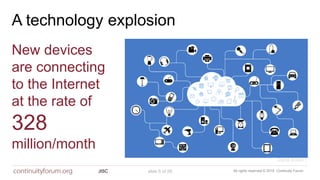
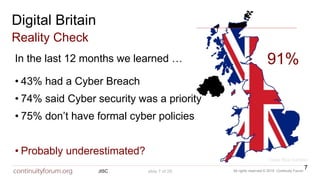
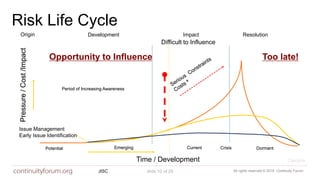
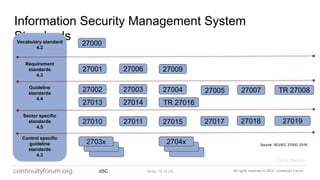
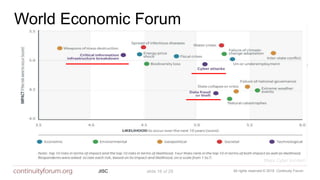
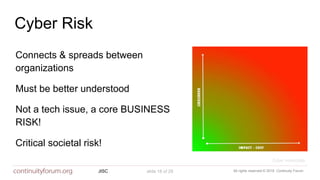
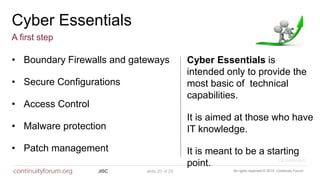
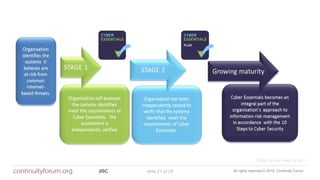
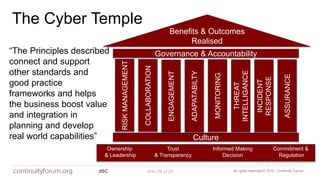
The document discusses cybersecurity standards and managing cyber risk at the business level. It provides context on the evolution of cybersecurity standards over time from BS 7799 in 1995 to current standards like ISO 27001 and newer frameworks like Cyber Essentials. However, it argues these standards only provide basic technical capabilities and that businesses need to view cyber risk as a core business risk, requiring engagement from the board level and a risk management approach integrated with business objectives. The document advocates for the principles in the new BS 31111 standard which aims to better connect cyber risk management with overall business strategy, governance, culture and operations.