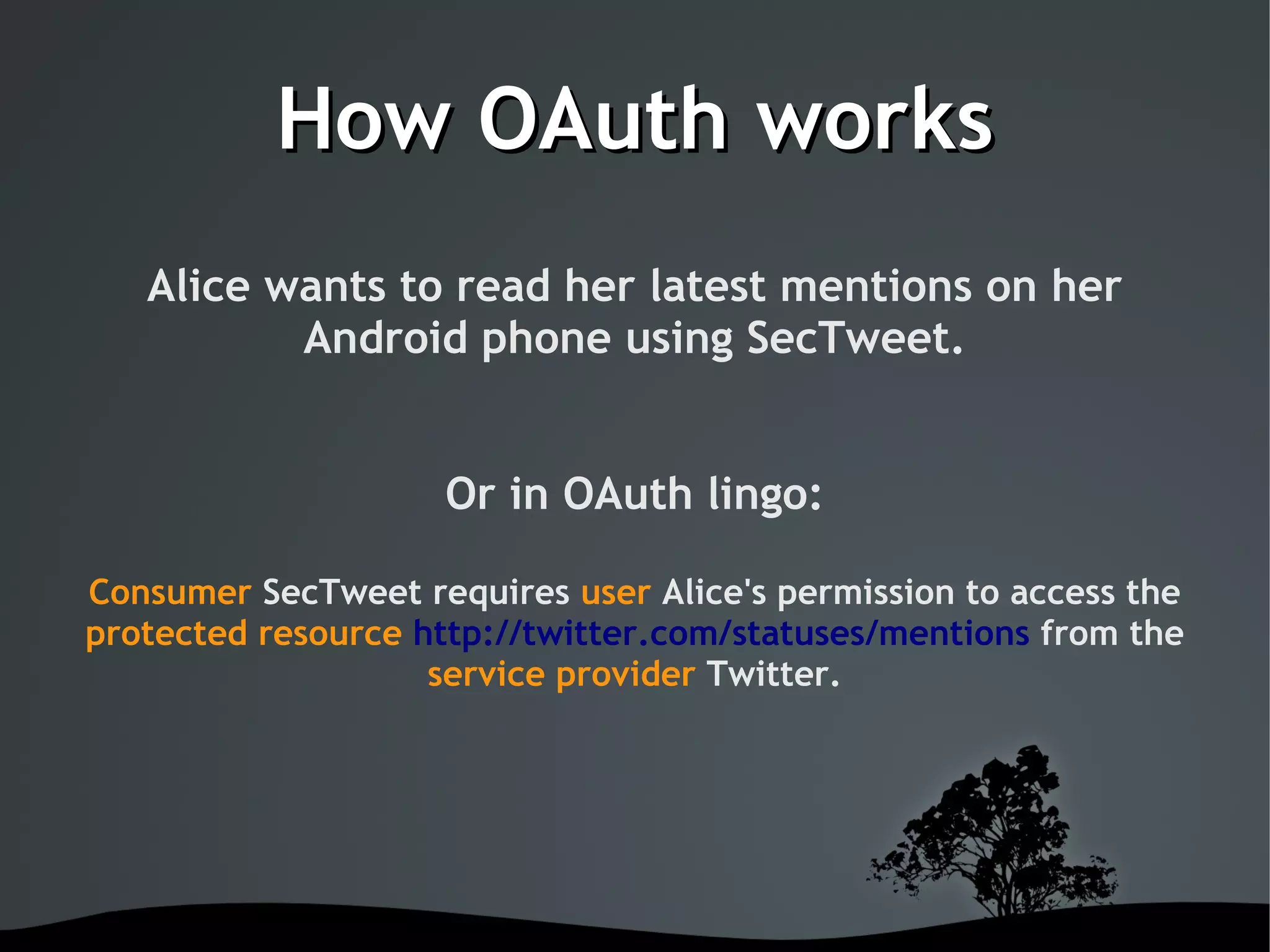
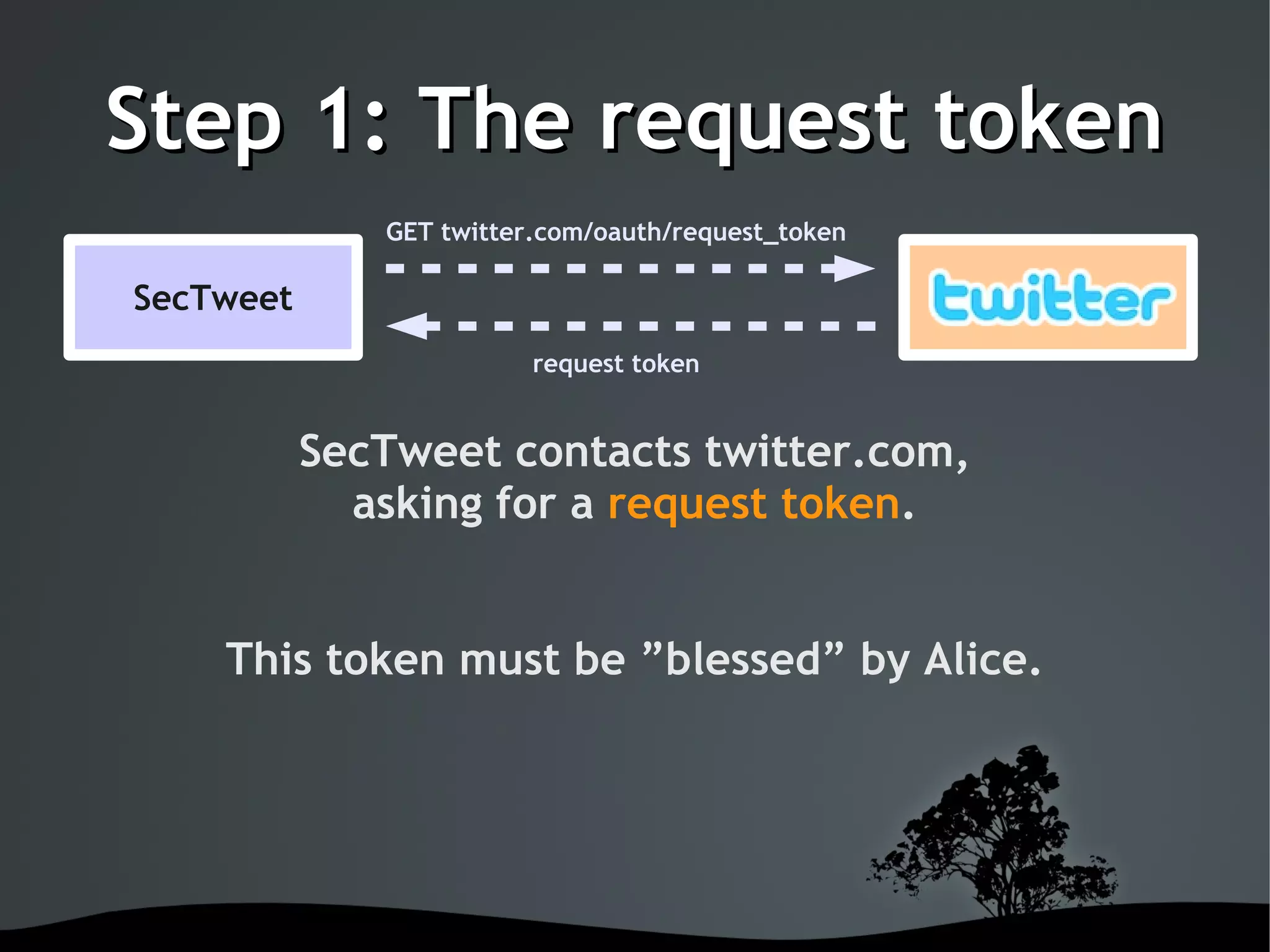
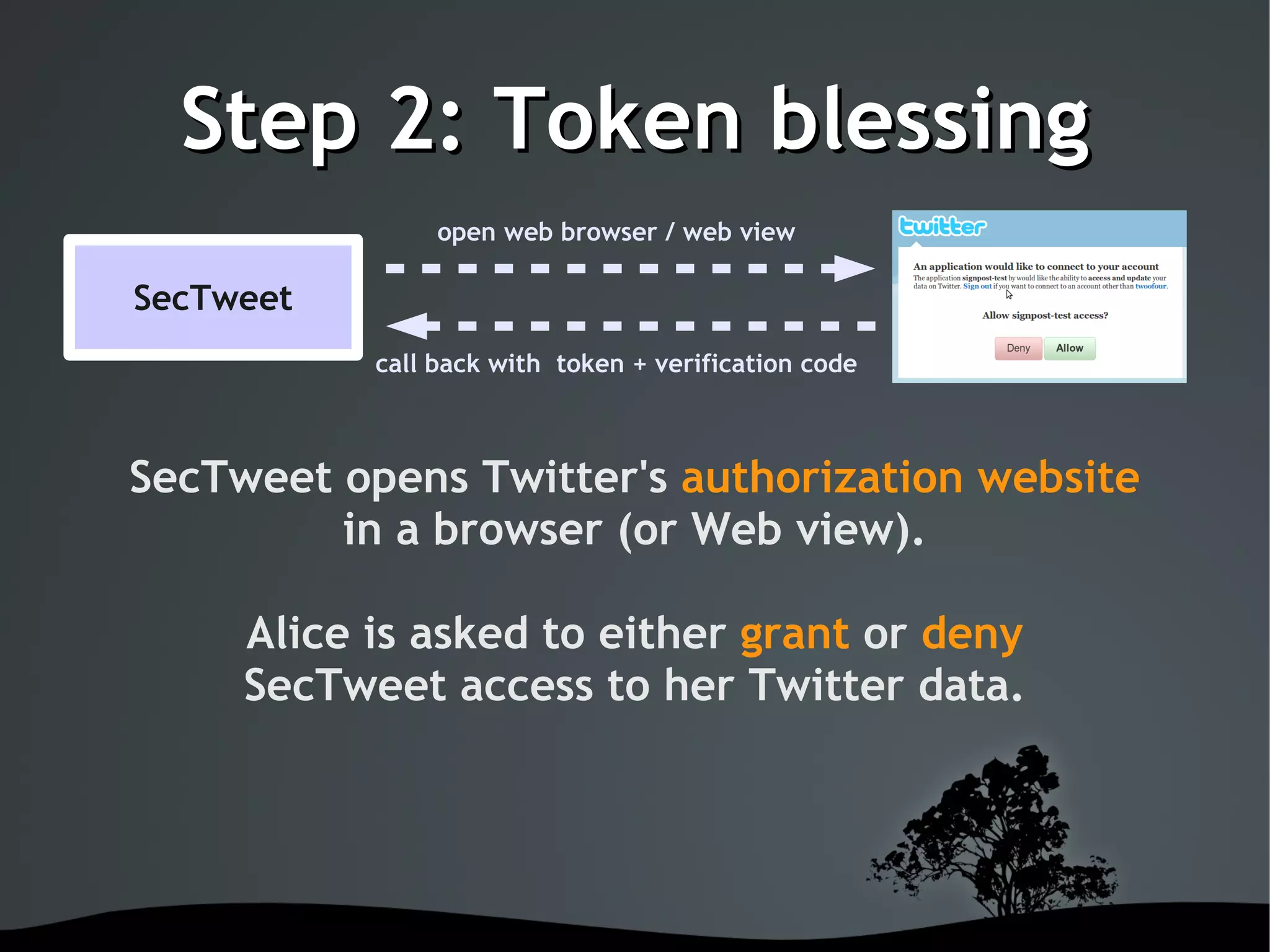
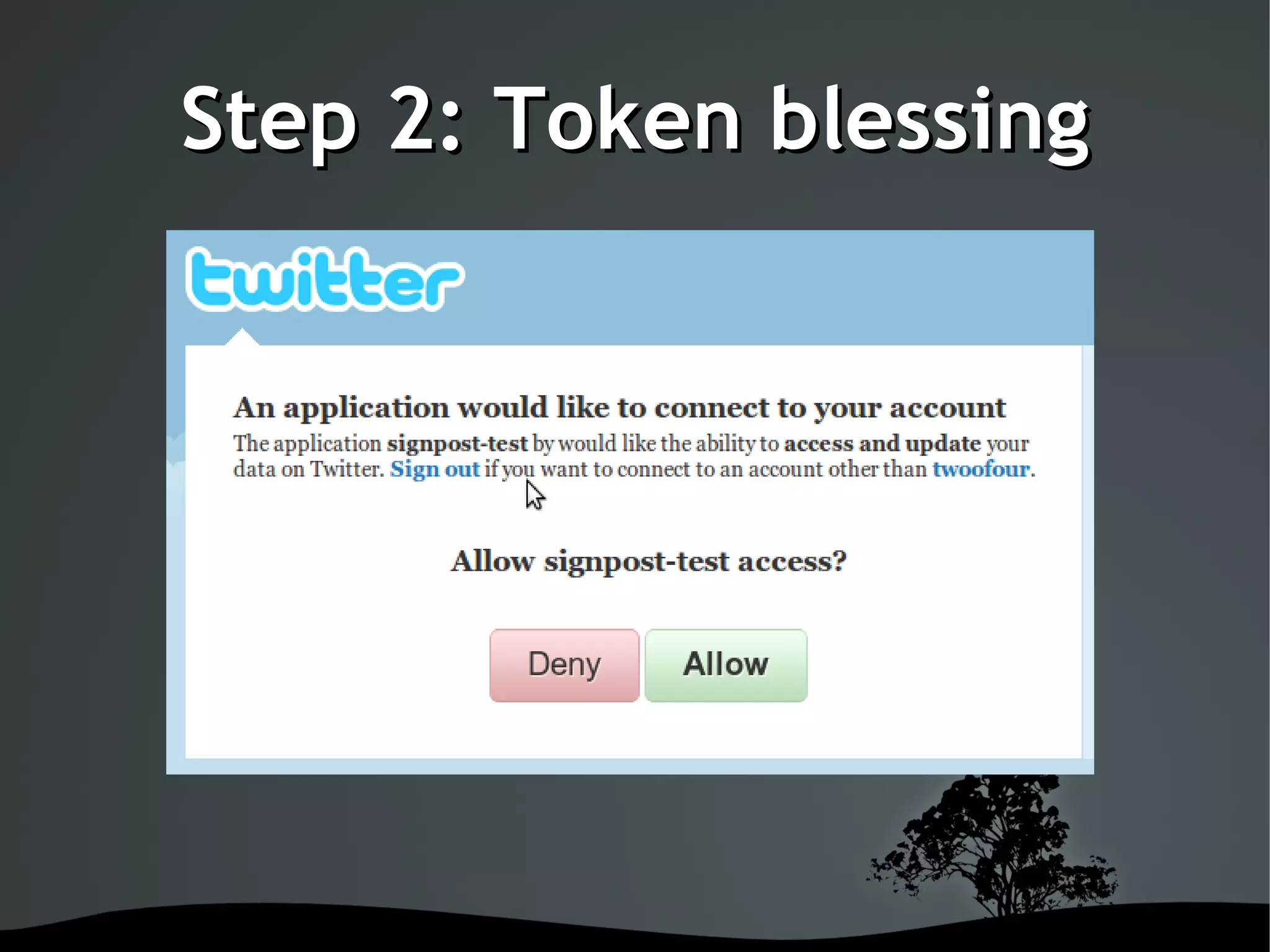
