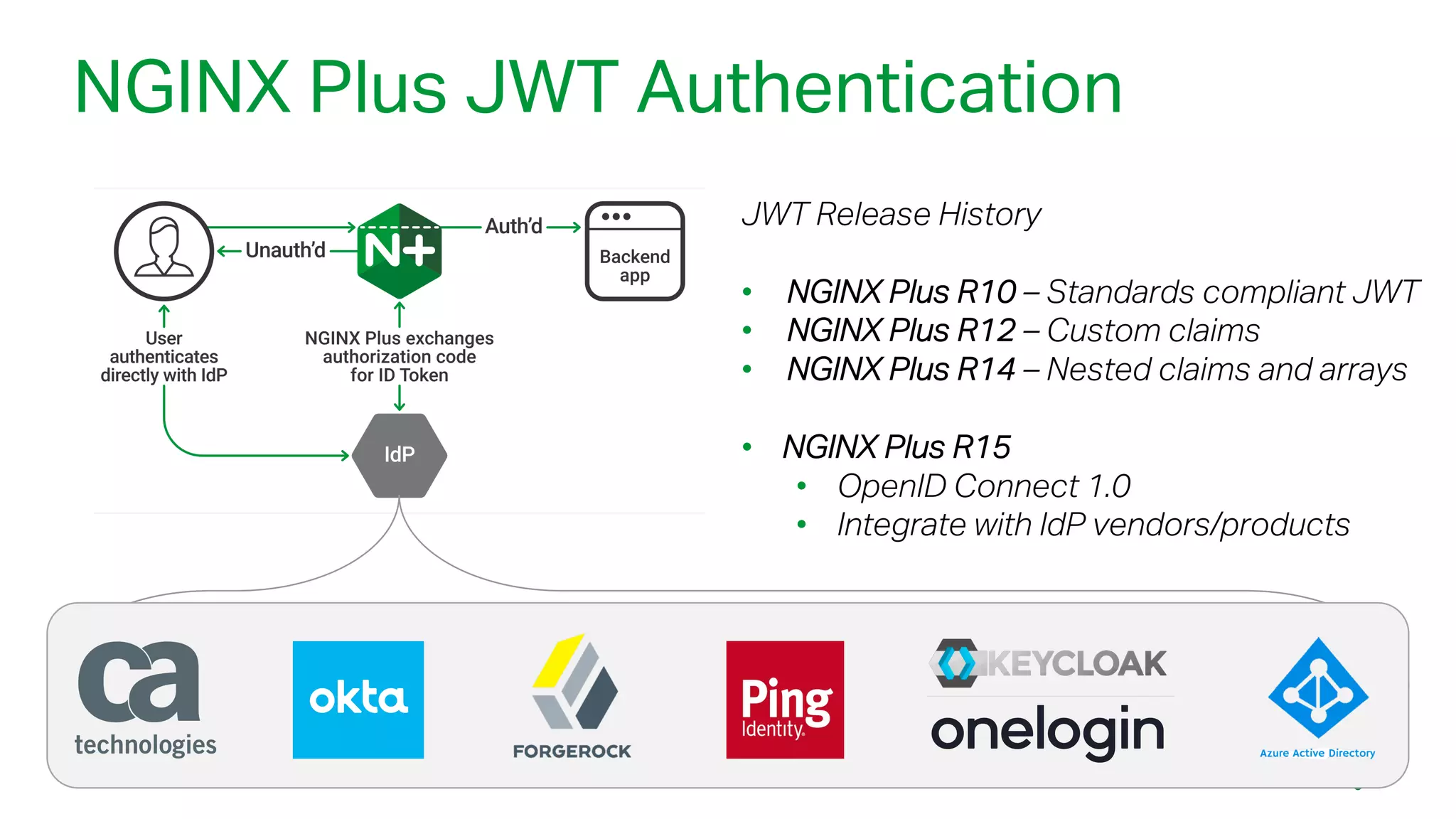
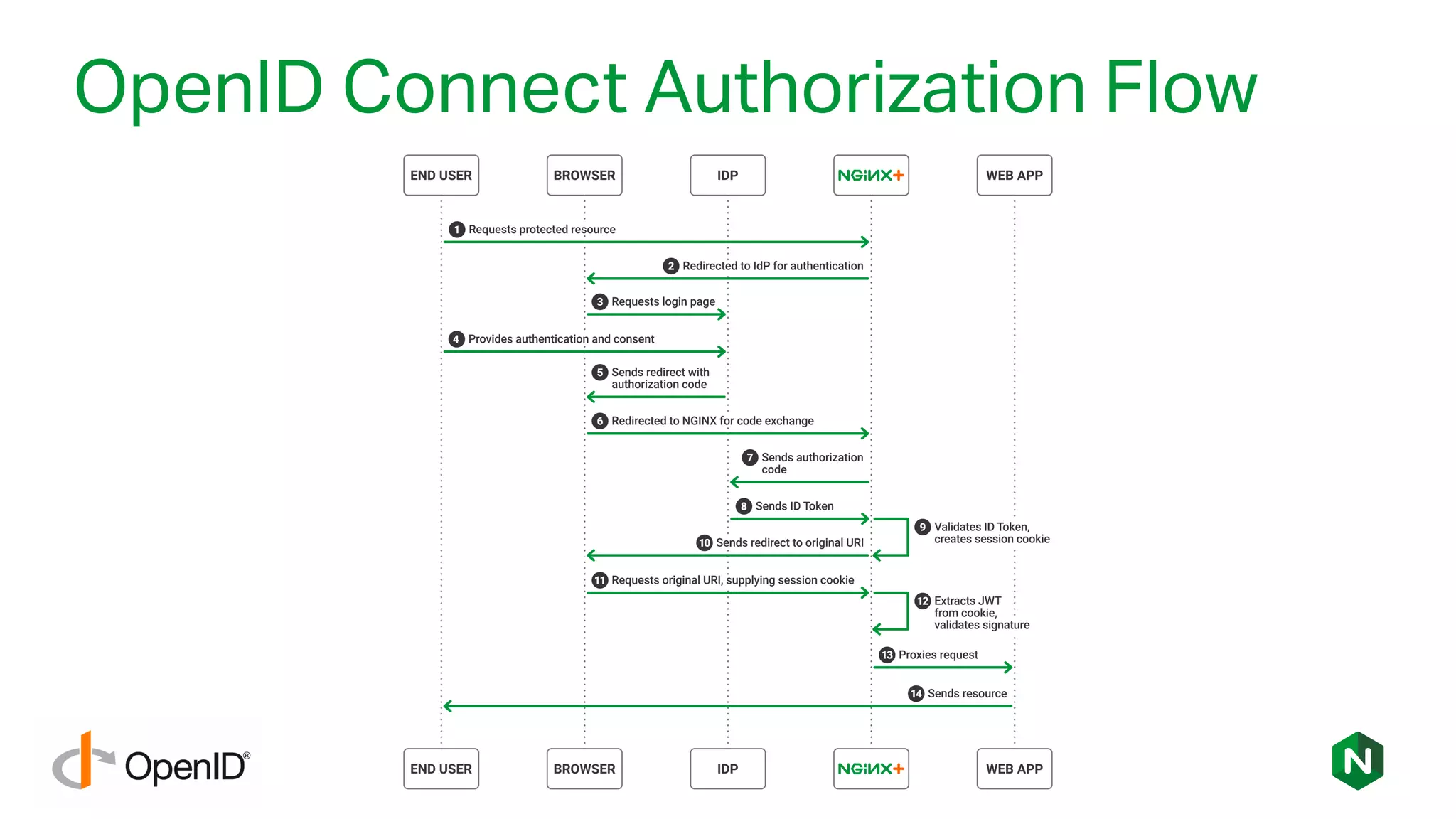
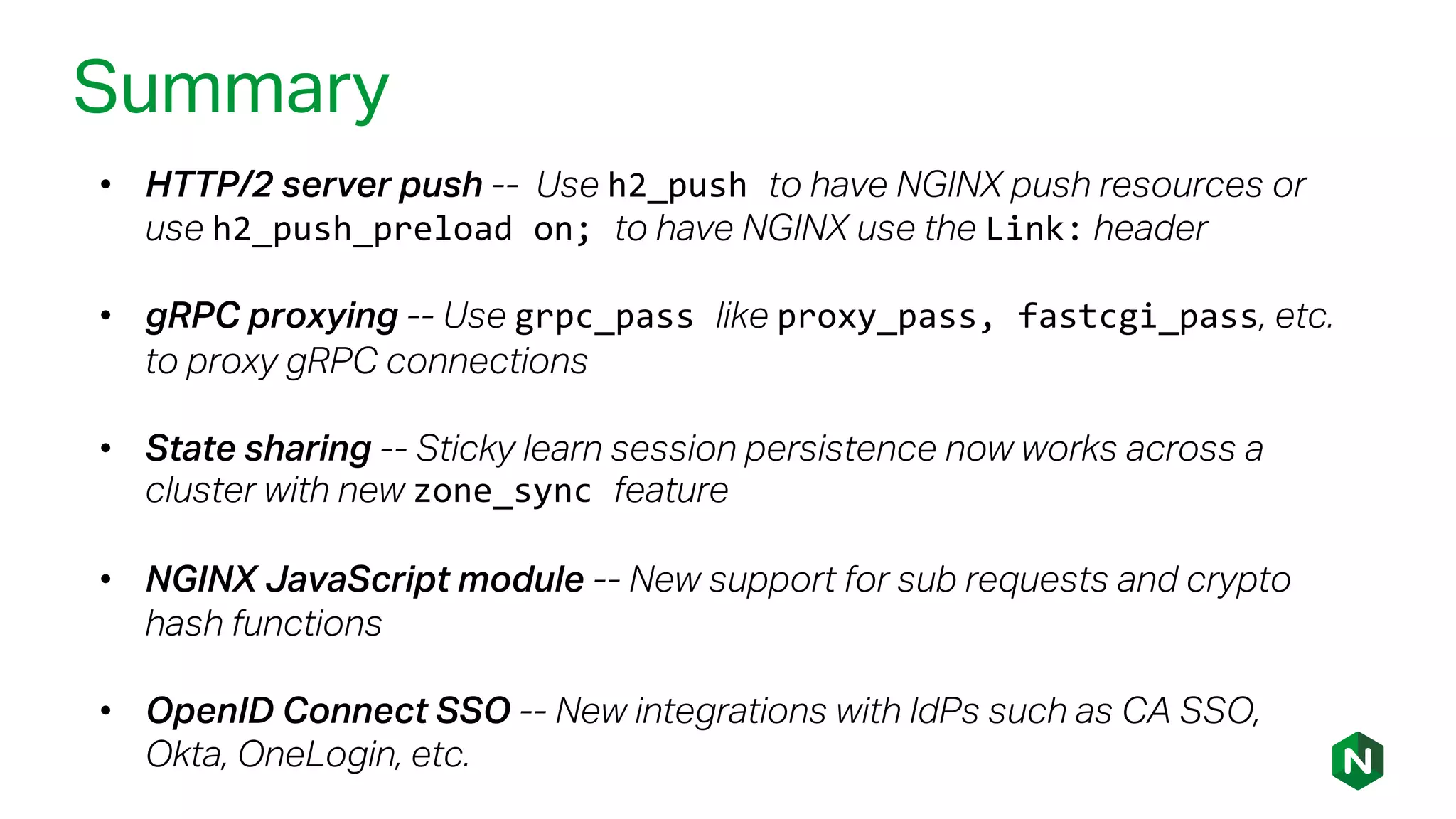
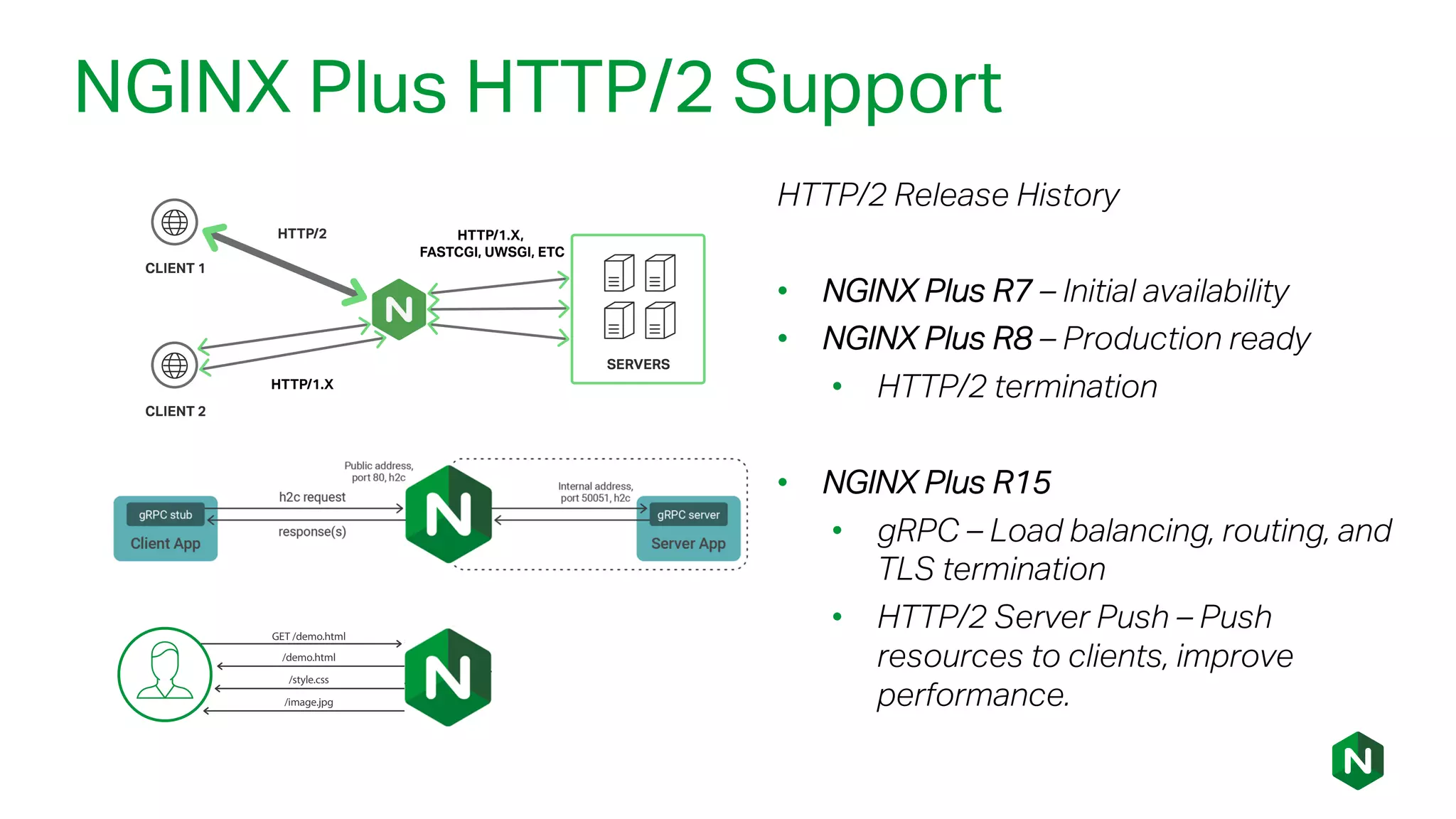
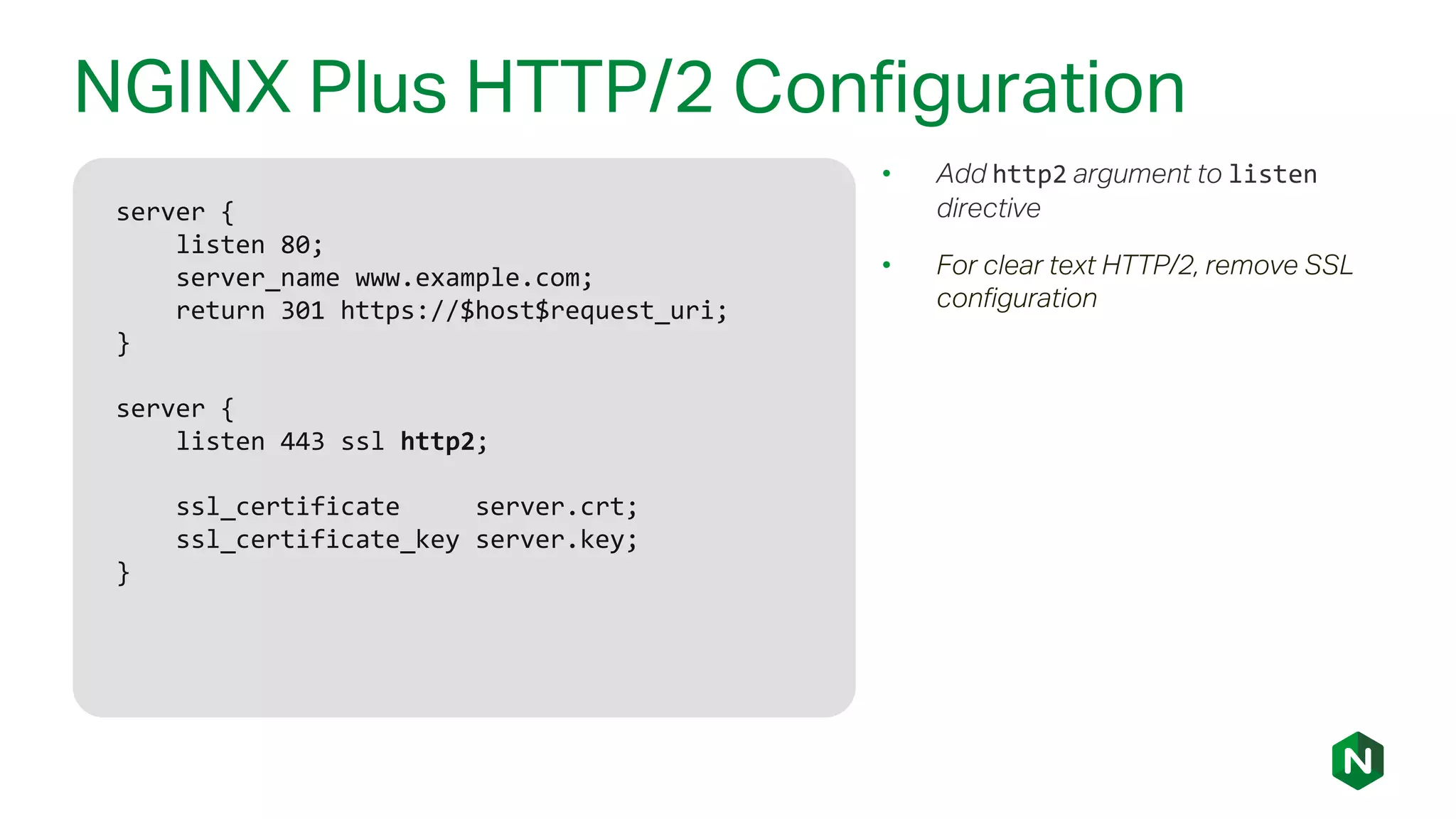
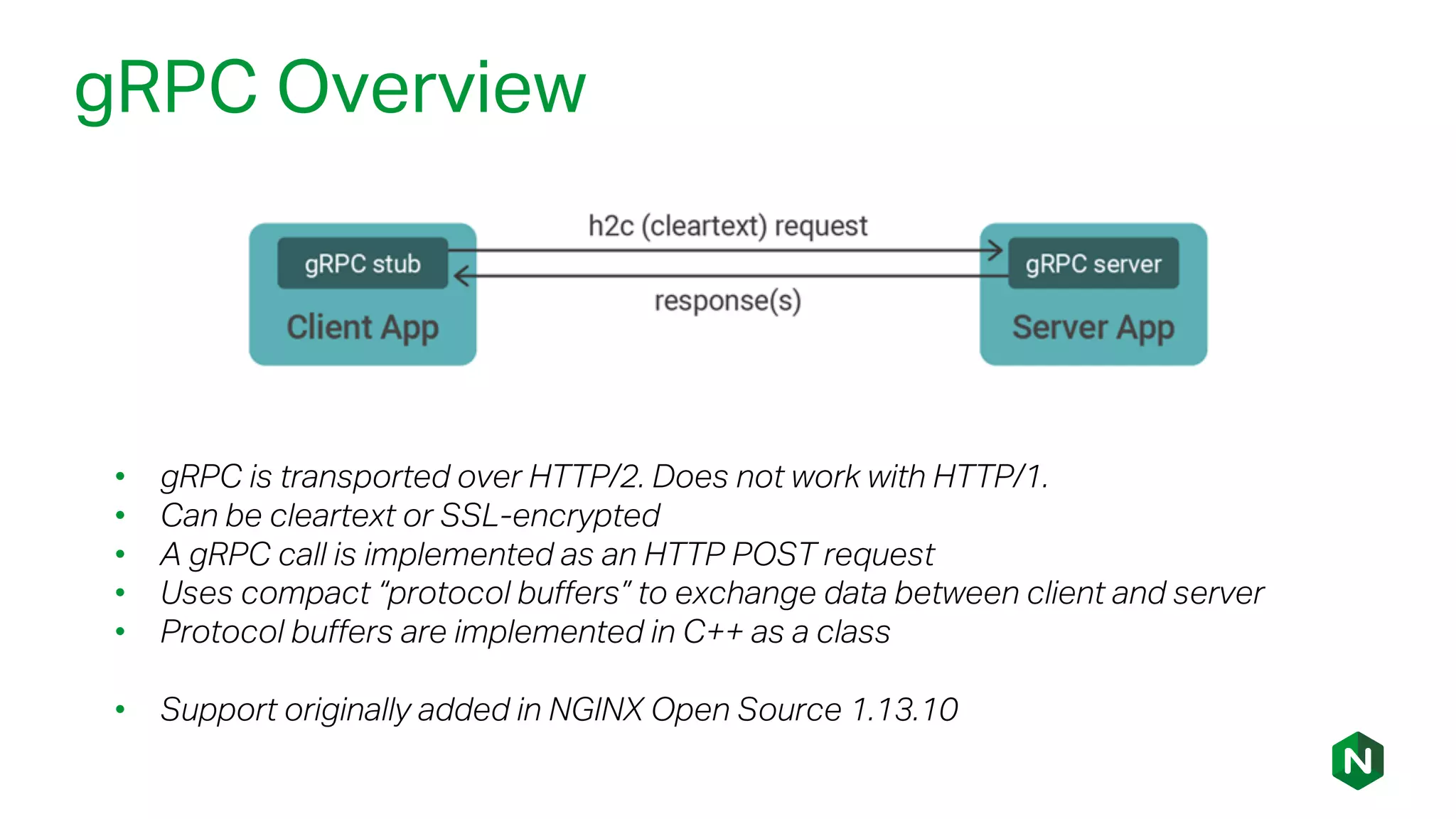
