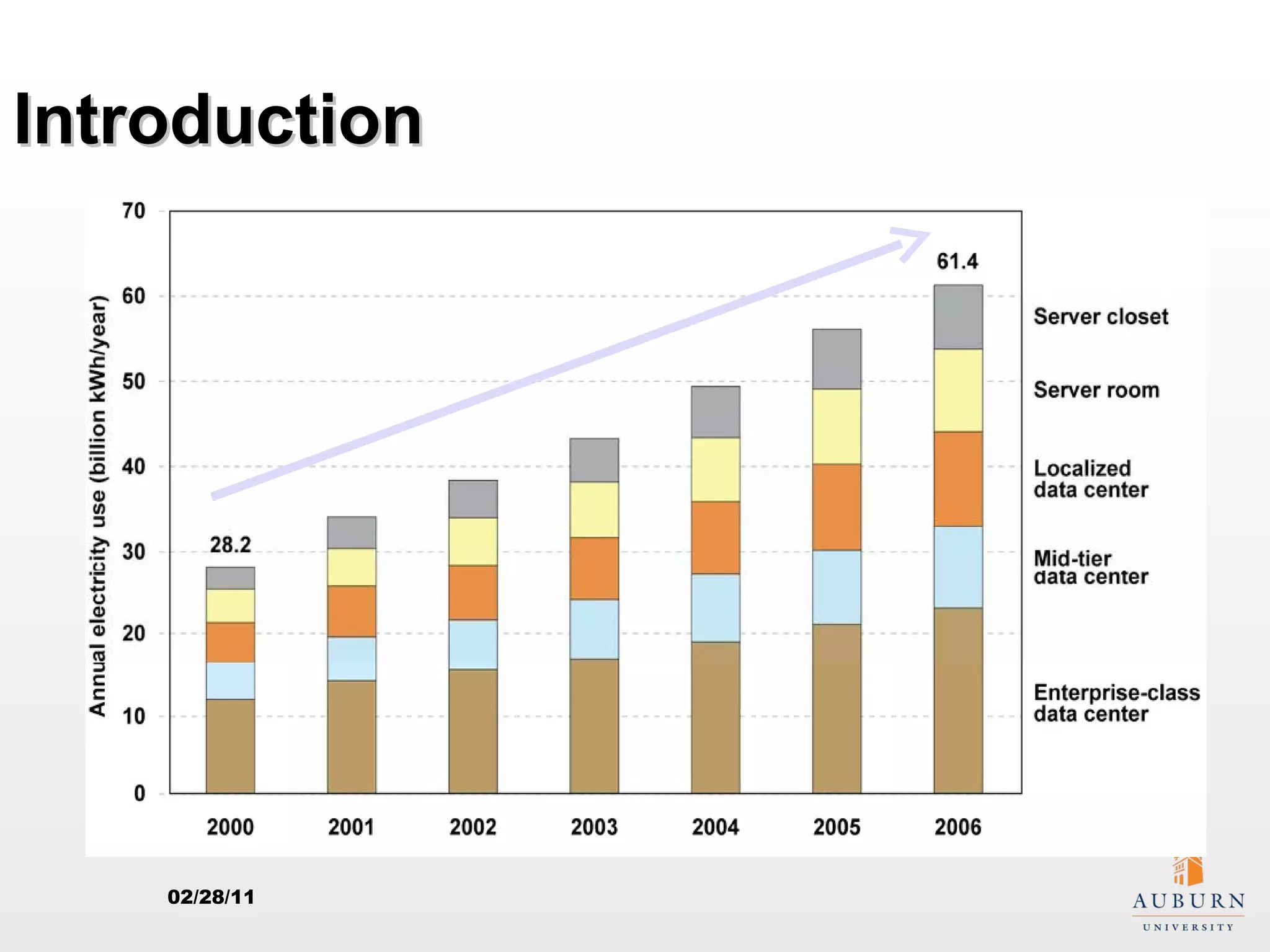
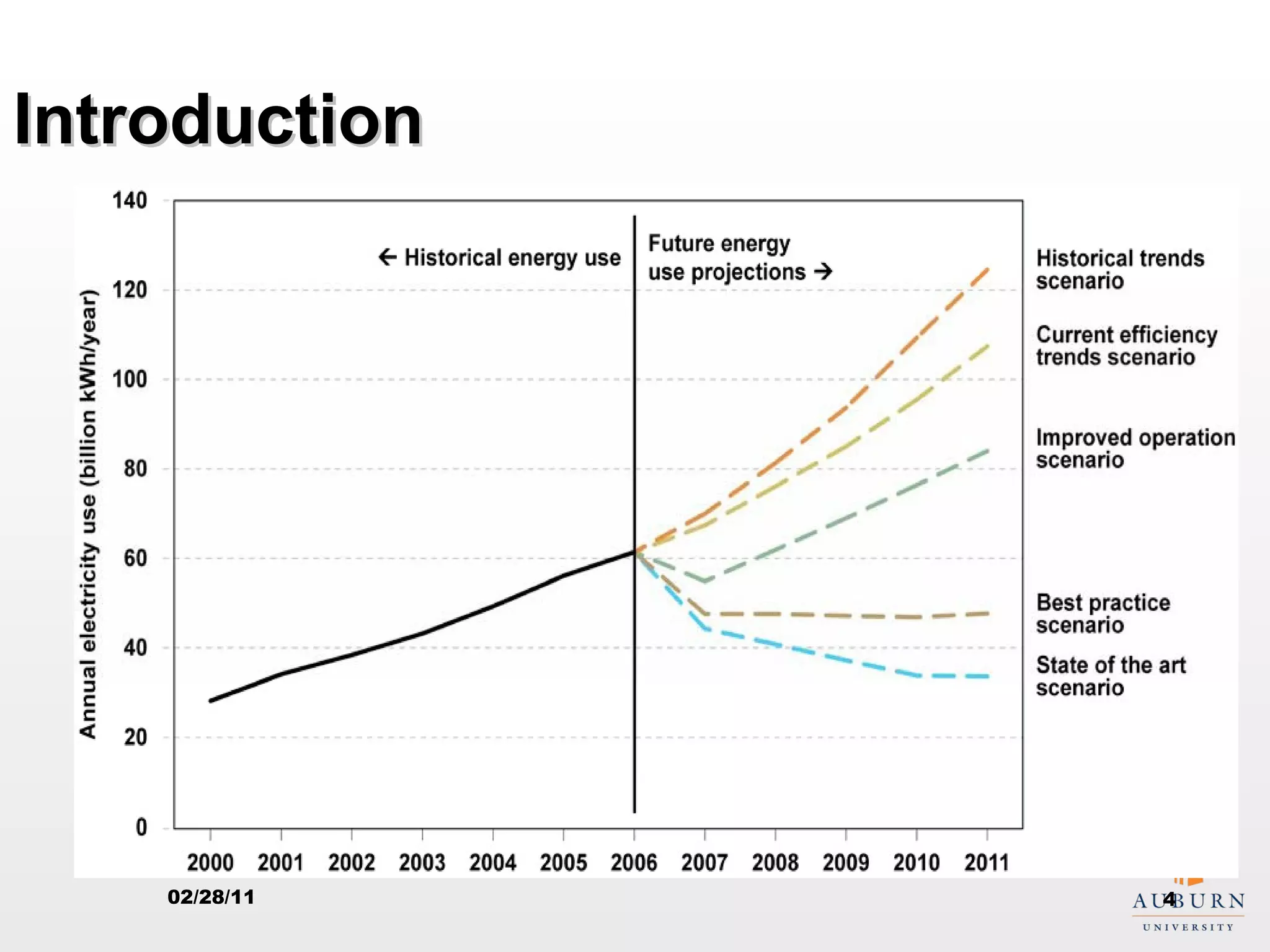
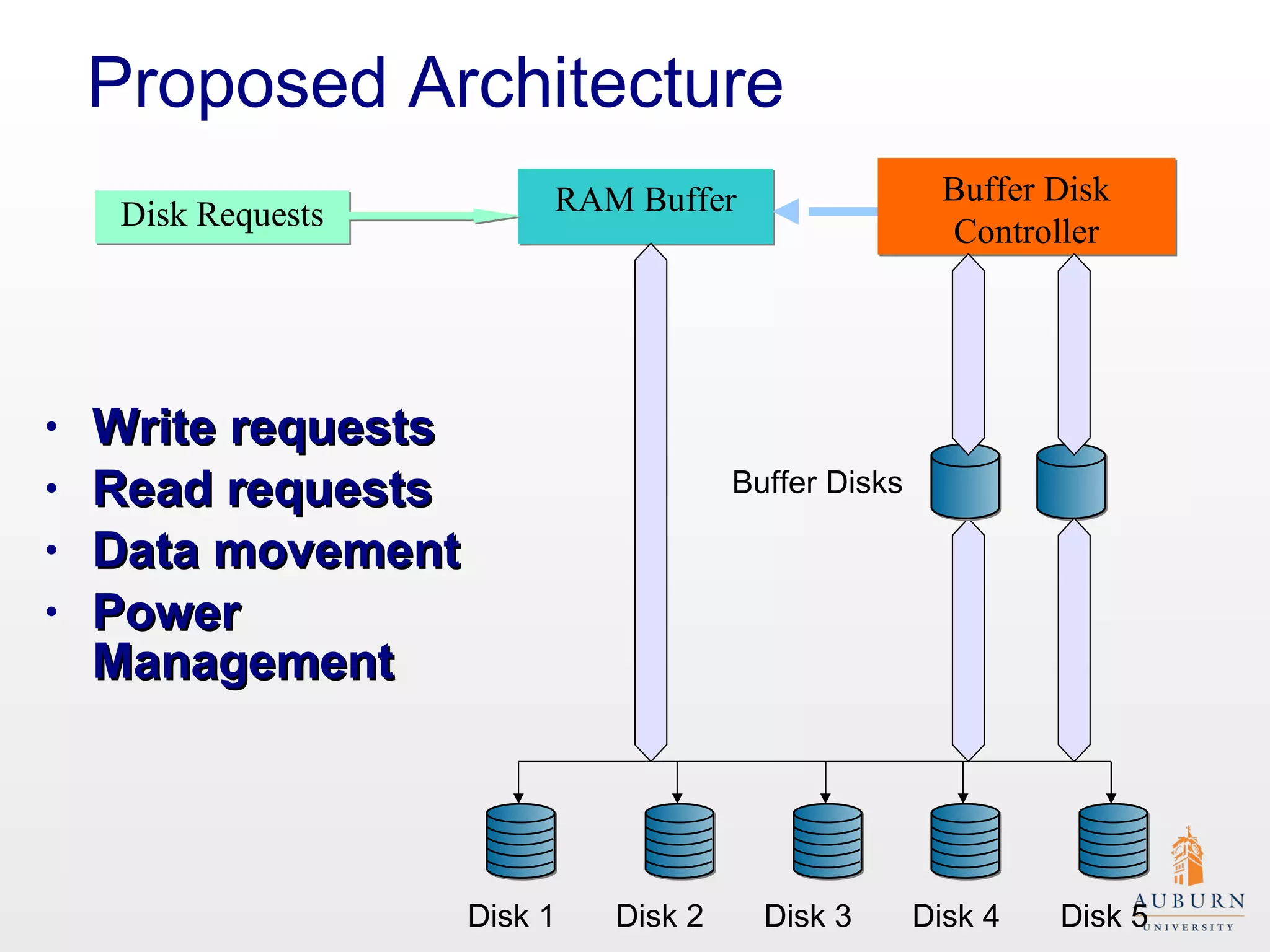
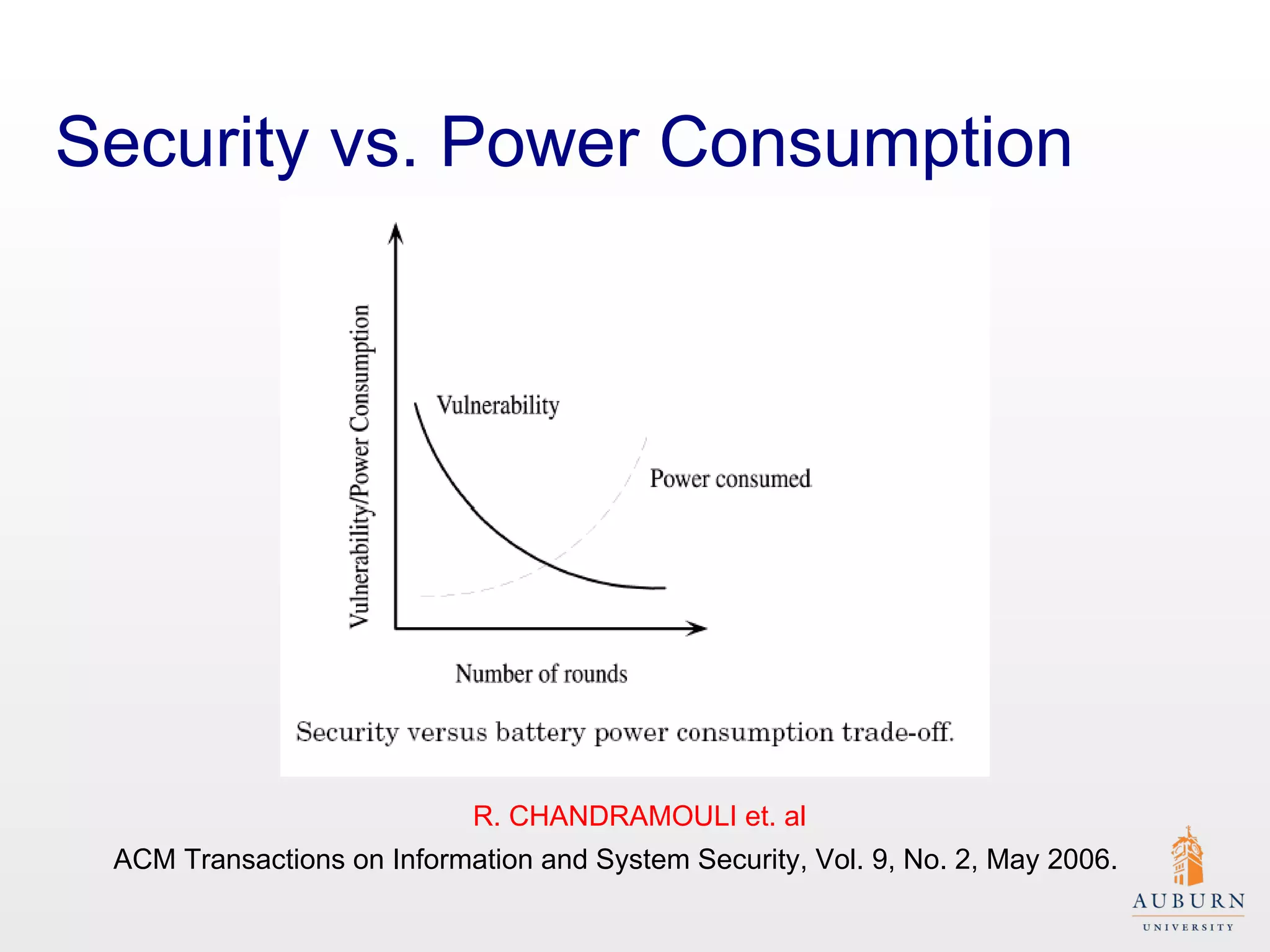
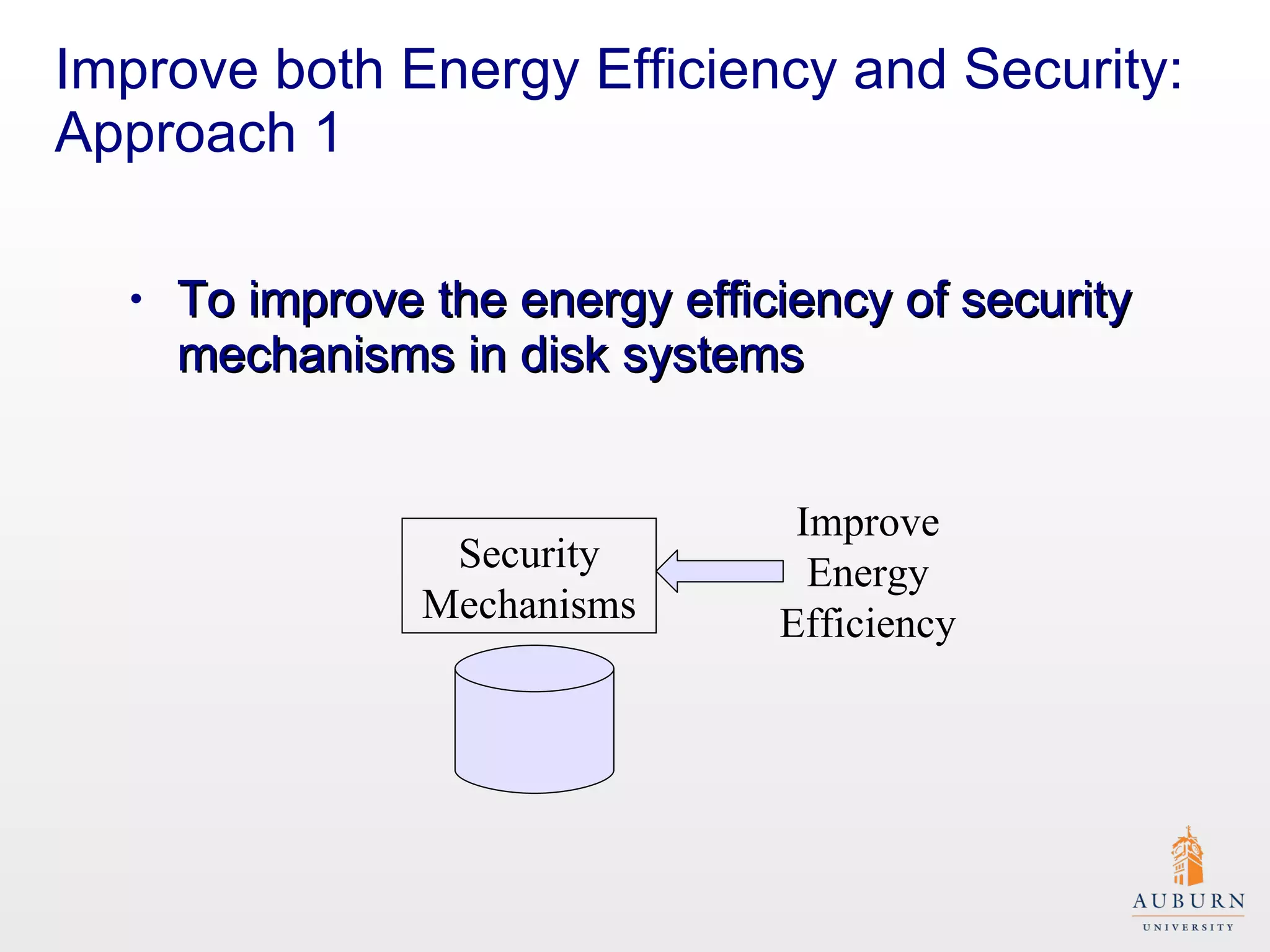
