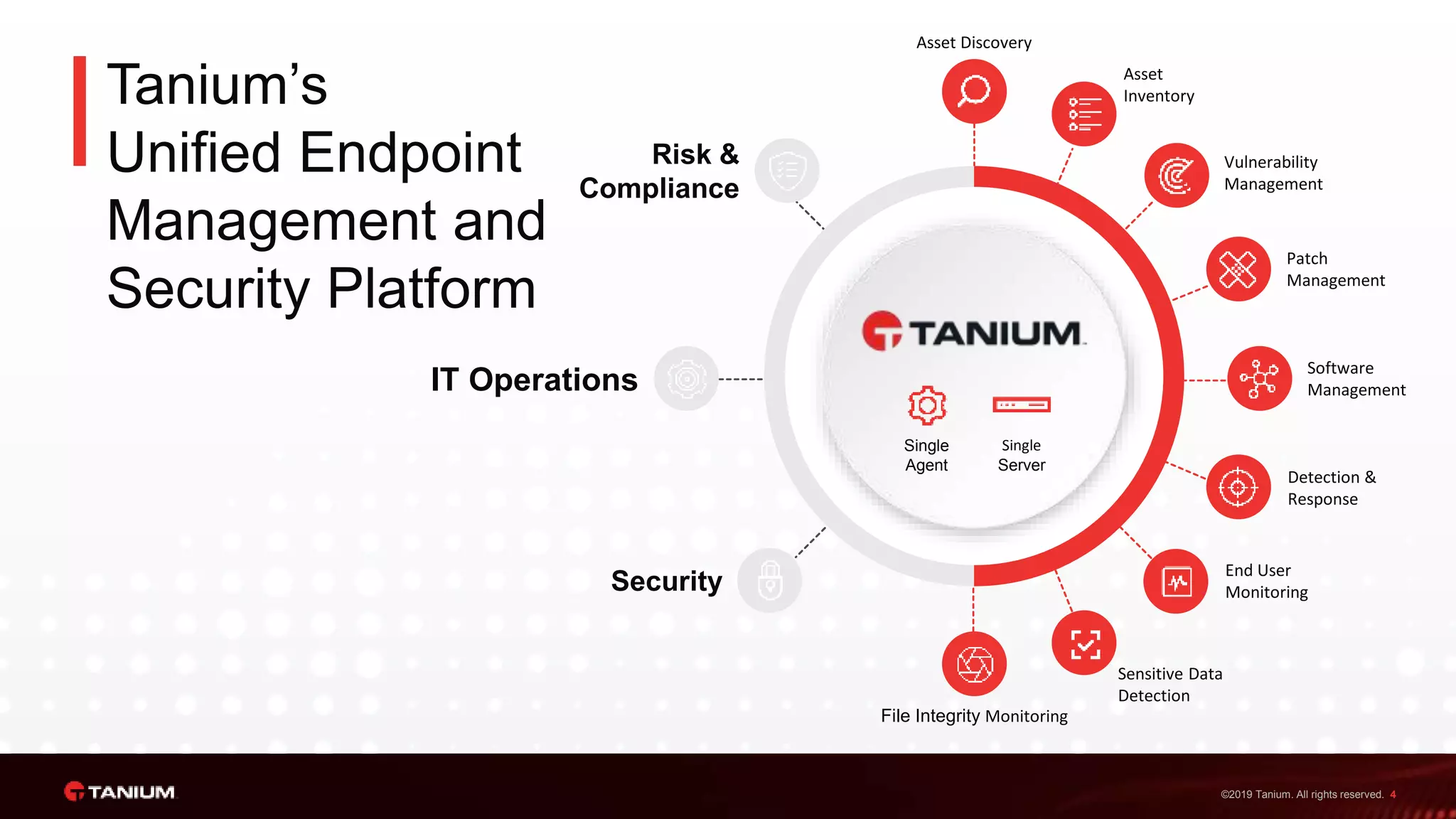
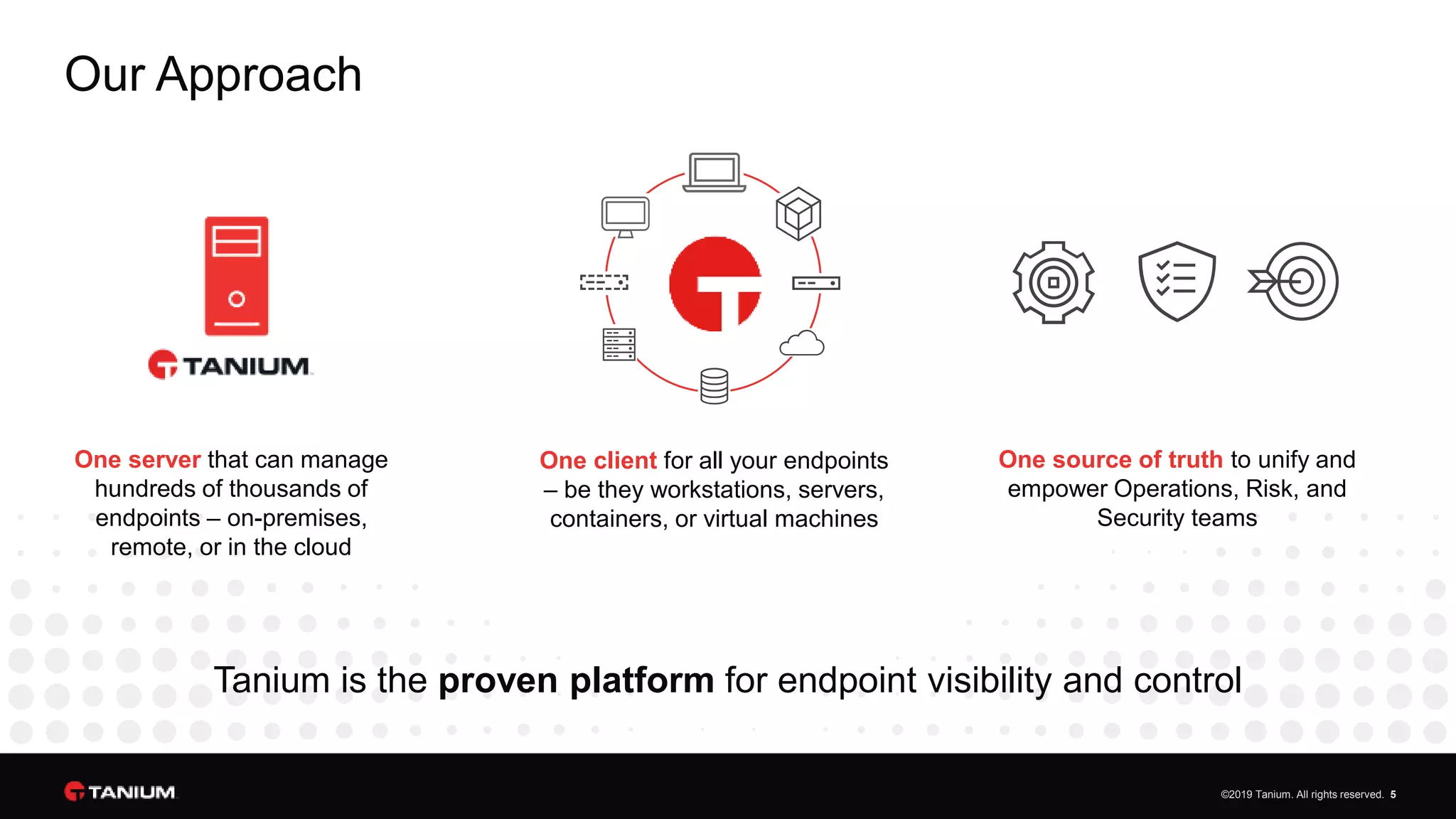
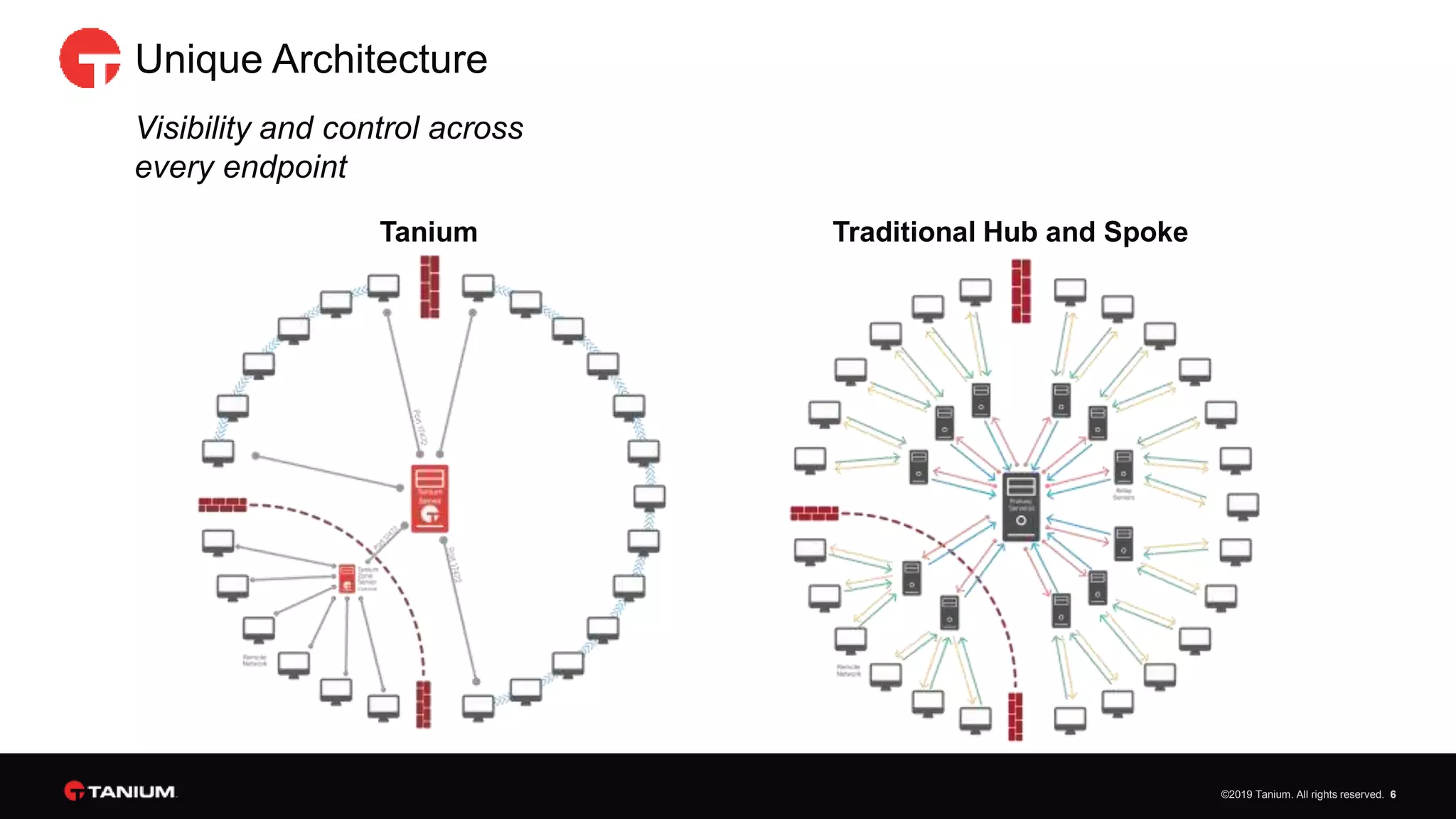