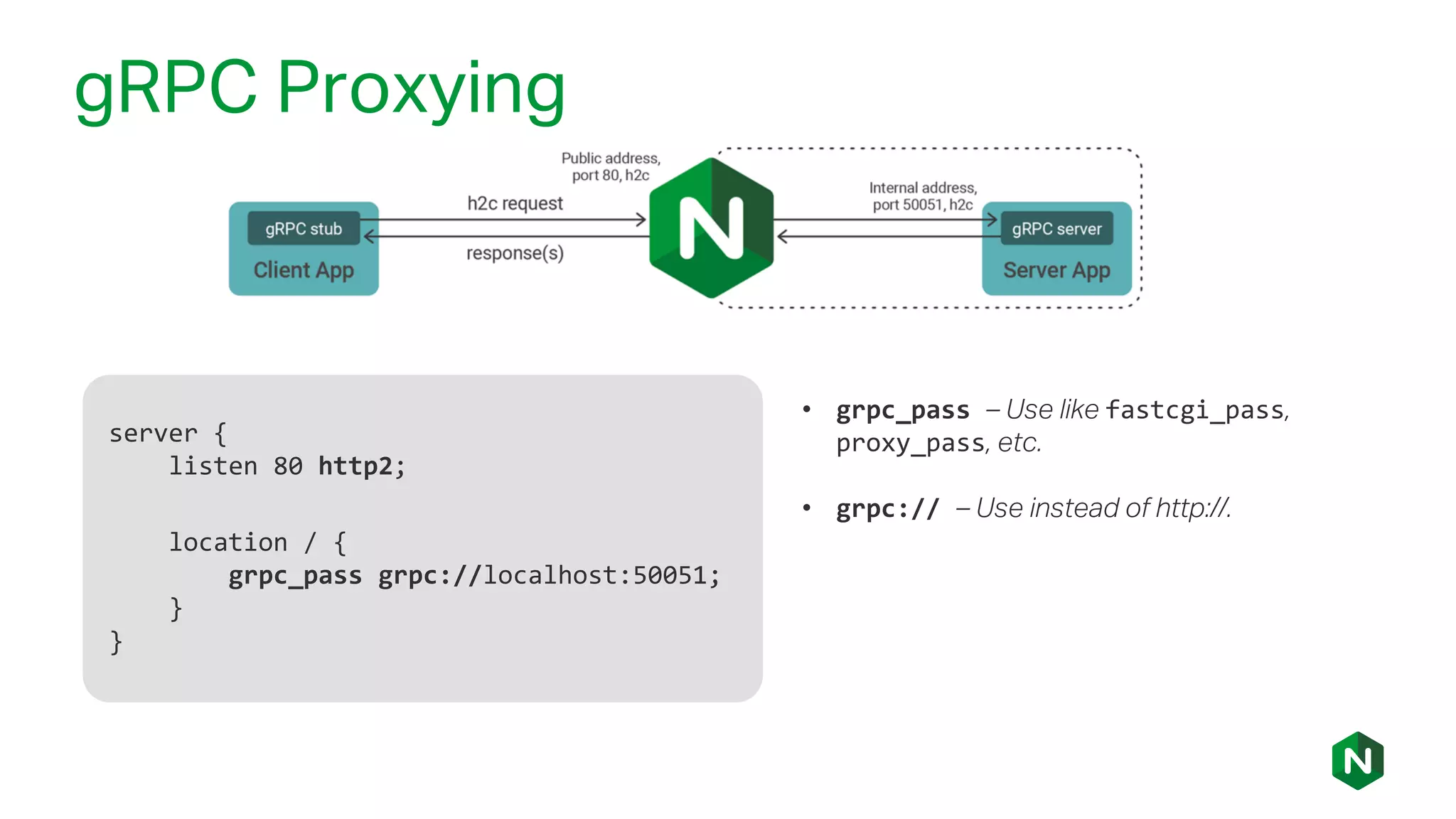
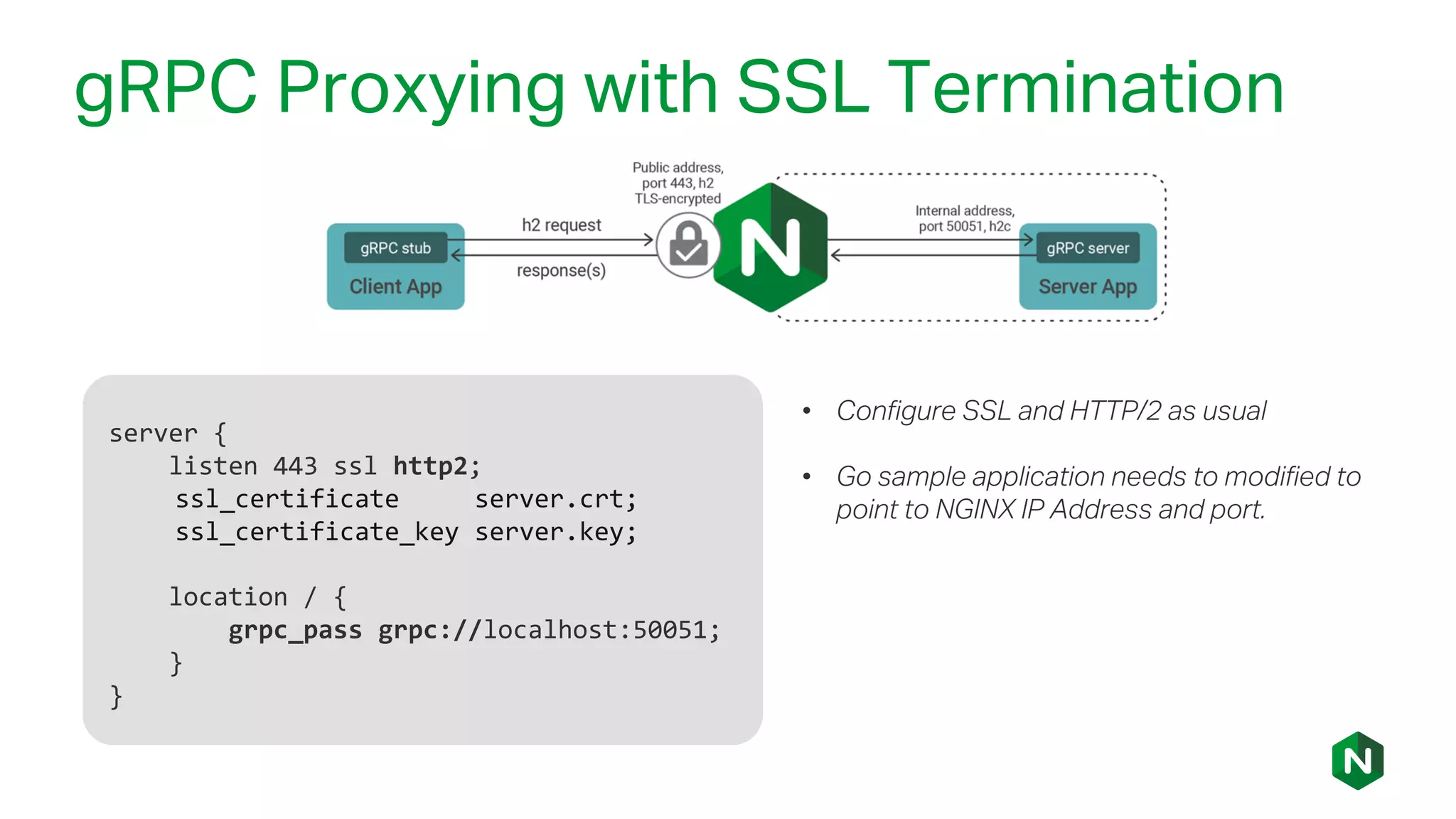
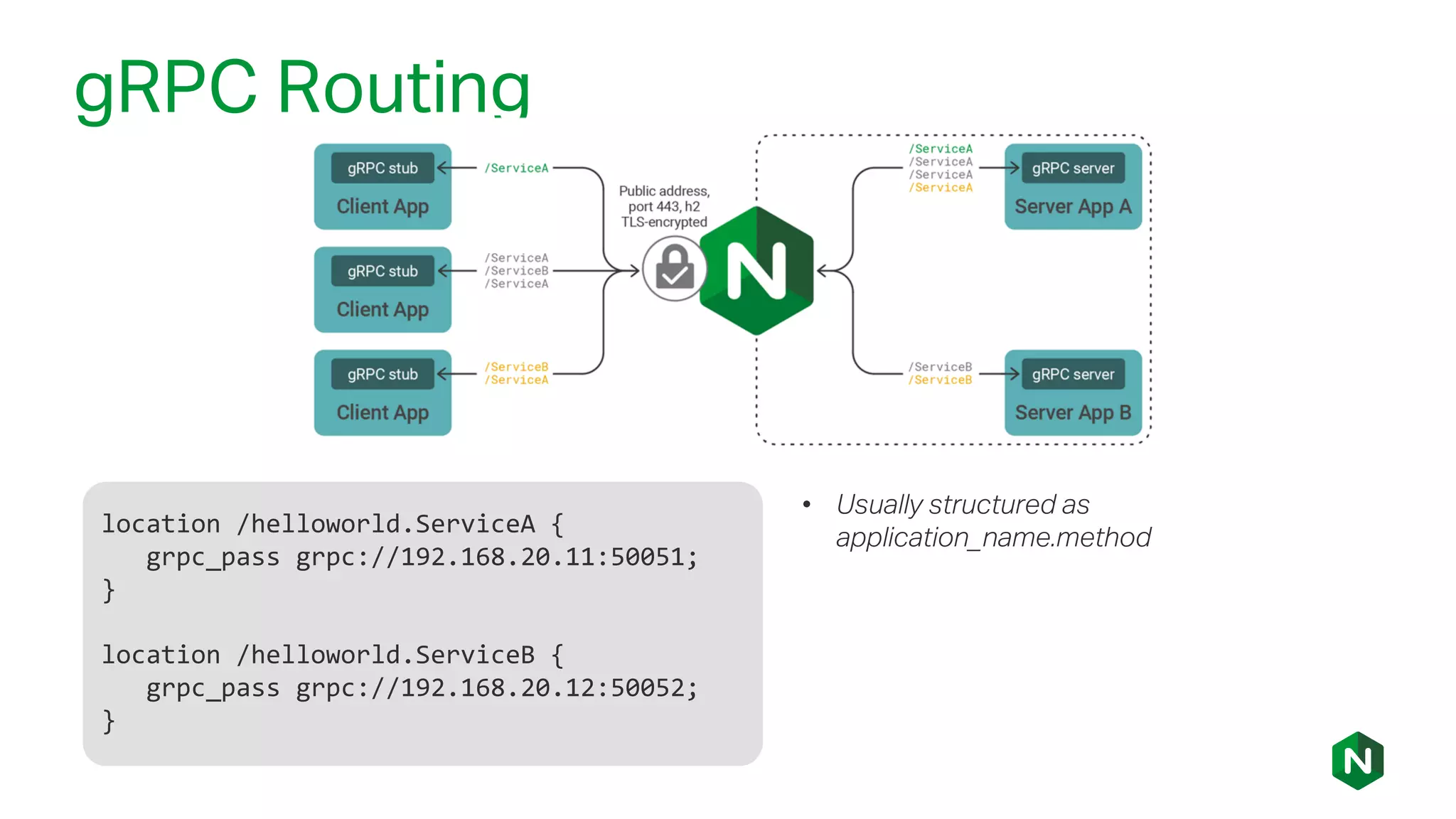
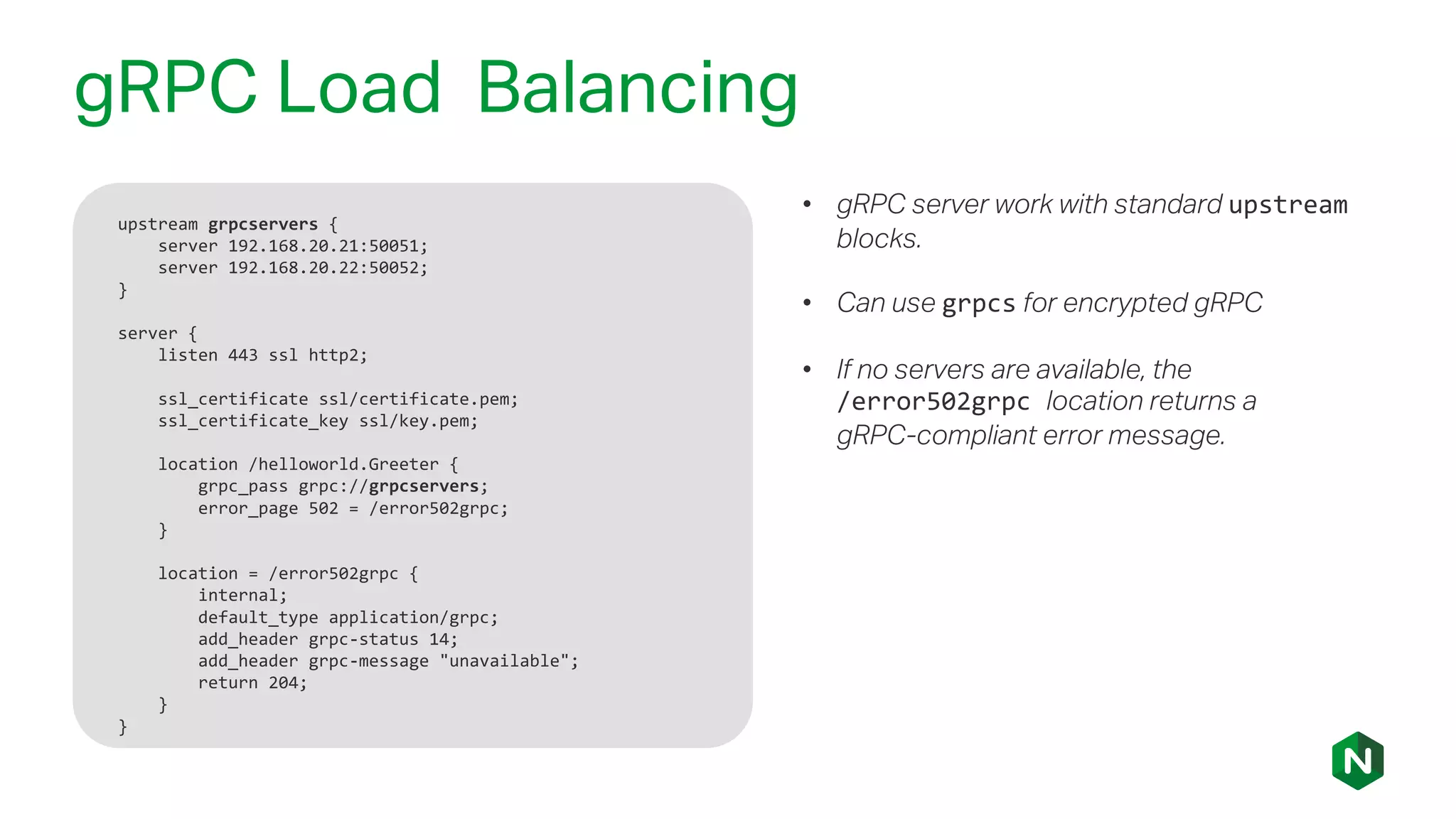
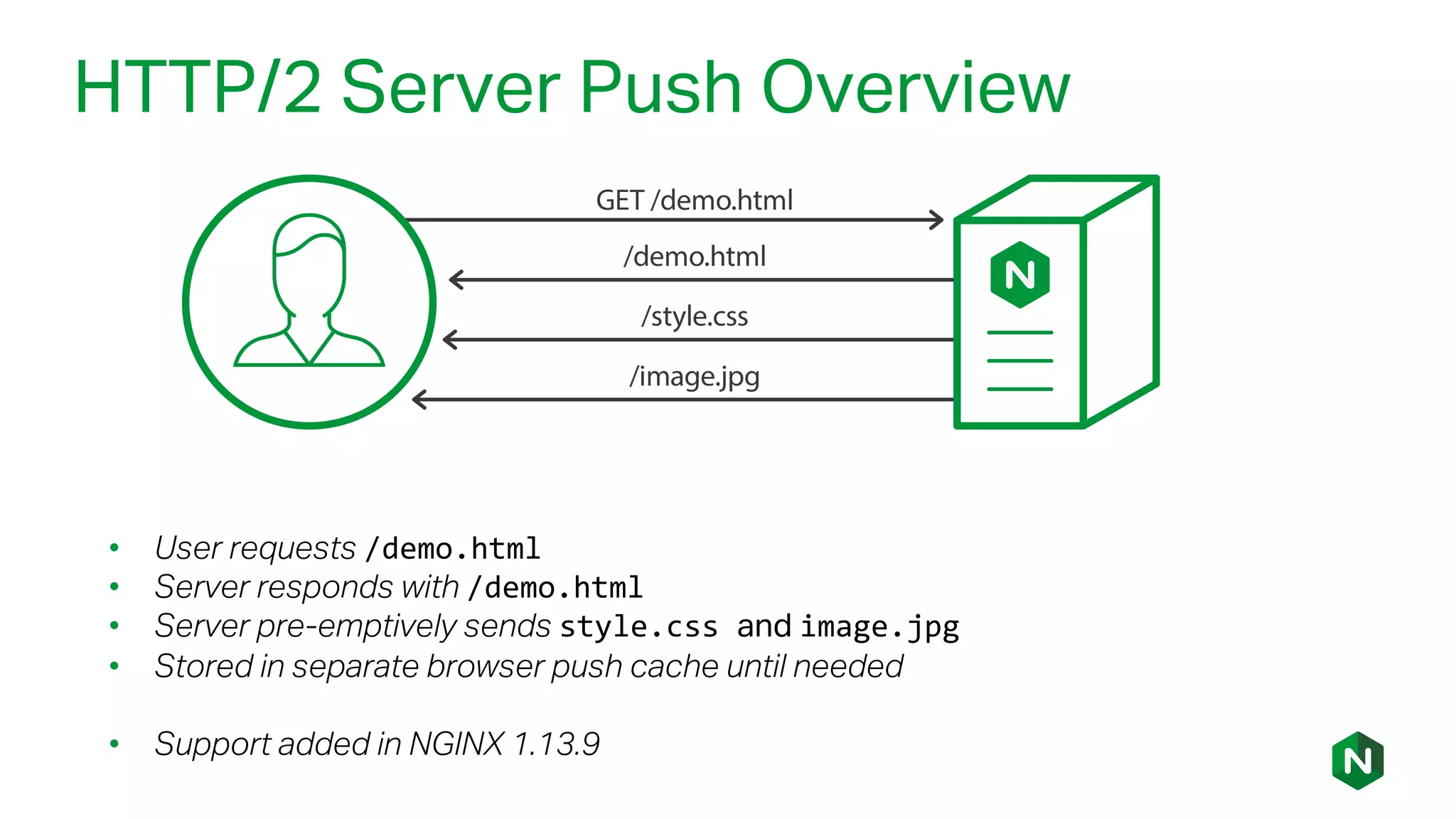
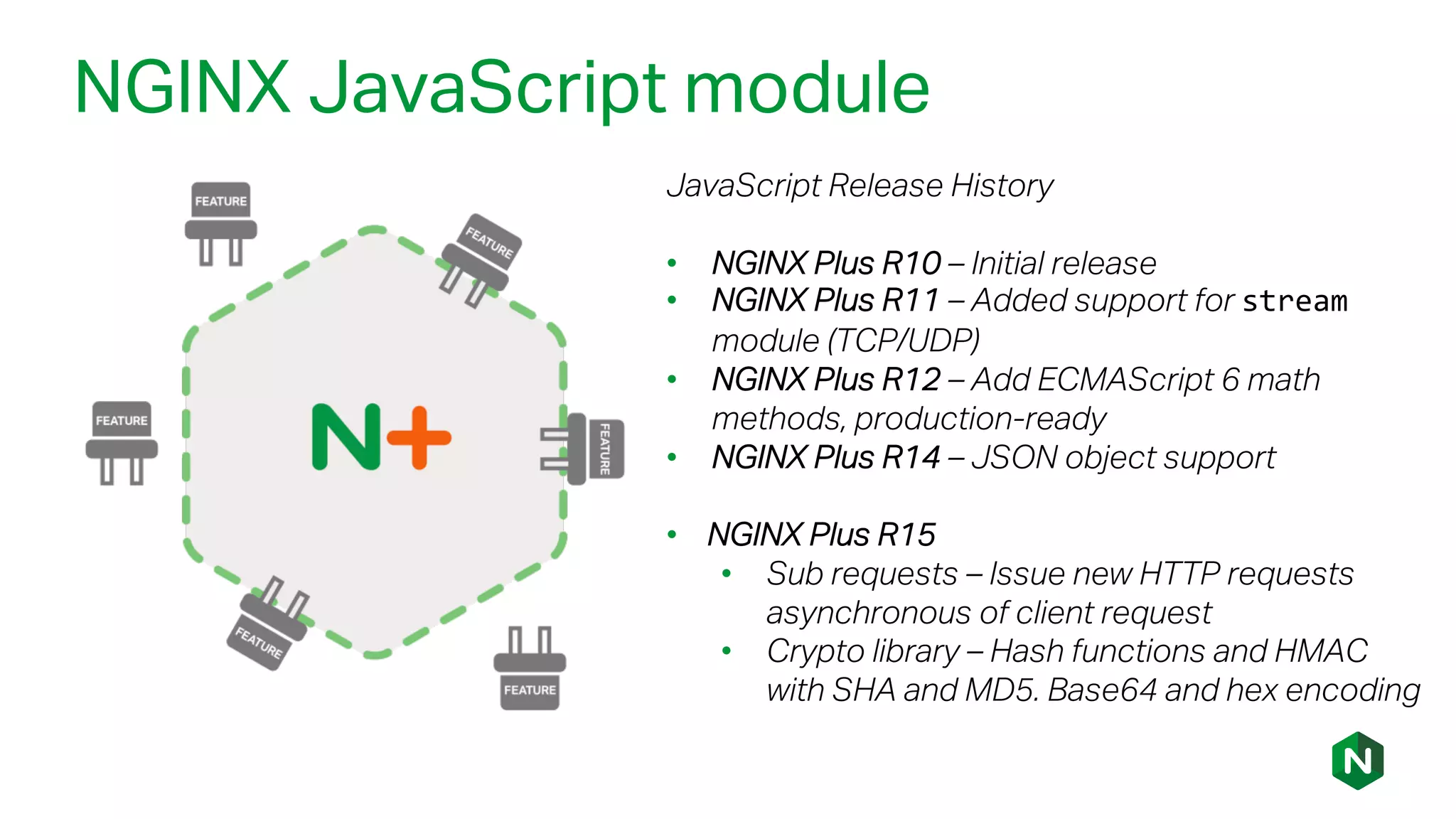