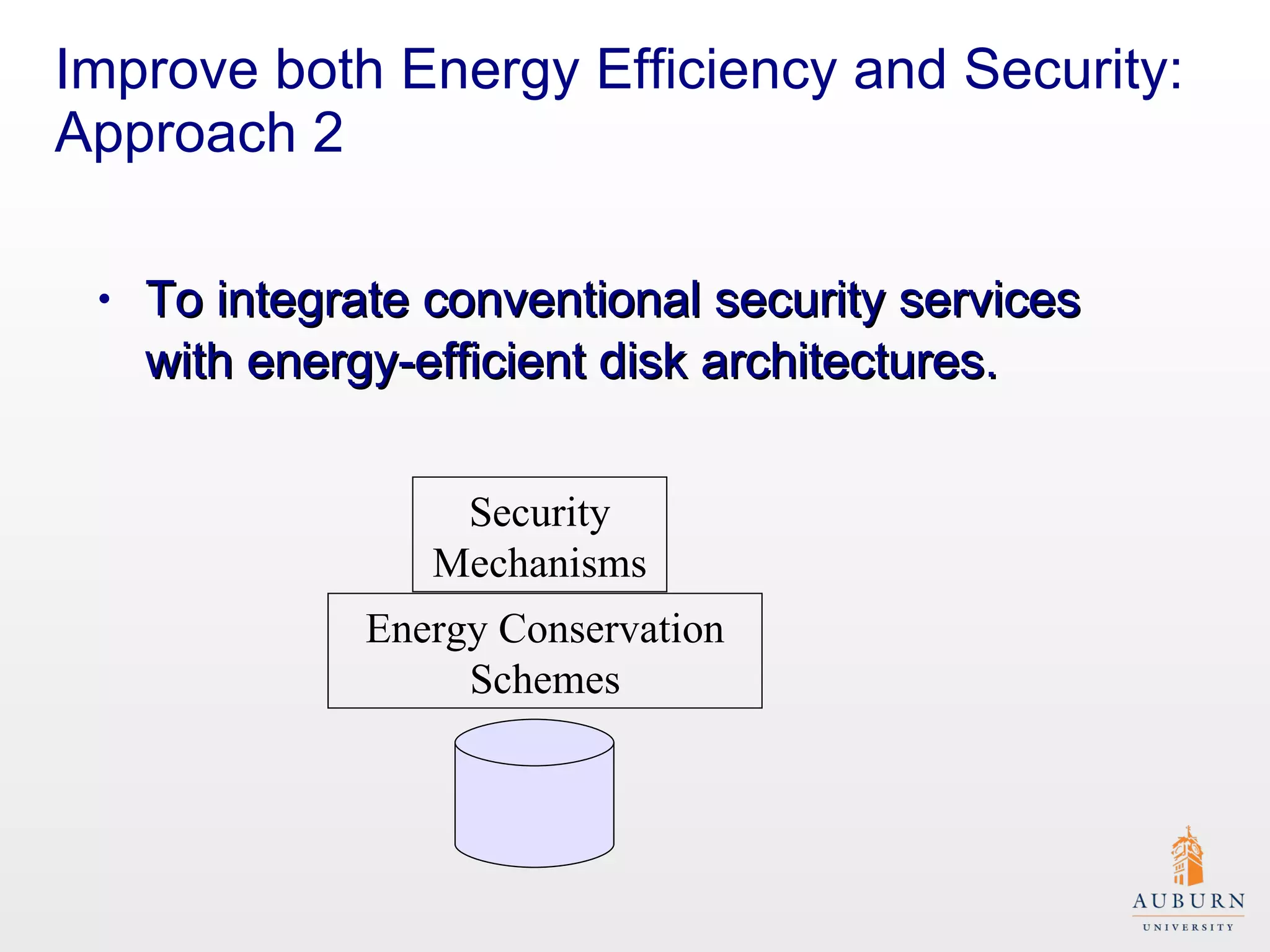
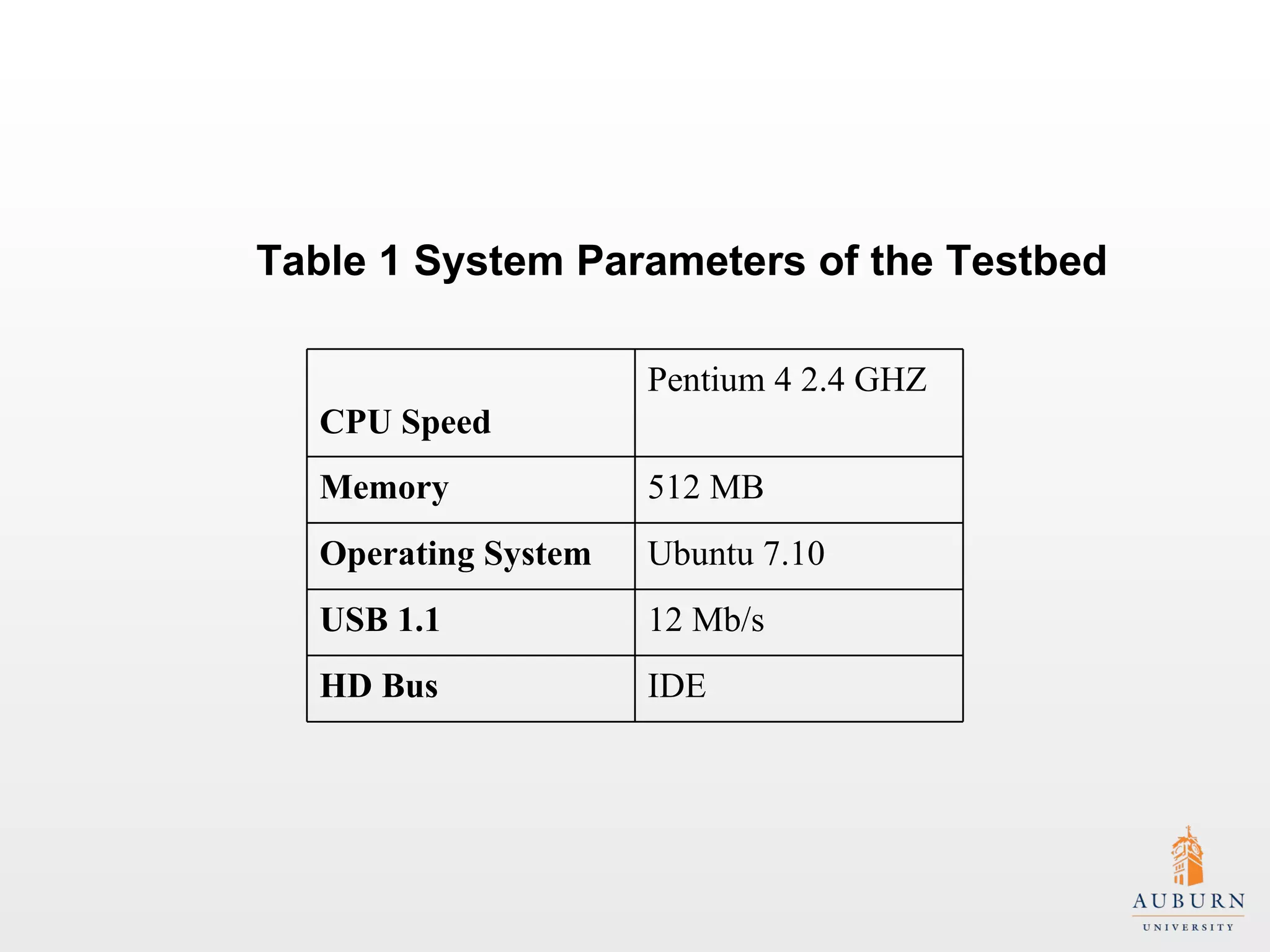
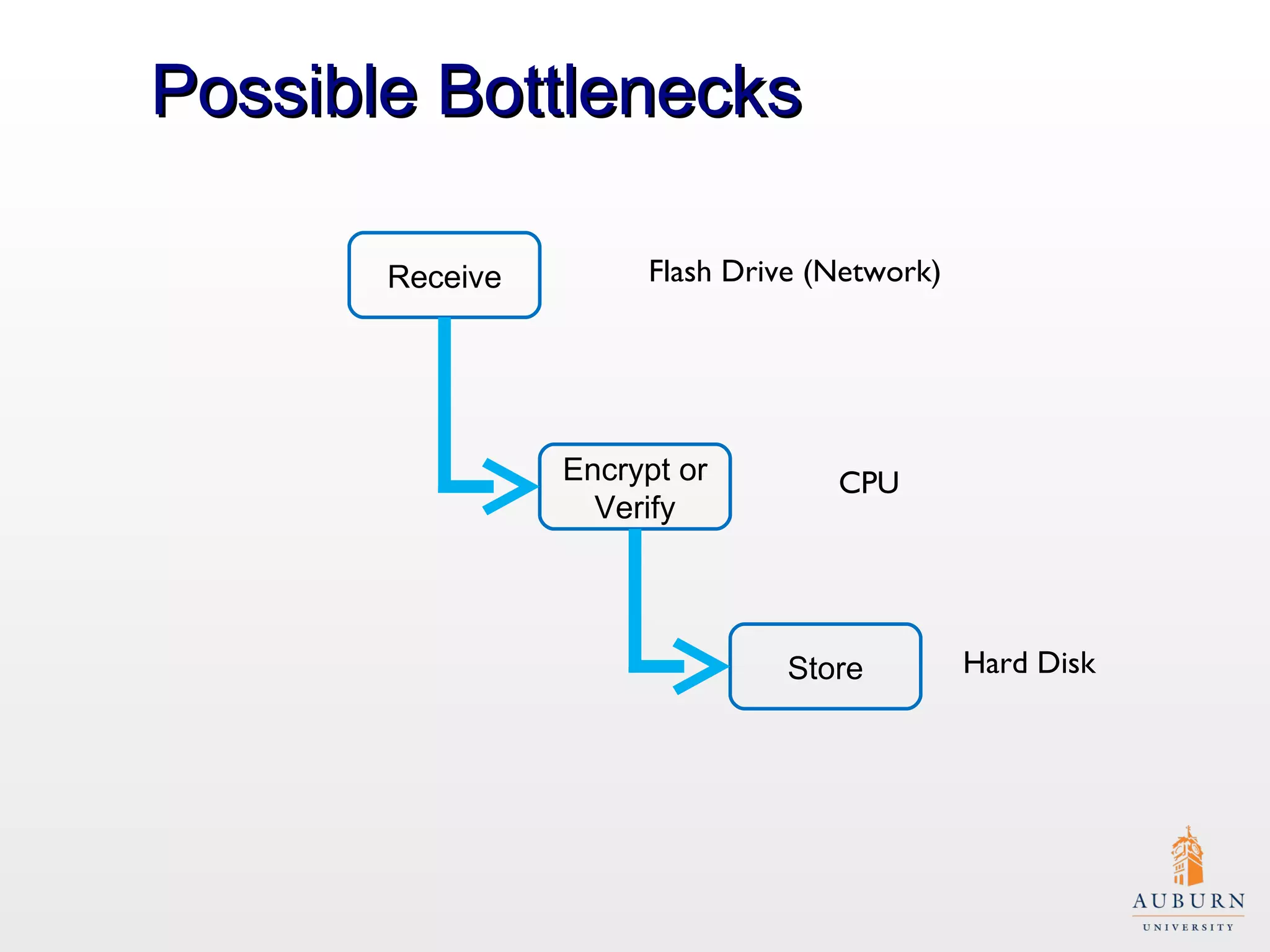
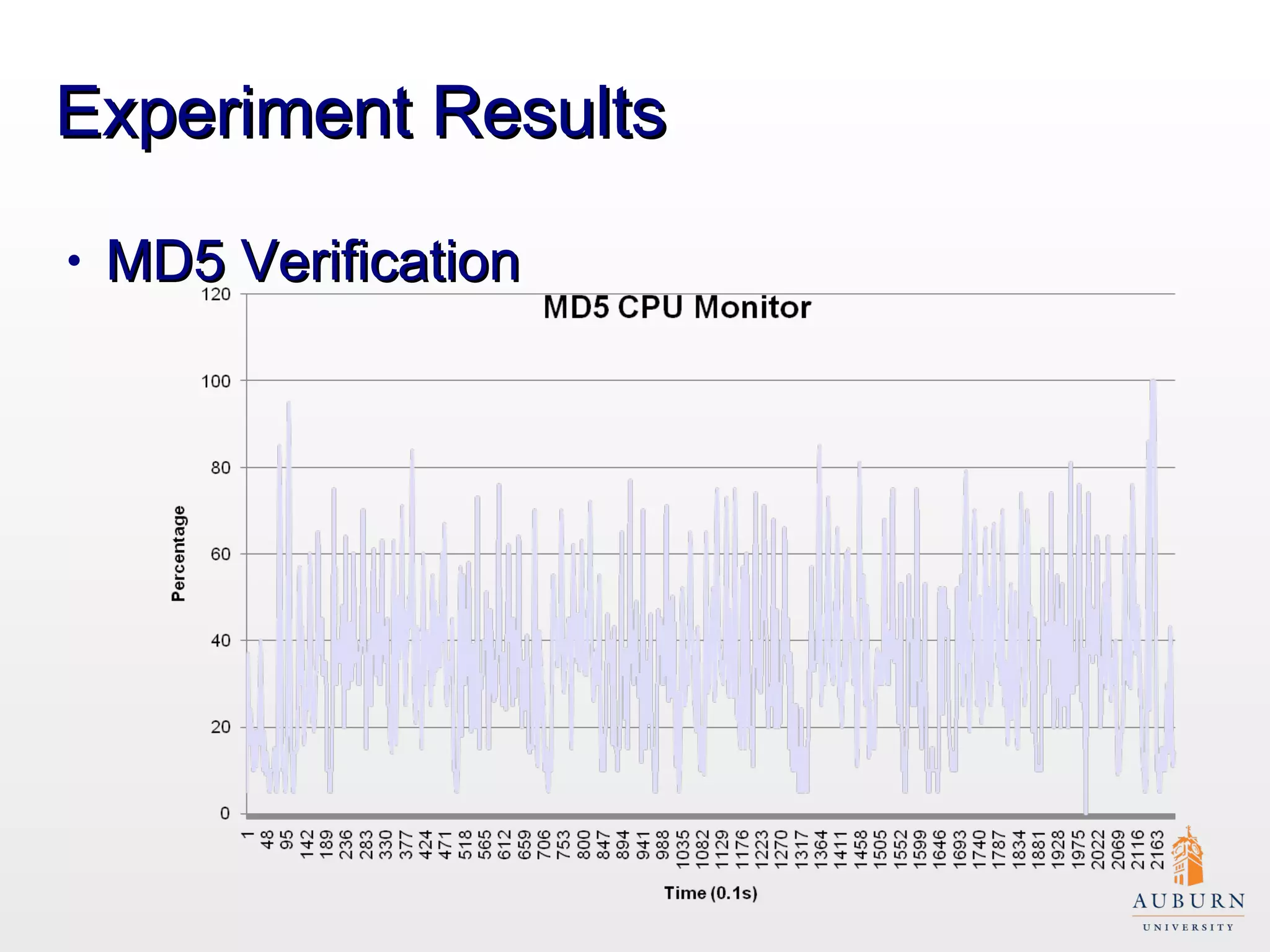
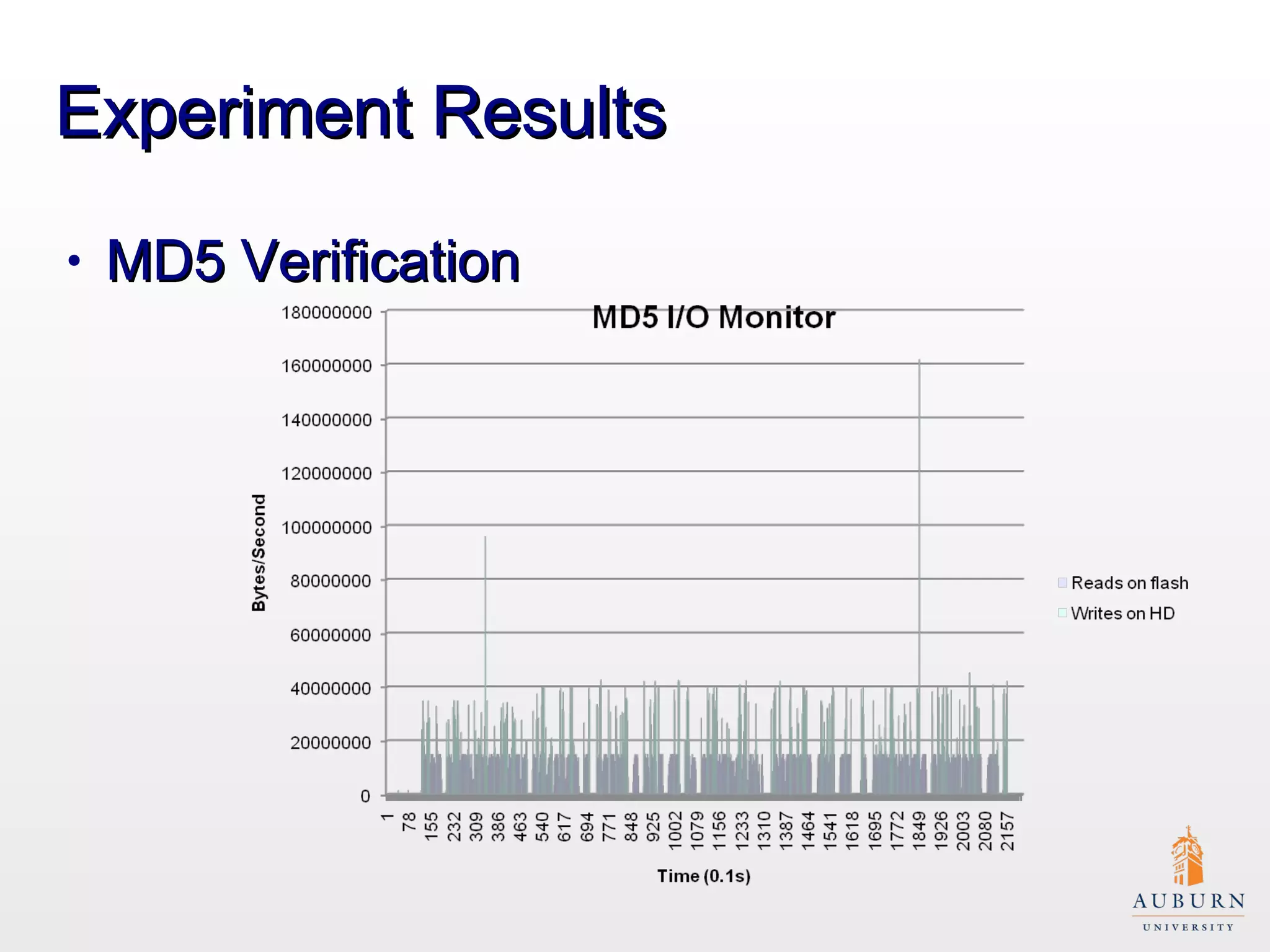
