1. The document introduces OAuth and defines key terms like resource owner, client, resource server, and authorization server.
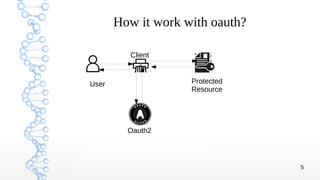
2. It explains how OAuth works, with the user granting access to a client which can then access protected resources from a resource server, compared to pre-OAuth where credentials would need to be shared.
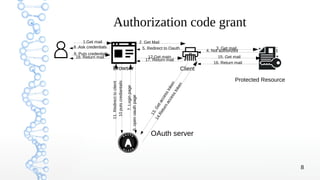
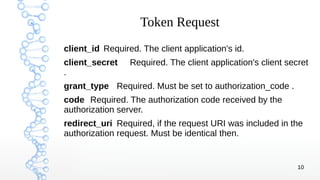
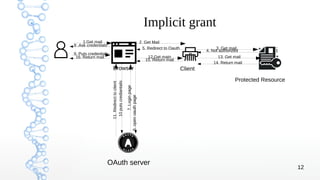
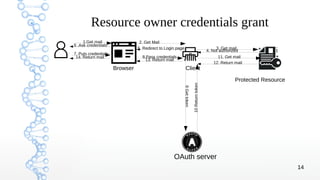
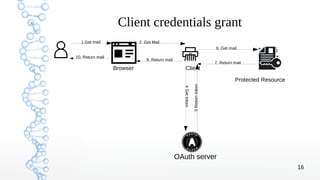
3. The different OAuth grant types are covered, including authorization code, implicit, resource owner credentials, client credentials, and refresh token grants with examples of the authorization code and implicit flows.