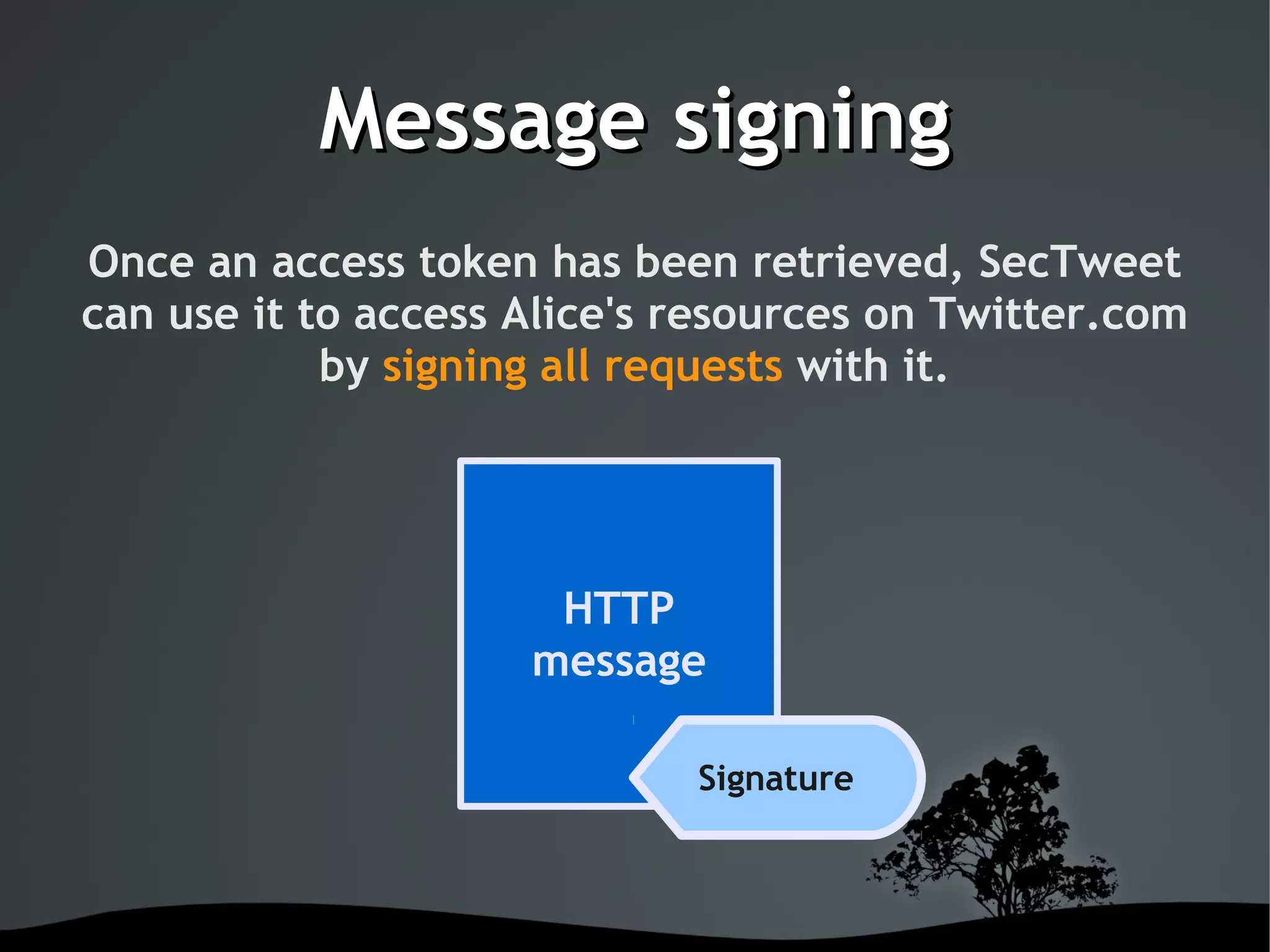
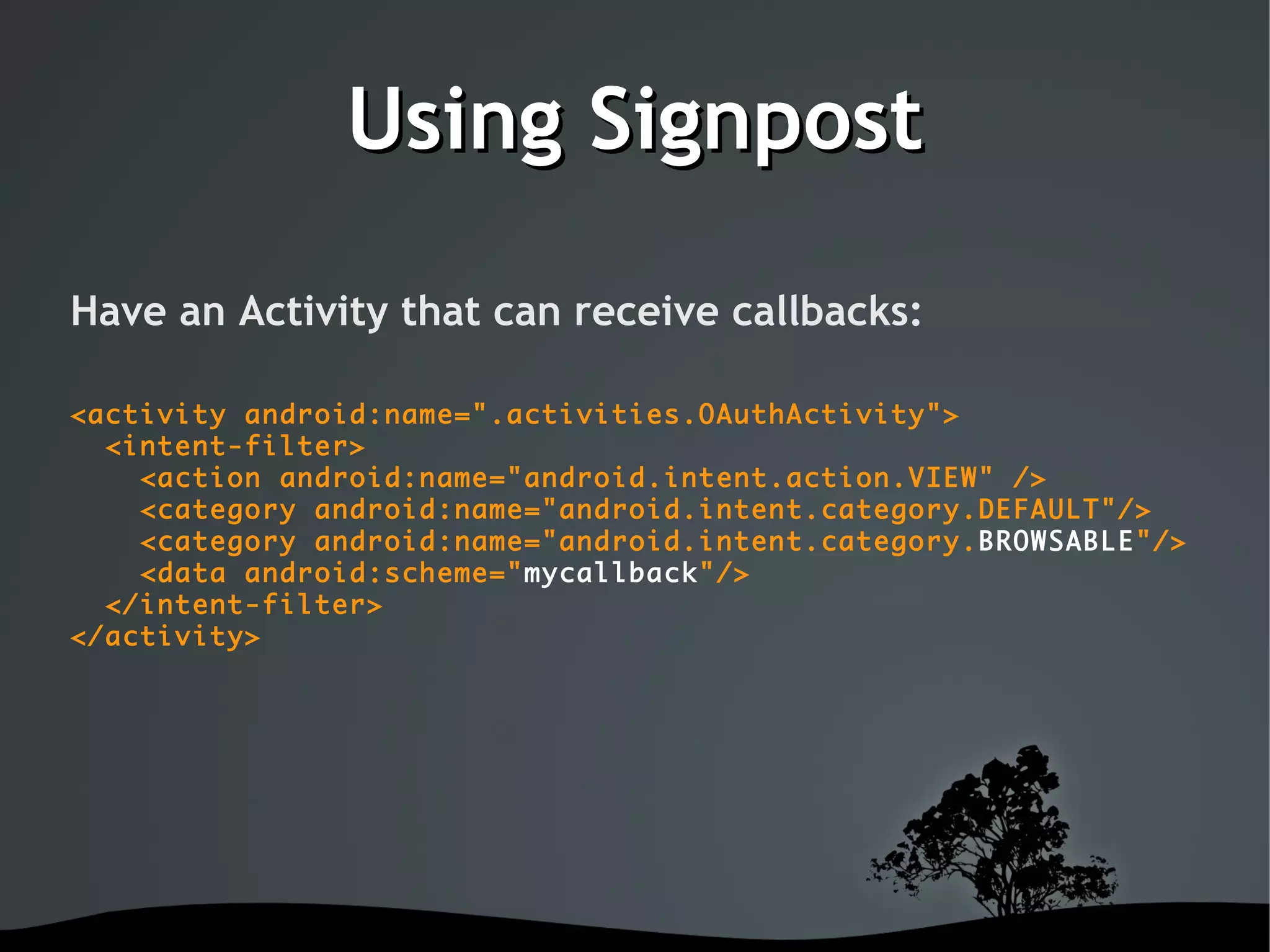
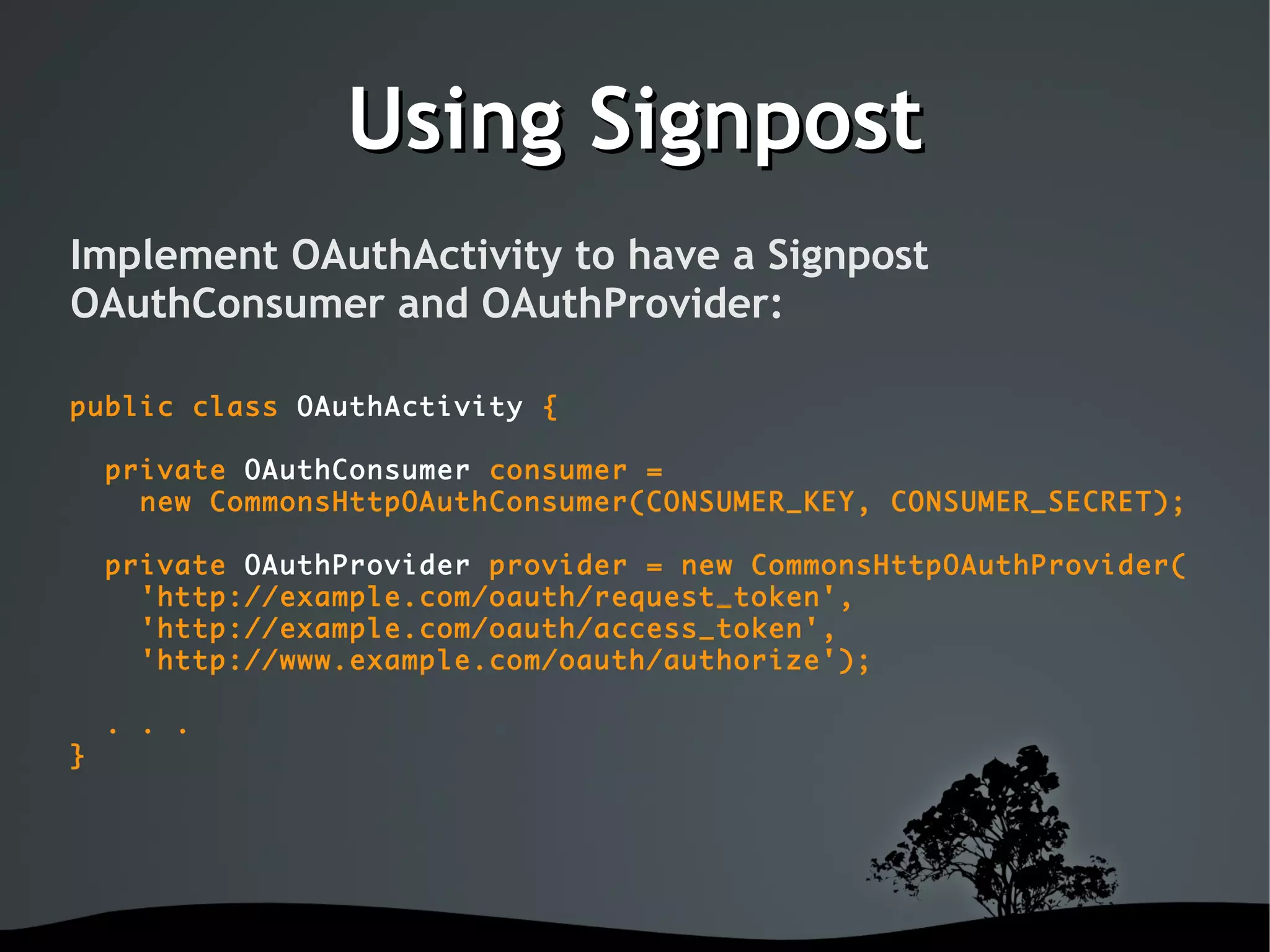
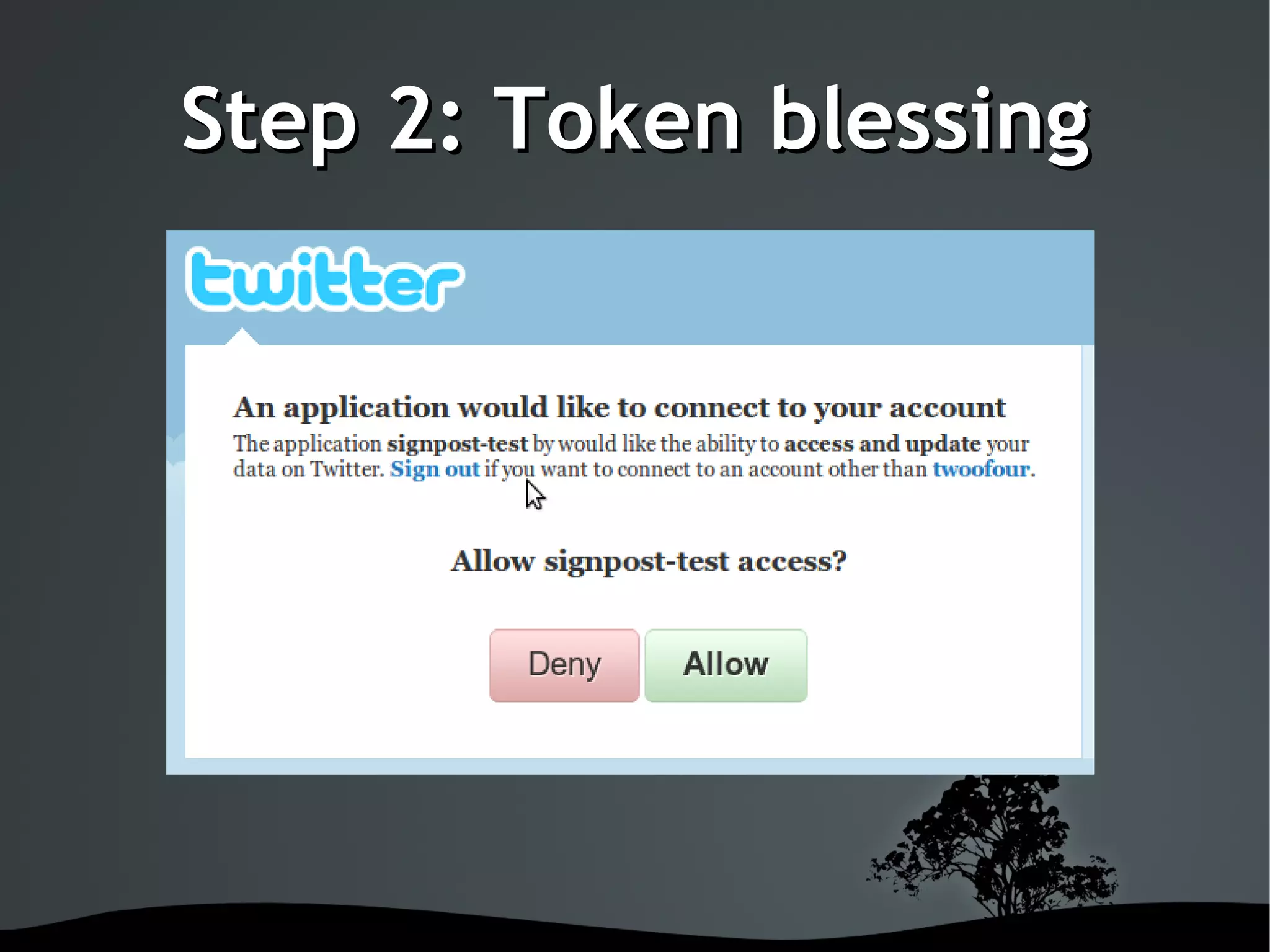
This document discusses using OAuth for securing web services on Android applications. It begins with an introduction to OAuth and its goals of allowing users to grant access to private resources like social media profiles without sharing usernames and passwords. It then explains the basic OAuth workflow involving a 3-step handshake to obtain a request token, having the user authorize the client, and exchanging the request token for an access token. The document concludes by demonstrating how to implement OAuth in an Android app using the Signpost library, which integrates with HTTP clients and handles token management.






![What is OAuth?
OAuth.net
”An open protocol to allow secure API authorization
in a simple and standard method from desktop and
web applications.”
Wikipedia.org
”OAuth is an open protocol that allows users to share
their private resources [...] stored on one site with
another site without having to hand out their
username and password.”](https://image.slidesharecdn.com/securewebservices-13008976390193-phpapp02/75/Secure-Webservices-8-2048.jpg)