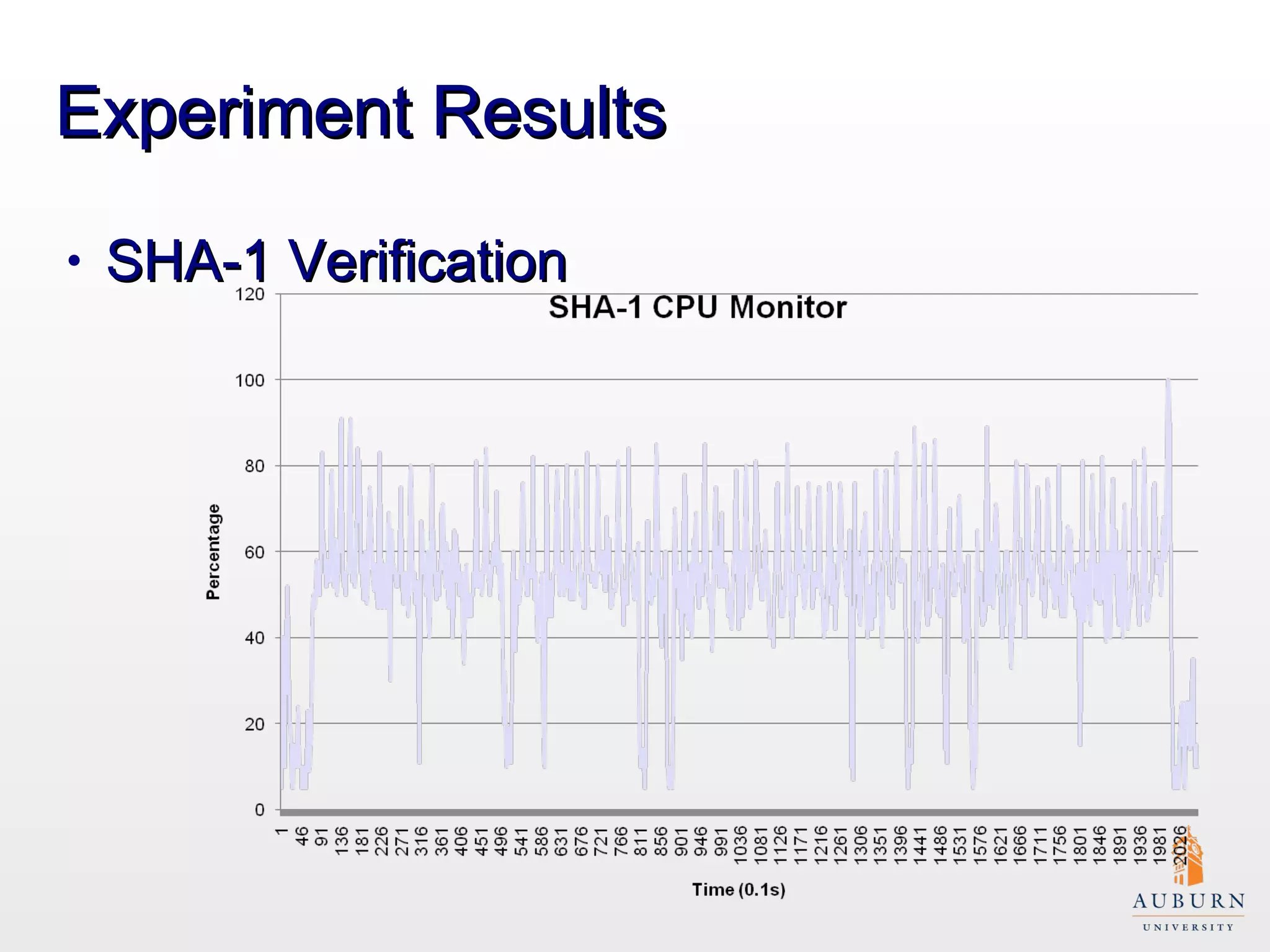
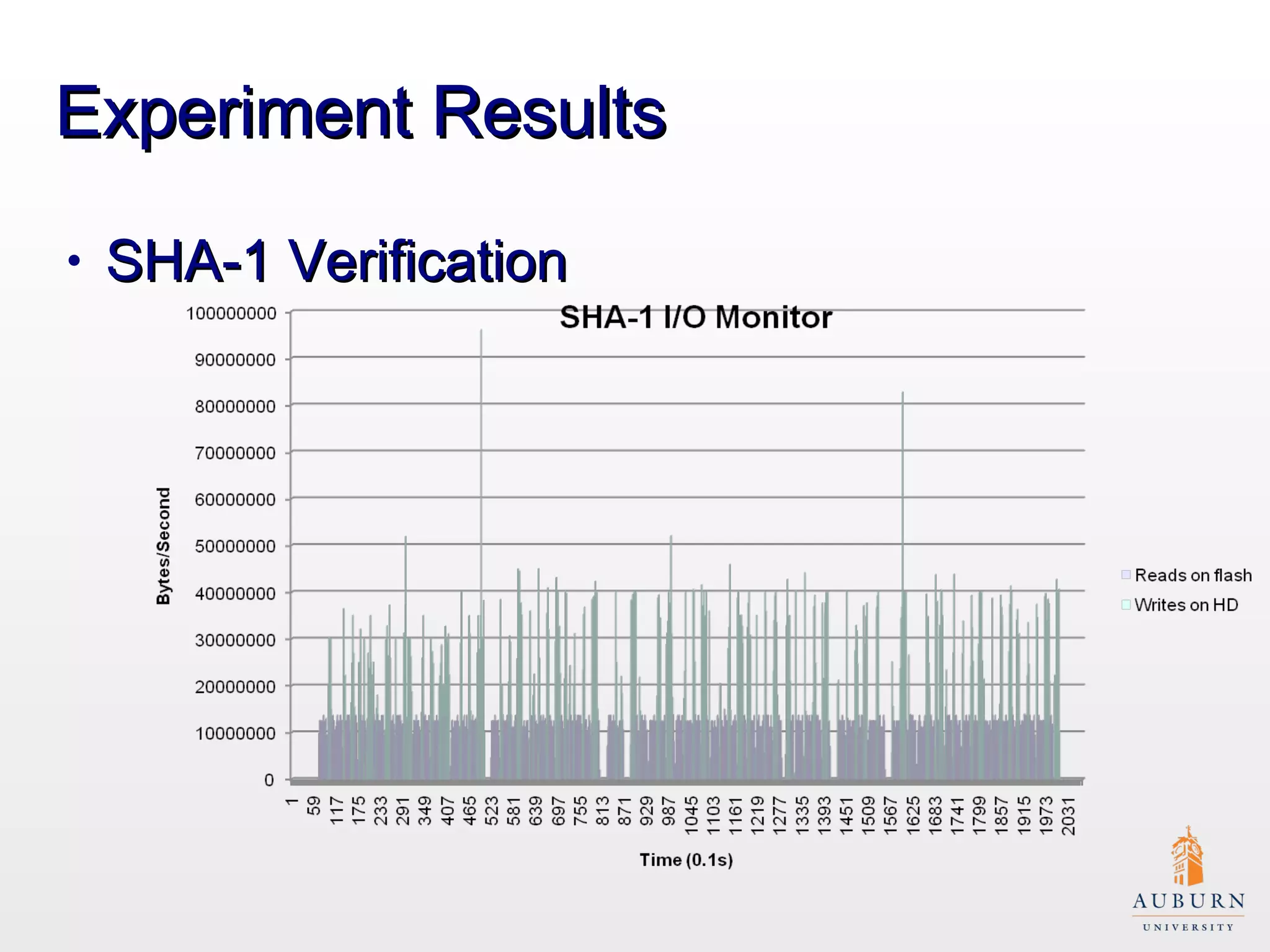
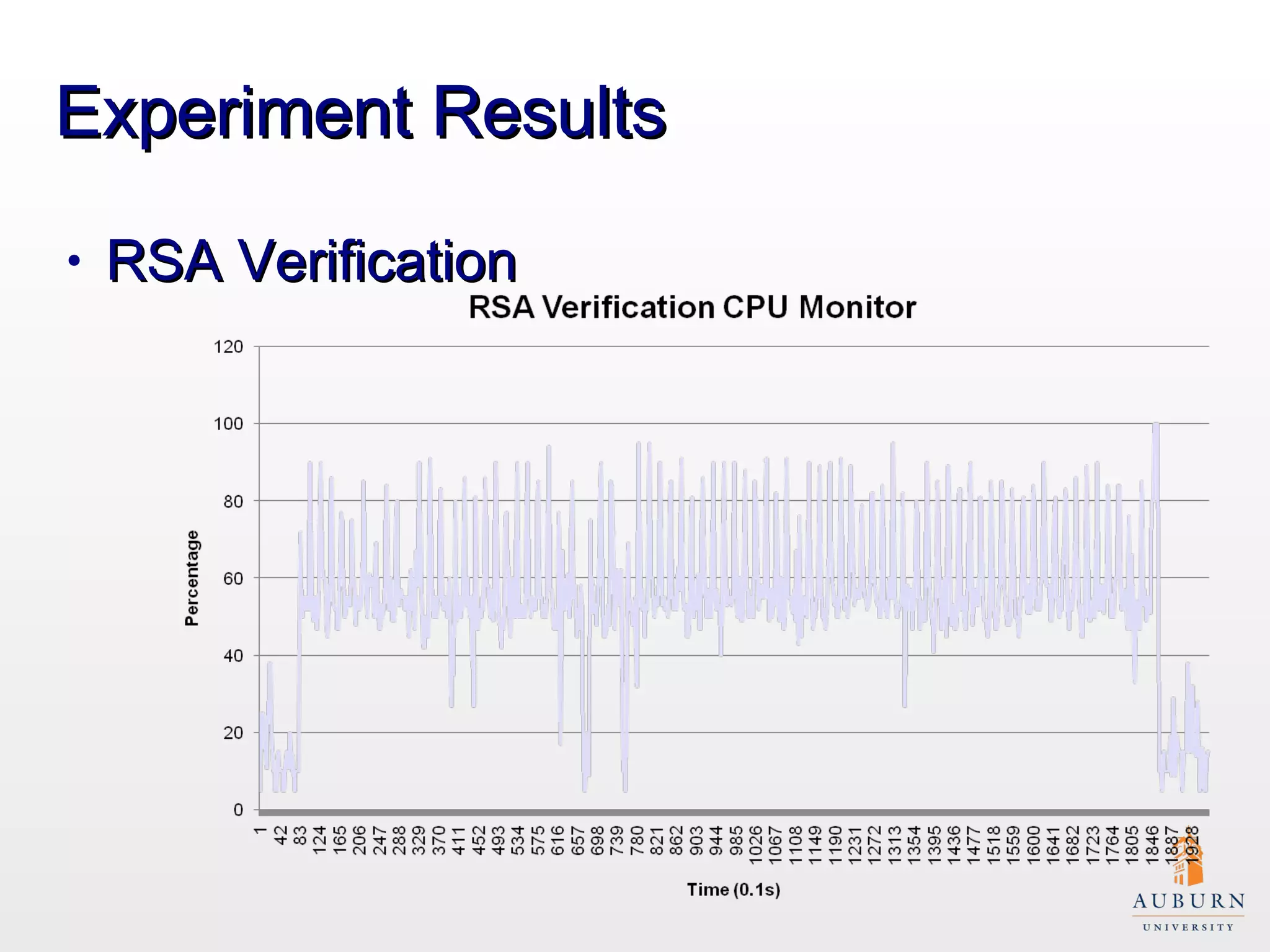
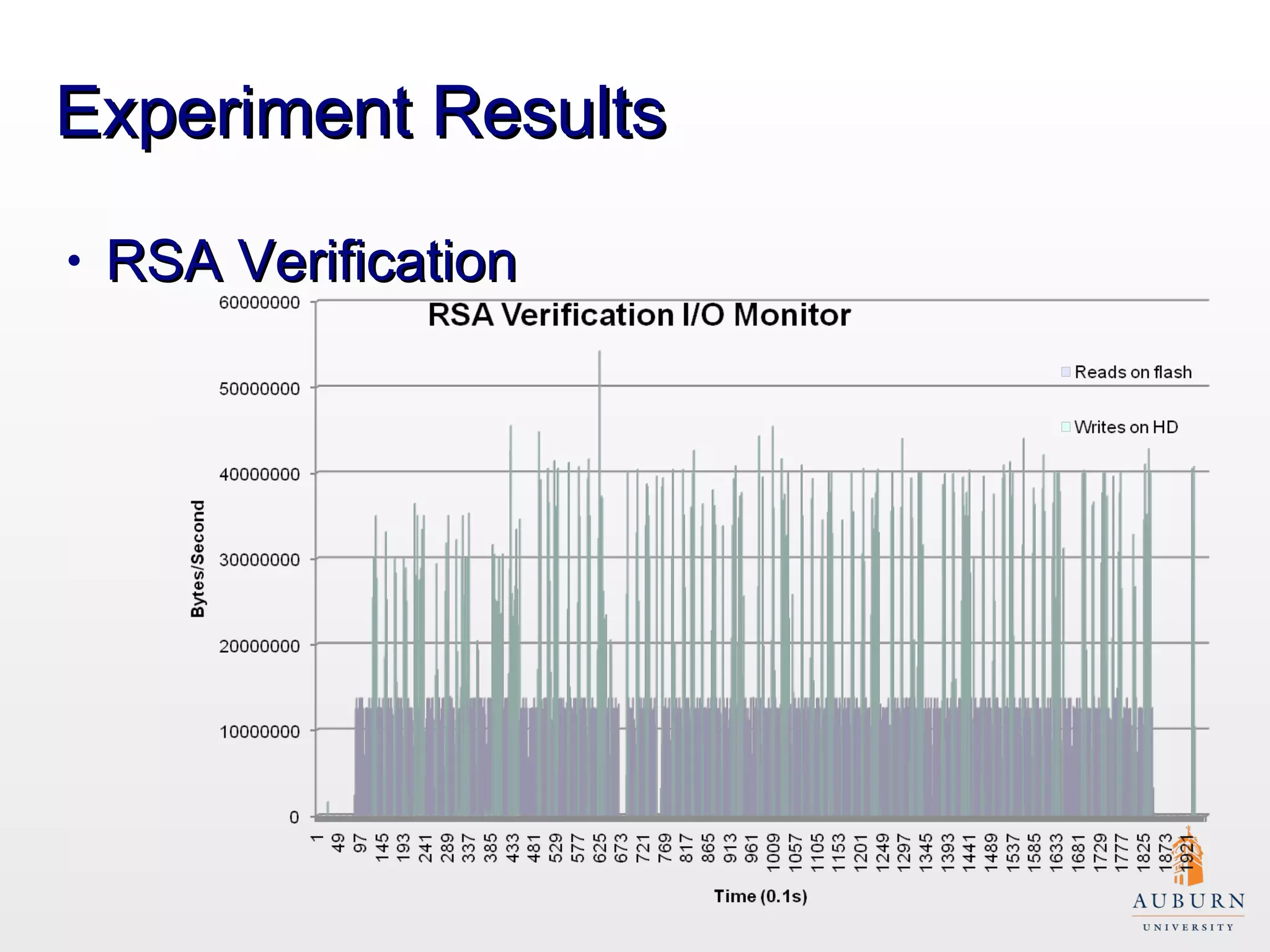
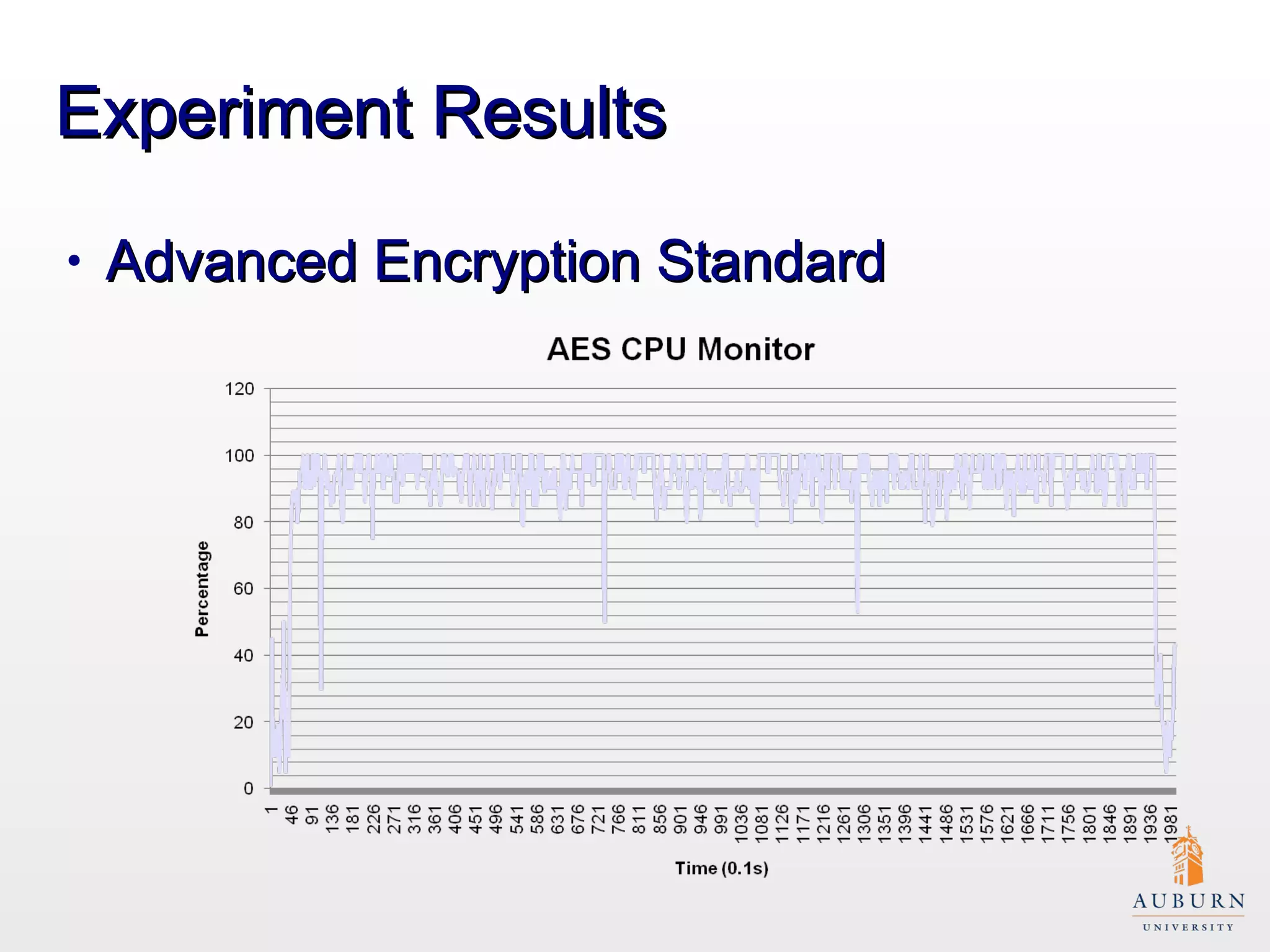
