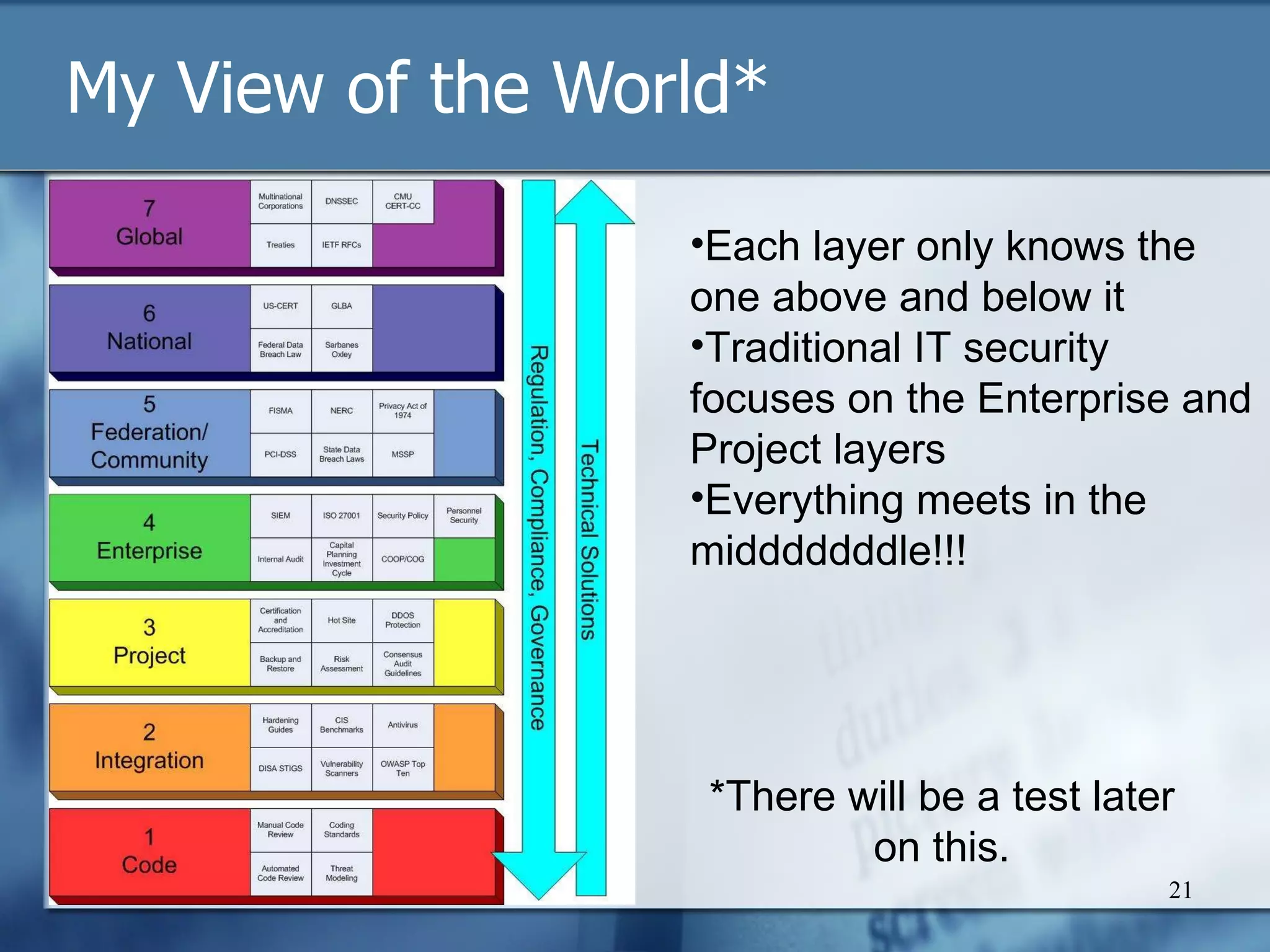
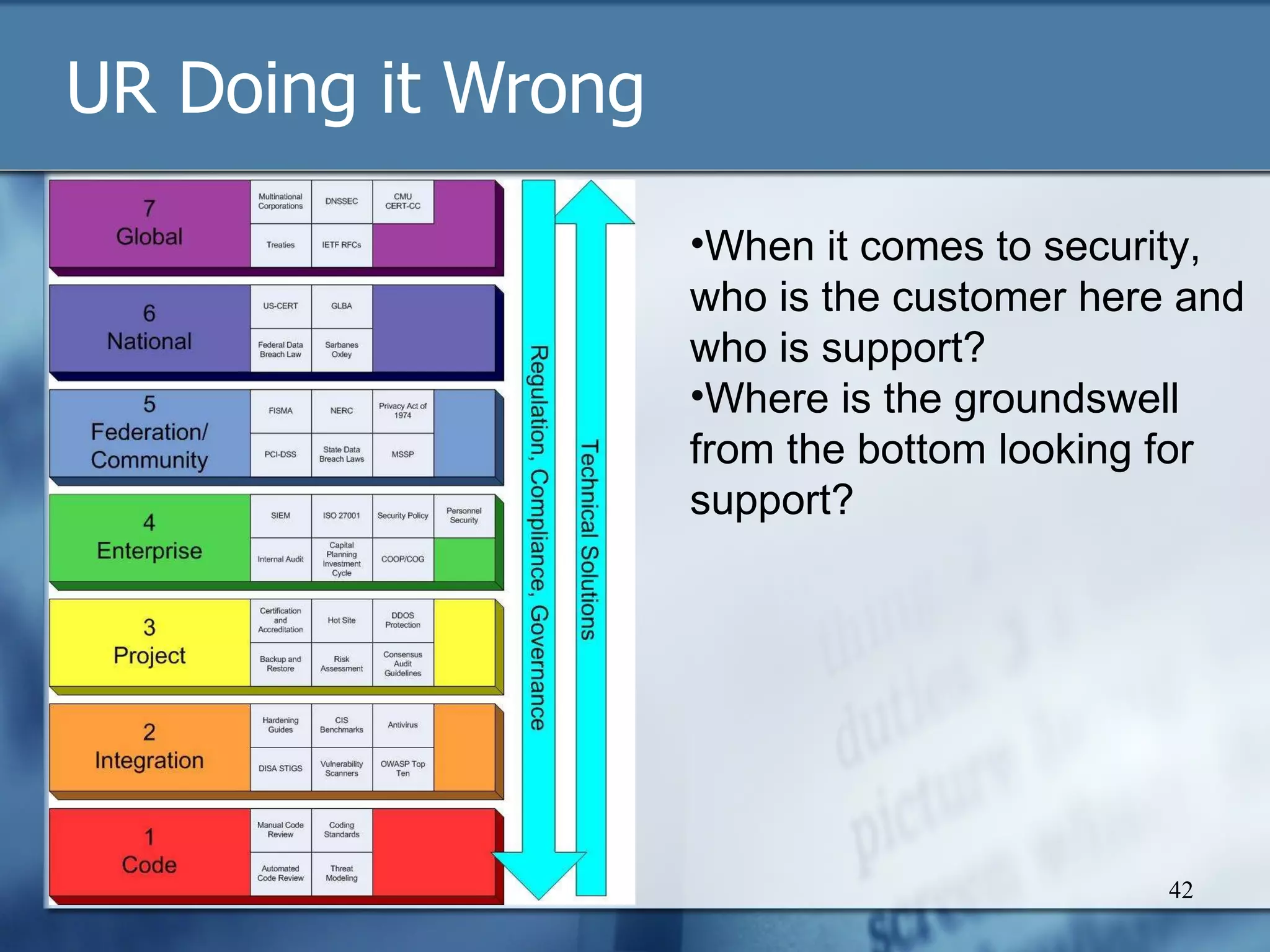
The document discusses the challenges and complexities of compliance in information security, highlighting the disconnect between decision-makers and the consequences of their choices. It emphasizes the need for better collaboration between compliance professionals and technical experts to bridge the gap in security practices. Ultimately, it argues for self-regulation and community-driven standards to foster a more effective compliance environment.