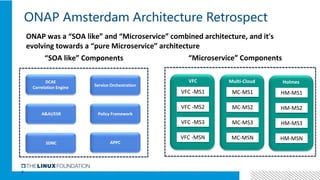
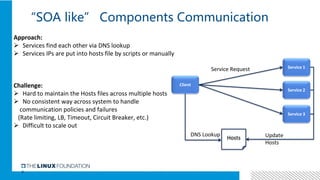
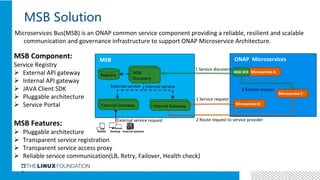
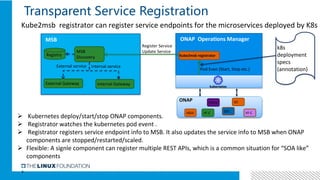
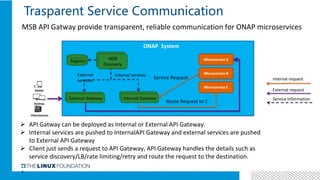
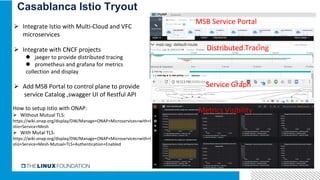
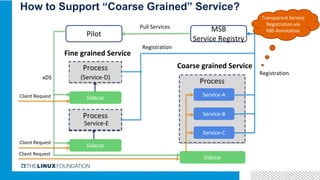
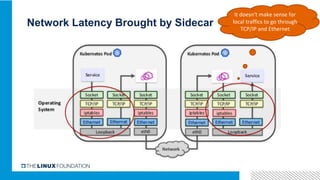
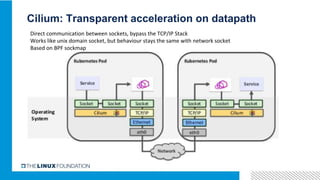
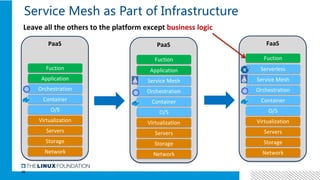
1. ONAP was evolving from a "SOA-like" architecture to a "pure microservices" architecture. MSB provided transparent service registration and communication for ONAP microservices.
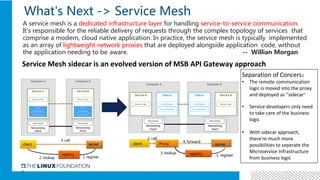
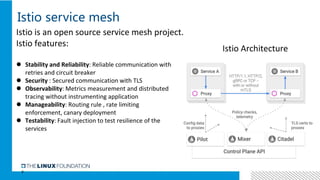
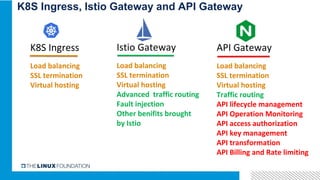
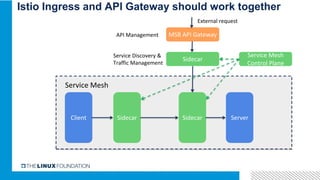
2. Istio is an open source service mesh that provides reliability, security, observability and manageability for microservices. It introduces a centralized control plane to manage distributed sidecars.
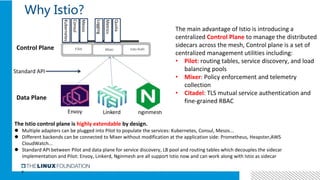
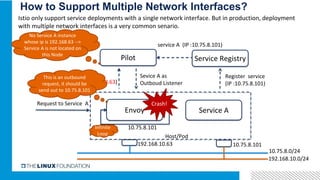
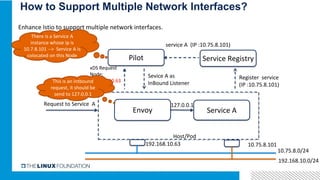
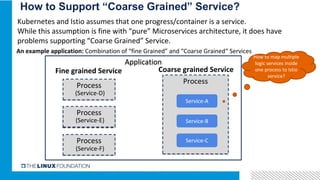
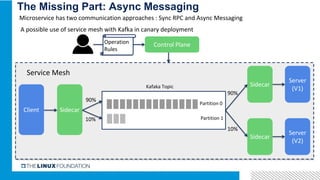
3. Integrating Istio with ONAP would provide benefits like distributed tracing, metrics visibility and service graph for ONAP microservices. It is important to address challenges in supporting multiple network interfaces and coarse-grained services.