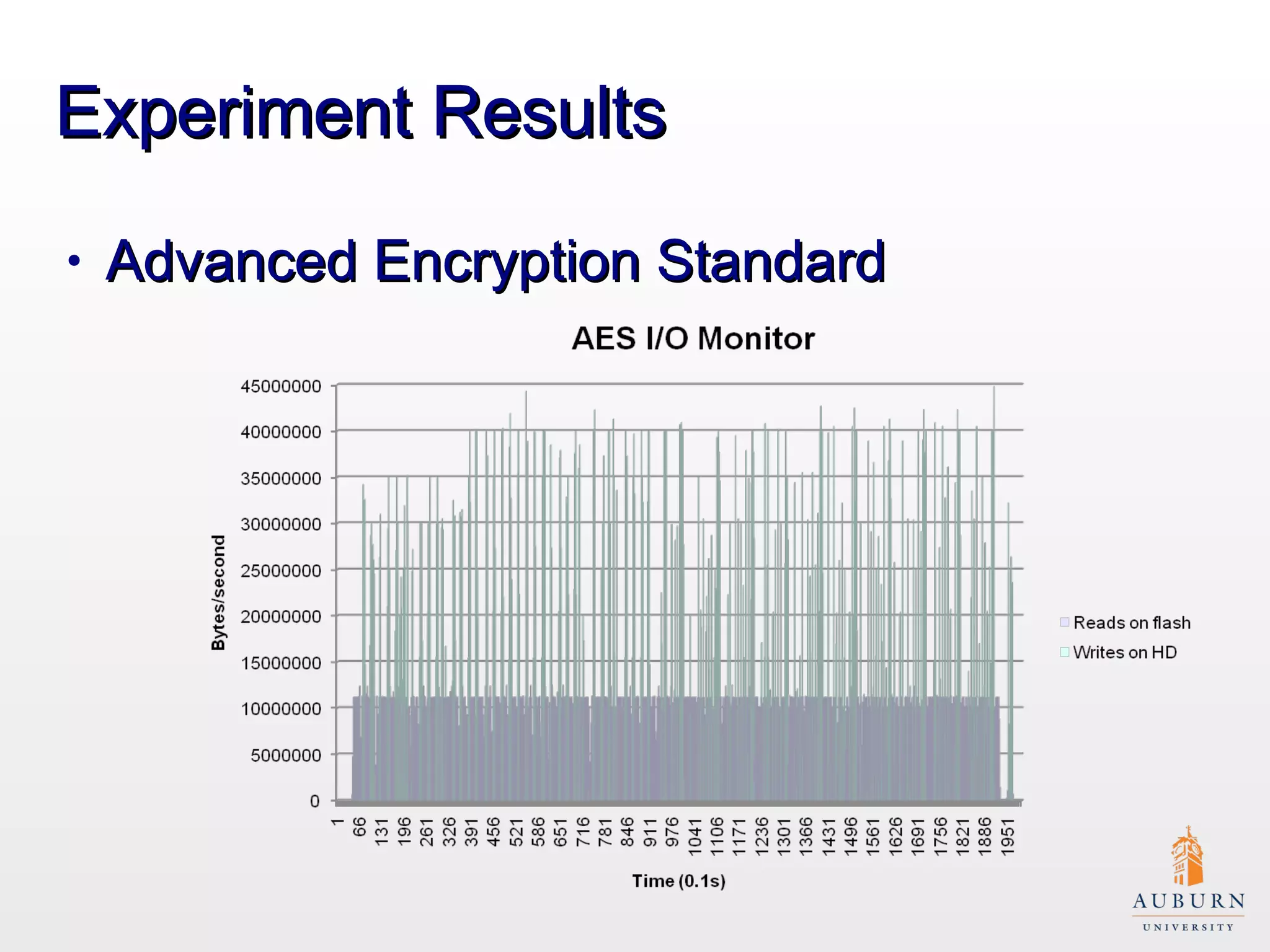
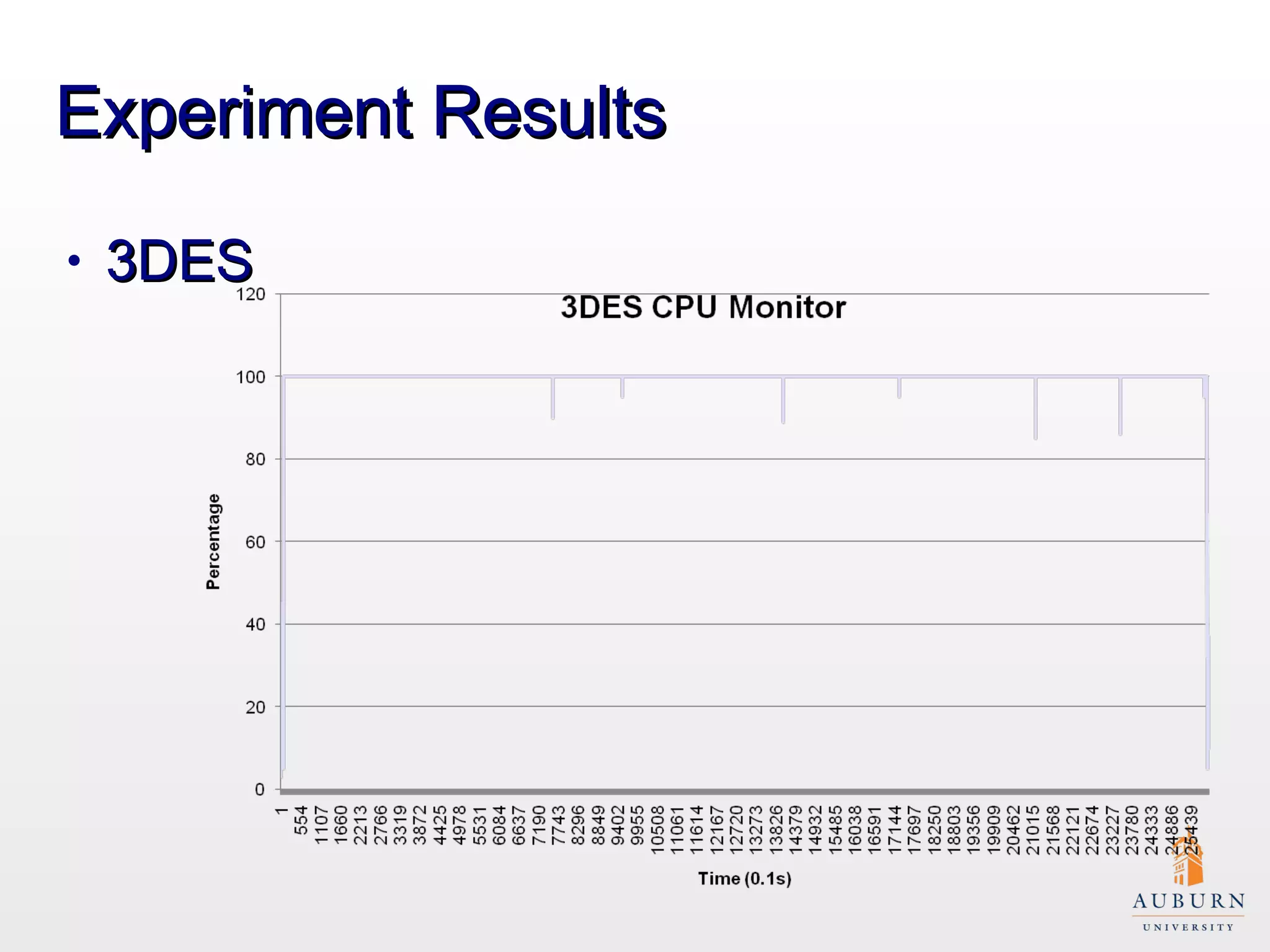
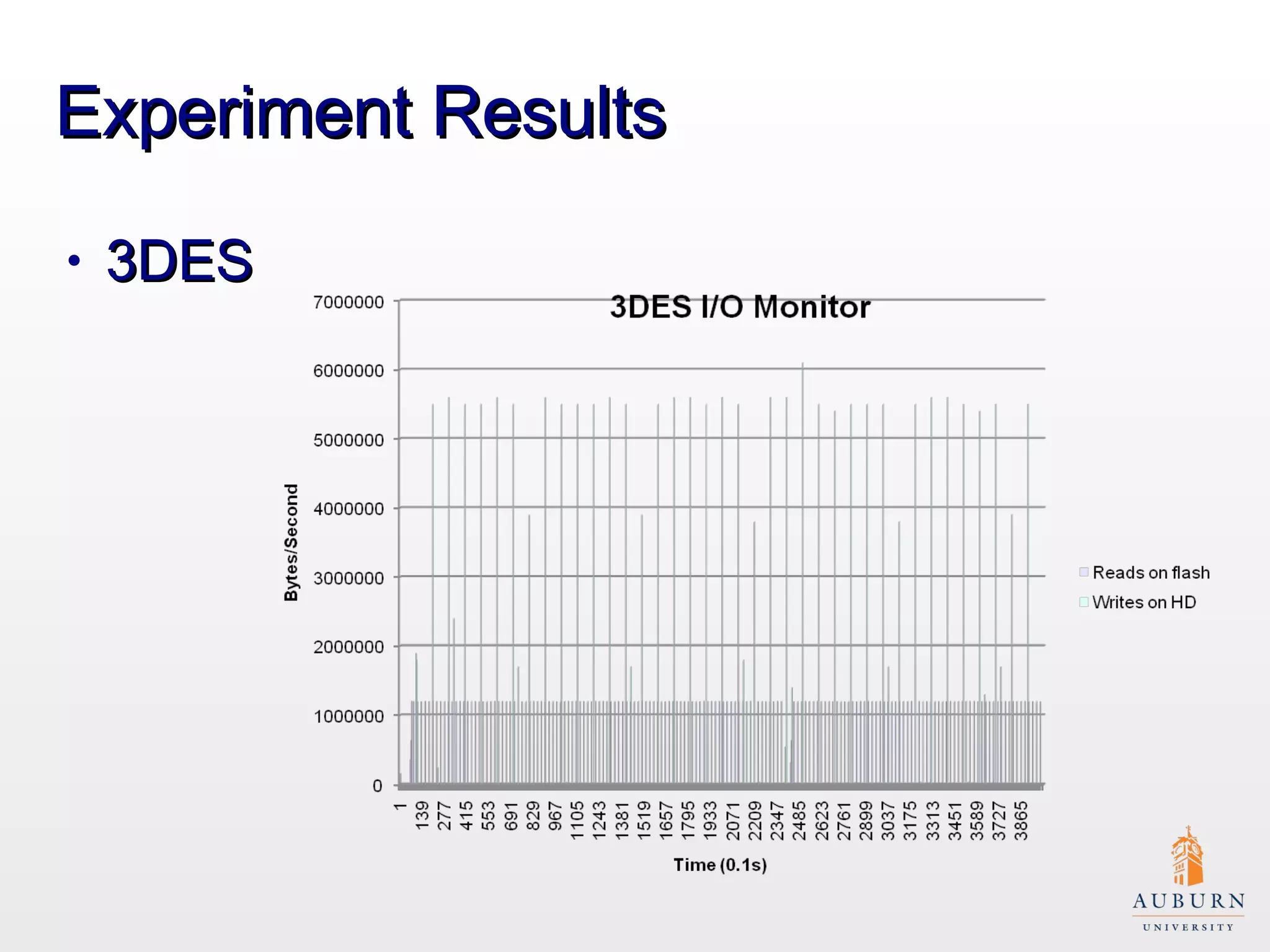
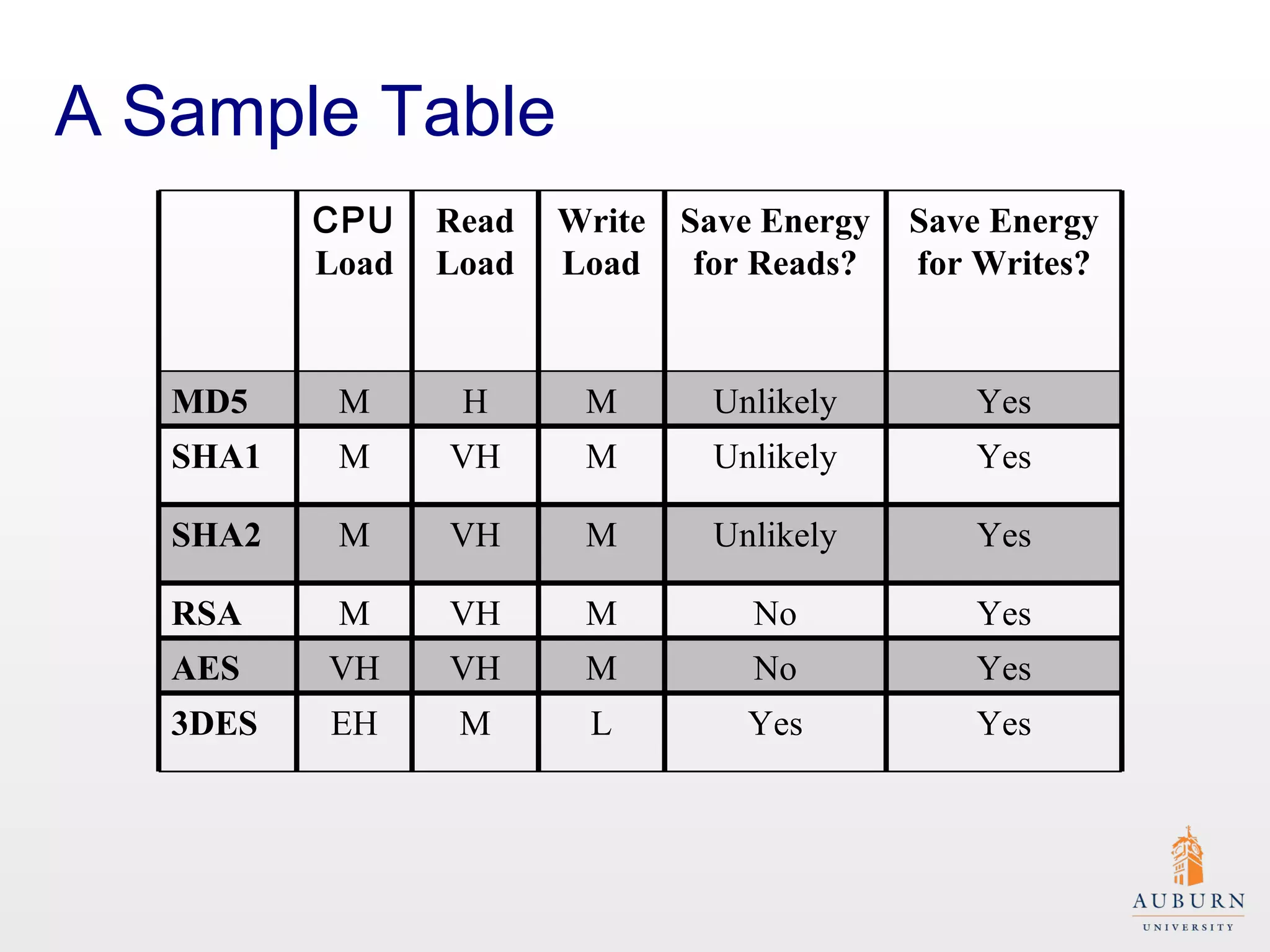
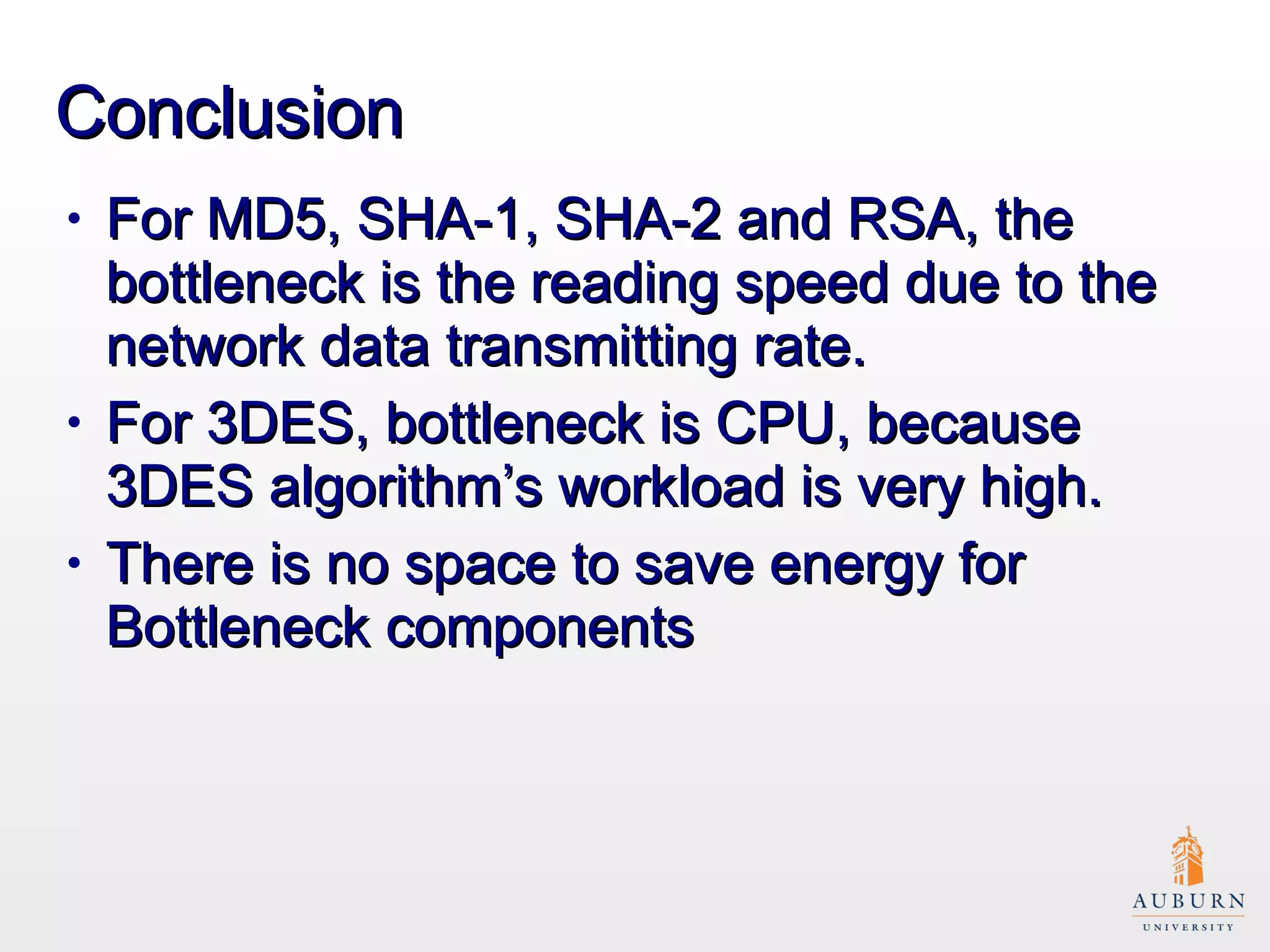
This document presents research on improving the energy efficiency of secure disk systems without altering existing security mechanisms. The study explores various approaches to enhance energy efficiency while implementing various encryption algorithms, highlighting bottlenecks in CPU and network data transmission rates. The authors also note limitations in their testbed environment and the representativeness of workloads analyzed.
![Can We Improve Energy Efficiency of Secure Disk Systems without Modifying Security Mechanisms? Xiaojun Ruan, Adam Manzanares , Shu Yin and Xiao Qin Auburn University http://www.eng.auburn.edu/~xqin [email_address]](https://image.slidesharecdn.com/improveenergyefficiencyofsecuredisksystems-nas09-110228161840-phpapp01/75/Improve-energy-efficiency-of-secure-disk-systems-nas09-1-2048.jpg)