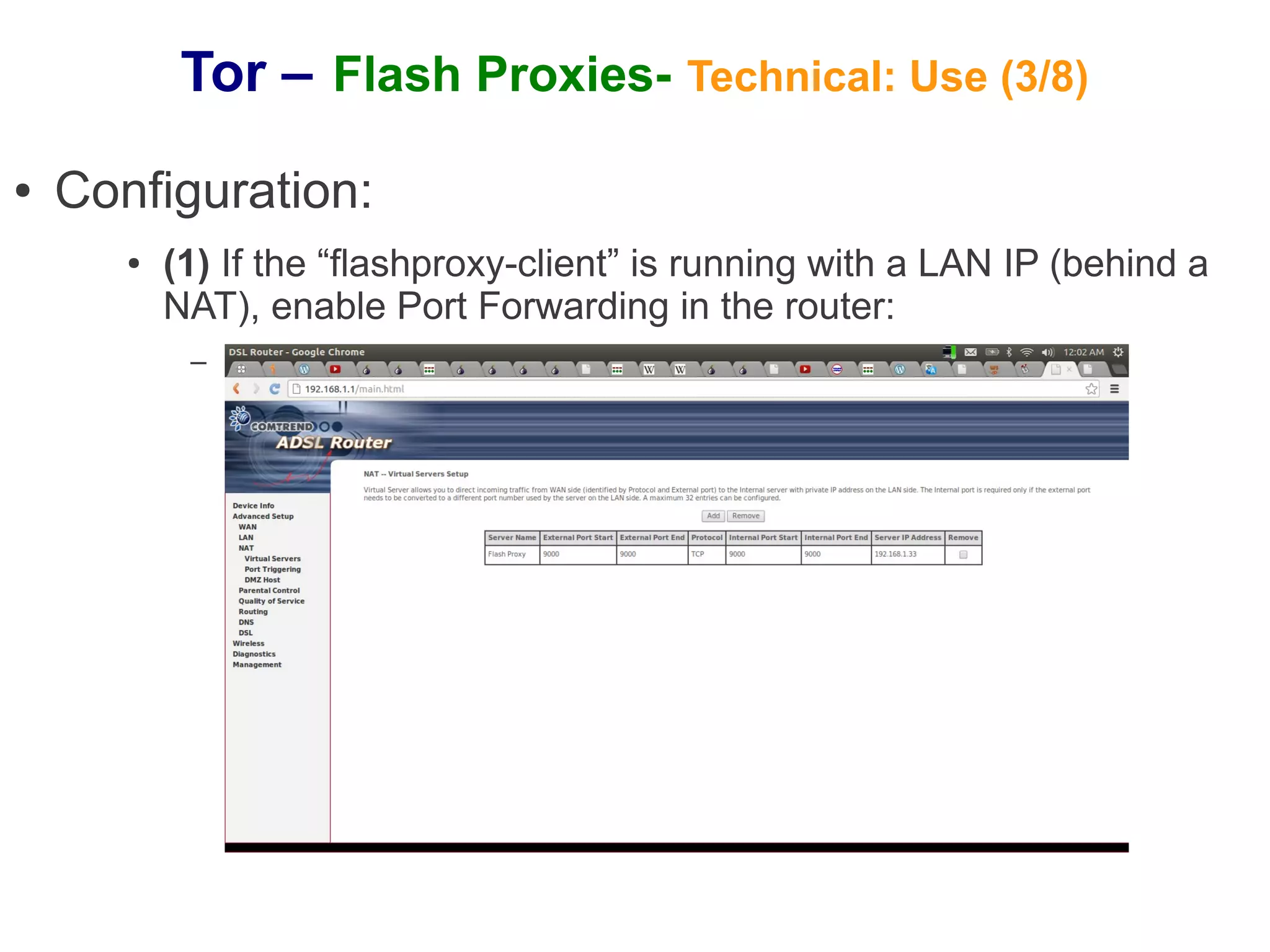
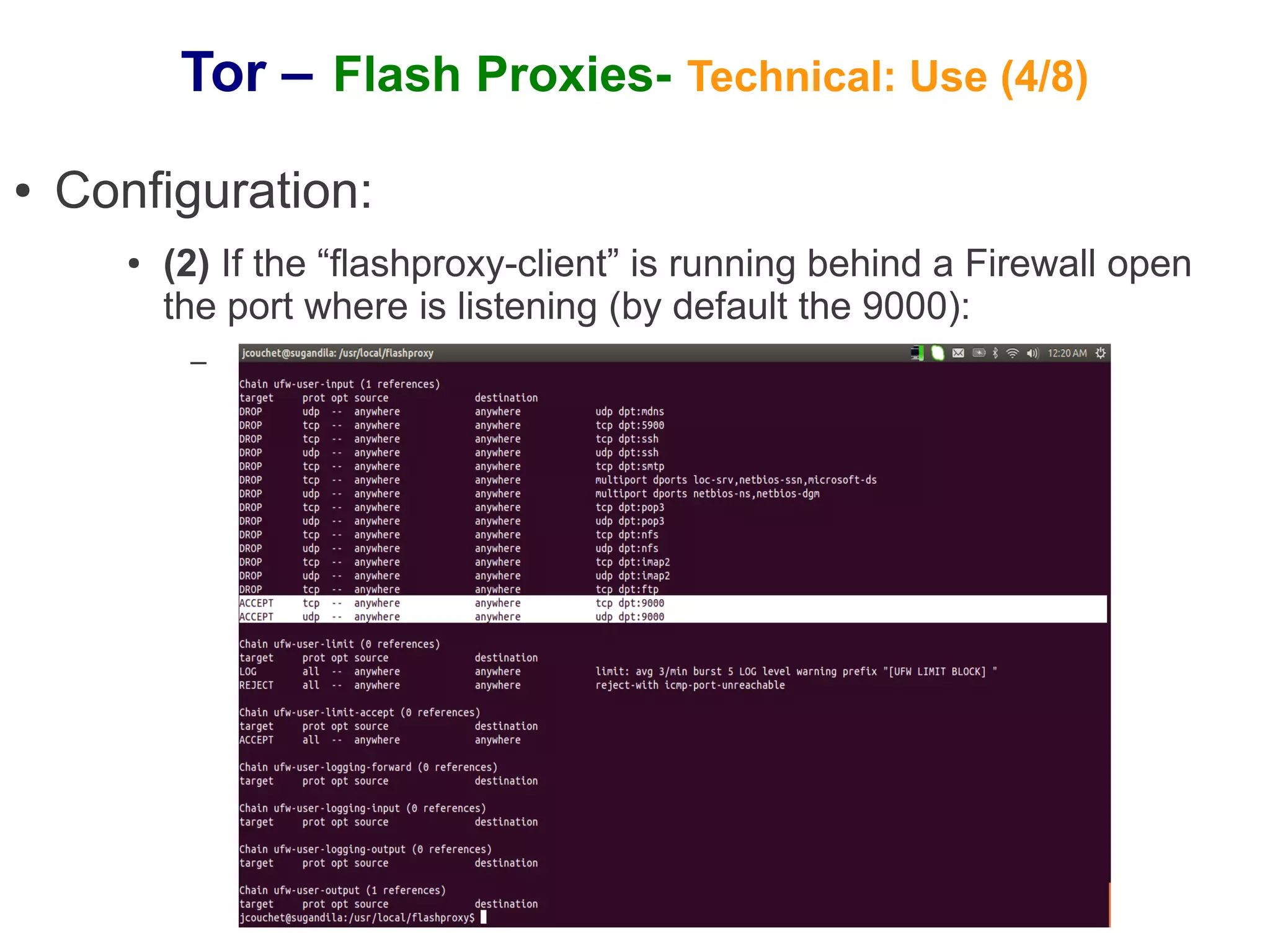
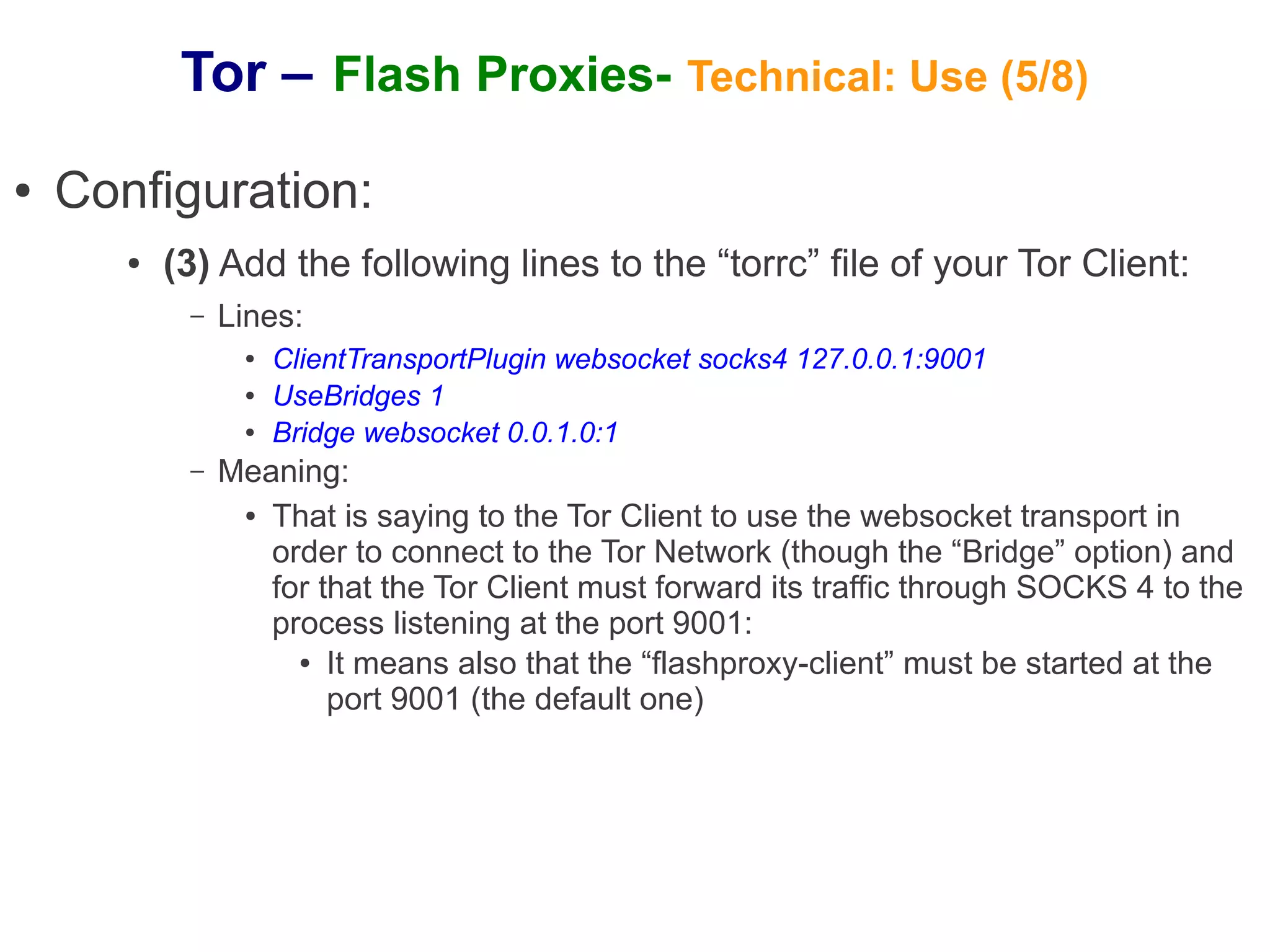
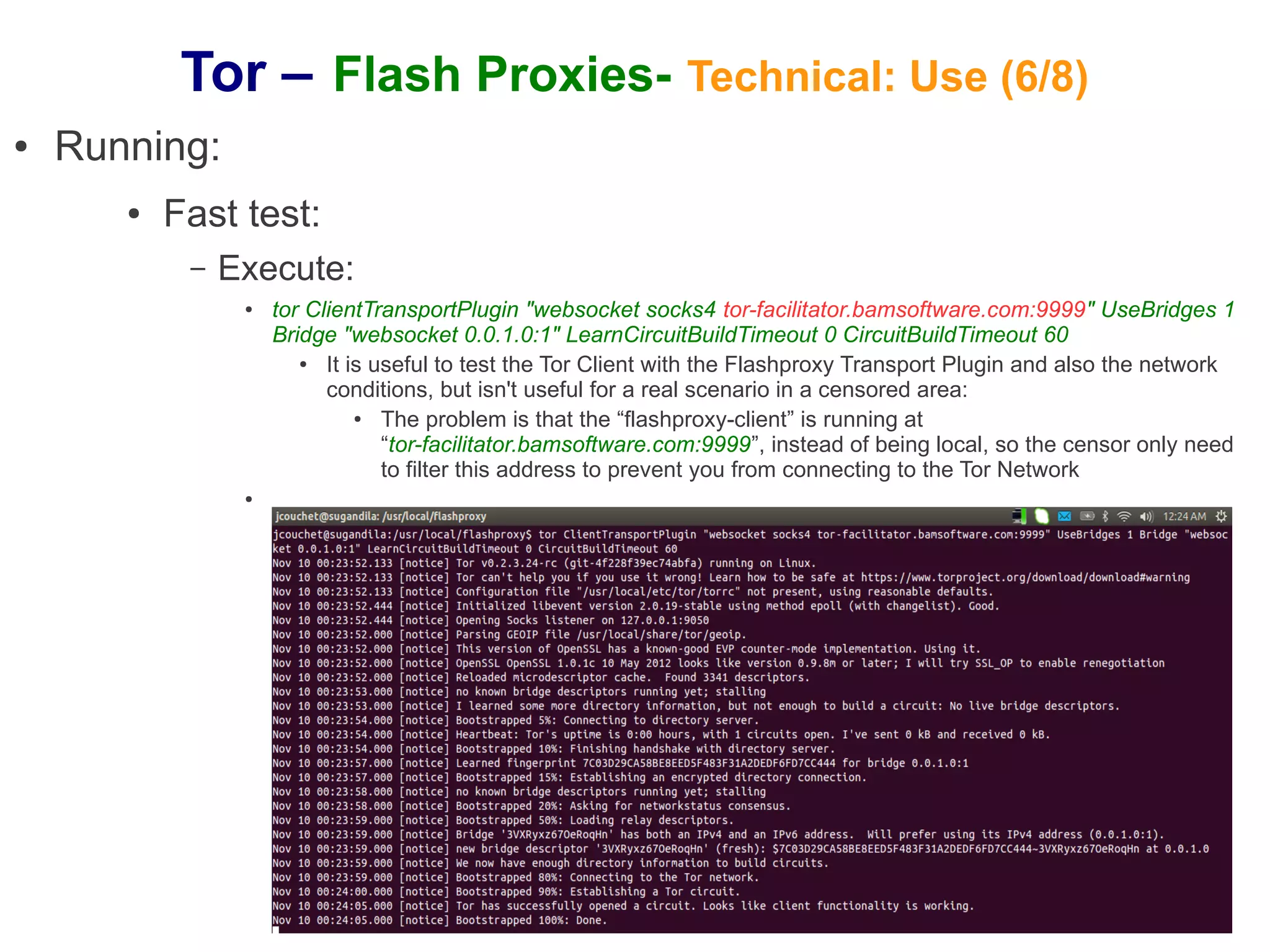
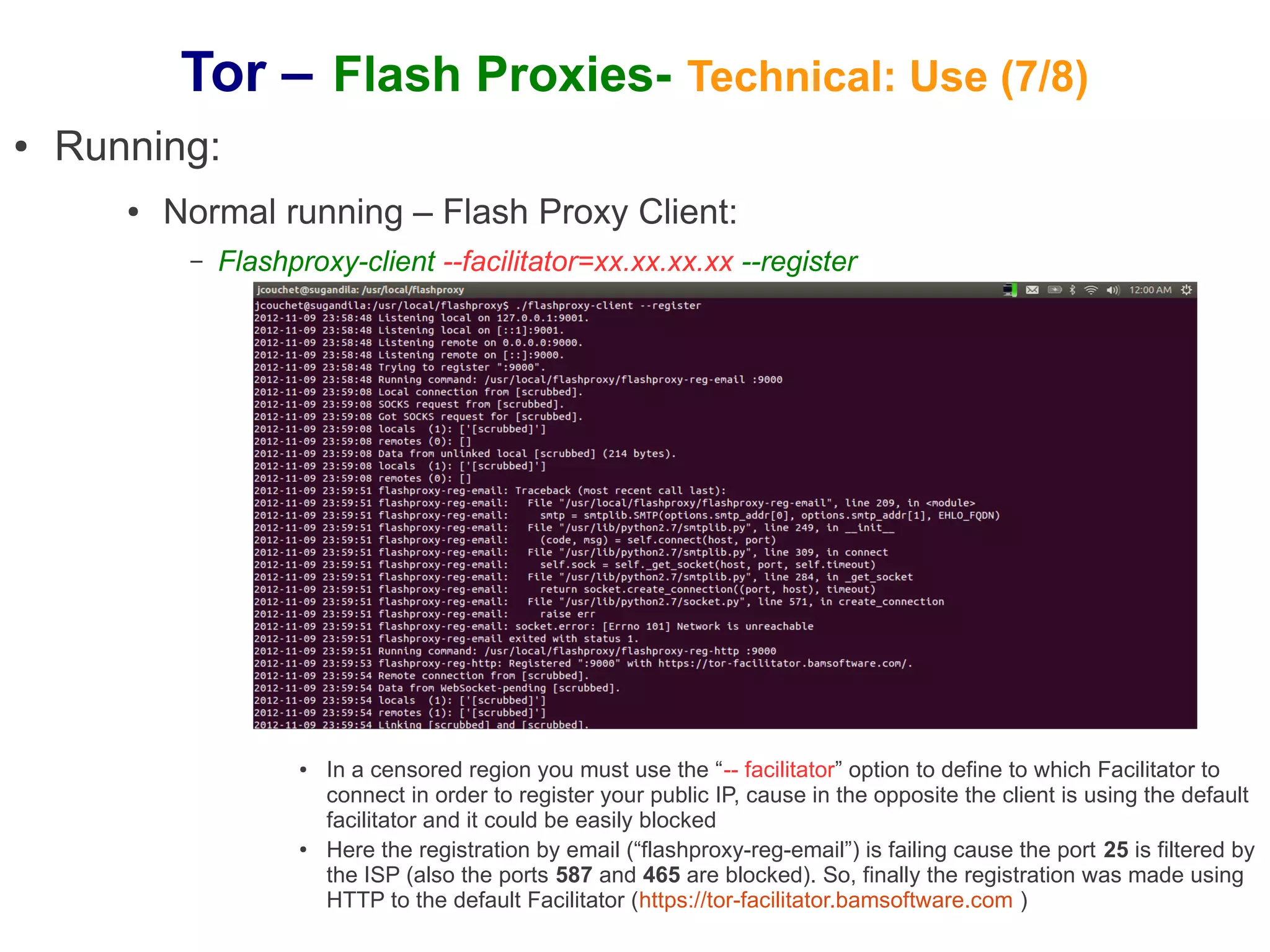
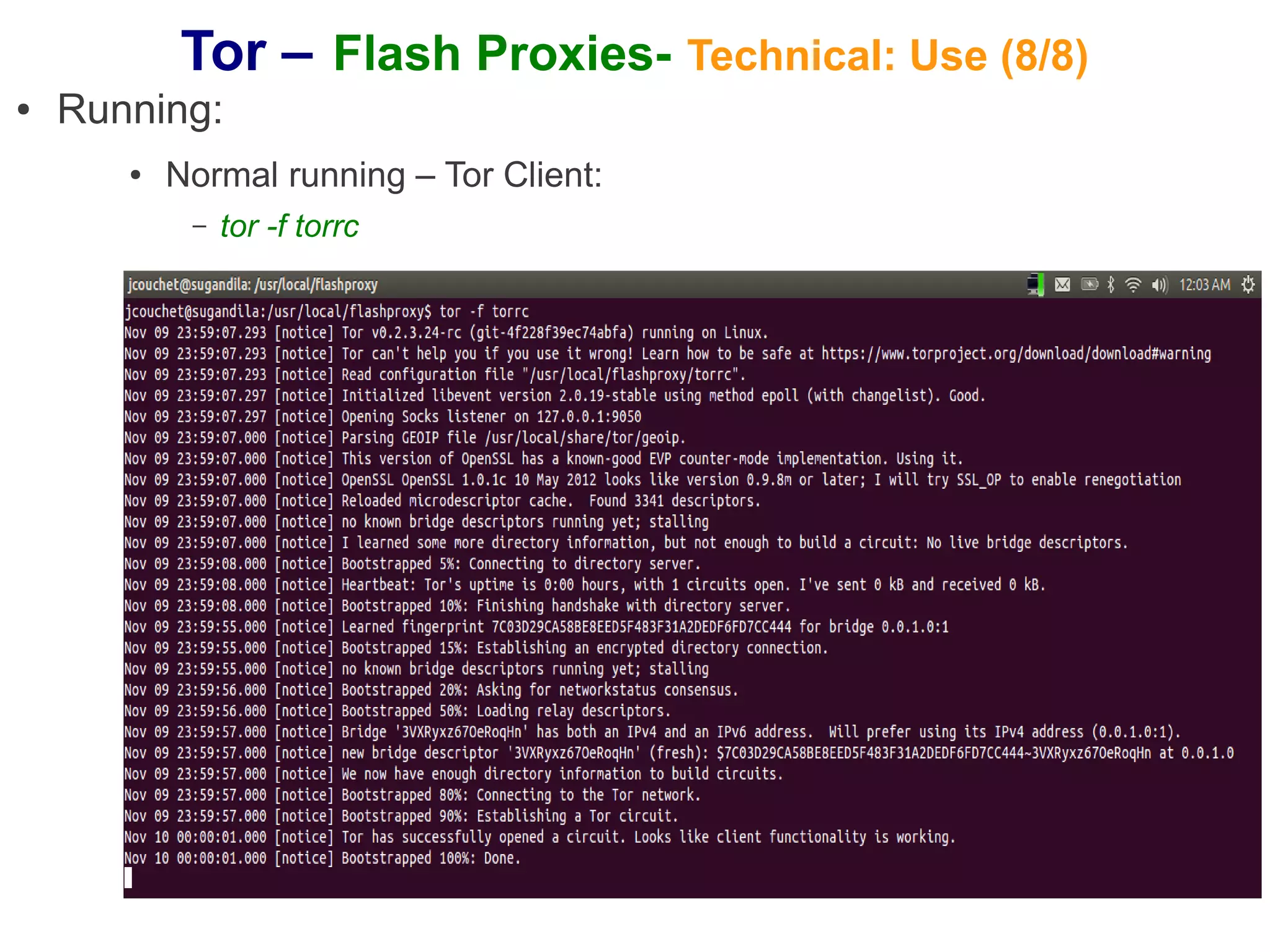
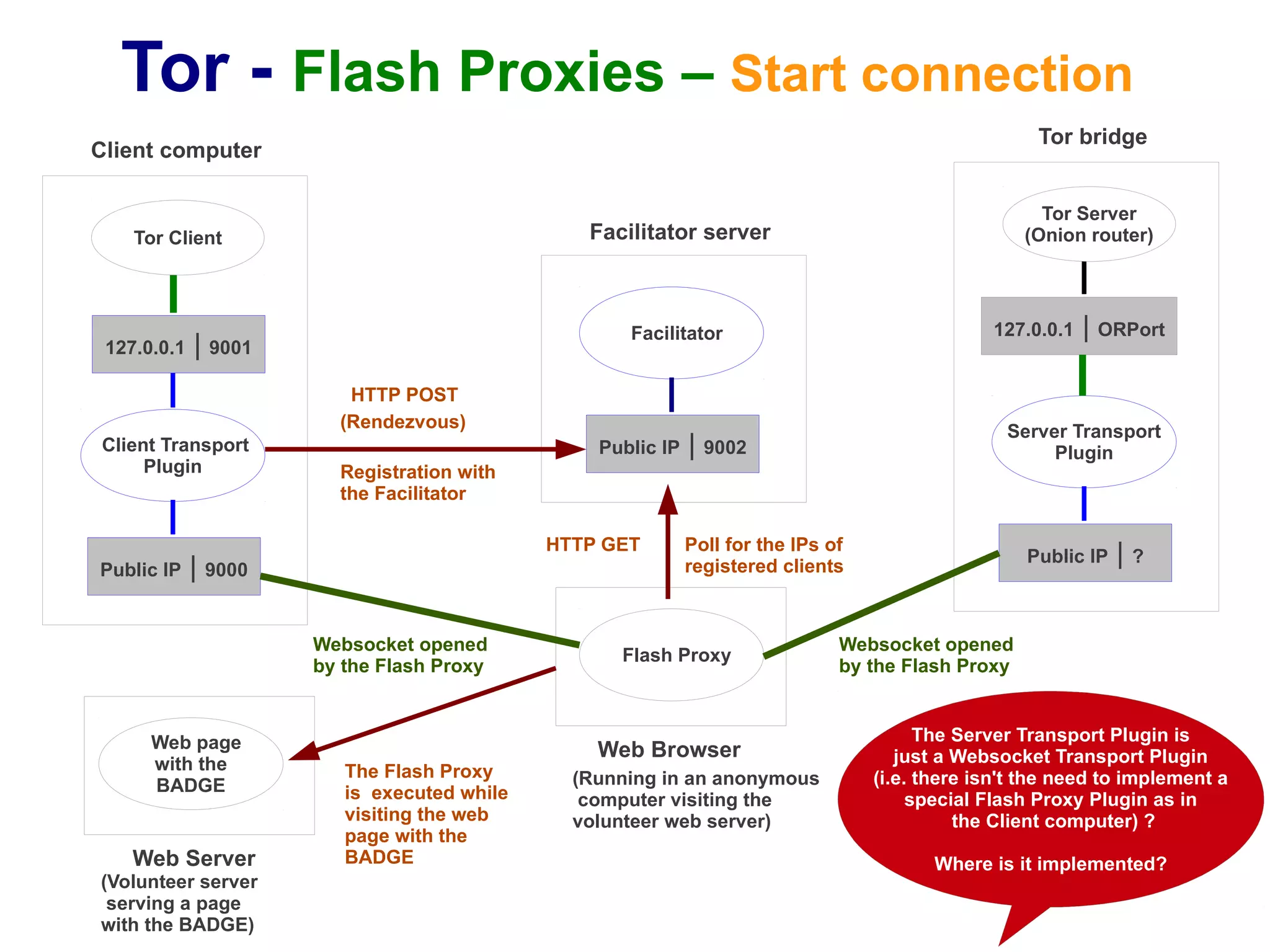
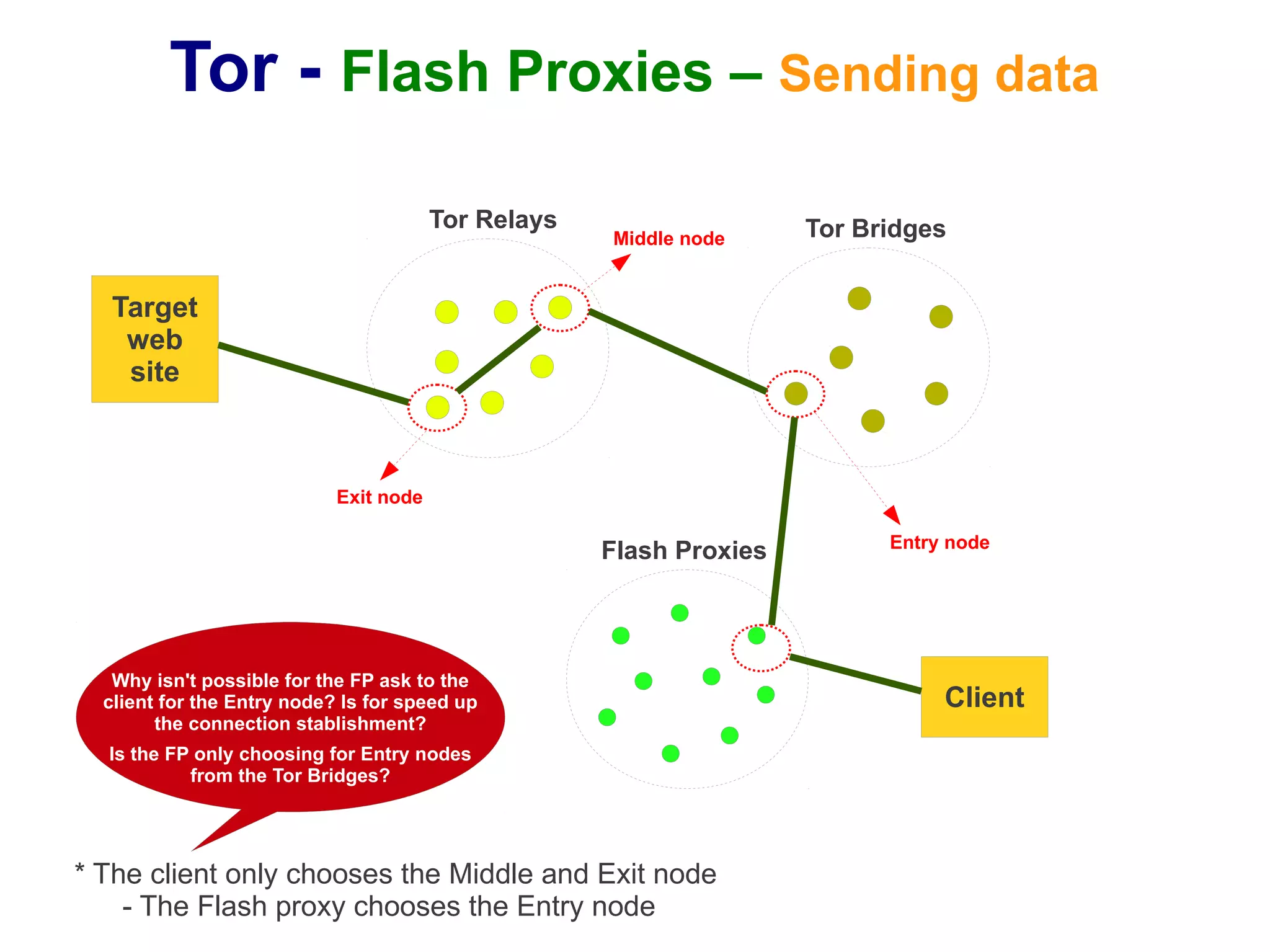
The document provides an overview of Tor and flash proxies. It defines key terms like