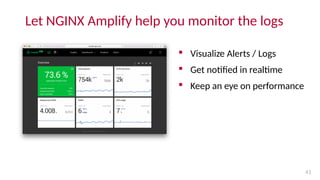
Christian Folini gave a presentation on optimizing ModSecurity on NGINX and NGINX Plus. Some key points:
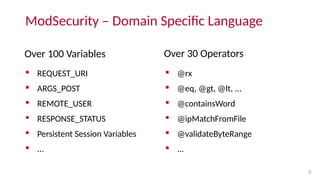
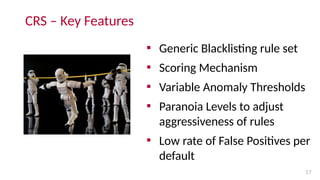
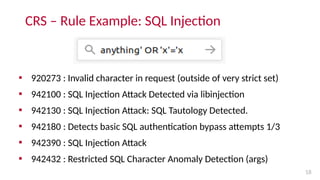
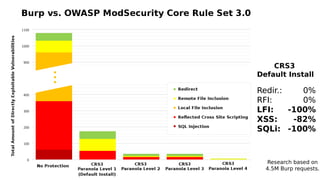
- ModSecurity is an open source web application firewall that provides a rule-based system. The OWASP ModSecurity Core Rule Set (CRS) is the default rule set that blocks over 80% of attacks.
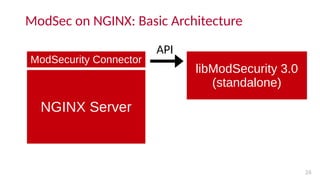
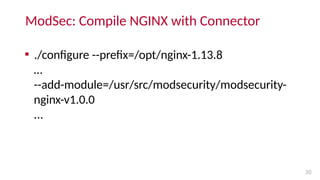
- To use ModSecurity with NGINX, one must compile ModSecurity 3.0 and the ModSecurity NGINX connector module, then compile NGINX with the connector. Alternatively, precompiled binaries are available with NGINX Plus.
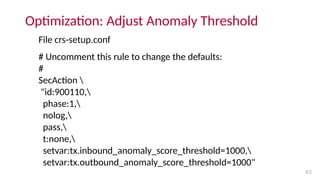
- Initial optimization steps include adjusting the anomaly threshold, learning to read logs using aliases, and handling false positives by







![ModSecurity – Rule Example I
10
Whitelisting rule allowing only parameter “firstname” matching a
predefined pattern:
SecRule ARGS:firstname "!@rx ^[a-zA-Z-]*$" "id:1000,deny"](https://image.slidesharecdn.com/modsec-nginx-webinar-2018-01-180109202133/85/Optimizing-ModSecurity-on-NGINX-and-NGINX-Plus-10-320.jpg)



















![Example Rule Alert – Right out of Sysadmin Hell
37
2018/01/09 14:55:50 [info] 1167#1167: *1 ModSecurity: Warning. Matched
"Operator `PmFromFile' with parameter `lfi-os-files.data' against variable
`ARGS:test' (Value: `/etc/passwd' ) [file "/tmp/nginx-crs/rules/REQUEST-930-
APPLICATION-ATTACK-LFI.conf"] [line "71"] [id "930120"] [rev "4"] [msg "OS File
Access Attempt"] [data "Matched Data: etc/passwd found within ARGS:test:
/etc/passwd"] [severity "2"] [ver "OWASP_CRS/3.0.0"] [maturity "0"] [accuracy
"0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag
"attack-lfi"] [tag "OWASP_CRS/WEB_ATTACK/FILE_INJECTION"] [tag
"WASCTC/WASC-33"] [tag "OWASP_TOP_10/A4"] [tag "PCI/6.5.4"] [hostname
"127.0.0.1"] [uri "/index.html"] [unique_id "151550615052.381887"] [ref
"o1,10v21,11t:utf8toUnicode,t:urlDecodeUni,t:normalizePathWin,t:lowercase"],
client: 127.0.0.1, server: localhost, request: "GET /index.html?test=/etc/passwd
HTTP/1.1", host: "localhost"](https://image.slidesharecdn.com/modsec-nginx-webinar-2018-01-180109202133/85/Optimizing-ModSecurity-on-NGINX-and-NGINX-Plus-37-320.jpg)


![Optimization: More aliases in the collection
40
meldata
melidmsg
melline
melmsg
meltags
melunique_id
...
sucs
greppl[1-4]
mappl
pathsegs[1-5]
col[1-20]
Swapcolumns
...](https://image.slidesharecdn.com/modsec-nginx-webinar-2018-01-180109202133/85/Optimizing-ModSecurity-on-NGINX-and-NGINX-Plus-40-320.jpg)