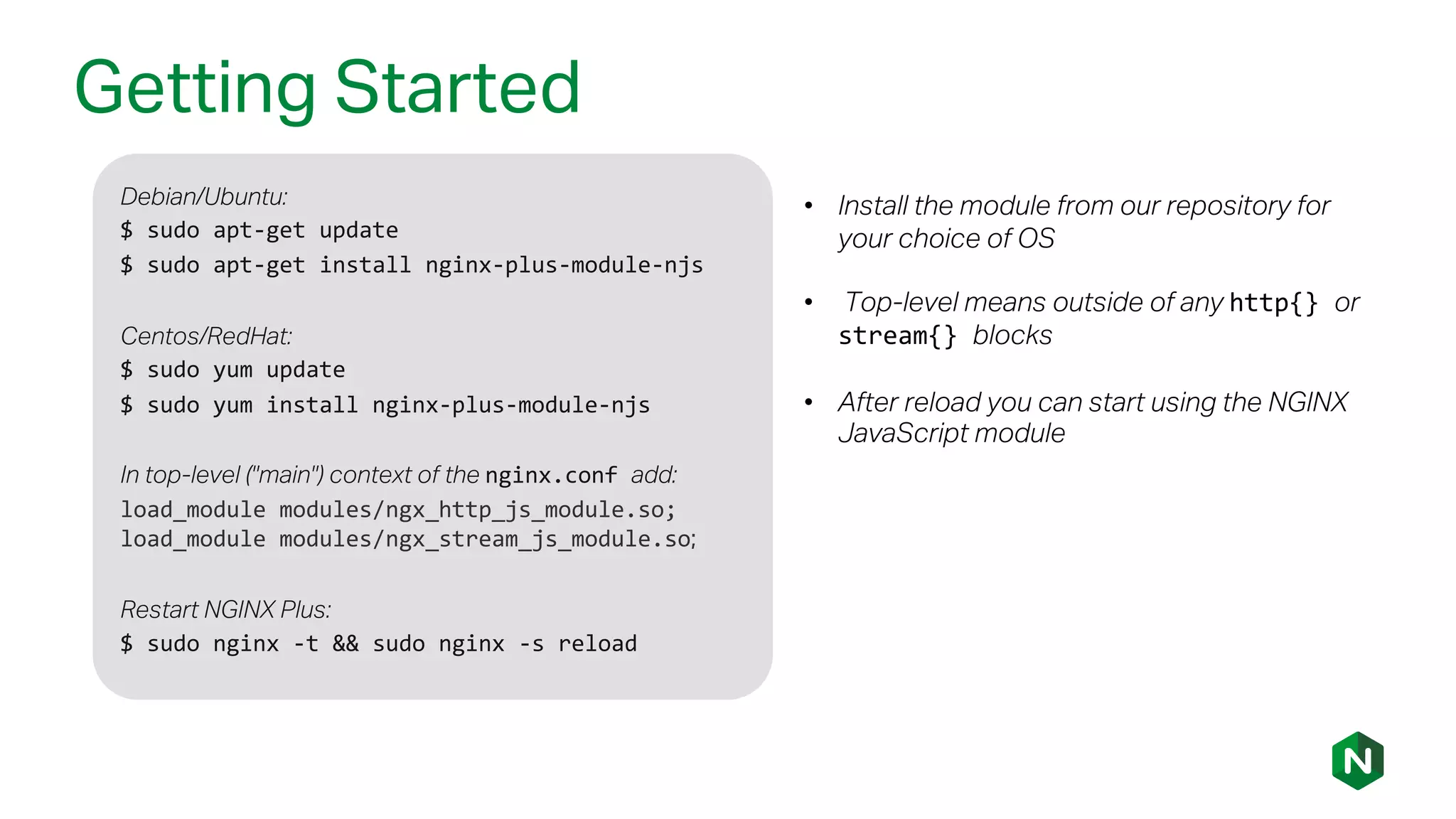
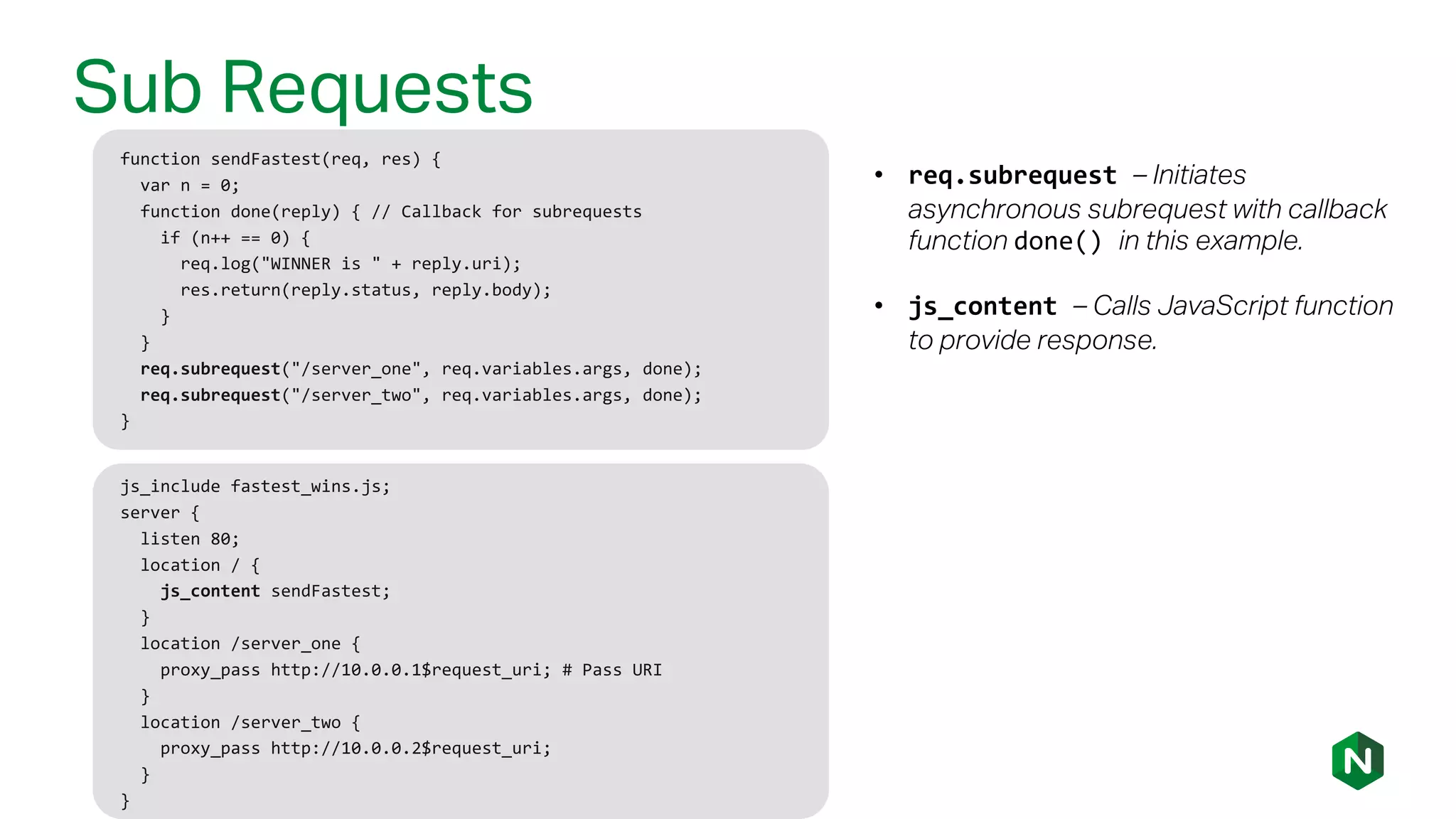
The document outlines the new features in NGINX Plus R15, including enhancements to HTTP/2, gRPC proxy support, HTTP/2 server push, improved clustering, and additions to the NGINX