anonymity and circumvention. It explains that flash proxies allow circumvention of censored networks by connecting to Tor bridges through volunteer web servers instead of directly. The technical implementation involves a client proxy plugin and server proxy that implement a new transport protocol to connect to Tor in a censored environment. The document provides instructions for installing Tor and flashproxy software and configuring them to work together.




![Tor – Flash Proxies- Technical: Pluggable transport (2/3)
● Implementation:
– "Client Proxy":
● At the “torrc” file:
– The “Bridge” option is modified in order to accept the <method> value:
● Bridge method address:port [[keyid=]id-fingerprint] [k=v] [k=v] [k=v]
– It is added the “ClientTransportPlugin” option:
● There are two kinds of “Client proxies”:
● The external ones: are running independent and the Tor Client must connect to them:
● ClientTransportPlugin <method> socks4 <address:port> [auth=X]
● ClientTransportPlugin <method> socks5 <address:port> [username=X] [password=Y]
● The managed ones: the Tor Client must execute them:
● ClientTransportPlugin <methods> exec <path> [options]
● Example:
– Configuration at the “torrc” file:
● Bridge trebuchet 200.178.1.34:3333 keyid=09F911 usr=xx pwd=yy
● ClientTransportPlugin trebuchet socks5 127.0.0.1:9999
– Meaning:
● The Tor Client knows that in order to connect to the Tor Network should use the “trebuchet” transport
(indicated by the “Brigde” option). In order to use this transport it must send its traffic to the local process
waiting at the port 9999 using SOCKS 5 (indicated by the “ClientTransportPlugin” option). This local
process must send the traffic to 200.178.1.34:3333, providing the strings "usr=xx;pwd=yy" as the user
and the password](https://image.slidesharecdn.com/tor-121110154315-phpapp01/75/Tor-Project-overview-9-2048.jpg)
![Tor – Flash Proxies- Technical: Pluggable transport (3/3)
● Implementation:
– "Server Proxy":
● At the “torrc” file:
– It is added the “ServerTransportPlugin” option:
● There are two kinds of “Server proxies”:
● The external ones: are running independent and the Tor Server must connect to
them:
● ServerTransportPlugin <method> proxy <address:port> <param=val> ...
● The managed ones: the Tor Server must execute them:
● ServerTransportPlugin <methods> exec </path/to/binary> [options]
● Example:
– Configuration at the “torrc” file:
● ServerTransportPlugin trebuchet proxy 127.0.0.1:999 usr=aa
– Meaning:
How is working it related with the “Client proxy” configuration and
with the Tor Server (i.e. in which address and port the “Server
Proxy” is listening the outside connection and how is it
sending the information to the Tor Server)?
How knows the “Client Proxy” where to connect to the “Server Proxy”?](https://image.slidesharecdn.com/tor-121110154315-phpapp01/75/Tor-Project-overview-10-2048.jpg)