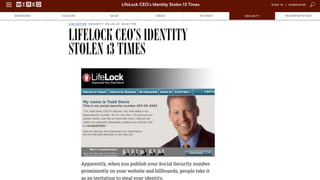
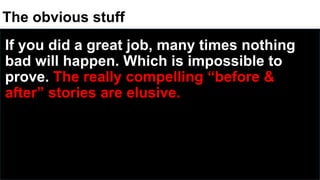
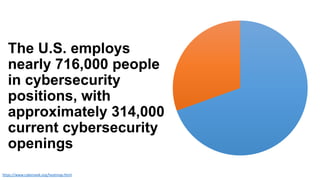
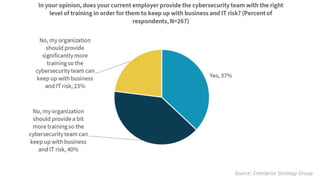
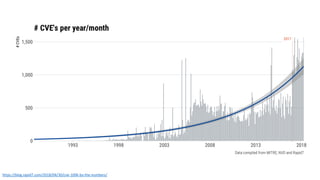
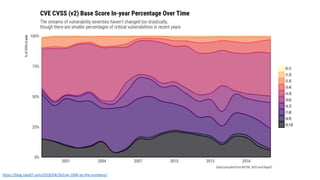
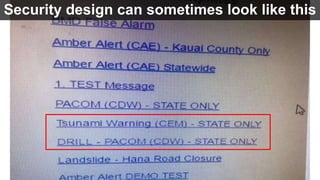
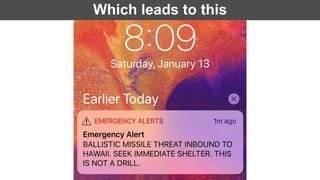
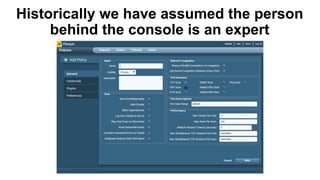
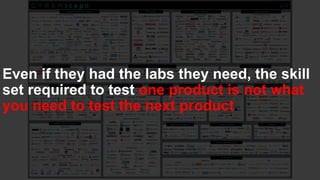
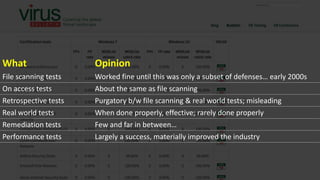
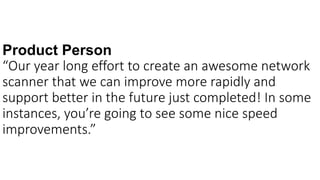
The document discusses the challenges in cybersecurity product development and evaluation, highlighting issues such as the difficulty of building secure products, the understaffing of security teams, and the pressure on professionals to make quick decisions amidst rising threats. It critiques the marketing and evaluation processes of security products, emphasizing the need for better testing environments and clearer communication of product benefits. Ultimately, the author suggests actionable steps for both security professionals and vendors to break the cyclical nature of these issues.