JavaScript module. It discusses how these updates improve performance, state sharing across clusters, and enhanced security via OpenID Connect integration. Additionally, it provides configuration examples and highlights how these updates meet the needs of a growing user base with increasing demands for efficient server management.











![Hash Functions
function signCookie(req, res) {
if (res.headers["set-cookie"].length) {
// Response includes a new cookie
var cookie_data = res.headers["set-cookie"].split(";");
var c = require('crypto’);
var h = c.createHmac('sha256').update(cookie_data[0] +
req.remoteAddress);
return "signature=" + h.digest('hex');
}
return "";
}
• c.createHmac – Calls crypto library to
provide HMAC of specified data.
• js_set – Sets variable to return value
from JavaScript function
Supported crypto library functions:
• Hash functions: MD5, SHA-1, SHA-256
• HMAC using: MD5, SHA-1, SHA-256
• Digest formats: Base64, Base64URL, hex
js_include cookie_signing.js;
js_set $signed_cookie signCookie;
server {
listen 80;
location / {
proxy_pass http://my_backend;
add_header Set-Cookie $signed_cookie;
}
}](https://image.slidesharecdn.com/whatsnewinnginxplusr15emea-180523170354/75/What-s-New-in-NGINX-Plus-R15-EMEA-35-2048.jpg)