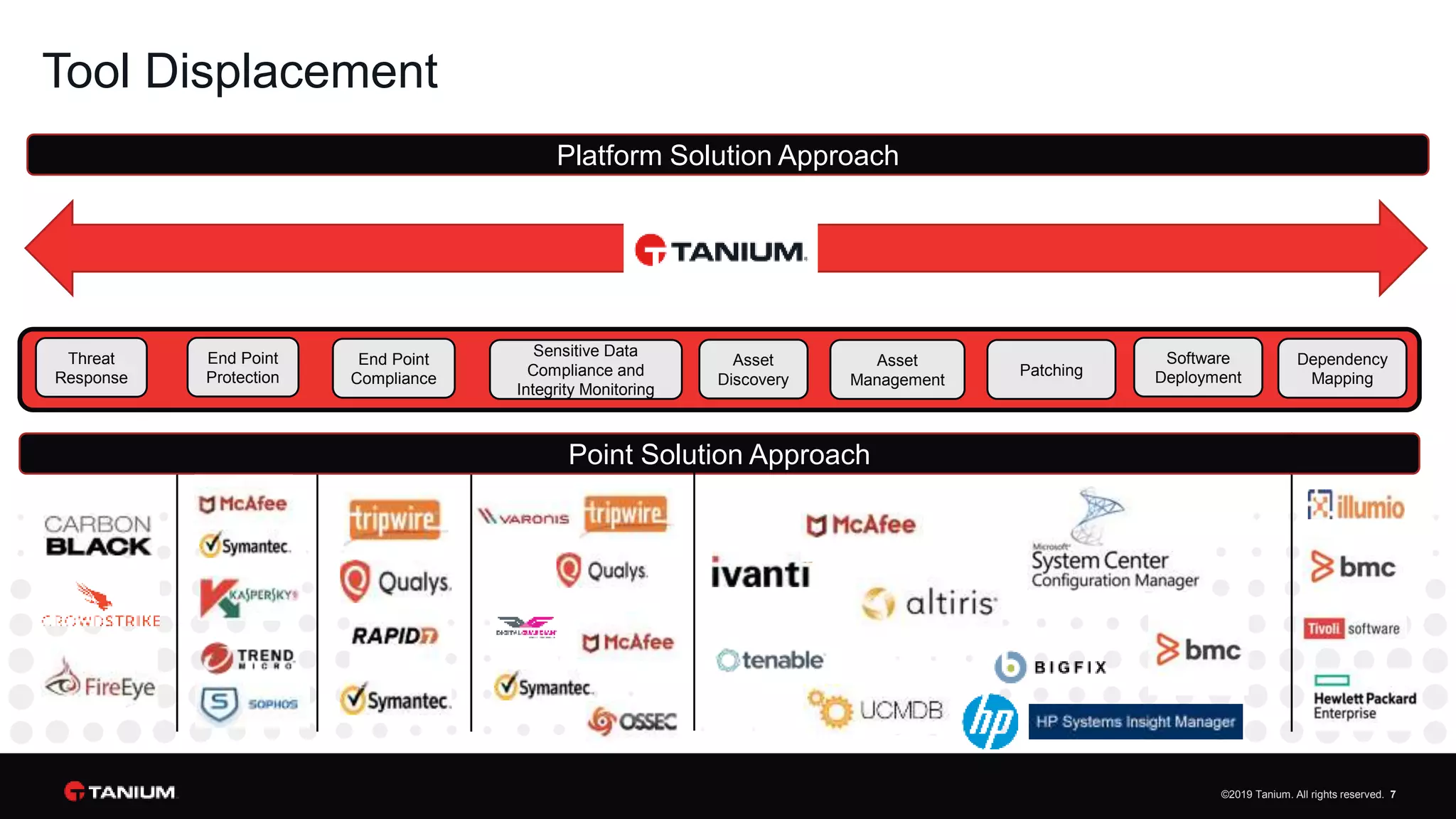
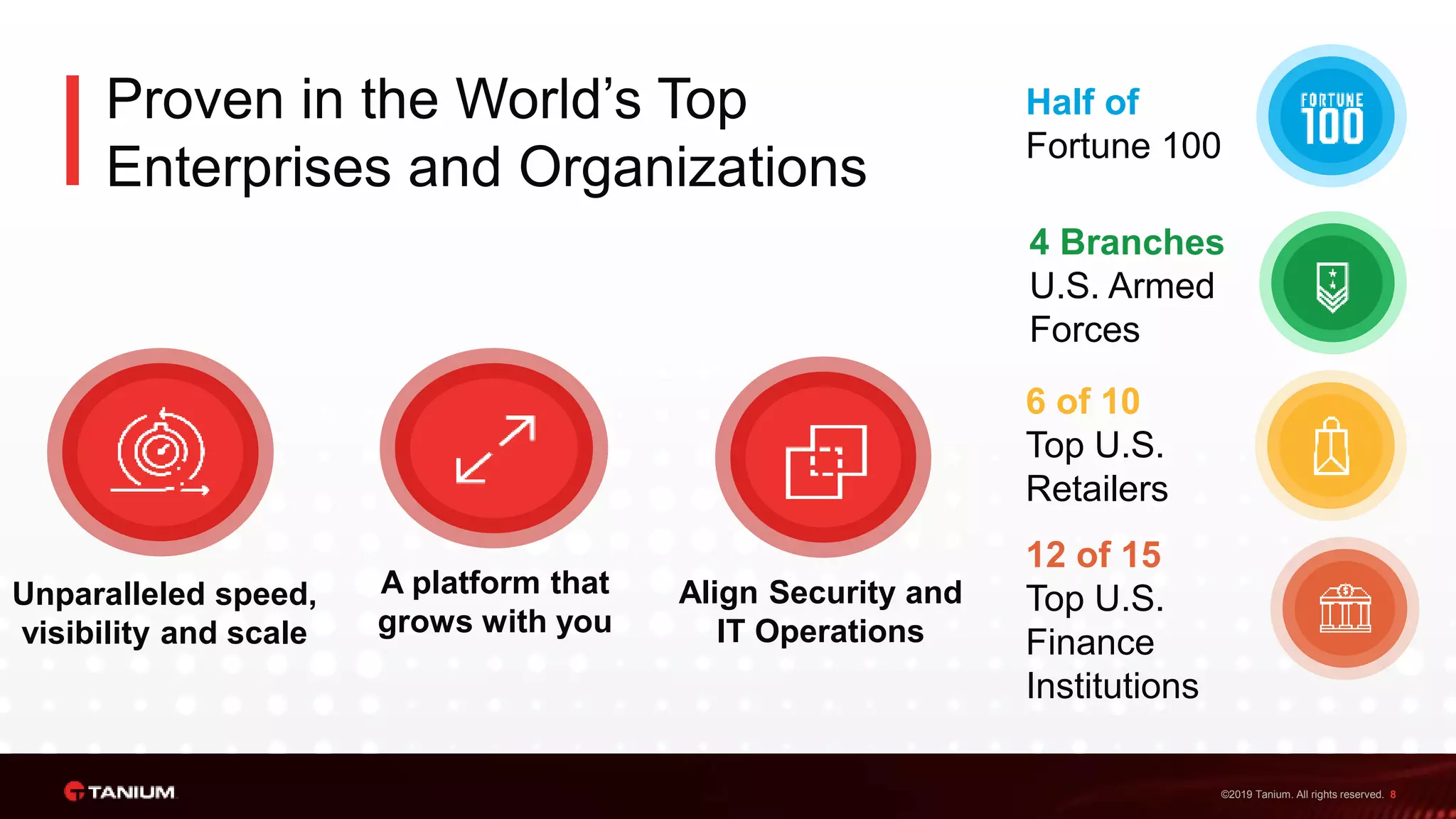
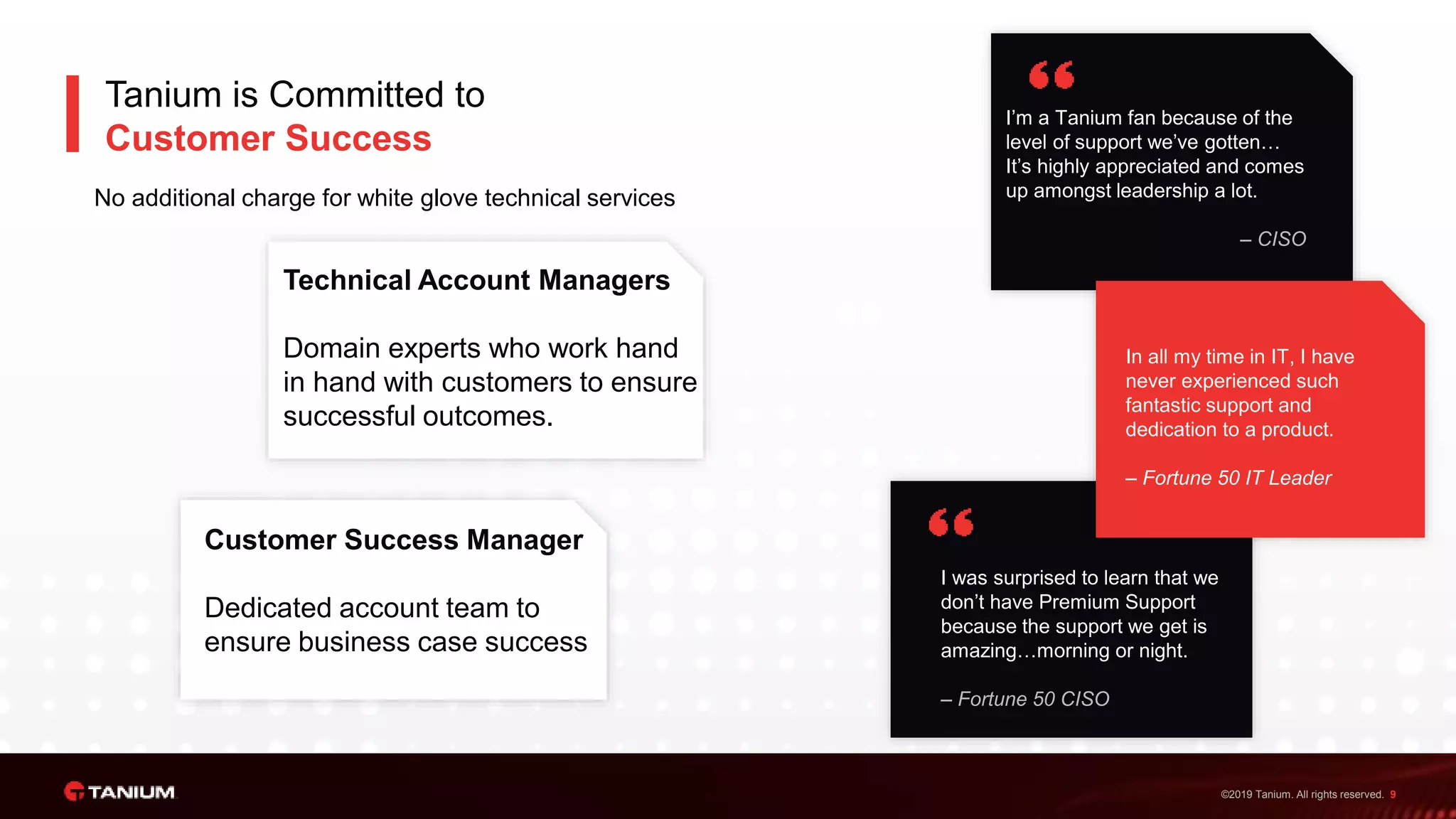
Tanium offers a unified platform for managing and securing endpoints, addressing the complexities faced by IT organizations due to tool proliferation and visibility gaps. The platform provides comprehensive visibility and control across various endpoint types, enabling organizations to respond rapidly to threats and manage compliance effectively. Trusted by top enterprises, Tanium emphasizes customer support and operational efficiency, catering to both security and IT operations teams.